Looking Back 2023
- 1. LOOKING BACK: 2023 OWASP SAITAMA MTG #17, TALK #1 Image by Abubakr Saeed on flickr, CC-BY 2.0
- 2. TEXT SESSION FLAGS ? Õh╗Ł?Õhę¶?╣½ķ_: OK Image by Nico Kaiser on flickr, CC-BY 2.0
- 3. TEXT WHO I AM ? Takahiro Yoshimura (@alterakey) https://keybase.io/alterakey ? Monolith Works Inc. Co-founder, CTO Security researcher ? ├„ų╬┤¾č¦źĄźżźą®`ź╗źŁźÕźĻźŲźŻčąŠ┐╦∙ ┐═åT蹊┐åT
- 4. TEXT WHAT I DO ? Security research and development ? iOS/Android Apps Ī·Financial, Games, IoT related, etc. (>200) Ī·trueseeing: Non-decompiling Android Application Vulnerability Scanner [2017] ? Windows/Mac/Web/HTML5 Apps Ī·POS, RAD tools etc. ? Network/Web penetration testing Ī·PCI-DSS etc. ? Search engine reconnaissance (aka. Google Hacking) ? Whitebox testing ? Forensic analysis
- 5. TEXT WHAT I DO ? CTF ? Enemy10, Sutegoma2 ? METI CTFCJ 2012 Qual.: Won ? METI CTFCJ 2012: 3rd ? DEF CON 21 CTF: 6th ? DEF CON 22 OpenCTF: 4th ? ░k▒Ē?ųvč▌ż╩ż╔ DEF CON 25 Demo Labs (2017) DEF CON 27 AI Village (2019) CODE BLUE (2017, 2019) CYDEF (2020) etc. Image by Wiyre Media on flickr, CC-BY 2.0
- 6. 2023.. Image by Transformer18 on flickr, CC-BY-ND 2.0
- 7. FEBURARY Image by Paul Sobczak on flickr, CC-BY 2.0
- 8. TEXT FEBURARY - #12 ? 2023─Ļ│§żßż╬ķ_┤▀ ? ┤║╚š▓┐╩ąķ_┤▀: żšżņżóżżźŁźÕ®`źų 4F ? ż│ż╬Ģræ®ėH╗ßż“ąąż╩ż├ż┐źįźČ╬▌ż¼Øóżņż┐ĪŁ orz Image by Erik Weibust on flickr, CC-BY-NC-ND 2.0
- 9. TICKET TO THE DARK WORLD FRONT Image by Alexandre Gallier on flickr, CC-BY-NC-ND 2.0
- 10. TEXT FRONT: TICKET TO THE DARK WORLD ? ¤oĘ©ĄžÄĪżŪżóżļź└®`ź»ź”ź¦źųŁhŠ│ ? źóź»ź╗ź╣ż╦żŽTorźųźķź”źČż¼ę¬Ū¾żĄżņżļż¼▀Wżż Ī·TorżŽFirefox ESR Ī·Firefoxūį╠Õż╬Ė─┴╝ż¼▀Mż¾żŪżżżļż╬ż└ż¼ĪŁ ? żŪżŽūį╝ęčuŁhŠ│ż¼ż╔żņż└ż▒═©ė├ż╣żļż╬ż½Ż┐ ż▐ż┐żĶżĻ░▓╚½ż╩ŁhŠ│ż“ū„żļż╦żŽŻ┐ Ī·Ś╩į^ż└ŻĪ Image by Alexandre Gallier on flickr, CC-BY-NC-ND 2.0
- 13. TEXT FRONT: TAKEAWAYS ? ¤oĘ©ĄžÄĪżŪżóżļź└®`ź»ź”ź¦źųŁhŠ│ ? øQżĘżŲź╩źßżŲżŽżżż▒ż╩żżJSż╬ł╠─Ņż“į½ķgęŖż┐╗ž Ī·non-JSŁhŠ│ż╩żķRFP+FPI+╔┘żĘż╬╣żĘ“żŪźżź▒żļ Ī·JSŁhŠ│żŽż½ż╩żĻż╬źĻź╣ź»; Torźųźķź”źČż¼▒žĒÜ Ī·żżż║żņż╦żĘżŲżŌ╚½╗Ł├µźŌ®`ź╔ż╬╩╣ė├żŽĮ~īØNG ? żĶżĻ░▓╚½ż╩ŁhŠ│ż“ū„żļż╦żŽŻ┐ Ī·Torźųźķź”źČż“╗∙▒ŠĄ─ż╦SafestżŪ▀\ė├ Ī·Extensionż╬ī¦╚ļ: uBO/LocalCDNżŽėąä┐ Ī∙Hard modeż¼┴╝żżż¼įS┐╔┬─Üsż╦ūóęŌ Image by Andrew on flickr, CC-BY-NC-ND 2.0
- 16. TEXT FRONT: TAKEAWAYS ? ¤oĘ©ĄžÄĪżŪżóżļź└®`ź»ź”ź¦źųŁhŠ│ ? żóż╩ż┐ż“żżż─żŪżŌęŖ╩žżļGuard nodeż╬┐ų▓└ Ī·Guard nodeżŽźūźķźżźąźĘ®`ż╬źóźŁźņź╣ļņ Ī·┴ó║“čażĄż©ż╣żņżąšlżŪżŌż╩żņżļ Ī·ż┐ż▐ż╦ČÓ╩²ż╬═¼┘|ź╬®`ź╔ż╦żĶżļcampaignż¼ ? żĮż¾ż╩ū░éõżŪ┤¾š╔Ę“ż½Ż┐ Ī¬ ┤¾š╔Ę“ż└å¢Ņ}ż╩żż (r ĪŁżĮż¾ż╩š╣ķ_ż¼Ųš═©ż╦żóżļ╩└Įń; ? ą┼ŅmżŪżŁżļbridgeż“┤¾Ūąż╦Īóż╔ż”ż½ż┤░▓╚½ż╦ĪŻ Image by KaCey97078 on flickr, CC-BY-NC 2.0
- 17. TEXT BACK: CHAPTER INTRO. ? 2į┬żŽŲ¼╩ų┬õż┴
- 18. APRIL Image by Walter on flickr, CC-BY-NC 2.0
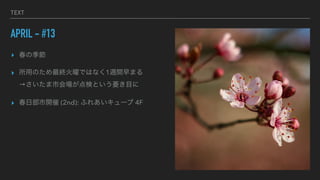
- 19. TEXT APRIL - #13 ? ┤║ż╬╝Š╣Ø ? ╦∙ė├ż╬ż┐żßūŅĮK╗ĻūżŪżŽż╩ż»1▀Lķgįńż▐żļ Ī·żĄżżż┐ż▐╩ą╗ßł÷ż¼ĄŃŚ╩ż╚żżż”ænżŁ─┐ż╦ ? ┤║╚š▓┐╩ąķ_┤▀ (2nd): żšżņżóżżźŁźÕ®`źų 4F
- 20. FILL IN THE BLANK FRONT Image by Ars Electronica on flickr, CC BY-NC-ND 2.0
- 21. TEXT FRONT: FILL IN THE BLANK ? ChatGPTż╦┤·▒ĒżĄżņżļLLMĪŁ ┼“┤¾ż╩ų¬ūRż“│ųż├żŲūį╚╗čįšZżŪ╗ßįÆżŪżŁżļÖCąĄ č¦┴ĢźŌźŪźļ ? Ūķł¾┬®ø¬żŽŻ┐╣źō─żŽŻ┐╚š▒ŠšZżŪżŽŻ┐ Ī·Ś╩į^ż└ŻĪŻ©ČÓĘų╬ęĪ®ż¼│§żßżŲŻ®
- 30. TEXT FRONT: TAKEAWAYS ? Ūķł¾┬®ø¬ż╦ż─żżżŲżŽ╚¶Ė╔“Xż«▀^ż«ż╬Ėą Ī·żĮż╬ż▐ż▐corpusż╦╚ļżļż’ż▒żŪżŌż╩żż Ī·ź¬źūź╚źóź”ź╚żŌżŪżŁżļ (OpenAIż╬ż▀) Ī∙żÓżĘżĒGoogleż╩ż╔ż╬ż█ż”ż¼å¢Ņ} ? Prompt Injection: ūį╚╗čįšZŠ│Įńż¼Ģß├┴ż╩ż│ż╚ż“└¹ ė├żĘżŲųĖ┴Ņż“ÆĘ╚ļż╣żļ╣źō─ Ī·═Ļ╚½ż╦Ę└ė∙ż╣żļ╩ų┴óżŲżŽ¼Fū┤ż╩żż Ī·╚š▒ŠšZżŪżŌ╩«Ęųż╦ėąä┐ Ī·└¹ė├ż╣żļż╩żķźĻź╣ź»źžź├źĖ▓▀ż“ Image by Howard Ignatius on flickr, CC-BY-NC-ND 2.0
- 31. KIA? CHALLENGE? ? ĪĖKia BoyzŻ©Ųüäź▄®`źżź║Ż®Ī╣ż╚żŽĪóŲ üäūįäė▄ćż“Ą┴ż▀ĪóĄ┴ż¾ż└Ēn╣·▄ćż“╩╣ż├żŲ ▒®ū▀▀\▄×Īóü\żĻÆ╬żŲĪó╩┬╣╩ż“Ųż│ż╣ż╩ż╔ żĘż┐äė╗Łż“TiktokżõYouTubeż╩ż╔ż╦═ČĖÕ ż╣żļźŲźŻ®`ź¾ź©®`źĖźŃ®`ż╬ż│ż╚ ? ż│ż╬Ī░ÉÖ┘|ż╩ź▓®`źÓĪ▒ż╬ż│ż╚ż“ĪĖKia ChallengeŻ©Ųüäź┴źŃźņź¾źĖŻ®Ī╣ż▐ż┐żŽ ĪĖKia Boyz ChallengeŻ©źŁźó?ź▄®`źżź║? ź┴źŃźņź¾źĖŻ®Ī╣ż╚║¶żążņżŲżżżļ THIEVES #1 BACK
- 32. TEXT BACK: THIEVES #1 ? ▄ćż╬Ą┴ļy╩┬╝■ż¼ŠA░k Ī·ż╔ż”ż╩ż├żŲżżżļż╬ż½Ż┐
- 33. TEXT BACK: TAKEAWAYS ? │§żßkia, ┤╬żżżŪRAV4 ? ╩ųĘ©ż╚īØ▓▀ż╬╣▓▀M╗»Ż©i.e. źżź┐ź┴ż┤ż├ż│Ż® ? źżźŌźėźķźżźČ®`ż╬┤µį┌ż╚╗ž▒▄ ? źŁ®`šJį^źūźĒź╚ź│źļżŽ═“╚½ż╚żŽčįż©ż╩żż ? żŌżŽżõ╬’└ĒĄ─ż╦╩žżļżĘż½ż╩żż Image by KaCey97078 on flickr, CC-BY-NC 2.0
- 34. JUNE Image by Thai Jasmine (Smile..smile...Smile..) on flickr, CC-BY-NC 2.0
- 35. TEXT JUNE - #14 ? ėĻż╬╝Š╣Ø ? ┤║╚š▓┐╩ąķ_┤▀ (3rd): żšżņżóżżźŁźÕ®`źų 4F Image by Pom' on flickr, CC-BY-SA 2.0
- 36. THIEVES #2 FRONT
- 37. TEXT FRONT: THIEVES #2 ? Ū░╗žżŽkiaż╚RAV4ż└ż├ż┐ż¼ĪóīgżŽhondażŌĪŁ Ī·ż╩ż╝Ż┐
- 38. TEXT FRONT: TAKEAWAYS ? CANźąź╣śŗ│╔ż╦Ū▒į┌ż╣żļå¢Ņ}ż╦╝ėż© RFźĻźŌź│ź¾ą┼║┼ż╬śŗįņż╦żŌå¢Ņ}ż¼ ? rolling codeżŪīØ▓▀żĘż┐ż╚╦╝ż©żąĪóżĮż╬īØ▓▀ż╦żŌ ŪĘĻłż¼ ? ĪŁżĘżążķż»ŠAż»ż╬ż└żĒż”ż½ĪŻ
- 39. TEXT BACK: CHAPTER INTRO. ? ż│ż╬į┬żŌŲ¼╩ų┬õż┴
- 40. AUGEST Image by Joe Penniston on flickr, CC-BY-NC-ND 2.0
- 41. TEXT AUGEST - #15 ? ¤åż▒ż─ż»├═╩Ņ ? żĄżżż┐ż▐╩ąķ_┤▀: RaiBoCź█®`źļ ╝»╗ß╩ę ? OWASP Sendai ąĪ¾ężĄż¾ż╬ż┤║±ęŌż╦żĶżļ │§ż╬ź’®`ź»źĘźńź├źū ? ķ_┤▀─┐Ū░ż╦āWż¼COVID-19żŪ╝▒ÕßźĻźŌ®`ź╚ż╦ĪŁ Ī·Ė„╬╗ż┤├į╗¾ż“ż¬ż½ż▒żĘż▐żĘż┐ Image by Shawn Harquail on flickr, CC-BY-NC 2.0
- 43. TEXT WORKSHOP: ├{═■źŌźŪźĻź¾ź░ź’®`ź»źĘźńź├źū ? OWASP Sendaiź┴źŃźūź┐®`źĻ®`ź└®`ż╬ąĪ¾ę┘FŪń (@TakaharuOgasa) żĄż¾ż½żķ ? ├{═■źŌźŪźĻź¾ź░ź’®`ź»źĘźńź├źū Ī·ųą╔Ēż¼ØŌżżż╬żŪź¬źšźķźżź¾Ž▐Č©ż╦ ? ▓╬╝ėĖ„╬╗ĪóżóżĻż¼ż╚ż”ż┤żČżżż▐żĘż┐ŻĪ
- 44. TEXT BACK: CHAPTER INTRO. ? āWż¼ż”ż├ż½żĻCOVID-19ż╦├░żĄżņż┐(ż╣ż▀ż▐ż╗ż¾) Ī·▀zė░▓╬╝ėżŪź┴źŃźūź┐®`ĮBĮķż“ĪŁ
- 45. OCTOBER Image by berniezang on flickr, CC-BY-NC 2.0
- 46. TEXT OCTOBER - #16 ? źė®`źļż╬į┬ ? ┤║╚š▓┐╩ąķ_┤▀; żšżņżóżżźŁźÕ®`źų6F .. ėĶŽļęį╔Žż╬łRŲ╚Ėąż╦ęįĮĄżŽ4FżŪż╚øQęŌżĘż┐╗ž ? ░Ą³aĄ─ż└ż├ż┐ź╣źį®`ź½®`▒Żūoźļ®`źļż“š¹éõżĘĪó ĪĖź┴źŃź┐źÓźŽź”ź╣źļ®`źļĪ╣ż“▀mė├ż╣żļų╝├„ėø Image by 5chw4r7z on flickr, CC-BY-SA 2.0
- 48. ECHIDNA: PENETRATION TEST ASSIST & COLLABORATION TOOL FRONT
- 49. TEXT FRONT: ECHIDNA: PENETRATION TEST ASSIST & COLLABORATION TOOL ? ķ_░kš▀ż╬╦┬╠’ėŲ (@chayakonanaika) żĄż¾ż½żķ źŪźŌż¬żĶżė─┌▓┐įOėŗż╦ķvż╣żļ┘Fųžż╩įÆ ? BlackHat EU 2023 ArsenalżŪ░k▒Ē ? ╣źō─ż“┐╔ęĢ╗»?ź┴®`źÓ─┌żŪ╣▓ėążĘ│§ą─š▀żŪżŌ╩« Ęųż╩│╔╣¹ż“│÷ż╗żļżĶż”ż╦ÅŖ┴”ż╦ų¦į«ż╣żļź─®`źļ ? https://github.com/Echidna-Pentest/Echidna
- 50. TEXT FRONT: TAKEAWAYS ? EchidnażŽ│§ą─š▀żõź╗źŁźÕźĻźŲźŻź┴®`źÓż¼╣źō─╩ų Ę©ż“č¦┴ĢżŪżŁżļżĶż”ż╦įOėŗżĄżņżŲżżżļ ? ū┤ørż╦ÅĻżĖżŲ┤╬ż╬ź│ź▐ź¾ź╔ż“╠ß░Ė ? ź│ź▐ź¾ź╔│÷┴”ż½żķųžę¬ż╩╣w╦∙ż“│ķ│÷żĘźĄź▌®`ź╚ ? │§ą─š▀żŪżŌź»źĻź├ź»ż└ż▒żŪŪų╚ļ┐╔─▄ ? źųźķź”źČĮUė╔żŪ╣▓ėąź┐®`ź▀ź╩źļż“╠ß╣®ż╣żļż│ż╚ żŪź┴®`źÓ─┌▀Bą»ż“źĄź▌®`ź╚
- 52. TEXT BACK: THREAT DRAGON ? OWASP Sendaiź┴źŃźūź┐®`źĻ®`ź└®` ąĪ¾ę┘FŪń (@TakaharuOgasa) żĄż¾ż½żķĪó OWASP Threat Dragonż╬ĮBĮķż╚źŽź¾ź║ź¬ź¾ ? OWASP╣½╩Įż╬├{═■źŌźŪźĻź¾ź░ź─®`źļ ? ż│żņżŌż▐ż┐┤¾ēõż╦┘Fųžż╩įÆ ? https://owasp.org/www-project-threat-dragon/
- 53. TEXT BACK: TAKEAWAYS ? ├{═■źŌźŪźĻź¾ź░żŽķ_░kš▀ż╬Į╠ė²ż╦ėąė├ ? ķ_░kŪ░ż╦źĻź╣ź»ż“Ž┤żż│÷ż╣Ż©WFżŪżŽųžę¬Ż® ? į\ČŽżõŪų╚ļźŲź╣ź╚ż╬┤·╠µżŪżŽż╩żż ? OWASP Threat Dragonż╬└¹ĄŃ ? DFDż“Ģ°żŁĪóSTRIDEż“ęĢęÖĄ─ż╦▒Ē¼F īØ▓▀ę╗ėEż“ū„│╔żĘĪóżĮżņż“▒Ż┤µ ? śŗ│╔ę¬╦žż┤ż╚ż╬░k╔·├{═■ź½źŲź┤źĻż“┐╝æ] (!)
- 54. DECEMBER Image by joanne clifford on flickr, CC-BY-ND 2.0
- 55. TEXT DECEMBER ? ─Ļ─® ? żĄżżż┐ż▐╩ąķ_┤▀: RaiBoCź█®`źļ╝»╗ß╩ę Image by DaPuglet on flickr, CC-BY-SA 2.0
- 56. LOOKING BACK 2023 FRONT Image by Abubakr Saeed on flickr, CC-BY 2.0
- 57. TEXT FRONT: LOOK BACK 2023 ? Į±─Ļż╬╗Ņäėż╬żšżĻż½ż©żĻ ? KPT: Keep, Problem, Try Image by Abubakr Saeed on flickr, CC-BY 2.0
- 58. TEXT KEEP ? żŪżŁż┐ż│ż╚ ? ź’®`ź»źĘźńź├źūż╬ķ_┤▀ Ż©ąĪ¾ężĄż¾żóżĻż¼ż╚ż”ż┤żČżżż▐ż╣ŻĪŻ® ? ╣½─╝ź╣źį®`ź½®`Ė„╬╗ż╬ż▀żŪż╬ķ_┤▀ Ż©╦┬╠’żĄż¾żóżĻż¼ż╚ż”ż┤żČżżż▐ż╣ŻĪŻ® ? ź¬źšźķźżź¾ż╬ż▀ķ_┤▀ Image by willi_bremen on flickr, CC-BY-NC-ND 2.0
- 59. TEXT PROBLEM ? Į±ę╗ż─ż└ż├ż┐ż│ż╚ ? ╗Ņäėū┤ørż¼ęŖż©ż╦ż»żż ? įÆŅ}ż╬Ėµų¬ż¼▀Wżż ? ĮŌ╬÷ŽĄż╬įÆŅ}ż“żŌż”╔┘żĘżõżņż┐ż╩ ? ╗Ļūż└ż╚ĄĻż¼ą▌ż¾żŪżżżļź▒®`ź╣ż¼ČÓżżĪŁ Image by Leonid Mamchemkov on flickr, CC-BY 2.0
- 60. TEXT TRY ? żõż├żŲżżżŁż┐żżż│ż╚ ? SNSżžą┤šµż“╚ļżņżŲ╗Ņäėł¾Ėµ Ī·šlż½ŻĪ ? ź╣źį®`ź½®`ż╬ę└Ņm Ī·ę└Ņmż¼żżż├ż┐żķżĶżĒżĘż»ż¬ŅŖżżżĘż▐ż╣mm ? appsec, ╠žż╦źóźūźĻĮŌ╬÷ ? ź’®`ź»źĘźńź├źūżóżļżżżŽCTFŅÉŻ©Ī∙╗ßł÷ż¼å¢Ņ}Ż® ? ķ_┤▀Ļū╚šż╬į┘┐╝ Image by Heiner Engbrocks on flickr, CC-BY-NC 2.0
- 61. FIN. 18.12.2023 TAKAHIRO YOSHIMURA (@ALTERAKEY) Image by Paul Moody on flickr, CC-BY-NC 2.0



![TEXT
WHAT I DO
? Security research and development
? iOS/Android Apps
Ī·Financial, Games, IoT related, etc. (>200)
Ī·trueseeing: Non-decompiling Android Application
Vulnerability Scanner [2017]
? Windows/Mac/Web/HTML5 Apps
Ī·POS, RAD tools etc.
? Network/Web penetration testing
Ī·PCI-DSS etc.
? Search engine reconnaissance
(aka. Google Hacking)
? Whitebox testing
? Forensic analysis](https://image.slidesharecdn.com/looking-back-2023-231225063521-670cedb6/85/Looking-Back-2023-4-320.jpg)




























![TEXT
BACK: TAKEAWAYS
? ├{═■źŌźŪźĻź¾ź░żŽķ_░kš▀ż╬Į╠ė²ż╦ėąė├
? ķ_░kŪ░ż╦źĻź╣ź»ż“Ž┤żż│÷ż╣Ż©WFżŪżŽųžę¬Ż®
? į\ČŽżõŪų╚ļźŲź╣ź╚ż╬┤·╠µżŪżŽż╩żż
? OWASP Threat Dragonż╬└¹ĄŃ
? DFDż“Ģ°żŁĪóSTRIDEż“ęĢęÖĄ─ż╦▒Ē¼F
īØ▓▀ę╗ėEż“ū„│╔żĘĪóżĮżņż“▒Ż┤µ
? śŗ│╔ę¬╦žż┤ż╚ż╬░k╔·├{═■ź½źŲź┤źĻż“┐╝æ] (!)](https://image.slidesharecdn.com/looking-back-2023-231225063521-670cedb6/85/Looking-Back-2023-53-320.jpg)