Finite automata and formal language lecture note
- 1. 18.404/6.840 Lecture 21 Last time: - Log-space reducibility - L = NL? question - is NL-complete - is NL-complete - NL = coNL (unfinished) Today: (Sipser ┬¦9.1) - Finish NL = coNL - Time and Space Hierarchy Theorems 1
- 2. Theorem (Immerman-Szelepcs├®nyi): NL = coNL Proof: Show NL Defn: NTM computes function if for all 1) All branches of on halt with on the tape or reject. 2) Some branch of on does not reject. Let Let YES} Let = Reachable nodes = # reachable YES, if has a path from to NO, if not Theorem: If some NL-machine (log-space NTM) computes , then some NL-machine computes . Proof: ŌĆ£On input 1. Let 2. For each node 3. If YES, then 4. If NO, then continue 5. Output ŌĆØ Next: Converse of above ØÉ║ ØæĀ Øæģ ØæÉ=┬┐ØæģŌł©┬┐ NL = coNL (part 1/4) Check-in 21.1 Check-in 21.1 Let be the graph below. What is the value of ? (a) 2 (e) 6 (b) 3 (f) 7 (c) 4 (g) 8 (d) 5 (h) 9 ØæĀ ØÉ║=┬┐ 2
- 3. NL = coNL (part 2/4) ŌĆō key idea Theorem: If some NL-machine computes , then some NL-machine computes . Proof: ŌĆ£On input where has nodes 1. Compute 2. 3. For each node 4. Nondeterministically go to (p) or (n) (p) Nondeterministically pick a path from to of length . If fail, then reject. If , then output YES, else set . (n) Skip and continue. 5. If then reject. 6. Output NO.ŌĆØ [found all reachable nodes and none were } ØÉ║ ØæĀ Øæģ ØæÉ=┬┐ØæģŌł©┬┐ 3
- 4. NL = coNL (part 2/4) ŌĆō key idea SIMPLIFIED!! Theorem: If some NL-machine computes , then some NL-machine computes . Proof: ŌĆ£On input where has nodes 1. Compute 2. 3. For each node 4. Nondeterministically pick a path from of length . If it ends at then output YES and stop. If it ends at , set . 5. If then reject. 6. Output NO.ŌĆØ [found all reachable nodes and none were } ØÉ║ ØæĀ Øæģ ØæÉ=┬┐ØæģŌł©┬┐ 4
- 5. NL = coNL (part 3/4) Theorem: If some NL-machine computes , then some NL-machine computes . Proof: ŌĆ£On input 1. Compute 2. 3. For each node 4. Nondeterministically go to (p) or (n) (p) Nondeterministically pick a path from to of length . If fail, then reject. If , then output YES, else set . (n) Skip and continue. 5. If then reject. 6. Output NOŌĆØ [found all reachable nodes and none were } ØÉ║ ØæĀ ØæģØææ ØæÉØææ=┬┐ØæģØææŌł©┬┐ Let Let YES} Let YES, if has a path to of length NO, if not 5
- 6. NL = coNL (part 4/4) Theorem: If some NL-machine computes , then some NL-machine computes . Proof: ŌĆ£On input 1. Compute 2. 3. For each node 4. Nondeterministically go to (p) or (n) (p) Nondeterministically pick a path from to of length . If fail, then reject. If has an edge to , then output YES, else set . (n) Skip and continue. 5. If then reject. 6. Output NO.ŌĆØ [found all reachable nodes and none had an edge to } ØÉ║ ØæĀ ØæģØææ ØæÉØææ+1=┬┐ ØæģØææ+1Ōł©┬┐ ØæģØææ+ 1 ØæÉØææ=┬┐ØæģØææŌł©┬┐ Corollary: Some NL-machine computes from . Hence NL ŌĆ£On input 1. . 2. Compute each from for to . 3. Accept if = NO. 4. Reject if = YES.ŌĆØ 6
- 7. L NL P NP PSPACE Review: Major Complexity Classes ŌēĀ Today The time and space hierarchy theorems show that if a TM is given more time (or space) then it can do more.* * certain restrictions apply. For example: TIME TIME [ means proper subset ] SPACE SPACE 7
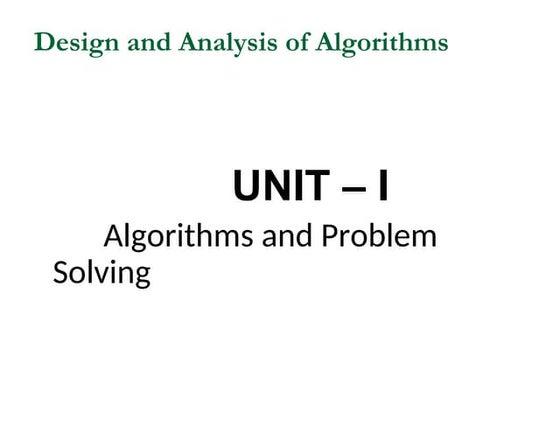
- 8. Space Hierarchy Theorem (1/2) Theorem: For any (where satisfies a technical condition) there is a language where requires space, i.e, 1) is decidable in space, and 2) is not decidable in space On other words, SPACE SPACE Notation: SPACEsome TM decides in space SPACE SPACE ØÉ┤ Proof outline: (Diagonalization) Give TM where 1) runs in space 2) ensures that for every TM that runs in space. Let . 8
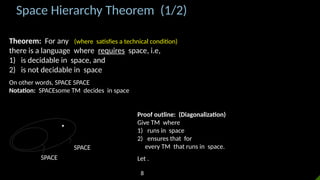
- 9. Goal: Exhibit SPACE but SPACE Give where and 1) runs in space 2) ensures that for every TM that runs in space. ŌĆ£On input 1. Mark off tape cells where . If ever try to use more tape, reject. 2. If for some TM , reject. 3. Simulate* on for steps Accept if rejects, Reject if accepts or hasnŌĆÖt halted.ŌĆØ *Note: can simulate with a constant factor space overhead. Space Hierarchy Theorem (2/2) Issues: 1. What if runs in space but has a big constant? Then wonŌĆÖt have space to simulate when is small. FIX: simulate on infinitely many . 2. What if loops? [ must always halt] FIX: Stop if it runs for steps. 3. How to compute ? FIX: Assume is space constructible, i.e., can compute within space. Nice functions like , , , , , ŌĆ” are all space constructible. Mark off tape Ōŗ» Øæż Ōŗ» # Øæż=010110Ōŗ»10100000 Ōī® ØæĆŌī¬ Øæø Øæō (Øæø) ØÉĘ Hide me ŌåÆ Check-in 21.2 Check-in 21.2 What happens when we run on input ? a) It loops b) It accepts c) It rejects d) We get a contradiction e) Smoke comes out 9
- 10. Time Hierarchy Theorem (1/2) Theorem: For any where is time constructible there is a language where requires time, i.e, 1) is decidable in time, and 2) is not decidable in time On other words, TIME TIME Proof outline: Give TM where 1) runs in time 2) ensures that for every TM that runs in time . Let . 10
- 11. Goal: Exhibit TIME but TIME where 1) runs in time 2) ensures that for every TM that runs in time. ŌĆ£On input 1. Compute . 2. If for some TM , reject. 3. Simulate* on for steps. Accept if rejects, Reject if accepts or hasnŌĆÖt halted.ŌĆØ *Note: can simulate with a log factor time overhead due to the step counter. Time Hierarchy Theorem (2/2) Why do we lose a factor of ? must halt within time. To do so, counts the number of steps it uses and stops if the limit is exceeded. The counter has size and is stored on the tape. It must be kept near the current head location. Cost of moving it adds a overhead factor. So to halt within time, stops when the counter reaches . 11
- 12. L NL P NP PSPACE Recap: Separating Complexity Classes ŌēĀ Space Hierarchy Theorem NL SPACE SPACE PSPACE Check-in 21.3 Check-in 21.3 Consider these two famous unsolved questions: 1. Does L = P? 2. Does P = PSPACE? What do the hierarchy theorems tell us about these questions? a) Nothing b) At least one of these has answer ŌĆ£NOŌĆØ c) At least one of these has answer ŌĆ£YESŌĆØ 12
- 13. Quick review of today 1. Finish NL = coNL 2. Space hierarchy theorem 3. Time hierarchy theorem 13
- 14. MIT OpenCourseWare https://ocw.mit.edu 18.404J Theory of Computation Fall 2020 For information about citing these materials or our Terms of Use, visit: https://ocw.mit.edu/terms.






![L NL P NP PSPACE
Review: Major Complexity Classes
ŌēĀ
Today
The time and space hierarchy theorems show that
if a TM is given more time (or space) then it can do more.*
* certain restrictions apply.
For example:
TIME TIME [ means proper subset ]
SPACE SPACE
7](https://image.slidesharecdn.com/0acb1321504f570d8ac581770f0ac5b5mit18404f20lec21-241026182320-2c467157/85/Finite-automata-and-formal-language-lecture-note-7-320.jpg)
![Goal: Exhibit SPACE but SPACE
Give where and
1) runs in space
2) ensures that
for every TM that runs in space.
ŌĆ£On input
1. Mark off tape cells where .
If ever try to use more tape, reject.
2. If for some TM , reject.
3. Simulate* on for steps
Accept if rejects,
Reject if accepts or hasnŌĆÖt halted.ŌĆØ
*Note: can simulate with a constant factor
space overhead.
Space Hierarchy Theorem (2/2)
Issues:
1. What if runs in space but has
a big constant? Then wonŌĆÖt have space
to simulate when is small.
FIX: simulate on infinitely many .
2. What if loops? [ must always halt]
FIX: Stop if it runs for steps.
3. How to compute ?
FIX: Assume is space constructible,
i.e., can compute within space.
Nice functions like , , , , , ŌĆ”
are all space constructible.
Mark off
tape
Ōŗ» Øæż Ōŗ» #
Øæż=010110Ōŗ»10100000
Ōī® ØæĆŌī¬
Øæø
Øæō (Øæø)
ØÉĘ
Hide me ŌåÆ
Check-in 21.2
Check-in 21.2
What happens when we run on input ?
a) It loops
b) It accepts
c) It rejects
d) We get a contradiction
e) Smoke comes out
9](https://image.slidesharecdn.com/0acb1321504f570d8ac581770f0ac5b5mit18404f20lec21-241026182320-2c467157/85/Finite-automata-and-formal-language-lecture-note-9-320.jpg)















![Shell sort[1]](https://cdn.slidesharecdn.com/ss_thumbnails/shellsort1-131120033842-phpapp02-thumbnail.jpg?width=560&fit=bounds)