Hard Disk Data Acquisition
Download as PPTX, PDF3 likes987 views
The document discusses various aspects of hard disk data acquisition for digital forensics purposes. It covers the general acquisition procedure, data acquisition layers, requirements for acquisition tools and hardware/software write blockers, and considerations around accessing disks directly versus through BIOS, dead versus live acquisitions, hidden areas like HPA and DCO, and writing output data and image file formats.
1 of 22
Downloaded 14 times



















Recommended
Computer forensics toolkit



Computer forensics toolkitMilap Oza
?
Computer forensics is the scientific process of preserving, identifying, extracting, and interpreting data from computer systems, networks, wireless communications, and storage devices in a way that is legally admissible. It involves using special tools to conduct a forensic examination of devices, networks, internet activities, and images in order to discover potential digital evidence. Common computer forensic tools are used to recover deleted files, analyze financial and communications records, and investigate crimes like fraud, identity theft, and child pornography.Digital Forensics



Digital ForensicsNicholas Davis
?
Digital forensics involves analyzing digital artifacts like computers, storage devices, and network traffic as potential legal evidence. The process includes preparing investigators, collecting evidence while maintaining a chain of custody, examining and analyzing the data, and reporting the results. Key steps are imaging systems to obtain an exact duplicate without altering the original, recovering volatile data from memory, and using tools like EnCase and The Sleuth Kit to manually review and search the evidence for relevant information.data hiding techniques.ppt



data hiding techniques.pptMuzamil Amin
?
The document discusses various data hiding techniques used to conceal information, including:
1) Manipulating file attributes like filenames, extensions, and hidden properties.
2) Hiding partitions by deleting references in disk editors or using partition tools.
3) Marking disk clusters as "bad" to hide data in free space.
4) Bit-shifting to alter byte values and make files look like executable code.
5) Using steganography tools to hide data within image or text files by inserting digital watermarks.Lecture 9 and 10 comp forensics 09 10-18 file system



Lecture 9 and 10 comp forensics 09 10-18 file systemAlchemist095
?
This document discusses various topics related to computer forensics, including data acquisition, digital evidence storage formats, acquisition methods, using acquisition tools, validating data acquisition, RAID acquisition methods, remote network acquisition tools, processing crime scenes, and analyzing evidence. It provides details on different types of data acquisition, such as static and live acquisition. It also describes best practices for securing evidence, gathering evidence, and analyzing evidence as part of a computer forensics investigation.File System FAT And NTFS



File System FAT And NTFSInocentshuja Ahmad
?
The document discusses different file systems including FAT, FAT12, FAT16, FAT32, and NTFS. FAT (File Allocation Table) was created by Microsoft in 1977 and tracks pieces of files that may be fragmented across disks. FAT8 supported 8-inch floppies. FAT12 was used for floppy disks. FAT16 supported drives up to 16GB. FAT32 supports drives up to 2TB. NTFS (New Technology File System) was introduced in 1993 and supports features like large partition and file sizes, security, reliability, and compression.Disk Management.pdf



Disk Management.pdfRandyGaray
?
This document provides an overview of disk management. It begins by explaining the difference between discs and disks, with discs referring to optical media like CDs and DVDs that are removable, while disks refer to magnetic hard drives and drives that are not removable. It then covers disk terminology like cylinders, tracks, and sectors. Next, it describes disk structure including platters, tracks, read/write heads, and cylinders. The document discusses disk scheduling algorithms like first-come first-served, shortest seek time first, and scan. Finally, it lists some common disk management operations and tools.Virtual Machine Forensics



Virtual Machine Forensicsprimeteacher32
?
Virtual machine forensics is an important topic for investigators. There are two types of hypervisors - Type 1 loads directly on hardware while Type 2 runs on an existing OS. The most common Type 2 hypervisors are Parallels, KVM, VirtualBox and VMware which allow virtual machines to run. Investigators must image both host systems and VMs, checking for VM files, network adapters and USB attachments to uncover any virtual machines. Live acquisitions of running VMs are also important to capture snapshot data.Cell Phone and Mobile Devices Forensics



Cell Phone and Mobile Devices ForensicsArthyR3
?
This document provides an overview of cell phone and mobile device forensics. It discusses the types of information commonly stored on mobile devices, challenges in investigating them due to varying storage schemes and rapidly changing models. It covers acquiring devices, assessing what data can be retrieved from internal memory, SIM cards, external memory, and servers. Tools for mobile forensics like SIM card readers and software from companies like Paraben and DataPilot are also summarized. The document provides high-level information on understanding and conducting mobile device forensics investigations.CNIT 121: 8 Forensic Duplication



CNIT 121: 8 Forensic DuplicationSam Bowne
?
This document discusses various types of forensic duplication including simple duplication that copies selected data versus forensic duplication that retains every bit on the source drive including deleted files. It covers requirements for forensic duplication including the need to act as admissible evidence. It describes different forensic image formats including complete disk, partition, and logical images and details scenarios for each type. Key aspects of forensic duplication covered include recovering deleted files, non-standard data types, ensuring image integrity with hashes, and traditional duplication methods like using hardware write blockers or live DVDs.L6 Digital Forensic Investigation Tools.pptx



L6 Digital Forensic Investigation Tools.pptxBhupeshkumar Nanhe
?
Digital forensic is defined as the process of preserving, identifying, extracting, and documenting computer evidence for use in a court of law. It involves identifying evidence stored on devices, preserving the data without alteration, analyzing the evidence using forensic tools, and documenting the findings. The key steps of the digital forensic process are identification, preservation, analysis, documentation, and presentation. Common types of digital forensics include disk, network, wireless, database, malware, email, memory, and mobile device forensics. Forensic tools used in the process include those for forensic imaging to make bit-by-bit copies of storage devices and data recovery tools to extract data from damaged sources.raid technology



raid technologyMangukiya Maulik
?
The document discusses different RAID levels for storing data across multiple disks. It provides details on RAID levels 0 through 6, including the minimum number of drives required, how data and parity are distributed, and example diagrams. The benefits of RAID include preventing data loss from disk failures through techniques like mirroring, striping, and parity.Data Acquisition



Data Acquisitionprimeteacher32
?
Digital evidence acquisitions can be stored in raw, proprietary, or Advanced Forensics Format (AFF). The document discusses various acquisition methods and tools for disk-to-image, disk-to-disk, logical, and sparse acquisitions. It emphasizes the importance of validation, contingency planning, and minimizing alteration of evidence during the acquisition process. Special considerations are given for acquiring data from RAID systems and using Linux tools or remote network tools.Network forensics and investigating logs



Network forensics and investigating logsanilinvns
?
The document discusses various aspects of network forensics and investigating logs. It covers analyzing log files as evidence, maintaining accurate timekeeping across systems, configuring extended logging in IIS servers, and the importance of log file accuracy and authenticity when using logs as evidence in an investigation.01 Computer Forensics Fundamentals - Notes



01 Computer Forensics Fundamentals - NotesKranthi
?
Computer forensics is the process of examining computer systems, storage devices, and digital evidence to recover data for legal cases. It involves collecting, preserving, analyzing and presenting computer-related evidence without altering it. Computer evidence can be useful in criminal, civil and employment cases. Computer forensics experts follow strict methodologies to carefully handle systems and extract potential evidence while maintaining data integrity and chain of custody. Their goal is to discover all relevant files, including deleted files, and analyze artifacts to understand attempts to hide, delete or encrypt information.Linux forensics



Linux forensicsSantosh Khadsare
?
Linux is well-suited for forensic investigations due to its free and open-source tools, flexible environment, and ability to access low-level interfaces. However, its tools are more complicated to use than commercial packages and typically lack technical support. Linux distributions use a directory tree with essential directories like /bin, /etc, /home, and /var. Important commands provide information on processes, network connections, and disk usage. The Linux boot process involves the BIOS, boot loader, kernel initialization, and starting of processes at designated run levels.File system



File systemHarleen Johal
?
The document discusses file systems and their components. It describes how files are organized logically and mapped to physical storage. It covers key file system concepts like directories, file allocation schemes, file attributes, and file operations. It also summarizes common file systems like FAT, FAT32, and NTFS and compares their features such as supported drive sizes, cluster sizes, and compatibility with different operating systems.Introduction to forensic imaging



Introduction to forensic imagingMarco Alamanni
?
This is a draft presentation of a video lesson taken from the course "Digital forensics with Kali Linux" published by Packt Publishing in May 2017: https://www.packtpub.com/networking-and-servers/digital-forensics-kali-linux
This presentation introduces the fundamentals of the forensic image acquisition process, explaining concepts like hardware and software write blocking, the physical and logical structure of hard disks and the different forensic image formats.Chapter 16



Chapter 16Ali Broumandnia
?
This document discusses managing and monitoring the storage infrastructure. It describes monitoring components like hosts, networks, and storage arrays to ensure accessibility, capacity, performance, and security. Key storage management activities are also outlined, such as availability, capacity, performance, and security management. Emerging standards for storage management are presented, along with challenges in monitoring today's complex storage environments and ideal solutions.Autopsy Digital forensics tool



Autopsy Digital forensics toolSreekanth Narendran
?
The document introduces Autopsy, an open source digital forensics platform. It provides an overview of Autopsy's features which allow users to efficiently analyze hard drives and smartphones through a graphical interface. Key capabilities include timeline analysis, keyword searching, web and file system artifact extraction, and support for common file systems. The document includes screenshots and references for additional information on Autopsy's functions and use in digital investigations.Operating System Forensics



Operating System ForensicsArunJS5
?
Ultimately, in a forensic examination, we are investigating the action of a Person
Almost every event or action on a system is the result of a user either doing something
Many events change the state of the Operating System (OS)
OS Forensics helps understand how system changes correlate to events resulting from the action of somebody in the real worldIntrusion detection system 



Intrusion detection system gaurav koriya
?
hey guys here comes my new implementation of my learning i.e the IDS a concept of network security go through it and add your valuable commentsMobile Forensics



Mobile Forensicsprimeteacher32
?
This document discusses mobile device forensics. It explains that mobile devices store a variety of personal information, including calls, texts, emails, photos and more. It also outlines the challenges of investigating mobile devices and describes the components of mobile devices like the IMEI, SIM card, and memory. The document provides details on acquiring data from mobile devices, including identifying the device, isolating it to prevent remote wiping, and extracting data from internal memory, SIM cards and external storage.E mail Investigation



E mail InvestigationDr Raghu Khimani
?
Introduction to Email, how email works, components of email, email investigation, time stamping, forensic examination of email.Memory forensics.pptx



Memory forensics.pptx9905234521
?
Memory forensics is a technique used in cyber investigations that allows analysts to capture the current state of a system's memory as an image file. This memory dump can then be analyzed offline to retrieve important artifacts like running processes, open network connections, and recently used files. It is useful because memory stores current system state information that may not be found through other forensic methods. Several challenges in memory forensics include ensuring the integrity of captured memory images and keeping analysis tools compatible with changing operating system structures.Initial Response and Forensic Duplication 



Initial Response and Forensic Duplication Jyothishmathi Institute of Technology and Science Karimnagar
?
UNIT-II Initial Response and forensic duplication, Initial Response & Volatile Data Collection from Windows system -Initial Response & Volatile Data Collection from Unix system ĻC Forensic Duplication: Forensic duplication: Forensic Duplicates as Admissible Evidence, Forensic Duplication Tool Requirements, Creating a Forensic. Duplicate/Qualified Forensic Duplicate of a Hard Drive File Carving



File CarvingAakarsh Raj
?
File carving is a process used in computer forensics to recover deleted files from unallocated space by analyzing fragments and reassembling them based on file headers and footers without relying on file system metadata. It works by searching raw data block by block for header and footer values to extract files. Common file carving tools include Foremost, Scalpel, and Photorec. New carving techniques like SmartCarving can recover even fragmented files through preprocessing, classifying fragments, and reassembling them in the proper sequence.HDD Partition



HDD PartitionAMZAD KHAN
?
A partition divides a hard drive into logical sections for storing files and installing operating systems. There are three types of partitions: primary, extended, and logical. A primary partition can host an operating system, while an extended partition contains logical drives. The master boot record (MBR) stores information on partition locations and boots the system, but is limited to 4 primary partitions under 2.2TB each. The GUID partition table (GPT) replaces MBR and supports over 18 exabytes per partition. GPT uses a protective MBR for compatibility with older systems.Lec1.ppt



Lec1.pptMUHAMMADALIASGHAR10
?
System programming focuses on operating at a low level to access hardware directly and optimize for efficiency. It allows writing parts of a program in assembly language and provides little abstraction from the hardware. Interrupt-driven I/O improves on programmed I/O by allowing devices to notify the CPU when an operation is complete rather than having the CPU continuously check. Direct memory access further optimizes I/O by allowing data transfers to bypass the CPU. Memory management in protected mode uses descriptor tables to define memory segments and privilege levels.Motherboard.pptx



Motherboard.pptxjulitapelovello
?
The document discusses the basic input/output system (BIOS) and its functions. It describes BIOS as firmware that acts as an intermediary between the operating system and computer hardware. When a computer is powered on, the BIOS performs tasks like testing hardware and loading the operating system. It identifies devices, configures the system, and allows data transfer between components. The BIOS can be accessed through the BIOS setup utility to configure hardware settings.More Related Content
What's hot (20)
Cell Phone and Mobile Devices Forensics



Cell Phone and Mobile Devices ForensicsArthyR3
?
This document provides an overview of cell phone and mobile device forensics. It discusses the types of information commonly stored on mobile devices, challenges in investigating them due to varying storage schemes and rapidly changing models. It covers acquiring devices, assessing what data can be retrieved from internal memory, SIM cards, external memory, and servers. Tools for mobile forensics like SIM card readers and software from companies like Paraben and DataPilot are also summarized. The document provides high-level information on understanding and conducting mobile device forensics investigations.CNIT 121: 8 Forensic Duplication



CNIT 121: 8 Forensic DuplicationSam Bowne
?
This document discusses various types of forensic duplication including simple duplication that copies selected data versus forensic duplication that retains every bit on the source drive including deleted files. It covers requirements for forensic duplication including the need to act as admissible evidence. It describes different forensic image formats including complete disk, partition, and logical images and details scenarios for each type. Key aspects of forensic duplication covered include recovering deleted files, non-standard data types, ensuring image integrity with hashes, and traditional duplication methods like using hardware write blockers or live DVDs.L6 Digital Forensic Investigation Tools.pptx



L6 Digital Forensic Investigation Tools.pptxBhupeshkumar Nanhe
?
Digital forensic is defined as the process of preserving, identifying, extracting, and documenting computer evidence for use in a court of law. It involves identifying evidence stored on devices, preserving the data without alteration, analyzing the evidence using forensic tools, and documenting the findings. The key steps of the digital forensic process are identification, preservation, analysis, documentation, and presentation. Common types of digital forensics include disk, network, wireless, database, malware, email, memory, and mobile device forensics. Forensic tools used in the process include those for forensic imaging to make bit-by-bit copies of storage devices and data recovery tools to extract data from damaged sources.raid technology



raid technologyMangukiya Maulik
?
The document discusses different RAID levels for storing data across multiple disks. It provides details on RAID levels 0 through 6, including the minimum number of drives required, how data and parity are distributed, and example diagrams. The benefits of RAID include preventing data loss from disk failures through techniques like mirroring, striping, and parity.Data Acquisition



Data Acquisitionprimeteacher32
?
Digital evidence acquisitions can be stored in raw, proprietary, or Advanced Forensics Format (AFF). The document discusses various acquisition methods and tools for disk-to-image, disk-to-disk, logical, and sparse acquisitions. It emphasizes the importance of validation, contingency planning, and minimizing alteration of evidence during the acquisition process. Special considerations are given for acquiring data from RAID systems and using Linux tools or remote network tools.Network forensics and investigating logs



Network forensics and investigating logsanilinvns
?
The document discusses various aspects of network forensics and investigating logs. It covers analyzing log files as evidence, maintaining accurate timekeeping across systems, configuring extended logging in IIS servers, and the importance of log file accuracy and authenticity when using logs as evidence in an investigation.01 Computer Forensics Fundamentals - Notes



01 Computer Forensics Fundamentals - NotesKranthi
?
Computer forensics is the process of examining computer systems, storage devices, and digital evidence to recover data for legal cases. It involves collecting, preserving, analyzing and presenting computer-related evidence without altering it. Computer evidence can be useful in criminal, civil and employment cases. Computer forensics experts follow strict methodologies to carefully handle systems and extract potential evidence while maintaining data integrity and chain of custody. Their goal is to discover all relevant files, including deleted files, and analyze artifacts to understand attempts to hide, delete or encrypt information.Linux forensics



Linux forensicsSantosh Khadsare
?
Linux is well-suited for forensic investigations due to its free and open-source tools, flexible environment, and ability to access low-level interfaces. However, its tools are more complicated to use than commercial packages and typically lack technical support. Linux distributions use a directory tree with essential directories like /bin, /etc, /home, and /var. Important commands provide information on processes, network connections, and disk usage. The Linux boot process involves the BIOS, boot loader, kernel initialization, and starting of processes at designated run levels.File system



File systemHarleen Johal
?
The document discusses file systems and their components. It describes how files are organized logically and mapped to physical storage. It covers key file system concepts like directories, file allocation schemes, file attributes, and file operations. It also summarizes common file systems like FAT, FAT32, and NTFS and compares their features such as supported drive sizes, cluster sizes, and compatibility with different operating systems.Introduction to forensic imaging



Introduction to forensic imagingMarco Alamanni
?
This is a draft presentation of a video lesson taken from the course "Digital forensics with Kali Linux" published by Packt Publishing in May 2017: https://www.packtpub.com/networking-and-servers/digital-forensics-kali-linux
This presentation introduces the fundamentals of the forensic image acquisition process, explaining concepts like hardware and software write blocking, the physical and logical structure of hard disks and the different forensic image formats.Chapter 16



Chapter 16Ali Broumandnia
?
This document discusses managing and monitoring the storage infrastructure. It describes monitoring components like hosts, networks, and storage arrays to ensure accessibility, capacity, performance, and security. Key storage management activities are also outlined, such as availability, capacity, performance, and security management. Emerging standards for storage management are presented, along with challenges in monitoring today's complex storage environments and ideal solutions.Autopsy Digital forensics tool



Autopsy Digital forensics toolSreekanth Narendran
?
The document introduces Autopsy, an open source digital forensics platform. It provides an overview of Autopsy's features which allow users to efficiently analyze hard drives and smartphones through a graphical interface. Key capabilities include timeline analysis, keyword searching, web and file system artifact extraction, and support for common file systems. The document includes screenshots and references for additional information on Autopsy's functions and use in digital investigations.Operating System Forensics



Operating System ForensicsArunJS5
?
Ultimately, in a forensic examination, we are investigating the action of a Person
Almost every event or action on a system is the result of a user either doing something
Many events change the state of the Operating System (OS)
OS Forensics helps understand how system changes correlate to events resulting from the action of somebody in the real worldIntrusion detection system 



Intrusion detection system gaurav koriya
?
hey guys here comes my new implementation of my learning i.e the IDS a concept of network security go through it and add your valuable commentsMobile Forensics



Mobile Forensicsprimeteacher32
?
This document discusses mobile device forensics. It explains that mobile devices store a variety of personal information, including calls, texts, emails, photos and more. It also outlines the challenges of investigating mobile devices and describes the components of mobile devices like the IMEI, SIM card, and memory. The document provides details on acquiring data from mobile devices, including identifying the device, isolating it to prevent remote wiping, and extracting data from internal memory, SIM cards and external storage.E mail Investigation



E mail InvestigationDr Raghu Khimani
?
Introduction to Email, how email works, components of email, email investigation, time stamping, forensic examination of email.Memory forensics.pptx



Memory forensics.pptx9905234521
?
Memory forensics is a technique used in cyber investigations that allows analysts to capture the current state of a system's memory as an image file. This memory dump can then be analyzed offline to retrieve important artifacts like running processes, open network connections, and recently used files. It is useful because memory stores current system state information that may not be found through other forensic methods. Several challenges in memory forensics include ensuring the integrity of captured memory images and keeping analysis tools compatible with changing operating system structures.Initial Response and Forensic Duplication 



Initial Response and Forensic Duplication Jyothishmathi Institute of Technology and Science Karimnagar
?
UNIT-II Initial Response and forensic duplication, Initial Response & Volatile Data Collection from Windows system -Initial Response & Volatile Data Collection from Unix system ĻC Forensic Duplication: Forensic duplication: Forensic Duplicates as Admissible Evidence, Forensic Duplication Tool Requirements, Creating a Forensic. Duplicate/Qualified Forensic Duplicate of a Hard Drive File Carving



File CarvingAakarsh Raj
?
File carving is a process used in computer forensics to recover deleted files from unallocated space by analyzing fragments and reassembling them based on file headers and footers without relying on file system metadata. It works by searching raw data block by block for header and footer values to extract files. Common file carving tools include Foremost, Scalpel, and Photorec. New carving techniques like SmartCarving can recover even fragmented files through preprocessing, classifying fragments, and reassembling them in the proper sequence.HDD Partition



HDD PartitionAMZAD KHAN
?
A partition divides a hard drive into logical sections for storing files and installing operating systems. There are three types of partitions: primary, extended, and logical. A primary partition can host an operating system, while an extended partition contains logical drives. The master boot record (MBR) stores information on partition locations and boots the system, but is limited to 4 primary partitions under 2.2TB each. The GUID partition table (GPT) replaces MBR and supports over 18 exabytes per partition. GPT uses a protective MBR for compatibility with older systems.Initial Response and Forensic Duplication 



Initial Response and Forensic Duplication Jyothishmathi Institute of Technology and Science Karimnagar
?
Similar to Hard Disk Data Acquisition (20)
Lec1.ppt



Lec1.pptMUHAMMADALIASGHAR10
?
System programming focuses on operating at a low level to access hardware directly and optimize for efficiency. It allows writing parts of a program in assembly language and provides little abstraction from the hardware. Interrupt-driven I/O improves on programmed I/O by allowing devices to notify the CPU when an operation is complete rather than having the CPU continuously check. Direct memory access further optimizes I/O by allowing data transfers to bypass the CPU. Memory management in protected mode uses descriptor tables to define memory segments and privilege levels.Motherboard.pptx



Motherboard.pptxjulitapelovello
?
The document discusses the basic input/output system (BIOS) and its functions. It describes BIOS as firmware that acts as an intermediary between the operating system and computer hardware. When a computer is powered on, the BIOS performs tasks like testing hardware and loading the operating system. It identifies devices, configures the system, and allows data transfer between components. The BIOS can be accessed through the BIOS setup utility to configure hardware settings.Device drivers by prabu m



Device drivers by prabu mPrabu Mariyappan
?
The document discusses user mode vs kernel mode in an operating system. It explains that applications run in user mode for isolation, while core OS components run in kernel mode with complete hardware access. If a kernel mode driver crashes, it can cause an OS crash. The document also discusses how new devices are installed, including how drivers are selected to match a device's hardware ID. It describes the components of a typical driver package, including driver files, installation files, and catalogs. It explains the role of the BIOS in supporting booting from USB devices by establishing the USB protocol.5120224.ppt



5120224.pptdedanndege
?
This document provides an overview of input/output (I/O) hardware and software principles. It discusses various I/O devices including disks, clocks, and terminals. It describes I/O hardware components like controllers and memory-mapped I/O. It outlines I/O software layers including interrupt handlers, device drivers, operating system I/O functions, and user-level I/O. It also provides details on specific I/O topics such as disk formatting, error handling, scheduling algorithms, and terminal input/output software.Windows optimization and customization



Windows optimization and customizationHiren Mayani
?
This document provides tips and tricks for optimizing computer performance. It discusses components like the processor, RAM, hard drive, display, and graphics card. It recommends upgrading RAM to at least 4GB and getting an SSD for faster access times. Other tips include overclocking the processor for better performance, clearing temporary files regularly using CCleaner, and configuring the BIOS. The document also discusses creating a bootable USB, sharing an internet connection, and making custom boot screens.Managing Hardware Devices.pdf



Managing Hardware Devices.pdfSolomonAnab1
?
This document discusses managing hardware devices in a Windows Server 2003 environment. It covers understanding device drivers, using Device Manager to manage drivers and hardware resources, resolving resource conflicts, optimizing processor and memory usage, and configuring driver signing options and virtual memory settings. Activities guide exploring these concepts, like installing devices, viewing resource settings, and configuring driver signing levels and virtual memory.Protecting Hosts



Protecting Hostsprimeteacher32
?
An attacker with physical access to a computer or network device can easily compromise security by booting from unauthorized media like LiveCDs, USB drives, or DVDs containing hacking tools. These bootable devices allow bypassing of firewalls and access to the hard drive contents. Drive imaging software on such media poses a big risk as it can copy the entire hard drive contents without leaving a trace. Disabling auto-run features and removable media like USB drives can help reduce these risks from physical access. Encryption and centralized file storage also make drives less valuable if imaged.Intro to digital forensic imaging



Intro to digital forensic imagingDetectalix
?
Introduction to the basic concepts of digital forensic image acquisition, hardware/software write-blocking techniques and forensic image formats
*
*
*
Subscribe to the YouTube channel:
https://youtube.com/channel/UC4bvx2ub2h7F_FrZKF9QGIgIGCSE_ICT_Chapter 1.pptx



IGCSE_ICT_Chapter 1.pptxFatimaWaheed30
?
The document provides an overview of hardware components of a computer system including internal components like the CPU, motherboard, and memory as well as external components like input, output, and storage devices. It also discusses system and application software. The summary discusses the roles of the CPU, motherboard, and different types of memory in a computer system.OS-20210426203801.ppt



OS-20210426203801.pptLadyChristianneBucsi
?
The document provides an introduction to operating systems (OS). It discusses what an OS is, its key functions such as process management, memory management, file management, and device management. It also covers the evolution of OS from batch systems to time-sharing, multiprocessing, distributed, and network OS. Popular types of OS discussed include UNIX, Windows, Linux, and network OS.OS-20210426203801.ppt



OS-20210426203801.pptROLANDOMORALES28
?
The document provides an introduction to operating systems (OS) and describes some of their key functions. It discusses what an OS is, popular OS types, and basics of UNIX/Windows. Some key points made include:
- An OS acts as an intermediary between the user and computer hardware, executing programs and making hardware resources available to users.
- OS functions include process management, memory management, file management, and I/O management like controlling hardware devices.
- When a computer boots up, the BIOS initializes basic hardware then loads the bootloader from disk which loads the OS kernel into memory to take over control of the system.OS-20210426203801.ppt



OS-20210426203801.pptManojKumar409578
?
The document provides an introduction to operating systems (OS). It discusses key functions of an OS including process management, memory management, file management, device management, security and protection, and user interface mechanisms. It also covers the history of OS, from early batch systems to modern distributed, network, and real-time OS. Popular OS types like batch, multiprogramming, time-sharing, multiprocessing, distributed and network OS are explained.OS full chapter.ppt



OS full chapter.pptKamalishwaranS
?
The document provides an introduction to operating systems (OS) and describes some of their key functions. It discusses what an OS is, popular OS types, and basics of UNIX/Windows. Some key points made include:
- An OS acts as an intermediary between the user and computer hardware, executing programs and making hardware resources available to users.
- OS functions include process management, memory management, file management, and I/O management like controlling hardware devices.
- When a computer boots up, the BIOS initializes basic hardware then loads the bootloader from disk which loads the OS kernel into memory to take over control of the system.Windows 1Fundaments.ppt



Windows 1Fundaments.pptkarthikvcyber
?
The document provides an introduction to operating systems (OS). It discusses key functions of an OS including process management, memory management, file management, device management, security and protection, and user interface mechanisms. It also covers the history of OS, from early batch systems to modern distributed, network, and real-time OS. Popular OS types like batch, multiprogramming, time-sharing, multiprocessing, distributed and network OS are explained.OS-20210426203801 introduction to os.ppt



OS-20210426203801 introduction to os.pptnaghamallella
?
The document provides an introduction to operating systems (OS) and describes some of their key functions. It discusses what an OS is, popular OS types, and basics of UNIX/Windows. Some key points made include:
- An OS acts as an intermediary between the user and computer hardware, executing programs and making hardware resources available to users.
- OS functions include process management, memory management, file management, and I/O management like controlling hardware devices.
- When a computer boots up, the BIOS initializes basic hardware then loads the bootloader from disk which loads the OS kernel into memory to take over control of the system.Recently uploaded (20)
Field Device Management Market Report 2030 - TechSci Research



Field Device Management Market Report 2030 - TechSci ResearchVipin Mishra
?
The Global Field Device Management (FDM) Market is expected to experience significant growth in the forecast period from 2026 to 2030, driven by the integration of advanced technologies aimed at improving industrial operations.
? According to TechSci Research, the Global Field Device Management Market was valued at USD 1,506.34 million in 2023 and is anticipated to grow at a CAGR of 6.72% through 2030. FDM plays a vital role in the centralized oversight and optimization of industrial field devices, including sensors, actuators, and controllers.
Key tasks managed under FDM include:
Configuration
Monitoring
Diagnostics
Maintenance
Performance optimization
FDM solutions offer a comprehensive platform for real-time data collection, analysis, and decision-making, enabling:
Proactive maintenance
Predictive analytics
Remote monitoring
By streamlining operations and ensuring compliance, FDM enhances operational efficiency, reduces downtime, and improves asset reliability, ultimately leading to greater performance in industrial processes. FDMĄŊs emphasis on predictive maintenance is particularly important in ensuring the long-term sustainability and success of industrial operations.
For more information, explore the full report: https://shorturl.at/EJnzR
Major companies operating in Global?Field Device Management Market are:
General Electric Co
Siemens AG
ABB Ltd
Emerson Electric Co
Aveva Group Ltd
Schneider Electric SE
STMicroelectronics Inc
Techno Systems Inc
Semiconductor Components Industries LLC
International Business Machines Corporation (IBM)
#FieldDeviceManagement #IndustrialAutomation #PredictiveMaintenance #TechInnovation #IndustrialEfficiency #RemoteMonitoring #TechAdvancements #MarketGrowth #OperationalExcellence #SensorsAndActuatorsUiPath Automation Developer Associate Training Series 2025 - Session 1



UiPath Automation Developer Associate Training Series 2025 - Session 1DianaGray10
?
Welcome to UiPath Automation Developer Associate Training Series 2025 - Session 1.
In this session, we will cover the following topics:
Introduction to RPA & UiPath Studio
Overview of RPA and its applications
Introduction to UiPath Studio
Variables & Data Types
Control Flows
You are requested to finish the following self-paced training for this session:
Variables, Constants and Arguments in Studio 2 modules - 1h 30m - https://academy.uipath.com/courses/variables-constants-and-arguments-in-studio
Control Flow in Studio 2 modules - 2h 15m - https:/academy.uipath.com/courses/control-flow-in-studio
?? For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. UiPath Document Understanding - Generative AI and Active learning capabilities



UiPath Document Understanding - Generative AI and Active learning capabilitiesDianaGray10
?
This session focus on Generative AI features and Active learning modern experience with Document understanding.
Topics Covered:
Overview of Document Understanding
How Generative Annotation works?
What is Generative Classification?
How to use Generative Extraction activities?
What is Generative Validation?
How Active learning modern experience accelerate model training?
Q/A
? If you have any questions or feedback, please refer to the "Women in Automation 2025" dedicated Forum thread. You can find there extra details and updates. BoxLang JVM Language : The Future is Dynamic



BoxLang JVM Language : The Future is DynamicOrtus Solutions, Corp
?
Just like life, our code must evolve to meet the demands of an ever-changing world. Adaptability is key in developing for the web, tablets, APIs, or serverless applications. Multi-runtime development is the future, and that future is dynamic. Enter BoxLang: Dynamic. Modular. Productive. (www.boxlang.io)
BoxLang transforms development with its dynamic design, enabling developers to write expressive, functional code effortlessly. Its modular architecture ensures flexibility, allowing easy integration into your existing ecosystems.
Interoperability at Its Core
BoxLang boasts 100% interoperability with Java, seamlessly blending traditional and modern development practices. This opens up new possibilities for innovation and collaboration.
Multi-Runtime Versatility
From a compact 6MB OS binary to running on our pure Java web server, CommandBox, Jakarta EE, AWS Lambda, Microsoft Functions, WebAssembly, Android, and more, BoxLang is designed to adapt to any runtime environment. BoxLang combines modern features from CFML, Node, Ruby, Kotlin, Java, and Clojure with the familiarity of Java bytecode compilation. This makes it the go-to language for developers looking to the future while building a solid foundation.
Empowering Creativity with IDE Tools
Unlock your creative potential with powerful IDE tools designed for BoxLang, offering an intuitive development experience that streamlines your workflow. Join us as we redefine JVM development and step into the era of BoxLang. Welcome to the future.
Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]Jonathan Bowen
?
Alan Turing arguably wrote the first paper on formal methods 75 years ago. Since then, there have been claims and counterclaims about formal methods. Tool development has been slow but aided by MooreĄŊs Law with the increasing power of computers. Although formal methods are not widespread in practical usage at a heavyweight level, their influence as crept into software engineering practice to the extent that they are no longer necessarily called formal methods in their use. In addition, in areas where safety and security are important, with the increasing use of computers in such applications, formal methods are a viable way to improve the reliability of such software-based systems. Their use in hardware where a mistake can be very costly is also important. This talk explores the journey of formal methods to the present day and speculates on future directions.
World Information Architecture Day 2025 - UX at a Crossroads



World Information Architecture Day 2025 - UX at a CrossroadsJoshua Randall
?
User Experience stands at a crossroads: will we live up to our potential to design a better world? or will we be co-opted by Ą°product managementĄą or another business buzzword?
Looking backwards, this talk will show how UX has repeatedly failed to create a better world, drawing on industry data from Nielsen Norman Group, Baymard, MeasuringU, WebAIM, and others.
Looking forwards, this talk will argue that UX must resist hype, say no more often and collaborate less often (you read that right), and become a true profession ĄŠ in order to be able to design a better world.The Future of Repair: Transparent and Incremental by Botond De?nes



The Future of Repair: Transparent and Incremental by Botond De?nesScyllaDB
?
Regularly run repairs are essential to keep clusters healthy, yet having a good repair schedule is more challenging than it should be. Repairs often take a long time, preventing running them often. This has an impact on data consistency and also limits the usefulness of the new repair based tombstone garbage collection. We want to address these challenges by making repairs incremental and allowing for automatic repair scheduling, without relying on external tools.Computational Photography: How Technology is Changing Way We Capture the World



Computational Photography: How Technology is Changing Way We Capture the WorldHusseinMalikMammadli
?
? Computational Photography (Computer Vision/Image): How Technology is Changing the Way We Capture the World
He? dĻđ?ĻđnmĻđsĻđnĻđzmĻđ, mĻđasir smartfonlar v? kameralar nec? bu q?d?r g?z?l g?rĻđntĻđl?r yarad?r? Bunun sirri Computational Fotoqrafiyas?nda(Computer Vision/Imaging) gizlidirĄŠ??kill?ri ??km? v? emal etm? Ļđsulumuzu t?kmill??dir?n, kompĻđter elmi il? fotoqrafiyan?n inqilabi birl??m?si.L01 Introduction to Nanoindentation - What is hardness



L01 Introduction to Nanoindentation - What is hardnessRostislavDaniel
?
Introduction to NanoindentationSMART SENTRY CYBER THREAT INTELLIGENCE IN IIOT



SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTTanmaiArni
?
SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTMIND Revenue Release Quarter 4 2024 - Finacial Presentation



MIND Revenue Release Quarter 4 2024 - Finacial PresentationMIND CTI
?
MIND Revenue Release Quarter 4 2024 - Finacial PresentationHow Discord Indexes Trillions of Messages: Scaling Search Infrastructure by V...



How Discord Indexes Trillions of Messages: Scaling Search Infrastructure by V...ScyllaDB
?
This talk shares how Discord scaled their message search infrastructure using Rust, Kubernetes, and a multi-cluster Elasticsearch architecture to achieve better performance, operability, and reliability, while also enabling new search features for Discord users.DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (Æ―É―Ōã)



DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (Æ―É―Ōã)Tsuyoshi Hirayama
?
DAO UTokyo 2025
|ūĐīóŅ§ĮéóŅ§h ĨÖĨíĨÃĨŊĨÁĨ§Đ`ĨóŅÐūŋĨĪĨËĨ·ĨĒĨÆĨĢĨÖ
https://utbciii.com/2024/12/12/announcing-dao-utokyo-2025-conference/
Session 1 :DLT mass adoption
IBM Tsuyoshi Hirayama (Æ―É―Ōã)UiPath Agentic Automation Capabilities and Opportunities



UiPath Agentic Automation Capabilities and OpportunitiesDianaGray10
?
Learn what UiPath Agentic Automation capabilities are and how you can empower your agents with dynamic decision making. In this session we will cover these topics:
What do we mean by Agents
Components of Agents
Agentic Automation capabilities
What Agentic automation delivers and AI Tools
Identifying Agent opportunities
? If you have any questions or feedback, please refer to the "Women in Automation 2025" dedicated Forum thread. You can find there extra details and updates.Build with AI on Google Cloud Session #4



Build with AI on Google Cloud Session #4Margaret Maynard-Reid
?
This is session #4 of the 5-session online study series with Google Cloud, where we take you onto the journey learning generative AI. YouĄŊll explore the dynamic landscape of Generative AI, gaining both theoretical insights and practical know-how of Google Cloud GenAI tools such as Gemini, Vertex AI, AI agents and Imagen 3. THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIA



THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIASrivaanchi Nathan
?
This business intelligence report, "The Big Ten Biopharmaceutical MNCs: Global Capability Centers in India", provides an in-depth analysis of the operations and contributions of the Global Capability Centers (GCCs) of ten leading biopharmaceutical multinational corporations in India. The report covers AstraZeneca, Bayer, Bristol Myers Squibb, GlaxoSmithKline (GSK), Novartis, Sanofi, Roche, Pfizer, Novo Nordisk, and Eli Lilly. In this report each company's GCC is profiled with details on location, workforce size, investment, and the strategic roles these centers play in global business operations, research and development, and information technology and digital innovation.Future-Proof Your Career with AI Options



Future-Proof Your Career with AI OptionsDianaGray10
?
Learn about the difference between automation, AI and agentic and ways you can harness these to further your career. In this session you will learn:
Introduction to automation, AI, agentic
Trends in the marketplace
Take advantage of UiPath training and certification
In demand skills needed to strategically position yourself to stay ahead
? If you have any questions or feedback, please refer to the "Women in Automation 2025" dedicated Forum thread. You can find there extra details and updates.Hard Disk Data Acquisition
- 1. Taha ?slamYILMAZ Computer Engineering TOBB ETU ADEO IWS - Digital Forensics HARD DISK DATA ACQUISITION
- 2. Hard Disk Data Acquisition ? System Preservation Phase ? ? Evidence Searching Phase ? Event Reconstruction Phase
- 3. General Acquisition Procedure ? ? Copy one byte and repeat the process ? Like copying a letter by hand ? Sector by sector
- 4. Data Acquition Layers ? Disk ? Volume ? File ? Application
- 5. Acquisition Tool Testing ? National Institute of Standards andTechnology (NIST) ? The Computer ForensicToolTesting (CFTT) ? Results and specifications can be found on their website https://www.cftt.nist.gov/disk_imaging.htm ?
- 6. Requirements For Mandatory Features-1 ? The tool shall be able to acquire a digital source using each access interface visible to the tool. ? The tool shall be able to create either a clone of a digital source, or an image of a digital source, or provide the capability for the user to select and then create either a clone or an image of a digital source. ? The tool shall operate in at least one execution environment and shall be able to acquire digital sources in each execution environment. ? The tool shall completely acquire all visible data sectors from the digital source. ? The tool shall completely acquire all hidden data sectors from the digital source.
- 7. Requirements For Mandatory Features-2 ? All data sectors acquired by the tool from the digital source shall be accurately acquired. ? If there are unresolved errors reading from a digital source then the tool shall notify the user of the error type and the error location. ? If there are unresolved errors reading from a digital source then the tool shall use a benign fill in the destination object in place of the inaccessible data.
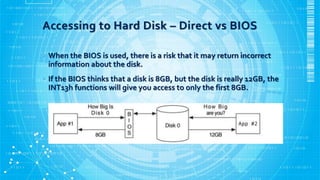
- 8. Accessing to Hard Disk ĻC Direct vs BIOS ? Accessing the hard disk directly is the fastest way to get data to and from the disk, but it requires the software to know quite a bit about the hardware. ? The BIOS knows about the hardware, and it provides services to the software so that they can more easily communicate with hardware.
- 9. Accessing to Hard Disk ĻC Direct vs BIOS ? When the BIOS is used, there is a risk that it may return incorrect information about the disk. ? If the BIOS thinks that a disk is 8GB, but the disk is really 12GB, the INT13h functions will give you access to only the first 8GB.
- 10. Dead vs Live Acquisition ? A dead acquisition occurs when the data from a suspect system is being copied without the assistance of the suspect operating system. ? A live acquisition is one where the suspect operating system is still running and being used to copy data. ? The risk of conducting a live acquisition is that the attacker has modified the operating system or other software to provide false data during the acquisition. ? Attackers may install tools called rootkits into systems that they compromise, and they return false information to a user
- 11. Host Protected Area (HPA) ? Special area of the disk that can be used to save data, and a casual observer might not see it. ? The HPA is at the end of the disk and, when used, can only be accessed by reconfiguring the hard disk. ? It could contain hidden data.
- 12. Host Protected Area (HPA) ? The READ_NATIVE_MAX_ADDRESS command gives the total number of sectors on the disk ? The IDENTIFY_DEVICE returns the total number of sectors that a user can access ? These two values will be different , if an HPA exists.
- 13. Device Configuration Overlay (DCO) ? Similar to an HPA a DCO may contain hidden data.They can exist at the same time. ? A DCO could show a smaller disk size and show that supported features are not supported. ? The DCO allows system vendors configure all HDDs to have the same number of sectors.
- 14. Device Configuration Overlay (DCO) ? The DEVICE_CONFIGURATION_IDENTIFY command returns the actual features and size of a disk. ? To remove a DCO, the DEVICE_CONFIGURATION_RESET command is used.
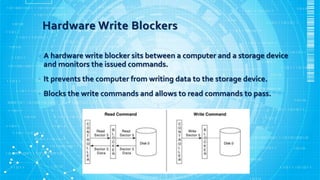
- 15. Hardware Write Blockers ? A hardware write blocker sits between a computer and a storage device and monitors the issued commands. ? It prevents the computer from writing data to the storage device. ? Blocks the write commands and allows to read commands to pass.
- 16. Requirements For Hardware Write Blockers ? A hardware write block (HWB) device shall not transmit a command to a protected storage device that modifies the data on the storage device. ? An HWB device shall return the data requested by a read operation. ? An HWB device shall return without modification any access-significant information requested from the drive. ? Any error condition reported by the storage device to the HWB device shall be reported to the host. ? Source: http://www.cftt.nist.gov/hardware_write_block.htm
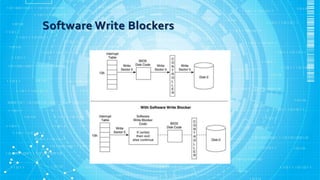
- 17. Software Write Blockers ? The software write blockers work by modifying the interrupt table, which is used to locate the code for a given BIOS service. ? INT13h points to the code that will write or read data to or from the disk. ? When the operating system calls INT13h, the write blocker code is executed and examines which function is being requested. ? If the command is write , software write blocker blocks the commands. If it is a non-write command , blocker pass it to BIOS.
- 19. Requirements For Software Write Blockers ? The tool shall not allow a protected drive to be changed. ? The tool shall not prevent obtaining any information from or about any drive. ? The tool shall not prevent any operations to a drive that is not protected. ? Source: http://www.cftt.nist.gov/software_write_block.htm
- 20. Writing The Output Data ? We can write the output data either directly to a disk or to a file. ? Disk should be wiped with zeros before acquisitions. ? Original and destination disks should have the same geometries.
- 21. Image File Format ? A raw image contains only the data from the source device, and it is easy to compare the image with the source data. ? An embedded image contains data from the source device and additional descriptive data about the acquisition, such as hash values, dates, and times. ? And some tools will create a raw image and save the additional descriptive data to a separate file.
- 22. Thank you for listening to me !








