Hazy Datagrams
- 1. HAZY DATAGRAMS 25.10.2022 OWASP SAITAMA MTG #10 TALK #1
- 2. TEXT SESSION FLAGS ? Õh╗Ł?Õhę¶?╣½ķ_: OK Image by Nico Kaiser on flickr, CC-BY 2.0
- 3. TEXT WHO I AM ? Takahiro Yoshimura (@alterakey) https://keybase.io/alterakey ? Monolith Works Inc. Co-founder, CTO Security researcher ? ├„ų╬┤¾č¦źĄźżźą®`ź╗źŁźÕźĻźŲźŻčąŠ┐╦∙ ┐═åT蹊┐åT
- 4. TEXT WHAT I DO ? Security research and development ? iOS/Android Apps Ī·Financial, Games, IoT related, etc. (>200) Ī·trueseeing: Non-decompiling Android Application Vulnerability Scanner [2017] ? Windows/Mac/Web/HTML5 Apps Ī·POS, RAD tools etc. ? Network/Web penetration testing Ī·PCI-DSS etc. ? Search engine reconnaissance (aka. Google Hacking) ? Whitebox testing ? Forensic analysis
- 5. TEXT WHAT I DO ? CTF ? Enemy10, Sutegoma2 ? METI CTFCJ 2012 Qual.: Won ? METI CTFCJ 2012: 3rd ? DEF CON 21 CTF: 6th ? DEF CON 22 OpenCTF: 4th ? ░k▒Ē?ųvč▌ż╩ż╔ DEF CON 25 Demo Labs (2017) DEF CON 27 AI Village (2019) CODE BLUE (2017, 2019) CYDEF (2020) etc. Image by Wiyre Media on flickr, CC-BY 2.0
- 7. TEXT WHAT IS NOISE? ? ░Ą║┼źūźĒź╚ź│źļż“ū„żļż┐żßż╬źšźņ®`źÓź’®`ź» ? ░Ą║┼źūźĒź╚ź│źļ (n.): ŲĮ╬─ź┴źŃź═źļż╦ż¬żżżŲĪó├ž─õąį?═Ļ╚½ąįż¼▒Żį^ żĄżņż┐═©ą┼ź┴źŃź═źļż╬śŗ║Bż“─┐ųĖż╣źūźĒź╚ź│źļ Ż©e.g. TLS, IPsec, etc.Ż®
- 8. TEXT WHAT IS NOISE? ? śŗ│╔ę¬╦žż“źųźĒź├ź»╗» ? s, e, ss, se, es, ee, pskż“ĮMż▀║Žż’ż╗żŲįOėŗ ? s: ķLŲ┌µIż╬╣½ķ_µI╦═ĖČ e: ę╗ĢrµIż╬╔·│╔?╣½ķ_µI╦═ĖČ ss/se/es/ee: Dif fi e-Hellman║ŽęŌą╬│╔ psk: Pre-shared key▀mė├ Image by Eric Haines on flickr, CC-BY 2.0
- 9. TEXT WHAT IS NOISE? ? ź═ź┤źĘź©®`źĘźńź¾ÖCśŗżŽ╠ß╣®żĘż╩żżŻ©cf. TLSŻ® ? ░Ą║┼ŽĄż“Ž▐Č©Ż©cf. TLSŻ® ? DH: Curve25519/Curve448 ? AEAD: ChaCha20-Poly1305/AES-GCM ? Hash: SHA256/512/BLAKE2s/BLAKE2d Image by plenty.r. on flickr, CC-BY-SA 2.0
- 10. TEXT WHAT IS NOISE? ? źšźņźŁźĘźųźļż└ż¼łį╣╠ż╩īgū░ż¼Ą├żķżņżļ ? Ž╚▀MĄ─ż╩╠žÅšż“│ųż─źūźĒź╚ź│źļįOėŗż╦żŌīØÅĻ ? 0-RTT ? Post-quantum resistance (i.e. PSK) etc. Image by Chris Elt on flickr, CC-BY-NC-ND 2.0
- 11. TEXT WHAT IS NOISE? ? Ʊė├└² ? WireGuard ? WhatsApp ? Lightning Network ? I2P etc, etc.. Image by Patras Gagilas on flickr, CC-BY-SA 2.0
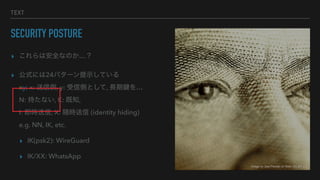
- 12. TEXT SECURITY POSTURE ? ż│żņżķżŽ░▓╚½ż╩ż╬ż½ĪŁŻ┐ ? ╣½╩Įż╦żŽ24źčź┐®`ź¾╠ß╩ŠżĘżŲżżżļ xy; x: ╦═ą┼é╚, y: ╩▄ą┼é╚ż╚żĘżŲ, ķLŲ┌µIż“ĪŁ N: │ųż┐ż╩żż, K: ╝╚ų¬, I: ╝┤Ģr╦═ą┼, X: ╦µĢr╦═ą┼ (identity hiding) e.g. NN, IK, etc. ? IK(psk2): WireGuard ? IK/XX: WhatsApp Image by Joel Penner on flickr, CC-BY 2.0
- 13. TEXT SECURITY POSTURE ? ūįū„ż╬żŌż╬żŽĪŁŻ┐ ? ź╔źŁźÕźßź¾ź╚7.3ĒŚż╦╗∙£╩4ĄŃ Ī· ż│żņż╦ÅŠż├żŲżżżņżąĪŁ https://noiseprotocol.org/noise.html#handshake- pattern-validity ? ╦═ĖČ╗ž╩²ĪóECDH║ŽęŌ╗ž╩²ęÄųŲ: źĘź¾źūźļż╩įOėŗ ? ░Ą║┼╗»ż╦Ž╚┴óż├ż┐ECDH║ŽęŌÅŖųŲ: ?ECDHµIż╬į┘└¹ė├ęÄųŲ ?ę╗ĢrµIż╦żĶżļForward-secrecy, key-compromise impersonation resistanceż╬ÅŖųŲ
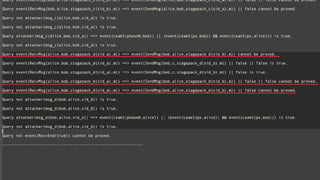
- 14. TEXT FORMAL VERIFICATION ? Noise Explorer [Kobeissi18] ? Handshakeż╦ż─żżżŲProVerifźŌźŪźļ╔·│╔ Go/Rustż╦żĶżļ░▓╚½ż╩īgū░╔·│╔ ? ╣½╩ĮŻ½┼╔╔·: ╚½57źčź┐®`ź¾ż╦īØÅĻ ? ╚╬ęŌźčź┐®`ź¾ż╦ż─żżżŲżŌīØÅĻ ? ╣źō─źĘź╩źĻź¬: active/passiveüIīØÅĻ ż┐ż└ĪŁ ┼“┤¾ż╩źļ®`źļ┴┐
- 15. TEXT FORMAL VERIFICATION ? ProVerif: INRIAųŲū„ż╬░Ą║┼źūźĒź╚ź│źļŚ╩į^ź─®`źļ ? Dolev-YaoźŌźŪźļż╦ż¬ż▒żļŽĄż╬╠žÅšż“į^├„ ? Secrecy (├ž─õąį) ? Authenticity (šµš²ąį) ? Strong secrecy (ÅŖżż├ž─õąį; ū┤æBēõ╗»ż╬├ž─õ) etc.
- 16. TEXT FORMAL VERIFICATION ? ProVerif: INRIAųŲū„ż╬░Ą║┼źūźĒź╚ź│źļŚ╩į^ź─®`źļ ? ┴óį^żŪżŁż╩żżł÷║ŽĘ┤į^Ż©i.e. ╣źō─╩ųČ╬Ż®ż“╩Šż╣ ĪŁż¼Īóš²żĘż»└ĒĮŌż╣żļż╬żŽ┤¾ēõ ? į^├„ż“ĢrĪ®ķg▀`ż”ż¼░▓╚½é╚ż╦Ą╣żĘżŲżóżļ Ī·īgąą▓╗─▄ż╩╣źō─ż“┴ó░ĖżĘżŲż»żļł÷║Žż¼żóżļ Ī·╠ž«ÉČ╚ż¼Ė▀żżįOėŗ ? Į±╗žDockerż╦ż▐ż╚żßż┐ https://gist.github.com/alterakey/ 9af9b6184ffce873f4d1e2eb0ac226c7
- 17. TEXT FORMAL VERIFICATION ? Dolev-YaoźŌźŪźļ ? ░Ą║┼ŽĄżŽ═Ļ╚½ Ī· CryptoVerif.. ? ź╚źķźšźŻź├ź»żŽĄ┴┬ŚĖ─ĖZé╬įņ┐╔─▄ (i.e. Ī░attacker carries message.Ī▒) ? źßź├ź╗®`źĖ─┌╚▌żŽ¤oųŲŽ▐ ? ¤oųŲŽ▐ż╬ČÓīØČÓ═©ą┼ ? ¤oųŲŽ▐ż╬ČÓųžź╗ź├źĘźńź¾ Image by Charlie Nguyen on flickr, CC-BY 2.0
- 18. TEXT FORMAL VERIFICATION ? Dolev-YaoźŌźŪźļ ? ėŗ╦ŃšōĄ─źŌźŪźļżĶżĻżŽ▓╗═Ļ╚½ ? ┤·╩²Ą─╩ųĘ©ż“╩╣ż©żļż╬żŪżĶżĻÆQżżżõż╣żż ? źūźĒź╚ź│źļż“ŲŲżļż╬ż╦żŽ▀mżĘżŲżżżļ (NB. ─µż╦═Ļ╚½ąįż╬Ś╩į^ż╦żŽŽ“żżżŲżżż╩żż) Image by Charlie Nguyen on flickr, CC-BY 2.0
- 19. TEXT SECURITY POSTURE ? ż│żņżķżŽ░▓╚½ż╩ż╬ż½ĪŁŻ┐ ? ╣½╩Įż╦żŽ24źčź┐®`ź¾╠ß╩ŠżĘżŲżżżļ xy; x: ╦═ą┼é╚, y: ╩▄ą┼é╚ż╚żĘżŲ, ķLŲ┌µIż“ĪŁ N: │ųż┐ż╩żż, K: ╝╚ų¬, I: ╝┤Ģr╦═ą┼, X: ╦µĢr╦═ą┼ (identity hiding) e.g. NN, IK, etc. ? IK(psk2): WireGuard ? IK/XX: WhatsApp Image by Joel Penner on flickr, CC-BY 2.0
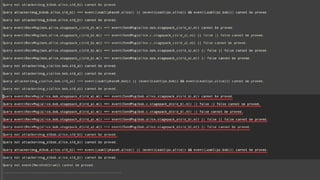
- 20. TEXT CASE STUDY: NEVER-AND-NEVER ? NN: ╦═ą┼š▀żŌ╩▄ą┼š▀żŌķLŲ┌µIż“│ųż┐ż╩żżĪŁŻ┐ ? NN: -> e <- e, ee -> ? ╦═ą┼é╚ż¼ę╗ĢrµIż“ū„ż├żŲ╦═żļ ╩▄ą┼é╚żŌę╗ĢrµIż“ū„ż├żŲ╦═żĻĪóDH║ŽęŌż“ą╬│╔ Image by SonnyandSandy on flickr, CC-BY-NC-ND 2.0
- 21. TEXT CASE STUDY: NEVER-AND-NEVER ? NN: ╦═ą┼š▀żŌ╩▄ą┼š▀żŌķLŲ┌µIż“│ųż┐ż╩żż ? Anonymous DH ? Passive Image by SonnyandSandy on flickr, CC-BY-NC-ND 2.0
- 23. TEXT CASE STUDY: NEVER-AND-NEVER ? NN: ╦═ą┼š▀żŌ╩▄ą┼š▀żŌķLŲ┌µIż“│ųż┐ż╩żż ? Anonymous DH ? Active Image by SonnyandSandy on flickr, CC-BY-NC-ND 2.0
- 25. TEXT CASE STUDY: NEVER-AND-NEVER ? NN: ╦═ą┼š▀żŌ╩▄ą┼š▀żŌķLŲ┌µIż“│ųż┐ż╩żż ? Anonymous DH Passive: secrecyż╬ż▀ (forward secrecy▐zż▀) Active: ║╬ż╬▒ŻūożŌ╠ß╣®żĘż╩żżŻ©ŻĪŻ® ? Noiseż“╩╣ż├żŲżżżļż½żķż╚čįż├żŲūįäėĄ─ż╦░▓╚½ż╦ ż╩żļż’ż▒żŪżŽż╩żż└² Image by SonnyandSandy on flickr, CC-BY-NC-ND 2.0
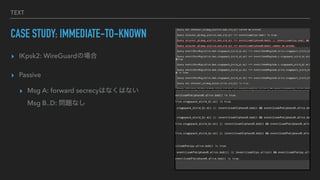
- 26. TEXT CASE STUDY: IMMEDIATE-TO-KNOWN ? IKpsk2: WireGuardż╬ł÷║Ž ? Passive ? Msg A: forward secrecyżŽż╩ż»żŽż╩żż Msg B..D: å¢Ņ}ż╩żĘ
- 27. TEXT CASE STUDY: IMMEDIATE-TO-KNOWN ? IKpsk2: WireGuardż╬ł÷║Ž ? Active ? Msg A: forward secrecyżŽż╩ż»żŽż╩żż Msg B: forward secrecyżŽż▐żó╚§żżż½ż╩ Msg C..D: å¢Ņ}ż╩żĘ
- 28. TEXT CASE STUDY: IMMEDIATE-TO-KNOWN ? IKpsk2: WireGuardż╬ł÷║Ž ? Passive/ActiveżŪĮU▀^ż¼▀`ż”ż¼ĪŁ ? Handshake╚½╠Õż“ęŖżļŽ▐żĻżŽ░▓╚½ ? ├ž─õąį: źŁ®`żŽ┬®żņż╩żżĪóż▐ż┐ę╗ĢrźŁ®`ż¼ĖŅżņ ż┐ł÷║ŽżŪżŌżĮżņęįŪ░ż╬═©ą┼─┌╚▌żŽĮŌšiżŪżŁż╩żż ? šµš²ąį: żŌż╚żŌż╚ķLŲ┌źŁ®`ż¼compromiseżĄżņ żŲżżż╩żżŽ▐żĻżŽå¢Ņ}ż¼ż╩żż Image by pfly on flickr, CC-BY-SA 2.0
- 29. TEXT TAKEAWAYS ? NoiseżŽ░Ą║┼źūźĒź╚ź│źļźšźņ®`źÓź’®`ź» ? śŗ│╔ę¬╦žż“ģŚ▀x?źųźĒź├ź»╗»?źčź┐®`ź¾╗» Ī·ą┬ęÄż╦ūĘ╝ėżŌżŪżŁżļż¼ĪŁ ? ģg╝ā?Ė▀╦┘?░▓╚½ż╩źūźĒź╚ź│źļįOėŗż╦╝─ėļ Ī·Ž╚▀MĄ─╠žąįż“│ųż─źūźĒź╚ź│źļįOėŗż╦żŌīØÅĻ (0-RTT, post-quantum resistanceż╩ż╔) ? į^├„┐╔─▄ąįż“ķ_żżż┐ż╚żŌčįż©żļĪŁ Image by Daisuke Matsumura on flickr, CC-BY-NC 2.0
- 30. TEXT TAKEAWAYS ? Noise Explorer: Kobeissiżķż╦żĶżļįOėŗ?źŌźŪźĻź¾ ź░ŽĄ [Kobeissi18] ? ╣½╩Į57źčź┐®`ź¾ż╬ż▀ż╩żķż║╚╬ęŌįOėŗż╦īØżĘżŲżŌ ProVerifźŌźŪźļż“╔·│╔┐╔─▄ ? ProVerif: INRIAųŲū„ż╬░Ą║┼źūźĒź╚ź│źļŚ╩į^ź─®`źļ ╣źō─Ą─ź═ź├ź╚ź’®`ź»Ż©Dolev-YaoźŌźŪźļŻ®Ž┬ż╦ż¬ żżżŲŽĄż╬│ųż─░▓╚½ąįż“┤·╩²Ą─ż╦į^├„ ? į^├„┐╔─▄ż╩░▓╚½ąįż¼ż½ż╩żĻaccessibleż╦ż╩ż├ż┐
- 31. TEXT TAKEAWAYS ? Noiseż“╩╣ė├żĘżŲżżżļż½żķż╚żżż├żŲ╚½żŲż¼░▓╚½ż╩ ż’ż▒żŪżŽż╩żż ? └²: NN (= anonymous DHż╚Ą╚ü²) ? ūįū„ż╣żļł÷║Ž: ź╔źŁźÕźßź¾ź╚7.3ĒŚż╬ź¼źżź╔źķźżź¾ż╦ÅŠż”╦¹ż╦Īó żŪżŁżļŽ▐żĻį^├„ż“ąąż” Image by SonnyandSandy on flickr, CC-BY-NC-ND 2.0
- 32. TEXT REFERENCES ? Noise: https://noiseprotocol.org/ ? Noise Explorer: https://noiseexplorer.com/ ? ProVerif: https://bblanche.gitlabpages.inria.fr/proverif/ ? Docker fi le: https://gist.github.com/alterakey/ 9af9b6184ffce873f4d1e2eb0ac226c7
- 33. FIN.



![TEXT
WHAT I DO
? Security research and development
? iOS/Android Apps
Ī·Financial, Games, IoT related, etc. (>200)
Ī·trueseeing: Non-decompiling Android Application
Vulnerability Scanner [2017]
? Windows/Mac/Web/HTML5 Apps
Ī·POS, RAD tools etc.
? Network/Web penetration testing
Ī·PCI-DSS etc.
? Search engine reconnaissance
(aka. Google Hacking)
? Whitebox testing
? Forensic analysis](https://image.slidesharecdn.com/hazy-221027121331-3bb50400/85/Hazy-Datagrams-4-320.jpg)




![TEXT
FORMAL VERIFICATION
? Noise Explorer [Kobeissi18]
? Handshakeż╦ż─żżżŲProVerifźŌźŪźļ╔·│╔
Go/Rustż╦żĶżļ░▓╚½ż╩īgū░╔·│╔
? ╣½╩ĮŻ½┼╔╔·: ╚½57źčź┐®`ź¾ż╦īØÅĻ
? ╚╬ęŌźčź┐®`ź¾ż╦ż─żżżŲżŌīØÅĻ
? ╣źō─źĘź╩źĻź¬: active/passiveüIīØÅĻ
ż┐ż└ĪŁ ┼“┤¾ż╩źļ®`źļ┴┐](https://image.slidesharecdn.com/hazy-221027121331-3bb50400/85/Hazy-Datagrams-14-320.jpg)









![TEXT
TAKEAWAYS
? Noise Explorer: Kobeissiżķż╦żĶżļįOėŗ?źŌźŪźĻź¾
ź░ŽĄ [Kobeissi18]
? ╣½╩Į57źčź┐®`ź¾ż╬ż▀ż╩żķż║╚╬ęŌįOėŗż╦īØżĘżŲżŌ
ProVerifźŌźŪźļż“╔·│╔┐╔─▄
? ProVerif: INRIAųŲū„ż╬░Ą║┼źūźĒź╚ź│źļŚ╩į^ź─®`źļ
╣źō─Ą─ź═ź├ź╚ź’®`ź»Ż©Dolev-YaoźŌźŪźļŻ®Ž┬ż╦ż¬
żżżŲŽĄż╬│ųż─░▓╚½ąįż“┤·╩²Ą─ż╦į^├„
? į^├„┐╔─▄ż╩░▓╚½ąįż¼ż½ż╩żĻaccessibleż╦ż╩ż├ż┐](https://image.slidesharecdn.com/hazy-221027121331-3bb50400/85/Hazy-Datagrams-30-320.jpg)