1 of 17
Download to read offline
















Recommended
Expl sw chapter_06_inter_vlan



Expl sw chapter_06_inter_vlanaghacrom
Ěý
This document discusses inter-VLAN routing and different methods for implementing it. It introduces inter-VLAN routing as a process of forwarding traffic between VLANs using a router. There are three main methods discussed: traditional routing using one interface per VLAN, router-on-a-stick using subinterfaces on a single router interface, and switch-based routing using switch virtual interfaces. The document provides detailed explanations and configurations for router-on-a-stick inter-VLAN routing.Expl sw chapter_07_wireless rev.01(additional)



Expl sw chapter_07_wireless rev.01(additional)aghacrom
Ěý
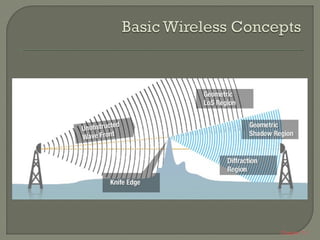
Bab 7-1 membahas tentang jarak antara titik A dan P yang sama dengan jarak antara titik B dan P dengan mengubah nilai panjang gelombang. Persamaan dijelaskan untuk menghitung nilai maksimum radius zon Fresnel pertama dengan mengkonversi frekuensi dan jarak total ke GHz dan Km. Diuraikan pula tentang grid antenna vertikal dan horizontal serta gelombang vertikal dan horizontal. Terakhir dijelaskan tentang radio point to point tanpa gangguan dan dengan gangguan pManaging Redundant Links & Inter-VLAN Routing



Managing Redundant Links & Inter-VLAN RoutingSandeep Sharma IIMK Smart City,IoT,Bigdata,Cloud,BI,DW
Ěý
This document discusses managing redundant links and spanning tree protocols. It describes spanning tree protocol (STP) operations including electing a root bridge, path cost calculations, port states and BPDU timers. It also covers spanning tree in VLAN environments, such as per-VLAN STP (PVST), and techniques for scaling STP, including modifying root selection, path costs, port priorities and timers. Other topics include Fast EtherChannel, PortFast and UplinkFast for improving convergence times.Inter-Vlan Routeando



Inter-Vlan RouteandoAlberto Jimenez
Ěý
This document discusses configuring inter-VLAN routing to enable communication between devices on different VLANs. It covers explaining how network traffic is routed between VLANs, configuring inter-VLAN routing on a router by adding subinterfaces for each VLAN and assigning IP addresses, and troubleshooting common inter-VLAN connectivity issues like misconfigured switches, routers, or incorrect IP addressing.CCNA Lab 5-Configuring Inter-VLAN Routing



CCNA Lab 5-Configuring Inter-VLAN RoutingAmir Jafari
Ěý
This document provides instructions for configuring inter-VLAN routing on a network with three switches and one router. It describes preparing the network topology, configuring basic settings on the devices, creating VLANs on the switches, configuring trunk links and EtherChannels, and using 802.1Q encapsulation on the router interfaces to route between the VLANs. Verification steps are provided to test the configuration at each stage.The Governance Framework For Managing Change



The Governance Framework For Managing ChangeSandeep Sharma IIMK Smart City,IoT,Bigdata,Cloud,BI,DW
Ěý
This document outlines key elements of a customer service operations model including resources like manpower, money, materials and machines as well as regulatory compliance and governance, risk and compliance processes. Resources such as employees, funding, materials and equipment are necessary to deliver customer service alongside adhering to relevant regulations and maintaining appropriate governance, risk and compliance protocols.Expl sw chapter_07_wireless rev.01



Expl sw chapter_07_wireless rev.01aghacrom
Ěý
This document discusses basic concepts of wireless networking and wireless LAN configuration. It begins by explaining how wireless networking allows for mobile productivity as users can access the network from any location. It then discusses why wireless networking is used, including flexibility and reduced costs compared to wired networks. Finally, it covers wireless LAN components like wireless access points that connect wireless clients to the wired LAN, and wireless network interface cards that allow devices to connect to the network wirelessly.Expl sw chapter_05_stp_part_i-rev2.



Expl sw chapter_05_stp_part_i-rev2.aghacrom
Ěý
Redundant layer 2 topologies can create loops in the network. Spanning Tree Protocol (STP) controls this by logically blocking ports on switches to ensure only a single path exists between devices. STP elects a root bridge and designates root, designated and blocked ports to break up loops while maintaining connectivity. It prevents issues like broadcast storms and duplicate unicast frames that can occur due to loops in the network.Expl sw chapter_04_vtp-full



Expl sw chapter_04_vtp-fullaghacrom
Ěý
VTP allows VLAN configurations to be synchronized across multiple switches, simplifying network management. It operates by electing a switch as the VTP server, where VLANs can be created and modified. This information is then propagated through VTP advertisements to other switches operating as clients or in transparent mode. Troubleshooting may involve checking the VTP domain name, revision number, and that at least one switch is operating as a server.Expl sw chapter_03_vla_ns_part_ii



Expl sw chapter_03_vla_ns_part_iiaghacrom
Ěý
VLAN trunking allows traffic from multiple VLANs to travel across the same link between two switches. This reduces the number of required physical links and saves on infrastructure costs. VLAN trunks use tagging to identify which VLAN each frame belongs to as switches forward frames based on MAC addresses only. Common trunking modes are 802.1Q, which is now the standard, and ISL, which was used in older Cisco switches but is no longer recommended. Dynamic Trunking Protocol (DTP) can be used to automatically negotiate trunking settings between switches.Expl sw chapter_03_vla_ns_part_i



Expl sw chapter_03_vla_ns_part_iaghacrom
Ěý
Dokumen tersebut membahas tentang VLAN (Virtual Local Area Network) yang merupakan teknologi jaringan untuk membagi logis jaringan switch menjadi beberapa subnet virtual. VLAN memungkinkan pembagian jaringan berdasarkan fungsi, tim proyek, aplikasi, atau koneksi ke jaringan lain. Komunikasi antar VLAN memerlukan router namun hanya membutuhkan satu koneksi fisik. Dokumen juga menjelaskan tipe-tipe VLAN seperti data VLAN, default VLANExpl sw chapter_02_switches_part_1



Expl sw chapter_02_switches_part_1aghacrom
Ěý
This document discusses key concepts of Ethernet and switch configuration. It describes Ethernet frame formats, MAC addresses, switch port settings including auto-negotiation and auto-MDIX. It explains how switches use MAC address tables to forward traffic, providing examples of entries being added to the table. Design considerations for Ethernet like bandwidth and collisions are also covered.Expl sw chapter_02_switches_part_2



Expl sw chapter_02_switches_part_2aghacrom
Ěý
This document discusses switch security configuration and common security attacks. It covers topics such as configuring passwords, console access, virtual terminal access, banners, telnet/SSH, and port security. Various security attacks are also described like MAC address flooding, spoofing attacks, CDP attacks, and telnet attacks. The document provides configuration examples for securing switch access and interfaces using passwords, banners, telnet/SSH, and port security features.More Related Content
More from aghacrom (7)
Expl sw chapter_04_vtp-full



Expl sw chapter_04_vtp-fullaghacrom
Ěý
VTP allows VLAN configurations to be synchronized across multiple switches, simplifying network management. It operates by electing a switch as the VTP server, where VLANs can be created and modified. This information is then propagated through VTP advertisements to other switches operating as clients or in transparent mode. Troubleshooting may involve checking the VTP domain name, revision number, and that at least one switch is operating as a server.Expl sw chapter_03_vla_ns_part_ii



Expl sw chapter_03_vla_ns_part_iiaghacrom
Ěý
VLAN trunking allows traffic from multiple VLANs to travel across the same link between two switches. This reduces the number of required physical links and saves on infrastructure costs. VLAN trunks use tagging to identify which VLAN each frame belongs to as switches forward frames based on MAC addresses only. Common trunking modes are 802.1Q, which is now the standard, and ISL, which was used in older Cisco switches but is no longer recommended. Dynamic Trunking Protocol (DTP) can be used to automatically negotiate trunking settings between switches.Expl sw chapter_03_vla_ns_part_i



Expl sw chapter_03_vla_ns_part_iaghacrom
Ěý
Dokumen tersebut membahas tentang VLAN (Virtual Local Area Network) yang merupakan teknologi jaringan untuk membagi logis jaringan switch menjadi beberapa subnet virtual. VLAN memungkinkan pembagian jaringan berdasarkan fungsi, tim proyek, aplikasi, atau koneksi ke jaringan lain. Komunikasi antar VLAN memerlukan router namun hanya membutuhkan satu koneksi fisik. Dokumen juga menjelaskan tipe-tipe VLAN seperti data VLAN, default VLANExpl sw chapter_02_switches_part_1



Expl sw chapter_02_switches_part_1aghacrom
Ěý
This document discusses key concepts of Ethernet and switch configuration. It describes Ethernet frame formats, MAC addresses, switch port settings including auto-negotiation and auto-MDIX. It explains how switches use MAC address tables to forward traffic, providing examples of entries being added to the table. Design considerations for Ethernet like bandwidth and collisions are also covered.Expl sw chapter_02_switches_part_2



Expl sw chapter_02_switches_part_2aghacrom
Ěý
This document discusses switch security configuration and common security attacks. It covers topics such as configuring passwords, console access, virtual terminal access, banners, telnet/SSH, and port security. Various security attacks are also described like MAC address flooding, spoofing attacks, CDP attacks, and telnet attacks. The document provides configuration examples for securing switch access and interfaces using passwords, banners, telnet/SSH, and port security features.Expl sw chapter_07_wireless rev.01(additional)
- 1. Chapter 7-1
- 2. Chapter 7-1
- 3. Chapter 7-1
- 4. Chapter 7-1
- 5. Chapter 7-1
- 6. Chapter 7-1
- 7. Chapter 7-1
- 8. Chapter 7-1 JarJaraak ak antara titik Antara titik A ke titik P akan sama dengan jarak darike titik P akan sama dengan jarak dari titiktitik BB keke titiktitik PP,, dengan mengubah nilai panjangdengan mengubah nilai panjang gelombanggelombang ((λλ) ke) ke sinyal frekuensi kita dapatsinyal frekuensi kita dapat membuatmembuat persamaanpersamaan sebagai berikut:sebagai berikut:
- 9. Chapter 7-1 Dari persamaan diatas,Dari persamaan diatas, jika nilai untuk frekuensi dan jarakjika nilai untuk frekuensi dan jarak total dikonversitotal dikonversi masing-masingmasing-masing keke GHzGHz dadann KmKm,, makamaka persamaan untukpersamaan untuk Nilai Maksimum RNilai Maksimum Radiusadius (r)(r) padapada 11stst Fresnel ZonFresnel Zonee dapat diturunkan dengan cara berikut:dapat diturunkan dengan cara berikut:
- 10. Chapter 7-1 Antenna GridAntenna Grid Vertical PolarizationVertical Polarization Antenna GridAntenna Grid Horizontal PolarizationHorizontal Polarization
- 11. Chapter 7-1 Wave Vertical PolarizationWave Vertical Polarization Wave Horizontal PolarizationWave Horizontal Polarization
- 12. Chapter 7-1
- 13. Chapter 7-1
- 14. Chapter 7-1
- 15. Chapter 7-1 Radio Point to Point – Non InterferenceRadio Point to Point – Non Interference 2.4Ghz/Ch12.4Ghz/Ch1 2.4Ghz/Ch12.4Ghz/Ch1
- 16. Chapter 7-1 Radio Point to Point – InterferenceRadio Point to Point – Interference 2.4Ghz/Ch12.4Ghz/Ch1 2.4Ghz/Ch12.4Ghz/Ch1 2.4Ghz/Ch22.4Ghz/Ch2
- 17. Chapter 7-1

