FIDO Munich Seminar Workforce Authentication Case Study.pptx
ŌĆóDownload as PPTX, PDFŌĆó
0 likesŌĆó684 views
FIDO Munich Seminar Workforce Authentication Case Study.pptx
1 of 8
Downloaded 10 times




Recommended
UX Webinar Series: Drive Revenue and Decrease Costs with Passkeys for Consume...



UX Webinar Series: Drive Revenue and Decrease Costs with Passkeys for Consume...FIDO Alliance
╠²
UX Webinar Series: Drive Revenue and Decrease Costs with Passkeys for Consumer AuthenticationAccess Control time attendence, Biometrics UAE



Access Control time attendence, Biometrics UAEsecuritysytem
╠²
AVI INFOSYS is an ISO 9001:2008 certified biometric solutions provider based in Dubai that provides business consulting, software, and system integration services for biometric security solutions. They offer products like fingerprint identification systems, access control solutions, and time attendance software. AVI INFOSYS works with clients in industries like government, banking, manufacturing, and education to design customized biometric security and information management systems. WatchGuard Integrates with CommScope RUCKUS: Full Solutions for 2021



WatchGuard Integrates with CommScope RUCKUS: Full Solutions for 2021Purdicom
╠²
We will be exploring the current issues on Wi-Fi security by identifying how safe is the end-user from existing and new Wi-Fi threats emerging daily, why we cannot depend on a standalone access point to detect and prevent all new threats from hackers.
Also, look into WatchGuard's solutions. How it automatically acts as an overlay on existing access points and not only provides safe Wi-Fi traffic but, also delivers unprecedented WIPS security protection that is 100% dedicated to scanning the air and protecting your business from wireless threats 24/7.
Join us as Alex Claro (Head of Technical) and Paul Summerland (Major Account Manager) - take us through the most fundamental security solutions for your access points.FIDO Masterclass



FIDO MasterclassFIDO Alliance
╠²
The document discusses FIDO Alliance's efforts to create simpler and stronger authentication standards to replace passwords. It provides an overview of FIDO authentication, including how it works, adoption rates, and certification programs. It also summarizes the Alliance's work in identity verification, binding, and FIDO Device Onboarding to fill gaps and further the passwordless vision.UX Webinar Series: Essentials for Adopting Passkeys as the Foundation of your...



UX Webinar Series: Essentials for Adopting Passkeys as the Foundation of your...FIDO Alliance
╠²
UX Webinar Series: Essentials for Adopting Passkeys as the Foundation of your Consumer Authentication StrategyWildix German Convention 2017 | Frankfurt am Main



Wildix German Convention 2017 | Frankfurt am MainWildix
╠²
Presentations of the Wildix German Convention 2017 in Frankfurt am Main on the 27th and 28th January. FIDO Munich Seminar FIDO Automotive Apps.pptx



FIDO Munich Seminar FIDO Automotive Apps.pptxFIDO Alliance
╠²
FIDO Munich Seminar FIDO Automotive Apps.pptxParadigmo specialised in Identity & Access Management



Paradigmo specialised in Identity & Access ManagementJulie Beuselinck
╠²
Olivier Naveau, Managing Director of the company, presented on identity and access management (IAM). Access control is a top priority for companies according to security surveys. IAM remains difficult due to the growing number of users and applications as well as an evolving landscape including cloud, mobile, social, and compliance needs. The presentation outlined a structured approach to IAM including administering identity data, key IAM processes, technologies, and identifying business value metrics. Paradigmo's proposal takes a process-based approach utilizing ForgeRock's identity platform and Brainwave for identity intelligence.Hardening as a Part of a holistic Security Strategy (UPDATE)



Hardening as a Part of a holistic Security Strategy (UPDATE)NoCodeHardening
╠²
Why are IT Forensic and System Hardening so important for your company? How can you significantly increase the level of your IT Security? This presentation gives you the answers.Black Box India_Corporate_Deck_May23-║▌║▌▀Żshare.pdf



Black Box India_Corporate_Deck_May23-║▌║▌▀Żshare.pdfBlack Box
╠²
Black Box® is a trusted IT solutions provider delivering cutting-edge technology solutions and world-class consulting services to businesses around the globe. The breadth of our global reach and the depth of our expertise accelerate customer success by bringing people, ideas, and technology together to solve real-world business problems. Our IT infrastructure solutions, services, and products enable secure, flawless connectivity and meaningful collaboration for businesses in every major market sector on six continents.
For more information please visit - https://www.blackbox.com/en-us/discover-bb/about-blackbox Smart Cards & Devices Forum 2013 - Protecting enterprise sensitive informatio...



Smart Cards & Devices Forum 2013 - Protecting enterprise sensitive informatio...OKsystem
╠²
This document introduces Gemalto and their solution called Armored Office. It discusses how static passwords are no longer enough for security and compliance with regulations. Armored Office provides a solution for strong authentication and encryption to securely access networks and data from any device. It offers a single credential to log in to endpoints, access networks remotely, and encrypt files/emails. The target market is security-sensitive organizations for executives and users with access to sensitive information. It aims to protect data and enable secure access from any device while meeting compliance requirements.Webinar: Eliminating Negative Impact on User Experience from Security Solutions



Webinar: Eliminating Negative Impact on User Experience from Security SolutionsUL Transaction Security
╠²
In this session, you will hear security experts from SECDUE talk about reducing a negative impact on user experience from traditional security solutions. You will also learn about emerging technologies that enable you to protect financial, PII, and other sensitive information inside and outside of SAP, while eliminating a negative productivity impact. Learn how you can gain a 360┬░ control by extending roles and authorization configured in SAP to any documents leaving SAP applications, allowing them to be safely accessed, shared, and stored inside the company and beyond, including mobile and cloud platforms. Find out how you can to track and analyze all download activity from SAP systems, identify sensitive data with intelligent classification, and create intuitive DLP policies to prevent data loss, all with minimal work disruptions.WISekey presentation 



WISekey presentation Creus Moreira Carlos
╠²
WISeKey provides a unique cybersecurity proposition as the only company offering an end-to-end cybersecurity platform for the Internet of Things. It authenticates and secures devices, websites, people and documents through digital identities. The document discusses WISeKey's scalable security offerings, enhanced security solutions, and easy integration of security into IoT platforms and devices. It also outlines threats in the cybersecurity landscape and analyzes WISeKey's competitors and positioning in the market.Portfolio Presentation Ashraf information Technologies 2020 



Portfolio Presentation Ashraf information Technologies 2020 Ashraf - AIT (Ashraf Information Technologies)
╠²
Ashraf & Co Ltd - Kuwait is one of the most diversified IT solutions provider in Kuwait, with it experience in Information Manageement, AIT has position itself as one of the most preferable partner of choice to the customer. AIT is also one of the pioneer in Digitization projects in Banking Industry providing Software, Hardwares & Human Resource outsourcing as end to end solutions provider. GoSecure



GoSecureNitesh Kulkarni
╠²
The Project to provide Security Solutions for MTA New York City Subway System. The ultimate goal is to drastically reduce storage cost for the New York Subway System and to achieve incremental profits for our parent company.Company Profile



Company ProfileITB001
╠²
IT Become One is an international ICT supplier based in the Netherlands that provides hardware, software, and consulting services. Their ambition is to become one of the top 20 ICT companies in the EMEA region by 2020. They have a flat organizational structure and strive to improve and simplify IT for their customers. Their main industries served include business, government, healthcare, education, and banking.Presentazione Wildix Convention 2015



Presentazione Wildix Convention 2015Wildix
╠²
The document discusses Wildix's performance and plans for 2015. Wildix saw significant growth in 2014, especially in France and Germany. However, the Italian economy is slowing. To address issues like long sales cycles and not enough leads, Wildix plans to implement permission marketing strategies using tools like Infusionsoft and generate more local leads. Technically, Wildix will release new phone models like the WP600A with a large touchscreen and new call continuity features across devices. Wildix also aims to expand its cloud offering to provide all features with improved security, stability, flexibility and global coverage.OptiCom Company Presentation



OptiCom Company PresentationVladimir PAVLENKO
╠²
OptiCom is a leading IT company in Latvia established in 1994 with over 33 professionals. It focuses on providing IT solutions and services to large and medium enterprises. OptiCom hosts the Latvian Networking School twice a year, which brings together 120 IT professionals to learn about the latest IT developments from 10 producer companies. OptiCom is an authorized partner or distributor of many major IT brands and provides a wide range of servers, storage, security, networking, and other solutions.Deploying FIDO Authentication - Business Considerations



Deploying FIDO Authentication - Business ConsiderationsFIDO Alliance
╠²
The document discusses modern authentication and Nok Nok Labs' role in pioneering this area. It notes that Nok Nok Labs invented modern authentication, founded and led the FIDO Alliance, and has deployed authentication solutions for major markets. The document promotes the benefits of leveraging modern authentication, such as improved customer experience, higher retention and satisfaction, and reduced fraud and costs. It argues that authentication, security, and privacy will be vital for society with the rise of cloud services, IoT, and other technologies.Scc soft token datasheet



Scc soft token datasheetHai Nguyen
╠²
The SecurAccess Two Factor Authentication solution provides strong, affordable, and convenient authentication without tokens or additional devices. It transforms any mobile phone into an authentication token by sending one-time passcodes via SMS. This eliminates hardware costs while providing enhanced security. The solution can be deployed on-premise or as a fully managed hosted service to maximize efficiencies and reduce costs.Dictao Company Brochure



Dictao Company BrochureDictao
╠²
An exceptional trust platform
- A comprehensive, full feature platform
- A high quality, internationally recognized offering
- A multi-sector experience
- A pragmatic vision of the future
- A team of experts at your serviceUX Webinar Series: Aligning Authentication Experiences with Business Goals



UX Webinar Series: Aligning Authentication Experiences with Business GoalsFIDO Alliance
╠²
UX Webinar Series: Aligning Authentication Experiences with Business GoalsOptix company profile



Optix company profileOlufolahan Sogbesan
╠²
Optix Limited is an ICT services and systems integration company founded in 2013 that provides solutions to clients across various sectors. The company's vision is to deliver innovative, robust, and efficient ICT solutions at competitive prices. Optix's mission is to be a leading ICT integration and building services company within the decade by offering reliable and scalable solutions. The company offers network infrastructure services, managed services and outsourcing, hardware and storage solutions, physical security and device monitoring, environmental monitoring, data security solutions, and enterprise unified communication solutions through global partnerships. The management team includes Fola Sogbesan as MD/CEO and Dare Olawoye as Solution Manager.Fujitsu & M2SYS Webinar - How Palm Vein Biometrics Can Strengthen PCI and Wor...



Fujitsu & M2SYS Webinar - How Palm Vein Biometrics Can Strengthen PCI and Wor...M2SYS Technology
╠²
This document discusses how palm vein biometric technology from Fujitsu and M2SYS can help strengthen compliance for PCI and workforce management. It outlines the costs of non-compliance for PCI and explains how palm vein biometrics can help by enabling stronger user validation and access controls. It also discusses the costs of non-compliance for workforce management regulations and how palm vein biometrics can help by preventing time theft and providing an audit trail. Representatives from Fujitsu and M2SYS then provide contact information for more details on their palm vein biometric solutions.Video Security Goes to the cloud



Video Security Goes to the cloudKingfin Enterprises Limited
╠²
Hosted video solutions store video data with a third party provider over the internet rather than onsite. This eliminates the need for companies to purchase, maintain and manage their own video storage equipment. Hosted video provides benefits such as lower costs, higher security, simple plug-and-play installation, and the ability to access video remotely from any internet connection. It is well suited for businesses that lack large IT budgets and staff but have security monitoring needs.Move your customer authentication to the next level!



Move your customer authentication to the next level!Ivona M
╠²
In this presentation you will learn:
-Industry best practices in ensuring the highest security and improved user experience.
-How to prevent fraud with advanced SCA techniques.
-Solving operational issues and optimizing costs with the all-in-one authentication system.
-Real examples of practical steps to ensure seamless UX.
-How to enhance your existing VPN security for remote work.
-From OTP to push and biometry ŌĆō which authentication method is the best fit for your business needs.ŌĆ»
For more info go to https://sxs.asseco.com/ FIDO Munich Seminar: FIDO Tech Principles.pptx



FIDO Munich Seminar: FIDO Tech Principles.pptxFIDO Alliance
╠²
FIDO Munich Seminar: FIDO Tech Principles.pptxFIDO Munich Seminar: Securing Smart Car.pptx



FIDO Munich Seminar: Securing Smart Car.pptxFIDO Alliance
╠²
FIDO Munich Seminar: Securing Smart Car.pptxMore Related Content
Similar to FIDO Munich Seminar Workforce Authentication Case Study.pptx (20)
Hardening as a Part of a holistic Security Strategy (UPDATE)



Hardening as a Part of a holistic Security Strategy (UPDATE)NoCodeHardening
╠²
Why are IT Forensic and System Hardening so important for your company? How can you significantly increase the level of your IT Security? This presentation gives you the answers.Black Box India_Corporate_Deck_May23-║▌║▌▀Żshare.pdf



Black Box India_Corporate_Deck_May23-║▌║▌▀Żshare.pdfBlack Box
╠²
Black Box® is a trusted IT solutions provider delivering cutting-edge technology solutions and world-class consulting services to businesses around the globe. The breadth of our global reach and the depth of our expertise accelerate customer success by bringing people, ideas, and technology together to solve real-world business problems. Our IT infrastructure solutions, services, and products enable secure, flawless connectivity and meaningful collaboration for businesses in every major market sector on six continents.
For more information please visit - https://www.blackbox.com/en-us/discover-bb/about-blackbox Smart Cards & Devices Forum 2013 - Protecting enterprise sensitive informatio...



Smart Cards & Devices Forum 2013 - Protecting enterprise sensitive informatio...OKsystem
╠²
This document introduces Gemalto and their solution called Armored Office. It discusses how static passwords are no longer enough for security and compliance with regulations. Armored Office provides a solution for strong authentication and encryption to securely access networks and data from any device. It offers a single credential to log in to endpoints, access networks remotely, and encrypt files/emails. The target market is security-sensitive organizations for executives and users with access to sensitive information. It aims to protect data and enable secure access from any device while meeting compliance requirements.Webinar: Eliminating Negative Impact on User Experience from Security Solutions



Webinar: Eliminating Negative Impact on User Experience from Security SolutionsUL Transaction Security
╠²
In this session, you will hear security experts from SECDUE talk about reducing a negative impact on user experience from traditional security solutions. You will also learn about emerging technologies that enable you to protect financial, PII, and other sensitive information inside and outside of SAP, while eliminating a negative productivity impact. Learn how you can gain a 360┬░ control by extending roles and authorization configured in SAP to any documents leaving SAP applications, allowing them to be safely accessed, shared, and stored inside the company and beyond, including mobile and cloud platforms. Find out how you can to track and analyze all download activity from SAP systems, identify sensitive data with intelligent classification, and create intuitive DLP policies to prevent data loss, all with minimal work disruptions.WISekey presentation 



WISekey presentation Creus Moreira Carlos
╠²
WISeKey provides a unique cybersecurity proposition as the only company offering an end-to-end cybersecurity platform for the Internet of Things. It authenticates and secures devices, websites, people and documents through digital identities. The document discusses WISeKey's scalable security offerings, enhanced security solutions, and easy integration of security into IoT platforms and devices. It also outlines threats in the cybersecurity landscape and analyzes WISeKey's competitors and positioning in the market.Portfolio Presentation Ashraf information Technologies 2020 



Portfolio Presentation Ashraf information Technologies 2020 Ashraf - AIT (Ashraf Information Technologies)
╠²
Ashraf & Co Ltd - Kuwait is one of the most diversified IT solutions provider in Kuwait, with it experience in Information Manageement, AIT has position itself as one of the most preferable partner of choice to the customer. AIT is also one of the pioneer in Digitization projects in Banking Industry providing Software, Hardwares & Human Resource outsourcing as end to end solutions provider. GoSecure



GoSecureNitesh Kulkarni
╠²
The Project to provide Security Solutions for MTA New York City Subway System. The ultimate goal is to drastically reduce storage cost for the New York Subway System and to achieve incremental profits for our parent company.Company Profile



Company ProfileITB001
╠²
IT Become One is an international ICT supplier based in the Netherlands that provides hardware, software, and consulting services. Their ambition is to become one of the top 20 ICT companies in the EMEA region by 2020. They have a flat organizational structure and strive to improve and simplify IT for their customers. Their main industries served include business, government, healthcare, education, and banking.Presentazione Wildix Convention 2015



Presentazione Wildix Convention 2015Wildix
╠²
The document discusses Wildix's performance and plans for 2015. Wildix saw significant growth in 2014, especially in France and Germany. However, the Italian economy is slowing. To address issues like long sales cycles and not enough leads, Wildix plans to implement permission marketing strategies using tools like Infusionsoft and generate more local leads. Technically, Wildix will release new phone models like the WP600A with a large touchscreen and new call continuity features across devices. Wildix also aims to expand its cloud offering to provide all features with improved security, stability, flexibility and global coverage.OptiCom Company Presentation



OptiCom Company PresentationVladimir PAVLENKO
╠²
OptiCom is a leading IT company in Latvia established in 1994 with over 33 professionals. It focuses on providing IT solutions and services to large and medium enterprises. OptiCom hosts the Latvian Networking School twice a year, which brings together 120 IT professionals to learn about the latest IT developments from 10 producer companies. OptiCom is an authorized partner or distributor of many major IT brands and provides a wide range of servers, storage, security, networking, and other solutions.Deploying FIDO Authentication - Business Considerations



Deploying FIDO Authentication - Business ConsiderationsFIDO Alliance
╠²
The document discusses modern authentication and Nok Nok Labs' role in pioneering this area. It notes that Nok Nok Labs invented modern authentication, founded and led the FIDO Alliance, and has deployed authentication solutions for major markets. The document promotes the benefits of leveraging modern authentication, such as improved customer experience, higher retention and satisfaction, and reduced fraud and costs. It argues that authentication, security, and privacy will be vital for society with the rise of cloud services, IoT, and other technologies.Scc soft token datasheet



Scc soft token datasheetHai Nguyen
╠²
The SecurAccess Two Factor Authentication solution provides strong, affordable, and convenient authentication without tokens or additional devices. It transforms any mobile phone into an authentication token by sending one-time passcodes via SMS. This eliminates hardware costs while providing enhanced security. The solution can be deployed on-premise or as a fully managed hosted service to maximize efficiencies and reduce costs.Dictao Company Brochure



Dictao Company BrochureDictao
╠²
An exceptional trust platform
- A comprehensive, full feature platform
- A high quality, internationally recognized offering
- A multi-sector experience
- A pragmatic vision of the future
- A team of experts at your serviceUX Webinar Series: Aligning Authentication Experiences with Business Goals



UX Webinar Series: Aligning Authentication Experiences with Business GoalsFIDO Alliance
╠²
UX Webinar Series: Aligning Authentication Experiences with Business GoalsOptix company profile



Optix company profileOlufolahan Sogbesan
╠²
Optix Limited is an ICT services and systems integration company founded in 2013 that provides solutions to clients across various sectors. The company's vision is to deliver innovative, robust, and efficient ICT solutions at competitive prices. Optix's mission is to be a leading ICT integration and building services company within the decade by offering reliable and scalable solutions. The company offers network infrastructure services, managed services and outsourcing, hardware and storage solutions, physical security and device monitoring, environmental monitoring, data security solutions, and enterprise unified communication solutions through global partnerships. The management team includes Fola Sogbesan as MD/CEO and Dare Olawoye as Solution Manager.Fujitsu & M2SYS Webinar - How Palm Vein Biometrics Can Strengthen PCI and Wor...



Fujitsu & M2SYS Webinar - How Palm Vein Biometrics Can Strengthen PCI and Wor...M2SYS Technology
╠²
This document discusses how palm vein biometric technology from Fujitsu and M2SYS can help strengthen compliance for PCI and workforce management. It outlines the costs of non-compliance for PCI and explains how palm vein biometrics can help by enabling stronger user validation and access controls. It also discusses the costs of non-compliance for workforce management regulations and how palm vein biometrics can help by preventing time theft and providing an audit trail. Representatives from Fujitsu and M2SYS then provide contact information for more details on their palm vein biometric solutions.Video Security Goes to the cloud



Video Security Goes to the cloudKingfin Enterprises Limited
╠²
Hosted video solutions store video data with a third party provider over the internet rather than onsite. This eliminates the need for companies to purchase, maintain and manage their own video storage equipment. Hosted video provides benefits such as lower costs, higher security, simple plug-and-play installation, and the ability to access video remotely from any internet connection. It is well suited for businesses that lack large IT budgets and staff but have security monitoring needs.Move your customer authentication to the next level!



Move your customer authentication to the next level!Ivona M
╠²
In this presentation you will learn:
-Industry best practices in ensuring the highest security and improved user experience.
-How to prevent fraud with advanced SCA techniques.
-Solving operational issues and optimizing costs with the all-in-one authentication system.
-Real examples of practical steps to ensure seamless UX.
-How to enhance your existing VPN security for remote work.
-From OTP to push and biometry ŌĆō which authentication method is the best fit for your business needs.ŌĆ»
For more info go to https://sxs.asseco.com/ Webinar: Eliminating Negative Impact on User Experience from Security Solutions



Webinar: Eliminating Negative Impact on User Experience from Security SolutionsUL Transaction Security
╠²
Portfolio Presentation Ashraf information Technologies 2020 



Portfolio Presentation Ashraf information Technologies 2020 Ashraf - AIT (Ashraf Information Technologies)
╠²
More from FIDO Alliance (20)
FIDO Munich Seminar: FIDO Tech Principles.pptx



FIDO Munich Seminar: FIDO Tech Principles.pptxFIDO Alliance
╠²
FIDO Munich Seminar: FIDO Tech Principles.pptxFIDO Munich Seminar: Securing Smart Car.pptx



FIDO Munich Seminar: Securing Smart Car.pptxFIDO Alliance
╠²
FIDO Munich Seminar: Securing Smart Car.pptxFIDO Munich Seminar: Strong Workforce Authn Push & Pull Factors.pptx



FIDO Munich Seminar: Strong Workforce Authn Push & Pull Factors.pptxFIDO Alliance
╠²
FIDO Munich Seminar: Strong Workforce Authn Push & Pull Factors.pptxFIDO Munich Seminar: Biometrics and Passkeys for In-Vehicle Apps.pptx



FIDO Munich Seminar: Biometrics and Passkeys for In-Vehicle Apps.pptxFIDO Alliance
╠²
FIDO Munich Seminar: Biometrics and Passkeys for In-Vehicle Apps.pptxFIDO Munich Seminar In-Vehicle Payment Trends.pptx



FIDO Munich Seminar In-Vehicle Payment Trends.pptxFIDO Alliance
╠²
FIDO Munich Seminar In-Vehicle Payment Trends.pptxFIDO Munich Seminar Blueprint for In-Vehicle Payment Standard.pptx



FIDO Munich Seminar Blueprint for In-Vehicle Payment Standard.pptxFIDO Alliance
╠²
FIDO Munich Seminar Blueprint for In-Vehicle Payment Standard.pptxFIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf



FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdfFIDO Alliance
╠²
FIDO Alliance Osaka SeminarFIDO Alliance Osaka Seminar: LY-DOCOMO-KDDI-Mercari Panel.pdf



FIDO Alliance Osaka Seminar: LY-DOCOMO-KDDI-Mercari Panel.pdfFIDO Alliance
╠²
FIDO Alliance Osaka SeminarFIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf



FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdfFIDO Alliance
╠²
FIDO Alliance Osaka SeminarFIDO Alliance Osaka Seminar: PlayStation Passkey Deployment Case Study.pdf



FIDO Alliance Osaka Seminar: PlayStation Passkey Deployment Case Study.pdfFIDO Alliance
╠²
FIDO Alliance Osaka SeminarFDO for Camera, Sensor and Networking Device ŌĆō Commercial Solutions from VinC...



FDO for Camera, Sensor and Networking Device ŌĆō Commercial Solutions from VinC...FIDO Alliance
╠²
FIDO Taipei Workshop: Securing the Edge with FDOASRock Industrial FDO Solutions in Action for Industrial Edge AI _ Kenny at A...



ASRock Industrial FDO Solutions in Action for Industrial Edge AI _ Kenny at A...FIDO Alliance
╠²
FIDO Taipei Workshop: Securing the Edge with FDOHow Red Hat Uses FDO in Device Lifecycle _ Costin and Vitaliy at Red Hat.pdf



How Red Hat Uses FDO in Device Lifecycle _ Costin and Vitaliy at Red Hat.pdfFIDO Alliance
╠²
FIDO Taipei Workshop: Securing the Edge with FDOSecure Zero Touch enabled Edge compute with Dell NativeEdge via FDO _ Brad at...



Secure Zero Touch enabled Edge compute with Dell NativeEdge via FDO _ Brad at...FIDO Alliance
╠²
FIDO Taipei Workshop: Securing the Edge with FDORecently uploaded (20)
Revolutionizing Field Service: How LLMs Are Powering Smarter Knowledge Access...



Revolutionizing Field Service: How LLMs Are Powering Smarter Knowledge Access...Earley Information Science
╠²
Revolutionizing Field Service with LLM-Powered Knowledge Management
Field service technicians need instant access to accurate repair information, but outdated knowledge systems often create frustrating delays. Large Language Models (LLMs) are changing the gameŌĆöenhancing knowledge retrieval, streamlining troubleshooting, and reducing technician dependency on senior staff.
In this webinar, Seth Earley and industry experts Sanjay Mehta, and Heather Eisenbraun explore how LLMs and Retrieval-Augmented Generation (RAG) are transforming field service operations. Discover how AI-powered knowledge management is improving efficiency, reducing downtime, and elevating service quality.
LLMs for Instant Knowledge Retrieval ŌĆō How AI-driven search dramatically cuts troubleshooting time.
Structured Data & AI ŌĆō Why high-quality, organized knowledge is essential for LLM success.
Real-World Implementation ŌĆō Lessons from deploying LLM-powered knowledge tools in field service.
Business Impact ŌĆō How AI reduces service delays, optimizes workflows, and enhances technician productivity.
Empower your field service teams with AI-driven knowledge access. Watch the webinar to see how LLMs are revolutionizing service efficiency.Artificial Intelligence Quick Research Guide by Arthur Morgan



Artificial Intelligence Quick Research Guide by Arthur MorganArthur Morgan
╠²
This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG (coming 2025)
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at art_morgan@att.net.
100% human made.Build with AI on Google Cloud Session #3



Build with AI on Google Cloud Session #3Margaret Maynard-Reid
╠²
This is session #3 of the 5-session online study series with Google Cloud, where we take you onto the journey learning generative AI. YouŌĆÖll explore the dynamic landscape of Generative AI, gaining both theoretical insights and practical know-how of Google Cloud GenAI tools such as Gemini, Vertex AI, AI agents and Imagen 3. Combining Lexical and Semantic Search with Milvus 2.5



Combining Lexical and Semantic Search with Milvus 2.5Zilliz
╠²
In short, lexical search is a way to search your documents based on the keywords they contain, in contrast to semantic search, which compares the similarity of embeddings. WeŌĆÖll be covering:
ŌĆŗWhy, when, and how should you use lexical search
ŌĆŗWhat is the BM25 distance metric
ŌĆŗHow exactly does Milvus 2.5 implement lexical search
ŌĆŗHow to build an improved hybrid lexical + semantic search with Milvus 2.516 KALALU¤Ģē’ĖŤÅ椬ō¤¬ł¤Å╣¤ææ¤ææ¤ææ¤ææ¤ææ¤ż┤¤”ü¤Æ┐Ō£ł’ĖŤøĖ¤ÜƤ¬®¤źÅ¤Źź APARAMAHASAHASRA SIMHAMAHANKALKIADIPARASAKTIBH...



16 KALALU¤Ģē’ĖŤÅ椬ō¤¬ł¤Å╣¤ææ¤ææ¤ææ¤ææ¤ææ¤ż┤¤”ü¤Æ┐Ō£ł’ĖŤøĖ¤ÜƤ¬®¤źÅ¤Źź APARAMAHASAHASRA SIMHAMAHANKALKIADIPARASAKTIBH...IT Industry
╠²
¤Ģē’ĖŤĢ║¤īĤīī¤”Ė¤ææ¤ææ¤ææ¤ææ¤ææ¤ż┤¤ÆؤÄē¤ÅåŌ£ł’ĖŤøĖ¤ÜƤ¬®¤źÅ¤Æ┐¤Źź¤Å╣¤¬ł¤¬ō¤Åć BHAGWAN SRI RAMA SIMHA OMKARAM SRI SRI KING VISNU KALKI SRI KRISNA PARAMATMA SRI SRI KING VISNU SARAT KRISNA PARAMATMA SRI SRI KING ADISIMHA APARAMAHASAHASRA SAHASRASAMASTA SAHASRA SAMASTA APARAMAHASAHASRA BHARGAVA SIMHA TRINETRA APARAMAHASAHASRA SIMHAMAHANKALI ADIPARASAKTI KVADIPARASAKTI ANEKASAHASRA MAHA INFINITY SIMHA SAHASRA AVATARAMULU SRI SRI KING VISNU SUPREME GODS HEADS KING VISNU SUPREME ALFAONKA SAHASRA SAMASTA APARAMAHASAHASRA BHARGAVA SIMHA TRINETRA APARAMAHASAHASRA SIMHAMAHANKALI ADIPARASAKTI KVADIPARASAKTI VAARE SRI SRI KING VISNU KAVERI VEERA BHARAT BHUSHAN MR.KALKIKINGSUPREMEGODSHEADS MEGA KALKI ROBO ALIENS KING SUPREME GODS HEADS KING ALFA SUPREMO 16 KALALU !! ¤¬ō¤Å椬ł¤Å╣¤Źź¤Æ┐¤źÅ¤¬®¤ÜƤøĖŌ£ł’ĖŤÅå¤Äē¤Æؤż┤¤ææ¤ææ¤ææ¤ææ¤æ椔Ė¤Ģ║¤īī¤īĤĢē’ĖÅSB7 Mobile Ltd: Simplified & Secure Services



SB7 Mobile Ltd: Simplified & Secure ServicesReuben Jasper
╠²
SB7 Mobile Ltd is enhancing customer experience by improving support accessibility, billing transparency, and security. The company has strengthened payment authorization, simplified unsubscription, and expanded customer service channels to address common concerns.Understanding & Utilizing SharePoint Advanced Management



Understanding & Utilizing SharePoint Advanced ManagementDrew Madelung
╠²
Drew Madelung is a Cloud Solutions Architect and a Microsoft MVP for Office Apps and Services. He helps organizations realize what is possible with Microsoft 365 & Azure, onboard them in a secure and compliant way, and drive sustained adoption for those solutions. He is experienced in a range of technologies but specializes in the collaboration and teamwork workspaces such as Microsoft Teams, SharePoint, and OneDrive. He has helped deploy Microsoft 365 to multiple global companies while rolling out modern information protection and information governance technologies. He has been doing Microsoft consulting for 10+ years with a strength in security & compliance solutions.Not a Kubernetes fan? The state of PaaS in 2025



Not a Kubernetes fan? The state of PaaS in 2025Anthony Dahanne
╠²
Kubernetes won the containers orchestration war. But has it made deploying your apps easier?
Let's explore some of Kubernetes extensive app developer tooling, but mainly what the PaaS space looks like in 2025; 18 years after Heroku made it popular.
Is Heroku still around? What about Cloud Foundry?
And what are those new comers (fly.io, railway, porter.sh, etc.) worth?
Did the Cloud giants replace them all?William Maclyn Murphy McRae - A Seasoned Professional Renowned



William Maclyn Murphy McRae - A Seasoned Professional RenownedWilliam Maclyn Murphy McRae
╠²
William Maclyn Murphy McRae, a logistics expert with 9+ years of experience, is known for optimizing supply chain operations and consistently exceeding industry standards. His strategic approach, combined with hands-on execution, has streamlined distribution processes, reduced lead times, and consistently delivered exceptional results.THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIA



THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIASrivaanchi Nathan
╠²
This business intelligence report, "The Big Ten Biopharmaceutical MNCs: Global Capability Centers in India", provides an in-depth analysis of the operations and contributions of the Global Capability Centers (GCCs) of ten leading biopharmaceutical multinational corporations in India. The report covers AstraZeneca, Bayer, Bristol Myers Squibb, GlaxoSmithKline (GSK), Novartis, Sanofi, Roche, Pfizer, Novo Nordisk, and Eli Lilly. In this report each company's GCC is profiled with details on location, workforce size, investment, and the strategic roles these centers play in global business operations, research and development, and information technology and digital innovation.UiPath Automation Developer Associate Training Series 2025 - Session 1



UiPath Automation Developer Associate Training Series 2025 - Session 1DianaGray10
╠²
Welcome to UiPath Automation Developer Associate Training Series 2025 - Session 1.
In this session, we will cover the following topics:
Introduction to RPA & UiPath Studio
Overview of RPA and its applications
Introduction to UiPath Studio
Variables & Data Types
Control Flows
You are requested to finish the following self-paced training for this session:
Variables, Constants and Arguments in Studio 2 modules - 1h 30m - https://academy.uipath.com/courses/variables-constants-and-arguments-in-studio
Control Flow in Studio 2 modules - 2h 15m - https:/academy.uipath.com/courses/control-flow-in-studio
Ōüē’ĖÅ For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. Transcript: AI in publishing: Your questions answered - Tech Forum 2025



Transcript: AI in publishing: Your questions answered - Tech Forum 2025BookNet Canada
╠²
George Walkley, a publishing veteran and leading authority on AI applications, joins us for a follow-up to his presentation "Applying AI to publishing: A balanced and ethical approach". George gives a brief overview of developments since that presentation and answers attendees' pressing questions about AIŌĆÖs impact and potential applications in the book industry.
Link to recording and presentation slides: https://bnctechforum.ca/sessions/ai-in-publishing-your-questions-answered/
Presented by BookNet Canada on February 20, 2025 with support from the Department of Canadian Heritage.Mastering ChatGPT & LLMs for Practical Applications: Tips, Tricks, and Use Cases



Mastering ChatGPT & LLMs for Practical Applications: Tips, Tricks, and Use CasesSanjay Willie
╠²
Our latest session with Astiostech covered how to unlock the full potential of ChatGPT and LLMs for real-world use!
Ō£ģ Key Takeaways:
¤ö╣ Effective Prompting: Crafting context-specific, high-quality prompts for optimal AI responses.
¤ö╣ Advanced ChatGPT Features: Managing system prompts, conversation memory, and file uploads.
¤ö╣ Optimizing AI Outputs: Refining responses, handling large texts, and knowing when fine-tuning is needed.
¤ö╣ Competitive Insights: Exploring how ChatGPT compares with other AI tools.
¤ö╣ Business & Content Use Cases: From summarization to SEO, sales, and audience targeting.
¤ÆĪ The session provided hands-on strategies to make AI a powerful tool for content creation, decision-making, and business growth.
¤ÜĆ Are you using AI effectively in your workflow? LetŌĆÖs discuss how it can improve efficiency and creativity!
#AI #ChatGPT #PromptEngineering #ArtificialIntelligence #LLM #Productivity #Astiostech5 Must-Use AI Tools to Supercharge Your Productivity



5 Must-Use AI Tools to Supercharge Your Productivitycryptouniversityoffi
╠²
5 Must-Use AI Tools to Supercharge Your Productivity!
AI is changing the game! ¤ÜĆ From research to creativity and coding, here are 5 powerful AI tools you should try.
NotebookLM
¤ōÜ NotebookLM ŌĆō Your AI Research Assistant
Ō£ģ Organizes & summarizes notes
Ō£ģ Generates insights from multiple sources
Ō£ģ Ideal for students, researchers & writers
¤ōØ Boost your productivity with smarter note-taking!
Napkin.ai
¤Ä© Napkin.ai ŌĆō The Creativity Booster
Ō£ģ Connects and organizes ideas
Ō£ģ Perfect for writers, designers & entrepreneurs
Ō£ģ Acts as your AI-powered brainstorming partner
¤ÆĪ Unleash your creativity effortlessly!
DeepSeek
¤öŹ DeepSeek ŌĆō Smarter AI Search
Ō£ģ Delivers deeper & more precise search results
Ō£ģ Analyzes large datasets for better insights
Ō£ģ Ideal for professionals & researchers
¤öÄ Find what you needŌĆöfaster & smarter!
ChatGPT
¤Æ¼ ChatGPT ŌĆō Your AI Chat Assistant
Ō£ģ Answers questions, writes content & assists in coding
Ō£ģ Helps businesses with customer support
Ō£ģ Boosts learning & productivity
¤ż¢ From content to codingŌĆöChatGPT does it all!
Devin AI
¤Æ╗ Devin AI ŌĆō AI for Coders
Ō£ģ Writes, debugs & optimizes code
Ō£ģ Assists developers at all skill levels
Ō£ģ Makes coding faster & more efficient
¤æ©ŌĆŹ¤Æ╗ Let AI be your coding partner!
¤ÜĆ AI is transforming the way we work!Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan
╠²
This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG (coming 2025)
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at art_morgan@att.net.
100% human made.UiPath Automation Developer Associate Training Series 2025 - Session 1



UiPath Automation Developer Associate Training Series 2025 - Session 1DianaGray10
╠²
Welcome to UiPath Automation Developer Associate Training Series 2025 - Session 1.
In this session, we will cover the following topics:
Introduction to RPA & UiPath Studio
Overview of RPA and its applications
Introduction to UiPath Studio
Variables & Data Types
Control Flows
You are requested to finish the following self-paced training for this session:
Variables, Constants and Arguments in Studio 2 modules - 1h 30m - https://academy.uipath.com/courses/variables-constants-and-arguments-in-studio
Control Flow in Studio 2 modules - 2h 15m - https:/academy.uipath.com/courses/control-flow-in-studio
Ōüē’ĖÅ For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. Data-Driven Public Safety: Reliable Data When Every Second Counts



Data-Driven Public Safety: Reliable Data When Every Second CountsSafe Software
╠²
When every second counts, you need access to data you can trust. In this webinar, weŌĆÖll explore how FME empowers public safety services to streamline their operations and safeguard communities. This session will showcase workflow examples that public safety teams leverage every day.
WeŌĆÖll cover real-world use cases and demo workflows, including:
Automating Police Traffic Stop Compliance: Learn how the City of Fremont meets traffic stop data standards by automating QA/QC processes, generating error reports ŌĆō saving over 2,800 hours annually on manual tasks.
Anonymizing Crime Data: Discover how cities protect citizen privacy while enabling transparent and trustworthy open data sharing.
Next Gen 9-1-1 Integration: Explore how Santa Clara County supports the transition to digital emergency response systems for faster, more accurate dispatching, including automated schema mapping for address standardization.
Extreme Heat Alerts: See how FME supports disaster risk management by automating the delivery of extreme heat alerts for proactive emergency response.
Our goal is to provide practical workflows and actionable steps you can implement right away. Plus, weŌĆÖll provide quick steps to find more information about our public safety subscription for Police, Fire Departments, EMS, HAZMAT teams, and more.
Whether youŌĆÖre in a call center, on the ground, or managing operations, this webinar is crafted to help you leverage data to make informed, timely decisions that matter most.Revolutionizing Field Service: How LLMs Are Powering Smarter Knowledge Access...



Revolutionizing Field Service: How LLMs Are Powering Smarter Knowledge Access...Earley Information Science
╠²
16 KALALU¤Ģē’ĖŤÅ椬ō¤¬ł¤Å╣¤ææ¤ææ¤ææ¤ææ¤ææ¤ż┤¤”ü¤Æ┐Ō£ł’ĖŤøĖ¤ÜƤ¬®¤źÅ¤Źź APARAMAHASAHASRA SIMHAMAHANKALKIADIPARASAKTIBH...



16 KALALU¤Ģē’ĖŤÅ椬ō¤¬ł¤Å╣¤ææ¤ææ¤ææ¤ææ¤ææ¤ż┤¤”ü¤Æ┐Ō£ł’ĖŤøĖ¤ÜƤ¬®¤źÅ¤Źź APARAMAHASAHASRA SIMHAMAHANKALKIADIPARASAKTIBH...IT Industry
╠²
FIDO Munich Seminar Workforce Authentication Case Study.pptx
- 1. Workforce Authentication Case Study Overcoming the hurdles on the way to a passwordless futureŌĆ”. July 2024 Malte Kahrs CEO and Founder of MTRIX GmbH
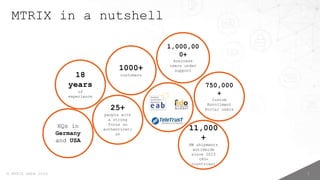
- 2. 1 ┬® MTRIX GmbH 2024 MTRIX in a nutshell 18 years of experience HQs in Germany and USA 25+ people with a strong focus on authenticati on 1,000,00 0+ business users under support 750,000 + Custom Enrollment Portal users 11,000 + HW shipments worldwide since 2023 (80+ countries) 1000+ customers
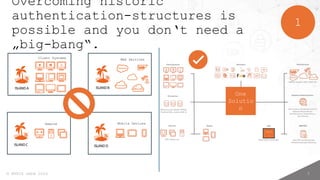
- 3. 2 ┬® MTRIX GmbH 2024 Enterprises often fail due to the same challenges. Overcome current ŌĆ£islandŌĆØ solutions ’é¦ Historically grown isolated solutions ’é¦ Not all solutions support FIDO as a modern authentication method 1 The ŌĆ×last mileŌĆ£ FIDO-Key-Delivery ’é¦ An (integrated) FIDO authenticator cannot be used in every situation ’é¦ Hardware FIDO keys are often required and desired 2 Ensuring the best user experience ’é¦ Users must be able to complete an enroll-ment independently ’é¦ Without acceptance, support costs explode, security shrinks 3
- 4. 3 ┬® MTRIX GmbH 2024 1 Client Systems Remote Mobile Devices Web Services ISLANDA ISLANDB ISLANDC ISLANDD One Solutio n Incl . Overcoming historic authentication-structures is possible and you donŌĆśt need a ŌĆ×big-bangŌĆ£.
- 5. 4 ┬® MTRIX GmbH 2024 Solving the ŌĆ£last mileŌĆ£ is critical to distribute FIDO hardware 2 Logistics ’é¦ Simply sending all FIDO Keys to customers HQ will not solve the challenge for him. ’é¦ You have to make sure that every person can order sufficient FIDO-key(s) to his / her place ’é¦ Ordering must be easy for the user Global shipment ’é¦ It shouldn't make any difference whether the FIDO-key goes to the north, east, south or west of the world -> deliver keys to wherever the user is (Customs and Tariffs) ’é¦ Ship from the US or Europe directly to your user to reduce delivery times ’é¦ Whenever you ship something: Make it trackable Services suggestions ’é¦ Appoint a project manager as SPOC ’é¦ Consider custom configuration of FIDO Keys (attestation, Applets, Seeds) ’é¦ If something goes wrong: someone has to take care of it (proactively) and make sure the FIDO-key(s) will arrive
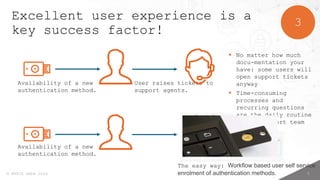
- 6. 5 ┬® MTRIX GmbH 2024 3 Excellent user experience is a key success factor! Availability of a new authentication method. Availability of a new authentication method. User raises tickets to support agents. ’é¦ No matter how much docu-mentation your have: some users will open support tickets anyway ’é¦ Time-consuming processes and recurring questions are the daily routine of the support team The easy way: Workflow based user self service enrolment of authentication methods.
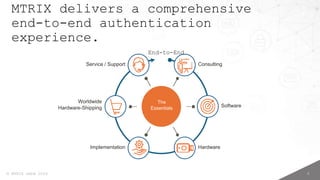
- 7. 6 ┬® MTRIX GmbH 2024 MTRIX delivers a comprehensive end-to-end authentication experience. The Essentials Service / Support Consulting Software Hardware Implementation Worldwide Hardware-Shipping End-to-End
- 8. 7 ┬® MTRIX GmbH 2024 Many thanks for your attention ’é¦ There are no (longer) technical reasons not to introduce FIDO as the desired standard for all authentication processes. ’é¦ The introduction of a central platform supports these efforts. ’é¦ Don't just solve the technology, letŌĆśs talk about how the FIDO technology will reach and impact the user. ’é¦ Key success factors are (web-)portals for the independent enrollment and management of (FIDO) authentication methods by every single user ’é¦ Let the user decide which (FIDO) method works best for him in which situation.
Editor's Notes
- #7: Click ŌĆō 1 ŌĆō show Serial Number Click ŌĆō 2 ŌĆō touch the key











