Get ahead of cloud network security trends and practices in 2020
- 1. 1 GET AHEAD OF CLOUD NETWORK SECURITY TRENDS AND PRACTICES FEB 12, 2020 WEBINAR
- 2. RICHARD STIENNON CEO and Co-Founder Valtix ROHIT GUPTA Global Segment Leader Security, Amazon Web Services SPEAKER PANEL VISHAL JAIN Chief Research Analyst, IT-Harvest
- 3. - Cloud security is just security. An evolution - 3 Stages of Digital Transformation - A new security model - Security model in AWS - Automate with integrated services - AWS security solutions AGENDA - Barriers and common seen practices - âUnboxingâ cloud network security - Cloud-Native Network Security Service - Q&A
- 4. 4 â An evolution, NOT a new layer â Endpoint for cloud (VMs, containers) â IAM for cloud â Network security for cloud DIGITAL TRANSFORMATION IS MOVING TO THE CLOUD
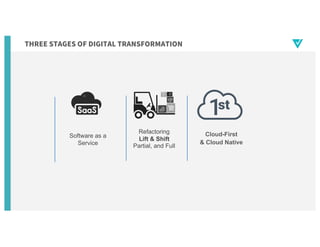
- 5. THREE STAGES OF DIGITAL TRANSFORMATION Software as a Service Refactoring Lift & Shift Partial, and Full Cloud-First & Cloud Native
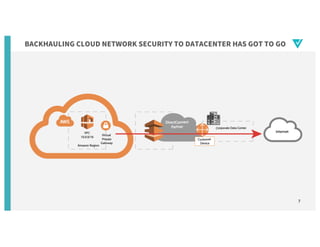
- 6. MOVING TO THE CLOUD INTRODUCED NETWORK BOTTLENECKS Traffic destined for cloud apps is forced through the corporate network
- 7. 7 BACKHAULING CLOUD NETWORK SECURITY TO DATACENTER HAS GOT TO GO
- 8. A NEW SECURITY MODEL: CLOUD NETWORK SECURITY SERVICE â Service centric â Controller based â Co-resident â Highly automated â Continuous awareness
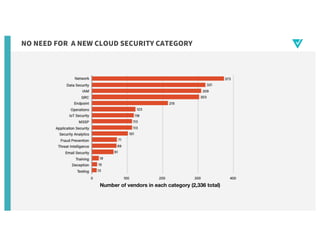
- 9. IS CLOUD SECURITY REALLY A NEW SECTOR OF THE SECURITY INDUSTRy? Or, are there just network, endpoint, and access controls applied to cloud properties?
- 10. NO NEED FOR A NEW CLOUD SECURITY CATEGORY Number of vendors in each category (2,336 total)
- 11. ROHIT GUPTA GLOBAL SEGMENT LEADER AMAZON WEB SERVICES
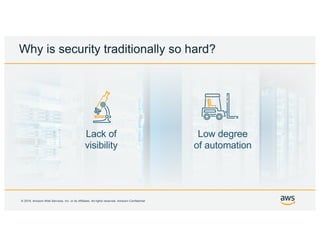
- 12. Š 2019, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential Why is security traditionally so hard? Low degree of automation Lack of visibility
- 13. Š 2019, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential O RMove fast Stay secure BeforeâŚ
- 14. Š 2019, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential O RMove fast Stay secure AN D BeforeâŚNowâŚ
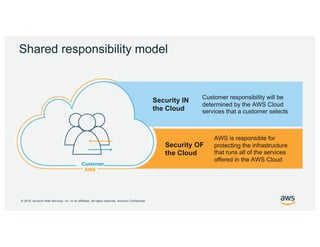
- 15. Š 2019, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential Shared responsibility model AWS Security OF the Cloud AWS is responsible for protecting the infrastructure that runs all of the services offered in the AWS Cloud Security IN the Cloud Customer responsibility will be determined by the AWS Cloud services that a customer selects Customer
- 16. Š 2019, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential âI have come to realize that as a relatively small organization, we can be far more secure in the cloud and achieve a higher level of assurance at a much lower cost, in terms of effort and dollars invested. We determined that security in AWS is superior to our on- premises data center across several dimensions, including patching, encryption, auditing and logging, entitlements, and compliance.â ⢠Looks for fraud, abuse, and insider trading over nearly 6 billion shares traded in U.S. equities markets every day ⢠Processes approximately 6 terabytes of data and 37 billion records on an average day ⢠Went from 3â4 weeks for server hardening to 3â4 minutes ⢠DevOps teams focus on automation and tools to raise the compliance bar and simplify controls ⢠Achieved incredible levels of assurance for consistencies of builds and patching via rebooting with automated deployment scripts âJohn Brady, CISO FINRA Financial industry regulatory authority
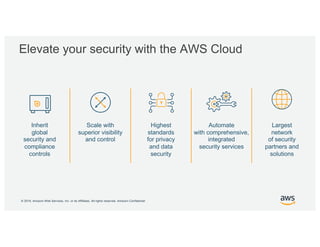
- 17. Š 2019, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential Automate with comprehensive, integrated security services Inherit global security and compliance controls Highest standards for privacy and data security Largest network of security partners and solutions Scale with superior visibility and control Elevate your security with the AWS Cloud
- 18. Š 2019, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential Inherit global security and compliance controls SOC 1 SOC 2 SOC 3 CJI S Gx P MPA A My Number Act VPAT Section 508 G-Cloud DoD SRG FERP A SEC Rule 17a-4(f)
- 19. Š 2019, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential Encryption at scale with keys managed by our AWS Key Management Service (KMS) or managing your own encryption keys with AWS CloudHSM using FIPS 140-2 Level 3 validated HSMs Meet data residency requirements Choose an AWS Region and AWS will not replicate it elsewhere unless you choose to do so Access services and tools that enable you to build compliant infrastructure on top of AWS Comply with local data privacy laws by controlling who can access content, its lifecycle, and disposal Highest standards for privacy
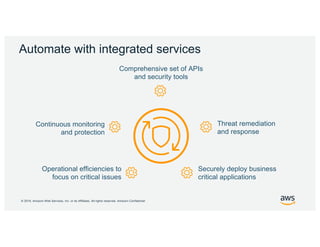
- 20. Š 2019, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential Threat remediation and response Securely deploy business critical applications Operational efficiencies to focus on critical issues Continuous monitoring and protection Automate with integrated services Comprehensive set of APIs and security tools
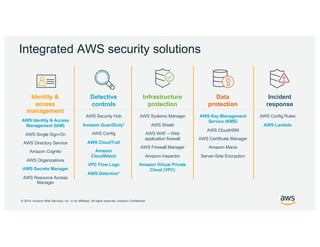
- 21. Š 2019, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential AWS Identity & Access Management (IAM) AWS Single Sign-On AWS Directory Service Amazon Cognito AWS Organizations AWS Secrets Manager AWS Resource Access Manager AWS Security Hub Amazon GuardDuty* AWS Config AWS CloudTrail Amazon CloudWatch VPC Flow Logs AWS Detective* AWS Systems Manager AWS Shield AWS WAF â Web application firewall AWS Firewall Manager Amazon Inspector Amazon Virtual Private Cloud (VPC) AWS Key Management Service (KMS) AWS CloudHSM AWS Certificate Manager Amazon Macie Server-Side Encryption AWS Config Rules AWS Lambda Identity & access management Detective controls Infrastructure protection Incident response Data protection Integrated AWS security solutions
- 22. VISHAL JAIN CEO & CO-FOUNDER, VALTIX
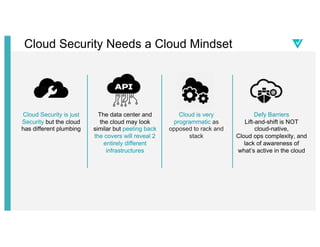
- 23. The data center and the cloud may look similar but peeling back the covers will reveal 2 entirely different infrastructures Cloud Security is just Security but the cloud has different plumbing Defy Barriers Lift-and-shift is NOT cloud-native, Cloud ops complexity, and lack of awareness of whatâs active in the cloud Cloud is very programmatic as opposed to rack and stack Cloud Security Needs a Cloud Mindset
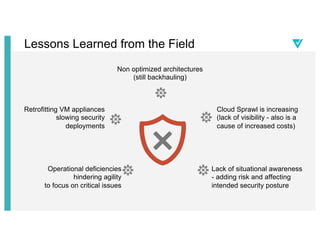
- 24. Lessons Learned from the Field Cloud Sprawl is increasing (lack of visibility - also is a cause of increased costs) Lack of situational awareness - adding risk and affecting intended security posture Operational deficiencies hindering agility to focus on critical issues Retrofitting VM appliances slowing security deployments Non optimized architectures (still backhauling)
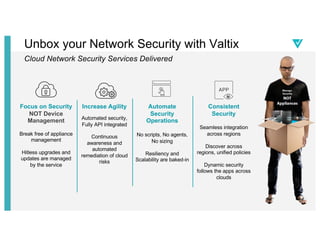
- 25. Unbox your Network Security with Valtix Cloud Network Security Services Delivered Focus on Security NOT Device Management Break free of appliance management Hitless upgrades and updates are managed by the service Increase Agility Automated security, Fully API integrated Continuous awareness and automated remediation of cloud risks Consistent Security Seamless integration across regions Discover across regions, unified policies Dynamic security follows the apps across clouds Automate Security Operations No scripts, No agents, No sizing Resiliency and Scalability are baked-in
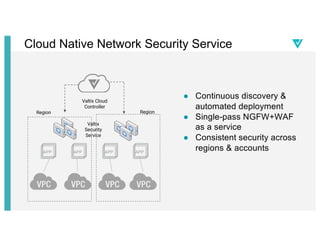
- 26. Cloud Native Network Security Service â Continuous discovery & automated deployment â Single-pass NGFW+WAF as a service â Consistent security across regions & accounts Valtix Cloud Controller Region Region Valtix Security Service
- 27. Valtix Cloud Security Service Solution â Cloud security requires a new mindset â Unbox your network security â Ship policies NOT packets Where third-party network security controls are used, favor cloud-native approaches. Vendors that simply take their on-premises physical appliance into a virtual appliance donât provide a cloud-native experience.Cloud-native security offerings offer built-in automated resiliency, scale- out architectures, ease of insertion into the programmable network fabric of the cloud provider and support for transit virtual private cloud (VPC)-like constructs. â â Neil MacDonald Distinguished VP Analyst, Gartner
- 28. 29 RMove fast Stay secureAND Achieving Now
- 30. Q&A
- 31. THANK YOU 3 2