Flowcharts
Download as docx, pdf0 likes199 views
Main types of computer memory include read-only memory (ROM), random-access memory (RAM), hard disks, floppy disks, CD-ROMs, and DVDs. Software is divided into system software, like operating systems, language processors, device drivers and utilities, which control internal computer operations, and application software for specific tasks. Common units for measuring memory are the bit, byte, kilobyte, megabyte, gigabyte and terabyte.
1 of 2
Download to read offline
Ad
Recommended
Creating ghost in windows
Creating ghost in windowsbhuruptdr
╠²
The document provides instructions for backing up PCs using Symantec Ghost by creating an image file of the entire hard drive contents. It involves preparing a USB drive with a folder structure to store images, booting from the Ghost CD, and selecting the hard drive and target folder to back up the image, which will contain all files, programs, and data from the PC. The process takes a PC's contents and saves it as a single image file for restoration if needed.Computer Basics
Computer Basicsnhumar
╠²
The document discusses the basic components and functions of a computer system. It describes computers as having input devices, output devices, processing devices, and storage devices. It then provides examples of common hardware components that fall into each of these categories and explains their basic functions. The document also discusses computer memory, motherboards, video cards, network cards, sound cards, and various storage devices. It provides a brief overview of operating systems, software development tools, and application software.┘ģ┘ā┘ł┘垦ž¬ ž¦┘䞣ž¦ž│ž©
┘ģ┘ā┘ł┘垦ž¬ ž¦┘䞣ž¦ž│ž©Rayaor
╠²
This document outlines the main components of a computer system including both hardware and software. It discusses the memory unit for data storage, the central processing unit for computations, various input units like keyboards and mice, storage units such as hard disks and CDs, and output units like monitors and printers that display or present the results of computations.Integrated Technology Unit Presentation
Integrated Technology Unit PresentationPoom Chitnuchtaranon
╠²
Diskeeper is disk defragmentation software developed by Diskeeper Corporation that performs basic and specialized defragmentation. It includes scheduled defragmentation settings and uses technologies like InvisiTasking to prevent fragmentation while running smoothly and HyperFast for solid state drives. Diskeeper is available in several editions for personal, server, and enterprise use ranging in price from $39.95 to $99.95 with additional HyperFast support available. It has won numerous awards between 2009 and 2010 from publications like Windows IT Pro and Redmond Magazine for its effectiveness.Basics of Computer
Basics of ComputerManish Goswami
╠²
A computer is a machine that allows users to enter data, process information, and produce output like documents, pictures, and music. It uses hardware components that can be touched like a CPU, monitor, keyboard, and mouse, as well as software programs and operating systems to perform tasks. The document then explains the basic parts and functions of a computer system including inputs, processors, memory, outputs, file management, desktop interface, start menu, and booting process.Computer components
Computer componentsMd. Sohanur Rahman
╠²
This document discusses the key components of a computer system including input, output, processing, storage, and networking devices. It provides details on common computer hardware such as the monitor, motherboard, CPU, RAM, expansion cards, power supply, disk drives, and input devices. It also covers software types including operating systems and applications. Memory and storage measurements and technologies are defined. The roles of components like graphics cards, motherboards, CPUs and memory are explained. Output devices such as printers and speakers are also outlined. Networking methods for connecting computers are described.Hardware it presentation
Hardware it presentationsyedamarziazaidi
╠²
The document discusses various computer hardware components including:
1. The keyboard, mouse, hard disk drive, CD-ROM drive, floppy disk drive, motherboard, microprocessor, RAM, and power supply are described as the primary physical components of a computer system.
2. Details are provided on the purpose and evolution of each component, for example keyboards have additional keys now and mice evolved from mechanical to optical models.
3. Types of each component are listed, such as AT, PS/2, and USB keyboards, and SATA, SCSI and ATA hard disk interfaces.EDP powerpoint
EDP powerpointklayd
╠²
Computer system hardware consists of input, processing, storage, and output components. Common input devices include keyboards, mice, and scanners which allow a user to enter data. Processing involves executing computer programs through processes. Data is stored using various storage devices like hard drives, CDs, DVDs, and flash drives. Output is presented to the user via monitors, printers, and speakers.Insides Of A Computer
Insides Of A ComputerJosh Mathew
╠²
The document outlines several key components of a computer and their functions. The power supply provides power for the computer to run. The motherboard is the main circuit board that allows components to communicate. The hard drive is mass storage, while the processor acts as the brain and RAM provides memory. The video card generates images and CD drives read discs.Lubuntu a Lightweight Desktop
Lubuntu a Lightweight Desktopmahrukh rafique
╠²
Lubuntu is a lightweight Linux distribution based on Ubuntu that uses LXDE as its desktop environment. It is optimized for older and lower-powered hardware. The document discusses Lubuntu's history, system requirements of 512MB RAM and a Pentium 4 or equivalent CPU. It also outlines Lubuntu's installation process, which involves downloading an ISO, burning it to a disc or USB, booting from it to start the installation, and selecting options like username during setup. Key features mentioned include system settings, office productivity apps, internet browsing, multimedia playback, and a lightweight file manager.Ubuntu 10.04 Installation Guide
Ubuntu 10.04 Installation GuideRanjith Siji
╠²
This document provides instructions for installing Ubuntu 10.04. It outlines the system requirements, boot process from a live CD, login to the live session, use GParted to create partitions including /, /boot, swap and /home, select installation parameters, install Ubuntu, and reboot into the new system. Upon completion, the new Ubuntu installation will provide applications like OpenOffice, Firefox, and multimedia programs without cost and free of viruses.Desktop environments
Desktop environmentshindalfalasi
╠²
This document discusses several common desktop environments including KDE, GNOME, LXDE, Unity, and Xfce. These desktop environments control the screen and provide utility programs to manage files and tasks. KDE is the default for Mandriva and SUSE, GNOME is used by Fedora and Debian, LXDE works well on older computers, Unity is used by Ubuntu, and Xfce aims to consume fewer system resources than other environments. It is also possible to create a custom desktop environment by combining individual components.Parts of a computer
Parts of a computerLitigante Independiente
╠²
This document provides brief descriptions of common computer hardware components including the hard disk drive located inside the system unit, CD and DVD drives that can play music CDs, the mouse connected by a wired tail or wireless, the keyboard with letter, number, and special keys, the monitor screen that displays still or moving pictures, and modems that can be built into the system unit or separate for higher speeds.It comp basics
It comp basicsA B
╠²
The document provides an overview of computer basics. It discusses:
1. The order of presentation for the slides, which cover introduction, inputs/outputs, storage devices, memory, and the CPU/uses.
2. The definition of a computer as a device that accepts input, processes data, and produces output according to stored instructions.
3. The main hardware components of a computer including input devices like keyboards and mice, output devices like monitors and printers, storage devices like hard drives and CDs/DVDs, and memory like RAM and ROM.
4. The central processing unit containing the arithmetic logic unit, control unit, and registers to perform calculations and coordinate processing.
5ž╣ž▒žČ žŻž¬ž╣ž▒┘ü ž╣┘ä┘ē žŁž¦ž│┘łž©┘Ŗ 04
ž╣ž▒žČ žŻž¬ž╣ž▒┘ü ž╣┘ä┘ē žŁž¦ž│┘łž©┘Ŗ 04┘å┘łž¦┘üž░ žŁž¦ž│┘łž©┘Ŗž®
╠²
ž╣ž▒žČ žŻž¬ž╣ž▒┘ü ž╣┘ä┘ē žŁž¦ž│┘łž©┘Ŗ 04Download Myboot disk
Download Myboot diskRoach
╠²
Myboot Disk is software that allows users to create startup disks with utilities like boot repair, file extraction, drive partitioning, and formatting. It supports Windows 7/Vista/XP/NT/2000/DOS and provides a graphical interface. The startup disks can be used to troubleshoot operating system errors, correct installations, fix registry issues, and backup files.Common componets
Common componetsTapz Mashanga
╠²
The document outlines the common components of a computer system including the CPU, HDD, RAM, power supply, expansion cards, optical disc drive, and motherboard. The CPU processes all calculations and functions, the HDD reads and writes data to the hard disk, RAM provides random access memory, the power supply provides power, expansion cards enhance capabilities, the optical disc drive reads and writes optical discs using lasers, and the motherboard connects the main computer components.Lesson 7 - Maintaining, Updating, and Protecting
Lesson 7 - Maintaining, Updating, and ProtectingGene Carboni
╠²
This document provides information on tools for maintaining, updating, and protecting Windows 7. It discusses Disk Defragmenter, Disk Cleanup, Task Scheduler, Action Center, System Information, the Windows Registry, Windows Updates, Windows Defender, Microsoft Security Essentials, and Microsoft Forefront Endpoint Protection. These tools help optimize performance, remove unnecessary files, automate tasks, monitor system status and security, manage updates, and protect against malware and viruses.Computer components
Computer componentssophie07
╠²
The document discusses several key components of a computer system: the processor, which controls the computer's instructions and is called the "brain"; the motherboard, which connects major internal components like drives, ports, and input devices to allow everything to work together; and the video card, which displays animated graphics and videos on the screen using 2D and 3D capabilities. A power supply provides electricity to run all of these internal computer components.Remote control system (rcs)
Remote control system (rcs)Shekh Md Mehedi Hasan
╠²
The document details the architecture and functionality of a Remote Control System (RCS) that includes various components such as backdoors, agents, and a database for logging activities. It outlines the communication processes, configuration management, and different methods of infection, including the use of melted executables and offline installation tools. The system is designed for stealthy monitoring and provides tools for remote management and configuration of backdoors.Components of the computer
Components of the computerRainishDhiman
╠²
A computer has four main functions: input, processing, output, and storage. It has five key components that enable these functions: the central processing unit (CPU), memory, input units, output units, and storage. The CPU contains the control unit which directs the flow of data and signals, and the arithmetic logic unit which performs basic math and logic operations.Asiabsdcon2013
Asiabsdcon2013krispcbsd
╠²
The document discusses automating the deployment of FreeBSD and PC-BSD systems using pc-thinclient utility. It describes using PXE to boot clients over the network and install operating systems from a server. Key steps include setting up the server with DHCP, ports tree and installation files. Customizations like disk layout, packages and scripts allow automating varied installations for multiple clients from a centralized management point. Tips provided optimize the process like using ZFS, SSD and tmpfs for improved scalability.Technical Presentation of Computer Components
Technical Presentation of Computer ComponentsDaniel Moore
╠²
The technical presentation discusses several components of a computer system including RAM, hard drives, the CPU and heat sink, adapter cards, and optical drives. RAM temporarily stores applications, hard drives permanently store programs and files, the CPU is the brain that processes data and a heat sink prevents overheating. Adapter cards display images using the processor and come in types like PCI, AGP, and PCIe. Optical drives read discs for software, entertainment, and troubleshooting.Operating system
Operating systemrocalima1
╠²
The document discusses the functions of modern operating systems. It notes that operating systems now allow users to run a variety of applications for tasks like displaying video, creating documents, and accessing the internet. It also explains that operating systems manage core computer functions like input/output, memory, and networking. Additionally, the document outlines that operating systems use kernel programs and system programs to implement required services and allow other programs to run. Examples of operating systems mentioned include Mac, Android, and Windows.Windows 7
Windows 7shikha23dec
╠²
Windows 7 is the 7th major version of Microsoft's Windows operating system, released in 2009. It was intended to be compatible with existing device drivers, applications, and hardware while including improvements such as better multi-touch support and a redesigned taskbar. Windows 7 features a more personalized user interface with themes and gadgets, improved performance, new media streaming and sharing capabilities, and enhanced support for touchscreens. It requires at least 1GB of RAM, 16GB of storage, and a graphics card with a WDDM 1.0 driver to run.Computer Parts Presentation
Computer Parts PresentationStacey Robinson
╠²
This document lists and defines common computer hardware components including the monitor, CPU, keyboard, mouse, disk drive, flash drive, headphones, printer, speakers, document camera, smartboard, webcam, iPad, laptop, and encourages identifying each component and playing a matching game to learn the names.Cyber Threat Hunting - Hunting in Memory at Scale
Cyber Threat Hunting - Hunting in Memory at ScaleInfocyte
╠²
The document discusses the architecture and functionalities of the Microsoft Windows Host API, covering user-mode and kernel-mode APIs including memory management and process manipulation. It also describes techniques for bypassing Windows security measures like AMSI through PowerShell scripts and risky API hooks that facilitate malicious activities. Additionally, it includes code snippets illustrating these concepts and examples of hiding registry keys and artifacts.Internal parts
Internal partssankarsrivatsa
╠²
The computer has several internal parts including the CPU for processing, RAM for temporary storage during computations, a hard drive for permanent storage, a network card to connect to the internet, and a graphics card or chip to handle visuals. Additional components are the mouse, keyboard, power supply, fan and DVD player.SESSION 9 - Storage on the computer .pdf
SESSION 9 - Storage on the computer .pdfMaxwell Musonda
╠²
The document discusses computer memory, detailing its types, units of measurement, and conversion methods. It distinguishes between primary memory (RAM and ROM) and secondary memory, explaining their characteristics and functions. It emphasizes the significance of storage capacity, access time, and the binary nature of data storage.computer storage
computer storageDipankar Dutta
╠²
This document discusses different types of computer storage. It describes primary memory (RAM), cache memory, and secondary memory. Primary memory is volatile and holds data currently being processed, while secondary memory (hard disks, USB drives, etc.) is non-volatile and used for long-term storage. Cache memory sits between the CPU and primary memory to provide faster access to frequently used data. The document also outlines different storage devices like hard disks, optical disks, USB drives and their characteristics.More Related Content
What's hot (20)
Insides Of A Computer
Insides Of A ComputerJosh Mathew
╠²
The document outlines several key components of a computer and their functions. The power supply provides power for the computer to run. The motherboard is the main circuit board that allows components to communicate. The hard drive is mass storage, while the processor acts as the brain and RAM provides memory. The video card generates images and CD drives read discs.Lubuntu a Lightweight Desktop
Lubuntu a Lightweight Desktopmahrukh rafique
╠²
Lubuntu is a lightweight Linux distribution based on Ubuntu that uses LXDE as its desktop environment. It is optimized for older and lower-powered hardware. The document discusses Lubuntu's history, system requirements of 512MB RAM and a Pentium 4 or equivalent CPU. It also outlines Lubuntu's installation process, which involves downloading an ISO, burning it to a disc or USB, booting from it to start the installation, and selecting options like username during setup. Key features mentioned include system settings, office productivity apps, internet browsing, multimedia playback, and a lightweight file manager.Ubuntu 10.04 Installation Guide
Ubuntu 10.04 Installation GuideRanjith Siji
╠²
This document provides instructions for installing Ubuntu 10.04. It outlines the system requirements, boot process from a live CD, login to the live session, use GParted to create partitions including /, /boot, swap and /home, select installation parameters, install Ubuntu, and reboot into the new system. Upon completion, the new Ubuntu installation will provide applications like OpenOffice, Firefox, and multimedia programs without cost and free of viruses.Desktop environments
Desktop environmentshindalfalasi
╠²
This document discusses several common desktop environments including KDE, GNOME, LXDE, Unity, and Xfce. These desktop environments control the screen and provide utility programs to manage files and tasks. KDE is the default for Mandriva and SUSE, GNOME is used by Fedora and Debian, LXDE works well on older computers, Unity is used by Ubuntu, and Xfce aims to consume fewer system resources than other environments. It is also possible to create a custom desktop environment by combining individual components.Parts of a computer
Parts of a computerLitigante Independiente
╠²
This document provides brief descriptions of common computer hardware components including the hard disk drive located inside the system unit, CD and DVD drives that can play music CDs, the mouse connected by a wired tail or wireless, the keyboard with letter, number, and special keys, the monitor screen that displays still or moving pictures, and modems that can be built into the system unit or separate for higher speeds.It comp basics
It comp basicsA B
╠²
The document provides an overview of computer basics. It discusses:
1. The order of presentation for the slides, which cover introduction, inputs/outputs, storage devices, memory, and the CPU/uses.
2. The definition of a computer as a device that accepts input, processes data, and produces output according to stored instructions.
3. The main hardware components of a computer including input devices like keyboards and mice, output devices like monitors and printers, storage devices like hard drives and CDs/DVDs, and memory like RAM and ROM.
4. The central processing unit containing the arithmetic logic unit, control unit, and registers to perform calculations and coordinate processing.
5ž╣ž▒žČ žŻž¬ž╣ž▒┘ü ž╣┘ä┘ē žŁž¦ž│┘łž©┘Ŗ 04
ž╣ž▒žČ žŻž¬ž╣ž▒┘ü ž╣┘ä┘ē žŁž¦ž│┘łž©┘Ŗ 04┘å┘łž¦┘üž░ žŁž¦ž│┘łž©┘Ŗž®
╠²
ž╣ž▒žČ žŻž¬ž╣ž▒┘ü ž╣┘ä┘ē žŁž¦ž│┘łž©┘Ŗ 04Download Myboot disk
Download Myboot diskRoach
╠²
Myboot Disk is software that allows users to create startup disks with utilities like boot repair, file extraction, drive partitioning, and formatting. It supports Windows 7/Vista/XP/NT/2000/DOS and provides a graphical interface. The startup disks can be used to troubleshoot operating system errors, correct installations, fix registry issues, and backup files.Common componets
Common componetsTapz Mashanga
╠²
The document outlines the common components of a computer system including the CPU, HDD, RAM, power supply, expansion cards, optical disc drive, and motherboard. The CPU processes all calculations and functions, the HDD reads and writes data to the hard disk, RAM provides random access memory, the power supply provides power, expansion cards enhance capabilities, the optical disc drive reads and writes optical discs using lasers, and the motherboard connects the main computer components.Lesson 7 - Maintaining, Updating, and Protecting
Lesson 7 - Maintaining, Updating, and ProtectingGene Carboni
╠²
This document provides information on tools for maintaining, updating, and protecting Windows 7. It discusses Disk Defragmenter, Disk Cleanup, Task Scheduler, Action Center, System Information, the Windows Registry, Windows Updates, Windows Defender, Microsoft Security Essentials, and Microsoft Forefront Endpoint Protection. These tools help optimize performance, remove unnecessary files, automate tasks, monitor system status and security, manage updates, and protect against malware and viruses.Computer components
Computer componentssophie07
╠²
The document discusses several key components of a computer system: the processor, which controls the computer's instructions and is called the "brain"; the motherboard, which connects major internal components like drives, ports, and input devices to allow everything to work together; and the video card, which displays animated graphics and videos on the screen using 2D and 3D capabilities. A power supply provides electricity to run all of these internal computer components.Remote control system (rcs)
Remote control system (rcs)Shekh Md Mehedi Hasan
╠²
The document details the architecture and functionality of a Remote Control System (RCS) that includes various components such as backdoors, agents, and a database for logging activities. It outlines the communication processes, configuration management, and different methods of infection, including the use of melted executables and offline installation tools. The system is designed for stealthy monitoring and provides tools for remote management and configuration of backdoors.Components of the computer
Components of the computerRainishDhiman
╠²
A computer has four main functions: input, processing, output, and storage. It has five key components that enable these functions: the central processing unit (CPU), memory, input units, output units, and storage. The CPU contains the control unit which directs the flow of data and signals, and the arithmetic logic unit which performs basic math and logic operations.Asiabsdcon2013
Asiabsdcon2013krispcbsd
╠²
The document discusses automating the deployment of FreeBSD and PC-BSD systems using pc-thinclient utility. It describes using PXE to boot clients over the network and install operating systems from a server. Key steps include setting up the server with DHCP, ports tree and installation files. Customizations like disk layout, packages and scripts allow automating varied installations for multiple clients from a centralized management point. Tips provided optimize the process like using ZFS, SSD and tmpfs for improved scalability.Technical Presentation of Computer Components
Technical Presentation of Computer ComponentsDaniel Moore
╠²
The technical presentation discusses several components of a computer system including RAM, hard drives, the CPU and heat sink, adapter cards, and optical drives. RAM temporarily stores applications, hard drives permanently store programs and files, the CPU is the brain that processes data and a heat sink prevents overheating. Adapter cards display images using the processor and come in types like PCI, AGP, and PCIe. Optical drives read discs for software, entertainment, and troubleshooting.Operating system
Operating systemrocalima1
╠²
The document discusses the functions of modern operating systems. It notes that operating systems now allow users to run a variety of applications for tasks like displaying video, creating documents, and accessing the internet. It also explains that operating systems manage core computer functions like input/output, memory, and networking. Additionally, the document outlines that operating systems use kernel programs and system programs to implement required services and allow other programs to run. Examples of operating systems mentioned include Mac, Android, and Windows.Windows 7
Windows 7shikha23dec
╠²
Windows 7 is the 7th major version of Microsoft's Windows operating system, released in 2009. It was intended to be compatible with existing device drivers, applications, and hardware while including improvements such as better multi-touch support and a redesigned taskbar. Windows 7 features a more personalized user interface with themes and gadgets, improved performance, new media streaming and sharing capabilities, and enhanced support for touchscreens. It requires at least 1GB of RAM, 16GB of storage, and a graphics card with a WDDM 1.0 driver to run.Computer Parts Presentation
Computer Parts PresentationStacey Robinson
╠²
This document lists and defines common computer hardware components including the monitor, CPU, keyboard, mouse, disk drive, flash drive, headphones, printer, speakers, document camera, smartboard, webcam, iPad, laptop, and encourages identifying each component and playing a matching game to learn the names.Cyber Threat Hunting - Hunting in Memory at Scale
Cyber Threat Hunting - Hunting in Memory at ScaleInfocyte
╠²
The document discusses the architecture and functionalities of the Microsoft Windows Host API, covering user-mode and kernel-mode APIs including memory management and process manipulation. It also describes techniques for bypassing Windows security measures like AMSI through PowerShell scripts and risky API hooks that facilitate malicious activities. Additionally, it includes code snippets illustrating these concepts and examples of hiding registry keys and artifacts.Internal parts
Internal partssankarsrivatsa
╠²
The computer has several internal parts including the CPU for processing, RAM for temporary storage during computations, a hard drive for permanent storage, a network card to connect to the internet, and a graphics card or chip to handle visuals. Additional components are the mouse, keyboard, power supply, fan and DVD player.Similar to Flowcharts (20)
SESSION 9 - Storage on the computer .pdf
SESSION 9 - Storage on the computer .pdfMaxwell Musonda
╠²
The document discusses computer memory, detailing its types, units of measurement, and conversion methods. It distinguishes between primary memory (RAM and ROM) and secondary memory, explaining their characteristics and functions. It emphasizes the significance of storage capacity, access time, and the binary nature of data storage.computer storage
computer storageDipankar Dutta
╠²
This document discusses different types of computer storage. It describes primary memory (RAM), cache memory, and secondary memory. Primary memory is volatile and holds data currently being processed, while secondary memory (hard disks, USB drives, etc.) is non-volatile and used for long-term storage. Cache memory sits between the CPU and primary memory to provide faster access to frequently used data. The document also outlines different storage devices like hard disks, optical disks, USB drives and their characteristics.Unit-II Memory Interfacing.pptx
Unit-II Memory Interfacing.pptxpvg123456
╠²
This document provides information about computer memory. It discusses the different types of memory including primary memory (RAM and ROM), secondary memory, and cache memory. Primary memory is the main memory located on the motherboard that is directly accessible by the CPU. It is faster than secondary memory but volatile, meaning data is lost when power is removed. The document also defines the basic units of memory such as bits, bytes, kilobytes, megabytes, and gigabytes. RAM is the type of primary memory that temporarily stores active data and needs constant power, while ROM permanently stores basic startup instructions.Computer memory
Computer memoryMrjonesit
╠²
This document discusses different types of computer memory and storage. It defines ROM as permanent memory that cannot be changed and RAM as temporary memory that only works when a computer is turned on. It then explains units of measurement for memory like bytes, kilobytes, megabytes and gigabytes. Finally, it describes various methods of external storage like hard drives, floppy disks, CDs, DVDs, and flash drives, noting their storage capacities and common uses.Storing data ch 4
Storing data ch 4Khan Yousafzai
╠²
This document discusses data storage and memory. It explains that instructions and data are stored in main memory which is made up of bytes that each hold 8 bits. It defines different units of measurement for memory size like kilobytes, megabytes, and gigabytes. The document outlines different types of memory like RAM, ROM, SRAM, and DRAM. It also describes various storage devices like floppy disks, hard drives, magnetic tapes, CDs, DVDs, and backup devices like tape streamers, zip drives, and jaz drives.STORAGE_DEVICES - Copy coooooooopyyyy.ppt
STORAGE_DEVICES - Copy coooooooopyyyy.pptnarifmsit18seecs
╠²
The document discusses different types of storage devices, their capacities, and the distinctions between main store (ROM and RAM) and backing stores (internal and external). It explains measurement relationships between various storage units from bits to petabytes and highlights the purpose of different storage media such as hard disks and magnetic tapes. Additionally, it includes activities and quizzes related to understanding storage concepts.STORAGE ppt /presentation for clg project
STORAGE ppt /presentation for clg projectcardsfish64
╠²
The document discusses various types of storage devices, including their capacities and functionalities, detailing measurements from bits to petabytes and the distinction between main (ROM and RAM) and backing stores (internal and external). It explains the characteristics of hard disks, floppy disks, zip disks, and magnetic tapes, including their uses, data retention, and access methods. Activities and homework are included to reinforce understanding of storage capacity relationships and device characteristics.What is memory
What is memoryAzaanNaqvi
╠²
This document defines computer memory and storage and describes the different types. It explains that memory is where data is temporarily stored for quick access by the CPU, while storage is for permanent storage of data and programs. The primary types of memory are RAM and ROM, which are volatile and directly accessed by the CPU. Secondary storage includes hard disks, flash drives, and optical discs for non-volatile and permanent storage of data.Computer Memory
Computer MemorySweta Kumari Barnwal
╠²
The document provides an overview of computer memory, detailing the importance of primary (RAM and ROM) and secondary memory (e.g., hard drives, CDs) in data storage and processing. It describes various types of memory, including cache, RAM (static and dynamic), and ROM, as well as their characteristics, advantages, and disadvantages. Additionally, it explains different secondary storage devices such as magnetic tapes and disks, highlighting their roles in long-term data retention and cost-effectiveness compared to primary memory.Storage devices
Storage devicesChitranshi Haridas
╠²
This document discusses computer storage and memory. It explains that computers use binary digits (bits) to store data, with a byte being 8 bits. It describes different types of memory like ROM and RAM. It also discusses various storage devices like hard drives, floppy disks, CDs/DVDs, and flash drives. It explains the differences between these storage types and how they have varying storage capacities depending on being fixed or removable media.Chapter1 9-07
Chapter1 9-07punjab universty
╠²
The chapter introduces computer memory units including main memory (RAM) and secondary storage. It discusses different types of memory like RAM, ROM, PROM, and EPROM. RAM is volatile and used for temporary storage while ROM permanently stores basic instructions. Secondary storage devices discussed include magnetic tapes, floppy disks, and hard disks which store large amounts of non-volatile data. Optical disks like CDs, DVDs, and Blu-ray are also covered as high capacity, portable secondary storage.Memory Unit
Memory UnitDAVIS THOMAS
╠²
Memory is divided into primary and secondary memory. Primary memory directly interacts with the CPU and includes ROM and RAM. ROM stores initial startup instructions and cannot be changed, while RAM stores active programs and data and comes in volatile DRAM and non-volatile SRAM types. Secondary memory like hard disks store data permanently and have greater storage than primary memory.primary memory
primary memoryRamya Kotyan
╠²
Primary memory, also known as main memory, is used to store data and instructions that the CPU is currently processing. It has limited capacity and is volatile, meaning data is lost when power is turned off. RAM and ROM are types of primary memory. Secondary memory is used for permanent storage and includes hard disks, CDs, DVDs. It has larger capacity but is slower to access. Memory is organized in a hierarchy with registers being fastest, then RAM, and finally secondary storage being slowest but able to store the most data.Chapter1 9-07
Chapter1 9-07dereennn
╠²
The document discusses different types of computer memory and storage devices. It describes RAM, ROM, PROM, and EPROM as memory devices, and how they differ in terms of volatility and accessibility. For storage, it outlines magnetic devices like hard disks, floppy disks, and tapes, as well as optical disks like CDs, DVDs, and Blu-ray. It provides details on the storage capacities and characteristics of each type of memory and storage device.Hardware
Hardwareamal312
╠²
The document provides information about computer hardware and components. It defines hardware as the physical parts of a computer system that can be touched, such as monitors, processors, and printers. It also explains that software refers to programs and data used with the computer. The document then covers various computer components in more detail, including the central processing unit, memory, storage devices, input devices, and output devices.Computer memory
Computer memoryUtsavMandaviya
╠²
Computer memory is used to temporarily store data and instructions for processing by the CPU. There are two main types of computer memory: primary and secondary. Primary memory, also called main memory or internal memory, is located directly on the motherboard and includes RAM and ROM. RAM is volatile and used for temporary storage, while ROM is non-volatile and contains the computer's basic input/output system. Secondary memory, also called external storage, is used for permanent storage and includes hard drives, solid state drives, CDs, DVDs, floppy disks, and flash drives. Memory is measured in bits, bytes, kilobytes, megabytes, gigabytes, and terabytes, with the largest units able to storeStorage devices
Storage deviceslatifah2001
╠²
The document discusses various computer storage devices and their characteristics. It describes primary storage RAM and secondary storage devices like hard disk drives. It explains what RAM and ROM are, their differences, and provides examples of different types of storage media like CD-ROMs, DVDs, hard disks, floppy disks, flash memory, and how many bytes and bits are used to store data.Data storage
Data storagetonysusu
╠²
ROM is permanent, non-volatile memory that contains instructions for booting the operating system and cannot be changed. RAM is temporary, volatile memory that runs programs and works only when the computer is on. Computer memory is measured in bytes, with kilobytes and megabytes denoting increasing sizes, while hard disks provide large internal storage and floppy disks and CDs provide external portable storage.Complete Computer Memory Information
Complete Computer Memory InformationJasur Ahmadov
╠²
Memory is a core component of computers that allows CPUs to interact with programs and data. It was invented in the 19th century and has grown enormously in capacity over time. Memory comes in two main types - primary memory (RAM) which is volatile and holds active data and instructions, and secondary memory like hard disks which is non-volatile for long-term storage. RAM itself comes in variants like DRAM and SRAM that differ in how they store bits of data. ROM is read-only memory that stores instructions during startup. Caches provide even faster access than RAM but have limited capacity. Overall memory allows computers to function by temporarily or permanently holding the digital information they require.Ad
Recently uploaded (20)
FIDO Seminar: New Data: Passkey Adoption in the Workforce.pptx
FIDO Seminar: New Data: Passkey Adoption in the Workforce.pptxFIDO Alliance
╠²
FIDO Seminar: New Data: Passkey Adoption in the Workforce"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays
╠²
We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. WeŌĆÖll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.OWASP Barcelona 2025 Threat Model Library
OWASP Barcelona 2025 Threat Model LibraryPetraVukmirovic
╠²
Threat Model Library Launch at OWASP Barcelona 2025
https://owasp.org/www-project-threat-model-library/Edge-banding-machines-edgeteq-s-200-en-.pdf
Edge-banding-machines-edgeteq-s-200-en-.pdfAmirStern2
╠²
ū×ūøūĢūĀū¬ ū¦ūĀūśūÖūØ ūöū×ū¬ūÉūÖū×ūö ū£ūĀūÆū©ūÖūĢū¬ ū¦ūśūĀūĢū¬ ūÉūĢ ūÆūōūĢū£ūĢū¬ (ūøū×ūøūĢūĀū¬ ūÆūÖūæūĢūÖ).
ū×ūōūæūÖū¦ūö ū¦ūĀūśūÖūØ ū×ūÆū£ūÖū£ ūÉūĢ ūżūĪūÖūØ, ūóūō ūóūĢūæūÖ ū¦ūĀūś ŌĆō 3 ū×"ū× ūĢūóūĢūæūÖ ūŚūĢū×ū© ūóūō 40 ū×"ū×. ūæū¦ū© ū×ū×ūĢūŚū®ūæ ūöū×ū¬ū©ūÖūó ūóū£ ū¬ū¦ū£ūĢū¬, ūĢū×ūĀūĢūóūÖūØ ū×ūÉūĪūÖūæūÖūÖūØ ū¬ūóū®ūÖūÖū¬ūÖūÖūØ ūøū×ūĢ ūæū×ūøūĢūĀūĢū¬ ūöūÆūōūĢū£ūĢū¬.ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...
ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...Edge AI and Vision Alliance
╠²
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/from-enterprise-to-makers-driving-vision-ai-innovation-at-the-extreme-edge-a-presentation-from-sony-semiconductor-solutions/
Amir Servi, Edge Deep Learning Product Manager at Sony Semiconductor Solutions, presents the ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme EdgeŌĆØ tutorial at the May 2025 Embedded Vision Summit.
SonyŌĆÖs unique integrated sensor-processor technology is enabling ultra-efficient intelligence directly at the image source, transforming vision AI for enterprises and developers alike. In this presentation, Servi showcases how the AITRIOS platform simplifies vision AI for enterprises with tools for large-scale deployments and model management.
Servi also highlights his companyŌĆÖs collaboration with Ultralytics and Raspberry Pi, which brings YOLO models to the developer community, empowering grassroots innovation. Whether youŌĆÖre scaling vision AI for industry or experimenting with cutting-edge tools, this presentation will demonstrate how Sony is accelerating high-performance, energy-efficient vision AI for all.FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptx
FIDO Seminar: Evolving Landscape of Post-Quantum Cryptography.pptxFIDO Alliance
╠²
FIDO Seminar: Evolving Landscape of Post-Quantum CryptographyPowering Multi-Page Web Applications Using Flow Apps and FME Data Streaming
Powering Multi-Page Web Applications Using Flow Apps and FME Data StreamingSafe Software
╠²
Unleash the potential of FME Flow to build and deploy advanced multi-page web applications with ease. Discover how Flow Apps and FMEŌĆÖs data streaming capabilities empower you to create interactive web experiences directly within FME Platform. Without the need for dedicated web-hosting infrastructure, FME enhances both data accessibility and user experience. Join us to explore how to unlock the full potential of FME for your web projects and seamlessly integrate data-driven applications into your workflows.Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software
╠²
In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software
╠²
This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection."Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays
╠²
What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.Enabling BIM / GIS integrations with Other Systems with FME
Enabling BIM / GIS integrations with Other Systems with FMESafe Software
╠²
Jacobs has successfully utilized FME to tackle the complexities of integrating diverse data sources in a confidential $1 billion campus improvement project. The project aimed to create a comprehensive digital twin by merging Building Information Modeling (BIM) data, Construction Operations Building Information Exchange (COBie) data, and various other data sources into a unified Geographic Information System (GIS) platform. The challenge lay in the disparate nature of these data sources, which were siloed and incompatible with each other, hindering efficient data management and decision-making processes.
To address this, Jacobs leveraged FME to automate the extraction, transformation, and loading (ETL) of data between ArcGIS Indoors and IBM Maximo. This process ensured accurate transfer of maintainable asset and work order data, creating a comprehensive 2D and 3D representation of the campus for Facility Management. FME's server capabilities enabled real-time updates and synchronization between ArcGIS Indoors and Maximo, facilitating automatic updates of asset information and work orders. Additionally, Survey123 forms allowed field personnel to capture and submit data directly from their mobile devices, triggering FME workflows via webhooks for real-time data updates. This seamless integration has significantly enhanced data management, improved decision-making processes, and ensured data consistency across the project lifecycle.Turning the Page ŌĆō How AI is Exponentially Increasing Speed, Accuracy, and Ef...
Turning the Page ŌĆō How AI is Exponentially Increasing Speed, Accuracy, and Ef...Impelsys Inc.
╠²
Artificial Intelligence (AI) has become a game-changer in content creation, automating tasks that were once very time-consuming and labor-intensive. AI-powered tools are now capable of generating high-quality articles, blog posts, and even poetry by analyzing large datasets of text and producing human-like writing.
However, AIŌĆÖs influence on content generation is not limited to text; it has also made advancements in multimedia content, such as image, video, and audio generation. AI-powered tools can now transform raw images and footage into visually stunning outputs, and are all set to have a profound impact on the publishing industry.ŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOpt...
ŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOpt...Edge AI and Vision Alliance
╠²
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/key-requirements-to-successfully-implement-generative-ai-in-edge-devices-optimized-mapping-to-the-enhanced-npx6-neural-processing-unit-ip-a-presentation-from-synopsys/
Gordon Cooper, Principal Product Manager at Synopsys, presents the ŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOptimized Mapping to the Enhanced NPX6 Neural Processing Unit IPŌĆØ tutorial at the May 2025 Embedded Vision Summit.
In this talk, Cooper discusses emerging trends in generative AI for edge devices and the key role of transformer-based neural networks. He reviews the distinct attributes of transformers, their advantages over conventional convolutional neural networks and how they enable generative AI.
Cooper then covers key requirements that must be met for neural processing units (NPU) to support transformers and generative AI in edge device applications. He uses transformer-based generative AI examples to illustrate the efficient mapping of these workloads onto the enhanced Synopsys ARC NPX NPU IP family.Raman Bhaumik - Passionate Tech Enthusiast
Raman Bhaumik - Passionate Tech EnthusiastRaman Bhaumik
╠²
A Junior Software Developer with a flair for innovation, Raman Bhaumik excels in delivering scalable web solutions. With three years of experience and a solid foundation in Java, Python, JavaScript, and SQL, she has streamlined task tracking by 20% and improved application stability.No-Code Workflows for CAD & 3D Data: Scaling AI-Driven Infrastructure
No-Code Workflows for CAD & 3D Data: Scaling AI-Driven InfrastructureSafe Software
╠²
When projects depend on fast, reliable spatial data, every minute counts.
AI Clearing needed a faster way to handle complex spatial data from drone surveys, CAD designs and 3D project models across construction sites. With FME Form, they built no-code workflows to clean, convert, integrate, and validate dozens of data formats ŌĆō cutting analysis time from 5 hours to just 30 minutes.
Join us, our partner Globema, and customer AI Clearing to see how they:
-Automate processing of 2D, 3D, drone, spatial, and non-spatial data
-Analyze construction progress 10x faster and with fewer errors
-Handle diverse formats like DWG, KML, SHP, and PDF with ease
-Scale their workflows for international projects in solar, roads, and pipelines
If you work with complex data, join us to learn how to optimize your own processes and transform your results with FME.FIDO Seminar: Authentication for a Billion Consumers - Amazon.pptx
FIDO Seminar: Authentication for a Billion Consumers - Amazon.pptxFIDO Alliance
╠²
FIDO Seminar: Authentication for a Billion Consumers - AmazonOpenACC and Open Hackathons Monthly Highlights June 2025
OpenACC and Open Hackathons Monthly Highlights June 2025OpenACC
╠²
The OpenACC organization focuses on enhancing parallel computing skills and advancing interoperability in scientific applications through hackathons and training. The upcoming 2025 Open Accelerated Computing Summit (OACS) aims to explore the convergence of AI and HPC in scientific computing and foster knowledge sharing. This year's OACS welcomes talk submissions from a variety of topics, from Using Standard Language Parallelism to Computer Vision Applications. The document also highlights several open hackathons, a call to apply for NVIDIA Academic Grant Program and resources for optimizing scientific applications using OpenACC directives.cnc-processing-centers-centateq-p-110-en.pdf
cnc-processing-centers-centateq-p-110-en.pdfAmirStern2
╠²
ū×ū©ūøū¢ ūóūÖūæūĢūōūÖūØ ū¬ūóū®ūÖūÖū¬ūÖ ūæūóū£ 3/4/5 ū”ūÖū©ūÖūØ, ūóūō 22 ūöūŚū£ūżūĢū¬ ūøū£ūÖūØ ūóūØ ūøū£ ūÉūżū®ū©ūĢūÖūĢū¬ ūöūóūÖūæūĢūō ūöūōū©ūĢū®ūĢū¬.╠²ūæūóū£ ū®ūśūŚ ūóūæūĢūōūö ūÆūōūĢū£ ūĢū×ūŚū®ūæ ūĀūĢūŚ ūĢū¦ū£ ū£ūöūżūóū£ūö ūæū®ūżūö ūöūóūæū©ūÖū¬/ū©ūĢūĪūÖū¬/ūÉūĀūÆū£ūÖū¬/ūĪūżū©ūōūÖū¬/ūóū©ūæūÖū¬ ūĢūóūĢūō..
ū×ūĪūĢūÆū£ ū£ūæū”ūó ūżūóūĢū£ūĢū¬ ūóūÖūæūĢūō ū®ūĢūĀūĢū¬ ūöū×ū¬ūÉūÖū×ūĢū¬ ū£ūóūĀūżūÖūØ ū®ūĢūĀūÖūØ: ū¦ūÖūōūĢūŚ ūÉūĀūøūÖ, ūÉūĢūżū¦ūÖ, ūĀūÖūĪūĢū©, ūĢūøū©ūĪūĢūØ ūÉūĀūøūÖ.ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...
ŌĆ£From Enterprise to Makers: Driving Vision AI Innovation at the Extreme Edge,...Edge AI and Vision Alliance
╠²
ŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOpt...
ŌĆ£Key Requirements to Successfully Implement Generative AI in Edge DevicesŌĆöOpt...Edge AI and Vision Alliance
╠²
Ad
Flowcharts
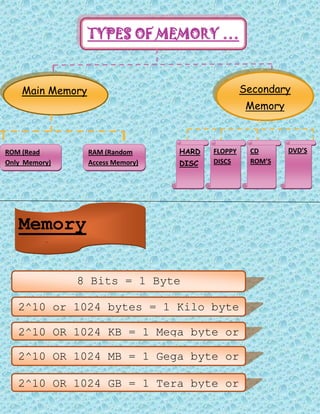
- 1. TYPES OF MEMORY ŌĆ” Main Memory Secondary Memory ROM (Read Only Memory) RAM (Random Access Memory) HARD DISC FLOPPY DISCS CD ROMŌĆÖS DVDŌĆÖS Memory Units 8 Bits = 1 Byte 2^10 or 1024 bytes = 1 Kilo byte or 1 KB 2^10 OR 1024 KB = 1 Mega byte or 1 MB 2^10 OR 1024 MB = 1 Gega byte or 1 GB 2^10 OR 1024 GB = 1 Tera byte or 1 TB
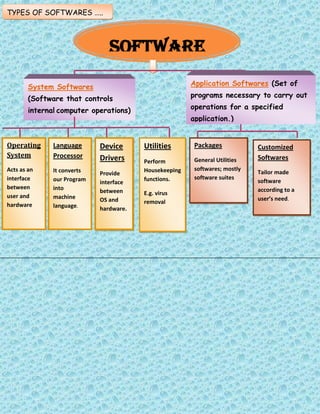
- 2. SOFTWARE SSystem Softwares (Software that controls internal computer operations) Application Softwares (Set of programs necessary to carry out operations for a specified application.) Operating System Acts as an interface between user and hardware Language Processor It converts our Program into machine language. Device Drivers Provide interface between OS and hardware. Utilities Perform Housekeeping functions. E.g. virus removal Packages General Utilities softwares; mostly software suites Customized Softwares Tailor made software according to a userŌĆÖs need. TYPES OF SOFTWARES ŌĆ”..