How to mitigate tcp syn flood attacks
0 likes109 views
Know All About Mitigate TCP Syn Flood Attacks. It is a cyberattack so you need to fix this issue to secure your device & data security using this method. To know more visit https://bit.ly/3czNIcM
1 of 6
Download to read offline





Recommended
DrupalCon Vienna 2017 - Anatomy of DDoS



DrupalCon Vienna 2017 - Anatomy of DDoSSuzanne Aldrich
╠²
This document provides an overview of distributed denial of service (DDoS) attacks including:
- Common types of DDoS attacks like UDP floods, SYN floods, DNS floods and HTTP floods and how they work to overwhelm servers.
- How DDoS attacks are evolving to larger sizes and more complex botnets.
- Methods for mitigating DDoS attacks including black hole routing, rate limiting, web application firewalls, anycast networks and cloud-based DDoS protection services.
- A real example of mitigating a massive 400Gbps DDoS attack and the largest attacks seen to date.Penetration testing is a field which has experienced rapid growth over the years



Penetration testing is a field which has experienced rapid growth over the yearsGregory Hanis
╠²
Sockstress is a denial of service attack that consumes server resources by opening many TCP connections. It was introduced in 2008 and targets vulnerabilities in how TCP handles connections. While tools exist to detect and prevent Sockstress, it remains a potential threat. The attack can be performed by one machine or multiple zombies to mask the source. Defenses include limiting connections per IP and dropping those with zero window responses. Monitoring server resources like RAM usage can also help detect Sockstress attacks. Penetration testing is needed to identify vulnerabilities like this and prove due diligence for organizations.BADCamp 2017 - Anatomy of DDoS



BADCamp 2017 - Anatomy of DDoSSuzanne Aldrich
╠²
DDoS attacks make headlines everyday, but how do they work and how can you defend against them? DDoS attacks can be high volume UDP traffic floods, SYN floods, DNS amplification, or Layer 7 HTTP attacks. Understanding how to protect yourself from DDoS is critical to doing business on the internet today. Suzanne Aldrich, a lead Solutions Engineer at Cloudflare, will cover how these attacks work, what is being targeted by the attackers, and how you can protect against the different attack types. She will cap the session with the rise in IoT attacks, and expectations for the future of web security.
https://2017.badcamp.net/session/devops-performance-security-privacy/beginner/anatomy-ddos-attackAnatomy of DDoS - Builderscon Tokyo 2017



Anatomy of DDoS - Builderscon Tokyo 2017Suzanne Aldrich
╠²
This document discusses distributed denial of service (DDoS) attacks. It begins by defining a DDoS attack as a malicious attempt to disrupt normal traffic by overwhelming a target with a flood of traffic utilizing multiple compromised systems. The document then discusses the evolution of DDoS attacks over time in terms of size and complexity. It provides examples of different types of DDoS attacks including application layer attacks like HTTP floods, protocol attacks like SYN floods, and volumetric attacks like DNS amplification attacks. Finally, it discusses common techniques for mitigating DDoS attacks such as black hole routing, rate limiting, web application firewalls, and anycast network diffusion.The Anatomy of DDoS Attacks



The Anatomy of DDoS AttacksAcquia
╠²
<p>DDoS attacks make headlines everyday, but how do they work and how can you defend against them? DDoS attacks can be high volume UDP traffic floods, SYN floods, DNS amplification, or Layer 7 HTTP attacks. Understanding how to protect yourself from DDoS is critical to doing business on the internet today.</p>
<p>Suzanne Aldrich, a lead Solutions Engineer at Cloudflare, will cover how these attacks work, what is being targeted by the attackers, and how you can protect against the different attack types. She will cap the session with the rise in IoT attacks, and expectations for the future of web security.</p>
<p><strong>Speaker Bio</strong>:</p>
<p>Suzanne is a solutions engineer team lead at Cloudflare, where she specializes in security, performance, and usability. Her interest in all things web started in high school when she created the schoolŌĆÖs first website. While at Stanford, Suzanne was the webmaster for a matchbox sized server running the Wearable Computing LabŌĆÖs site.</p>10 DDoS Mitigation Techniques



10 DDoS Mitigation TechniquesIntruGuard
╠²
Hemant Jain outlines 10 DDoS mitigation techniques:
1. SYN proxy screens connection requests and only forwards legitimate ones to prevent SYN floods from overwhelming servers.
2. Connection limiting gives preference to existing connections and limits new requests to temporarily reduce server overload.
3. Aggressive aging removes idle connections from firewalls and servers to free up space in connection tables.
4. Source rate limiting identifies and denies excessive bandwidth to outlier IP addresses launching attacks.DDOS Attack 



DDOS Attack Ahmed Salama
╠²
DDOS Attack was the first attack in the world and it was the biggest one. This presentation was part of the "Networking" Subject.DDoS Open Threat Signaling (DOTS) Working Group Presentation on draft-ietf-do...



DDoS Open Threat Signaling (DOTS) Working Group Presentation on draft-ietf-do...ShortestPathFirst
╠²
Presentation given by Roland Dobbins covering our recent draft of use case scenarios for use in DDoS Open Threat Signaling. This presentation was given on Nov. 3rd, 2015 at IETF 94 in Yokohama, Japan.MS_ISAC__DDoS_Attacks_Guide__2023_05.pdf



MS_ISAC__DDoS_Attacks_Guide__2023_05.pdfssuser262297
╠²
The document provides an overview of common DDoS attack types including SYN floods, UDP floods, ICMP floods, and HTTP floods. It describes how these attacks work to overwhelm servers and networks with traffic to cause denial of service. The document also covers reflection DDoS attacks using protocols like DNS, NTP, and Memcached to amplify the traffic and discusses recommendations for mitigating these attacks.DoS Attacks



DoS AttacksVladimir Menshikov
╠²
The document discusses denial of service (DoS) attacks, specifically SYN flooding and DNS amplification attacks. It describes how these attacks work by exploiting vulnerabilities in TCP connections and DNS servers. The document outlines the development of attack clients to launch SYN flooding and DNS amplification attacks against a server. It also details how the server was designed to detect and mitigate SYN flooding attacks by tracking and flushing incomplete connection requests. The server was able to withstand SYN flooding attacks but could not defend against DNS amplification. Evaluation results show the server had near perfect detection rates for SYN flooding but occasional dropped legitimate connections under high volume attacks.A ROBUST MECHANISM FOR DEFENDING DISTRIBUTED DENIAL OF SERVICE ATTACKS ON WEB...



A ROBUST MECHANISM FOR DEFENDING DISTRIBUTED DENIAL OF SERVICE ATTACKS ON WEB...IJNSA Journal
╠²
Distributed Denial of Service (DDoS) attacks have emerged as a popular means of causing mass targeted service disruptions, often for extended periods of time. The relative ease and low costs of launching such attacks, supplemented by the current inadequate sate of any viable defense mechanism, have made them one of the top threats to the Internet community today. Since the increasing popularity of web-based applications has led to several critical services being provided over the Internet, it is imperative to monitor the network traffic so as to prevent malicious attackers from depleting the resources of the network and denying services to legitimate users. This paper first presents a brief discussion on some of the important types of DDoS attacks that currently exist and some existing mechanisms to combat these attacks. It then points out the major drawbacks of the currently existing defense mechanisms and proposes a new mechanism for protecting a web-server against a DDoS attack. In the proposed mechanism, incoming traffic to the server is continuously monitored and any abnormal rise in the inbound traffic is immediately detected. The detection algorithm is based on a statistical analysis of the inbound traffic on the server and a robust hypothesis testing framework. While the detection process is on, the sessions from the legitimate sources are not disrupted and the load on the server is restored to the normal level by blocking the traffic from the attacking sources. To cater to different scenarios, the detection algorithm has various modules with varying level of computational and memory overheads for
their execution. While the approximate modules are fast in detection and involve less overhead, they provide lower level of detection accuracy. The accurate modules employ complex detection logic and hence involve more overhead for their execution. However, they have very high detection accuracy. Simulations carried out on the proposed mechanism have produced results that demonstrate effectiveness of the proposed defense mechanism against DDoS attacks.12 types of DDoS attacks



12 types of DDoS attacksHaltdos
╠²
A DDoS attack can have the potential to bring down any
business to its knees.This document gives a brief overview of various types of DDoS attacks. Design and Implementation of Artificial Immune System for Detecting Flooding ...



Design and Implementation of Artificial Immune System for Detecting Flooding ...Kent State University
╠²
Academic Paper: N. B. I. Al-Dabagh and I. A. Ali, "Design and implementation of artificial immune system for detecting flooding attacks," in High Performance Computing and Simulation (HPCS), 2011 International Conference on, 2011, pp. 381-390. DISTRIBUTED DENIAL OF SERVICE (DDOS) ATTACKS DETECTION MECHANISM



DISTRIBUTED DENIAL OF SERVICE (DDOS) ATTACKS DETECTION MECHANISMijcseit
╠²
Pushback is a mechanism for defending against Distributed Denial-of-Service (DDoS) attacks. DDoS attacks are treated as a congestion-control problem, but because most such congestion is caused by malicious hosts not obeying traditional end-to-end congestion control, the problem must be handled by the routers. Functionality is added to each router to detect and preferentially drop packets that probably belong to an attack. Upstream routers are also notified to drop such packets in order that the routerŌĆÖs resources be used to route legitimate traffic hence term pushback. Client puzzles have been advocated as a
promising countermeasure to DoS attacks in the recent years. In order to identify the attackers, the victim server issues a puzzle to the client that sent the traffic. When the client is able to solve the puzzle, it is assumed to be authentic and the traffic from it is allowed into the server. If the victim suspects that the
puzzles are solved by most of the clients, it increases the complexity of the puzzles. This puzzle solving technique allows the traversal of the attack traffic throughout the intermediate routers before reaching the destination. In order to attain the advantages of both pushback and puzzle solving techniques, a hybrid scheme called Router based Pushback technique, which involves both the techniques to solve the problem of DDoS attacks is proposed. In this proposal, the puzzle solving mechanism is pushed back to the core routers rather than having at the victim. The router based client puzzle mechanism checks the host system whether it is legitimate or not by providing a puzzle to be solved by the suspected host. DISTRIBUTED DENIAL OF SERVICE (DDOS) ATTACKS DETECTION MECHANISM 



DISTRIBUTED DENIAL OF SERVICE (DDOS) ATTACKS DETECTION MECHANISM ijcseit
╠²
Pushback is a mechanism for defending against Distributed Denial-of-Service (DDoS) attacks. DDoS
attacks are treated as a congestion-control problem, but because most such congestion is caused by
malicious hosts not obeying traditional end-to-end congestion control, the problem must be handled by the
routers. Functionality is added to each router to detect and preferentially drop packets that probably
belong to an attack. Upstream routers are also notified to drop such packets in order that the routerŌĆÖs
resources be used to route legitimate traffic hence term pushback. Client puzzles have been advocated as a
promising countermeasure to DoS attacks in the recent years. In order to identify the attackers, the victim
server issues a puzzle to the client that sent the traffic. When the client is able to solve the puzzle, it is
assumed to be authentic and the traffic from it is allowed into the server. If the victim suspects that the
puzzles are solved by most of the clients, it increases the complexity of the puzzles. This puzzle solving
technique allows the traversal of the attack traffic throughout the intermediate routers before reaching the
destination. In order to attain the advantages of both pushback and puzzle solving techniques, a hybrid
scheme called Router based Pushback technique, which involves both the techniques to solve the problem
of DDoS attacks is proposed. In this proposal, the puzzle solving mechanism is pushed back to the core
routers rather than having at the victim. The router based client puzzle mechanism checks the host system
whether it is legitimate or not by providing a puzzle to be solved by the suspected host. What is a TCP Flood Attack.pdf



What is a TCP Flood Attack.pdfuzair
╠²
Resource exhaustion
Detection and Prevention of TCP Flood Attacks
Intrusion Detection Systems (IDS)
Firewalls and access control measures
Rate limiting and traffic shaping
Mitigation Strategies for TCP Flood Attacks
IP blocking and filtering
SYN cookies and TCP sequence number randomization
Load balancing and traffic diversion
Case Studies of TCP Flood Attacks
Notable real-world examples
Protecting Against TCP Flood Attacks: Best Practices
Regular security audits and updates
Network segmentation and isolation
Collaborative threat intelligence sharing
Conclusion
Understanding TCP Flood Attacks
TCP Flood Attacks are a form of cyber attack that aims to overwhelm and disrupt computer networks by exploiting vulnerabilities in the Transmission Control Protocol (TCP). As one of the fundamental protocols of the internet, TCP plays a crucial role in ensuring reliable and ordered data transmission between devices. However, malicious actors can manipulate the protocol to flood target systems with a high volume of TCP connection requests, leading to network congestion, service disruptions, and resource exhaustion.
What is a TCP Flood Attack?
To understand TCP Flood Attacks, itŌĆÖs essential to grasp the basics of the TCP protocol. TCP operates as a connection-oriented protocol that provides reliable, error-checked data transmission across networks. It guarantees that data packets sent from one device reach the destination device in the correct order.
A TCP Flood Attack occurs when an attacker floods a target system with an overwhelming number of TCP connection requests. The attack is typically launched using botnets, which are networks of compromised devices controlled by the attacker. By initiating a large number of TCP connections simultaneously, the attacker aims to exhaust the target systemŌĆÖs resources and overload its capacity to handle legitimate network traffic.
How TCP Flood Attacks Work
TCP Flood Attacks follow a specific pattern to disrupt network communications.
Step 1: Reconnaissance: The attacker identifies potential target systems by scanning IP addresses or exploiting vulnerabilities in poorly secured devices.
Step 2: TCP Connection Initiation: The attacker uses a botnet to send a flood of TCP connection requests to the target system.
Step 3: Target System Response: The target system receives the TCP connection requests and allocates system resources to establish connections.
Step 4: Resource Exhaustion: As the number of connection requests overwhelms the target systemŌĆÖs capacity, resources such as memory, processing power, and network bandwidth become depleted.
Step 5: Service Disruption: The target system becomes unable to handle legitimate network traffic, resulting in network congestion, slowdowns, and potential service outages.
Types of TCP Flood Attacks
TCP Flood Attacks can manifest in different forms, each targeting specific aspects of the TCP protocol. Some common types of TCP Flood Attacks include:
SYN Flood Attacks
SYN Flood AttaDrdos



DrdosMarc Manthey
╠²
DRDoS is the latest in the series of Denial of Service attacks. An explanation of the history of this type of attack is in order to fully understand the ramifications of this new threat.http://servv89pn0aj.sn.sourcedns.com/~gbpprorg/2600/DRDoS-Spyrochaete.htmlIx3615551559



Ix3615551559IJERA Editor
╠²
International Journal of Engineering Research and Applications (IJERA) is an open access online peer reviewed international journal that publishes research and review articles in the fields of Computer Science, Neural Networks, Electrical Engineering, Software Engineering, Information Technology, Mechanical Engineering, Chemical Engineering, Plastic Engineering, Food Technology, Textile Engineering, Nano Technology & science, Power Electronics, Electronics & Communication Engineering, Computational mathematics, Image processing, Civil Engineering, Structural Engineering, Environmental Engineering, VLSI Testing & Low Power VLSI Design etc.Dos.pptx



Dos.pptxextralargesand
╠²
This document discusses several types of denial of service (DoS) attacks, including distributed denial of service (DDoS) attacks. It describes how a DDoS attack uses multiple compromised systems or "zombies" to launch a large-scale attack. It also explains specific DoS attack methods like Smurf attacks, which flood a target with ping replies by spoofing the target's IP address, and SYN flood attacks, which exploit the TCP three-way handshake process to overwhelm a server with half-open connections. The document provides technical details on how various DoS attacks work to crash systems or make networks and services unavailable.Internet Security Issues



Internet Security Issuesanides
╠²
This document discusses various internet security issues such as web spoofing, denial of service attacks, trojans, and SQL injection attacks. It provides details on how each attack works from the perspective of a hacker, including how web spoofing allows monitoring of a victim's online activities, how SYN flooding can be used in DoS attacks, how trojans can hide in a system's registry and startup folders to gain remote access, and how SQL injection can exploit poorly designed database queries. The intention is to help system administrators understand these threats to better secure their systems.Enhancing the impregnability of linux servers



Enhancing the impregnability of linux serversIJNSA Journal
╠²
Worldwide IT industry is experiencing a rapid shift towards Service Oriented Architecture (SOA). As a
response to the current trend, all the IT firms are adopting business models such as cloud based services
which rely on reliable and highly available server platforms. Linux servers are known to be highly
secure. Network security thus becomes a major concern to all IT organizations offering cloud based
services. The fundamental form of attack on network security is Denial of Service. This paper focuses on
fortifying the Linux server defence mechanisms resulting in an increase in reliability and availability of
services offered by the Linux server platforms. To meet this emerging scenario, most of the organizations
are adopting business models such as cloud computing that are dependant on reliable server platforms.
Linux servers are well ahead of other server platforms in terms of security. This brings network security
to the forefront of major concerns to an organization. The most common form of attacks is a Denial of
Service attack. This paper focuses on mechanisms to detect and immunize Linux servers from DoS .ENHANCING THE IMPREGNABILITY OF LINUX SERVERS



ENHANCING THE IMPREGNABILITY OF LINUX SERVERSIJNSA Journal
╠²
Worldwide IT industry is experiencing a rapid shift towards Service Oriented Architecture (SOA). As a response to the current trend, all the IT firms are adopting business models such as cloud based services which rely on reliable and highly available server platforms. Linux servers are known to be highly secure. Network security thus becomes a major concern to all IT organizations offering cloud based services. The fundamental form of attack on network security is Denial of Service. This paper focuses on fortifying the Linux server defence mechanisms resulting in an increase in reliability and availability of services offered by the Linux server platforms. To meet this emerging scenario, most of the organizations are adopting business models such as cloud computing that are dependant on reliable server platforms. Linux servers are well ahead of other server platforms in terms of security. This brings network security to the forefront of major concerns to an organization. The most common form of attacks is a Denial of Service attack. This paper focuses on mechanisms to detect and immunize Linux servers from DoS .
Denial of Service Attacks (DoS/DDoS)



Denial of Service Attacks (DoS/DDoS)Gaurav Sharma
╠²
This is a presentation i made about Denial of Service or a Distributed Denial of Service (DoS / DDoS) and the latest methods used to crash anything online and the future of such attacks which can disrupt the whole internet . Such attacks which are in TB's and can be launched from just single computer. And, there is not much that can be done to prevent them. Protection of server from syn flood attack



Protection of server from syn flood attackIAEME Publication
╠²
This document summarizes a research paper that proposes a method to protect servers from SYN flood attacks. The method uses an algorithm with a continuous self-detecting process to identify and update information about genuine clients, even in the presence of spoofed packets. It builds a repository of genuine client information that can then be used by security systems like intrusion detection systems and packet filtering to further protect the server. The performance of the SYN flood attack protection could also be improved by implementing the algorithm in hardware using an FPGA.Mattias eriksson



Mattias erikssonHai Nguyen
╠²
The document describes a man-in-the-middle attack against server-authenticated SSL sessions. It discusses how an attacker can: (1) redirect traffic by manipulating DNS or network topology; (2) sniff and modify traffic in real-time using a program; and (3) forward modified traffic while handling SSL/TLS encryption to avoid detection. The attack relies on flaws in SSL/TLS implementation and users' tendency to ignore security warnings to intercept secure connections without triggering alerts.DoS/DDoS



DoS/DDoSVihari Piratla
╠²
describes about DoS/DDoS attacks, popular methods of carrying the attack and some mitigation techniques.A10 issa d do s 5-2014



A10 issa d do s 5-2014Raleigh ISSA
╠²
This document discusses the growing threat of distributed denial of service (DDoS) attacks and strategies for mitigating them. It notes that DDoS attacks are increasing in size and sophistication, with some now reaching hundreds of gigabits per second. The document outlines different types of network layer and application layer DDoS attacks and examines methods that can be used to detect and prevent these attacks, such as packet anomaly checking, blacklisting, authentication, rate limiting, and protocol inspection. It also describes A10 Networks' Thunder TPS appliance for high-performance DDoS mitigation.UiPath Automation Developer Associate Training Series 2025 - Session 2



UiPath Automation Developer Associate Training Series 2025 - Session 2DianaGray10
╠²
In session 2, we will introduce you to Data manipulation in UiPath Studio.
Topics covered:
Data Manipulation
What is Data Manipulation
Strings
Lists
Dictionaries
RegEx Builder
Date and Time
Required Self-Paced Learning for this session:
Data Manipulation with Strings in UiPath Studio (v2022.10) 2 modules - 1h 30m - https://academy.uipath.com/courses/data-manipulation-with-strings-in-studio
Data Manipulation with Lists and Dictionaries in UiPath Studio (v2022.10) 2 modules - 1h - https:/academy.uipath.com/courses/data-manipulation-with-lists-and-dictionaries-in-studio
Data Manipulation with Data Tables in UiPath Studio (v2022.10) 2 modules - 1h 30m - https:/academy.uipath.com/courses/data-manipulation-with-data-tables-in-studio
Ōüē’ĖÅ For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. MIND Revenue Release Quarter 4 2024 - Finacial Presentation



MIND Revenue Release Quarter 4 2024 - Finacial PresentationMIND CTI
╠²
MIND Revenue Release Quarter 4 2024 - Finacial PresentationMore Related Content
Similar to How to mitigate tcp syn flood attacks (20)
MS_ISAC__DDoS_Attacks_Guide__2023_05.pdf



MS_ISAC__DDoS_Attacks_Guide__2023_05.pdfssuser262297
╠²
The document provides an overview of common DDoS attack types including SYN floods, UDP floods, ICMP floods, and HTTP floods. It describes how these attacks work to overwhelm servers and networks with traffic to cause denial of service. The document also covers reflection DDoS attacks using protocols like DNS, NTP, and Memcached to amplify the traffic and discusses recommendations for mitigating these attacks.DoS Attacks



DoS AttacksVladimir Menshikov
╠²
The document discusses denial of service (DoS) attacks, specifically SYN flooding and DNS amplification attacks. It describes how these attacks work by exploiting vulnerabilities in TCP connections and DNS servers. The document outlines the development of attack clients to launch SYN flooding and DNS amplification attacks against a server. It also details how the server was designed to detect and mitigate SYN flooding attacks by tracking and flushing incomplete connection requests. The server was able to withstand SYN flooding attacks but could not defend against DNS amplification. Evaluation results show the server had near perfect detection rates for SYN flooding but occasional dropped legitimate connections under high volume attacks.A ROBUST MECHANISM FOR DEFENDING DISTRIBUTED DENIAL OF SERVICE ATTACKS ON WEB...



A ROBUST MECHANISM FOR DEFENDING DISTRIBUTED DENIAL OF SERVICE ATTACKS ON WEB...IJNSA Journal
╠²
Distributed Denial of Service (DDoS) attacks have emerged as a popular means of causing mass targeted service disruptions, often for extended periods of time. The relative ease and low costs of launching such attacks, supplemented by the current inadequate sate of any viable defense mechanism, have made them one of the top threats to the Internet community today. Since the increasing popularity of web-based applications has led to several critical services being provided over the Internet, it is imperative to monitor the network traffic so as to prevent malicious attackers from depleting the resources of the network and denying services to legitimate users. This paper first presents a brief discussion on some of the important types of DDoS attacks that currently exist and some existing mechanisms to combat these attacks. It then points out the major drawbacks of the currently existing defense mechanisms and proposes a new mechanism for protecting a web-server against a DDoS attack. In the proposed mechanism, incoming traffic to the server is continuously monitored and any abnormal rise in the inbound traffic is immediately detected. The detection algorithm is based on a statistical analysis of the inbound traffic on the server and a robust hypothesis testing framework. While the detection process is on, the sessions from the legitimate sources are not disrupted and the load on the server is restored to the normal level by blocking the traffic from the attacking sources. To cater to different scenarios, the detection algorithm has various modules with varying level of computational and memory overheads for
their execution. While the approximate modules are fast in detection and involve less overhead, they provide lower level of detection accuracy. The accurate modules employ complex detection logic and hence involve more overhead for their execution. However, they have very high detection accuracy. Simulations carried out on the proposed mechanism have produced results that demonstrate effectiveness of the proposed defense mechanism against DDoS attacks.12 types of DDoS attacks



12 types of DDoS attacksHaltdos
╠²
A DDoS attack can have the potential to bring down any
business to its knees.This document gives a brief overview of various types of DDoS attacks. Design and Implementation of Artificial Immune System for Detecting Flooding ...



Design and Implementation of Artificial Immune System for Detecting Flooding ...Kent State University
╠²
Academic Paper: N. B. I. Al-Dabagh and I. A. Ali, "Design and implementation of artificial immune system for detecting flooding attacks," in High Performance Computing and Simulation (HPCS), 2011 International Conference on, 2011, pp. 381-390. DISTRIBUTED DENIAL OF SERVICE (DDOS) ATTACKS DETECTION MECHANISM



DISTRIBUTED DENIAL OF SERVICE (DDOS) ATTACKS DETECTION MECHANISMijcseit
╠²
Pushback is a mechanism for defending against Distributed Denial-of-Service (DDoS) attacks. DDoS attacks are treated as a congestion-control problem, but because most such congestion is caused by malicious hosts not obeying traditional end-to-end congestion control, the problem must be handled by the routers. Functionality is added to each router to detect and preferentially drop packets that probably belong to an attack. Upstream routers are also notified to drop such packets in order that the routerŌĆÖs resources be used to route legitimate traffic hence term pushback. Client puzzles have been advocated as a
promising countermeasure to DoS attacks in the recent years. In order to identify the attackers, the victim server issues a puzzle to the client that sent the traffic. When the client is able to solve the puzzle, it is assumed to be authentic and the traffic from it is allowed into the server. If the victim suspects that the
puzzles are solved by most of the clients, it increases the complexity of the puzzles. This puzzle solving technique allows the traversal of the attack traffic throughout the intermediate routers before reaching the destination. In order to attain the advantages of both pushback and puzzle solving techniques, a hybrid scheme called Router based Pushback technique, which involves both the techniques to solve the problem of DDoS attacks is proposed. In this proposal, the puzzle solving mechanism is pushed back to the core routers rather than having at the victim. The router based client puzzle mechanism checks the host system whether it is legitimate or not by providing a puzzle to be solved by the suspected host. DISTRIBUTED DENIAL OF SERVICE (DDOS) ATTACKS DETECTION MECHANISM 



DISTRIBUTED DENIAL OF SERVICE (DDOS) ATTACKS DETECTION MECHANISM ijcseit
╠²
Pushback is a mechanism for defending against Distributed Denial-of-Service (DDoS) attacks. DDoS
attacks are treated as a congestion-control problem, but because most such congestion is caused by
malicious hosts not obeying traditional end-to-end congestion control, the problem must be handled by the
routers. Functionality is added to each router to detect and preferentially drop packets that probably
belong to an attack. Upstream routers are also notified to drop such packets in order that the routerŌĆÖs
resources be used to route legitimate traffic hence term pushback. Client puzzles have been advocated as a
promising countermeasure to DoS attacks in the recent years. In order to identify the attackers, the victim
server issues a puzzle to the client that sent the traffic. When the client is able to solve the puzzle, it is
assumed to be authentic and the traffic from it is allowed into the server. If the victim suspects that the
puzzles are solved by most of the clients, it increases the complexity of the puzzles. This puzzle solving
technique allows the traversal of the attack traffic throughout the intermediate routers before reaching the
destination. In order to attain the advantages of both pushback and puzzle solving techniques, a hybrid
scheme called Router based Pushback technique, which involves both the techniques to solve the problem
of DDoS attacks is proposed. In this proposal, the puzzle solving mechanism is pushed back to the core
routers rather than having at the victim. The router based client puzzle mechanism checks the host system
whether it is legitimate or not by providing a puzzle to be solved by the suspected host. What is a TCP Flood Attack.pdf



What is a TCP Flood Attack.pdfuzair
╠²
Resource exhaustion
Detection and Prevention of TCP Flood Attacks
Intrusion Detection Systems (IDS)
Firewalls and access control measures
Rate limiting and traffic shaping
Mitigation Strategies for TCP Flood Attacks
IP blocking and filtering
SYN cookies and TCP sequence number randomization
Load balancing and traffic diversion
Case Studies of TCP Flood Attacks
Notable real-world examples
Protecting Against TCP Flood Attacks: Best Practices
Regular security audits and updates
Network segmentation and isolation
Collaborative threat intelligence sharing
Conclusion
Understanding TCP Flood Attacks
TCP Flood Attacks are a form of cyber attack that aims to overwhelm and disrupt computer networks by exploiting vulnerabilities in the Transmission Control Protocol (TCP). As one of the fundamental protocols of the internet, TCP plays a crucial role in ensuring reliable and ordered data transmission between devices. However, malicious actors can manipulate the protocol to flood target systems with a high volume of TCP connection requests, leading to network congestion, service disruptions, and resource exhaustion.
What is a TCP Flood Attack?
To understand TCP Flood Attacks, itŌĆÖs essential to grasp the basics of the TCP protocol. TCP operates as a connection-oriented protocol that provides reliable, error-checked data transmission across networks. It guarantees that data packets sent from one device reach the destination device in the correct order.
A TCP Flood Attack occurs when an attacker floods a target system with an overwhelming number of TCP connection requests. The attack is typically launched using botnets, which are networks of compromised devices controlled by the attacker. By initiating a large number of TCP connections simultaneously, the attacker aims to exhaust the target systemŌĆÖs resources and overload its capacity to handle legitimate network traffic.
How TCP Flood Attacks Work
TCP Flood Attacks follow a specific pattern to disrupt network communications.
Step 1: Reconnaissance: The attacker identifies potential target systems by scanning IP addresses or exploiting vulnerabilities in poorly secured devices.
Step 2: TCP Connection Initiation: The attacker uses a botnet to send a flood of TCP connection requests to the target system.
Step 3: Target System Response: The target system receives the TCP connection requests and allocates system resources to establish connections.
Step 4: Resource Exhaustion: As the number of connection requests overwhelms the target systemŌĆÖs capacity, resources such as memory, processing power, and network bandwidth become depleted.
Step 5: Service Disruption: The target system becomes unable to handle legitimate network traffic, resulting in network congestion, slowdowns, and potential service outages.
Types of TCP Flood Attacks
TCP Flood Attacks can manifest in different forms, each targeting specific aspects of the TCP protocol. Some common types of TCP Flood Attacks include:
SYN Flood Attacks
SYN Flood AttaDrdos



DrdosMarc Manthey
╠²
DRDoS is the latest in the series of Denial of Service attacks. An explanation of the history of this type of attack is in order to fully understand the ramifications of this new threat.http://servv89pn0aj.sn.sourcedns.com/~gbpprorg/2600/DRDoS-Spyrochaete.htmlIx3615551559



Ix3615551559IJERA Editor
╠²
International Journal of Engineering Research and Applications (IJERA) is an open access online peer reviewed international journal that publishes research and review articles in the fields of Computer Science, Neural Networks, Electrical Engineering, Software Engineering, Information Technology, Mechanical Engineering, Chemical Engineering, Plastic Engineering, Food Technology, Textile Engineering, Nano Technology & science, Power Electronics, Electronics & Communication Engineering, Computational mathematics, Image processing, Civil Engineering, Structural Engineering, Environmental Engineering, VLSI Testing & Low Power VLSI Design etc.Dos.pptx



Dos.pptxextralargesand
╠²
This document discusses several types of denial of service (DoS) attacks, including distributed denial of service (DDoS) attacks. It describes how a DDoS attack uses multiple compromised systems or "zombies" to launch a large-scale attack. It also explains specific DoS attack methods like Smurf attacks, which flood a target with ping replies by spoofing the target's IP address, and SYN flood attacks, which exploit the TCP three-way handshake process to overwhelm a server with half-open connections. The document provides technical details on how various DoS attacks work to crash systems or make networks and services unavailable.Internet Security Issues



Internet Security Issuesanides
╠²
This document discusses various internet security issues such as web spoofing, denial of service attacks, trojans, and SQL injection attacks. It provides details on how each attack works from the perspective of a hacker, including how web spoofing allows monitoring of a victim's online activities, how SYN flooding can be used in DoS attacks, how trojans can hide in a system's registry and startup folders to gain remote access, and how SQL injection can exploit poorly designed database queries. The intention is to help system administrators understand these threats to better secure their systems.Enhancing the impregnability of linux servers



Enhancing the impregnability of linux serversIJNSA Journal
╠²
Worldwide IT industry is experiencing a rapid shift towards Service Oriented Architecture (SOA). As a
response to the current trend, all the IT firms are adopting business models such as cloud based services
which rely on reliable and highly available server platforms. Linux servers are known to be highly
secure. Network security thus becomes a major concern to all IT organizations offering cloud based
services. The fundamental form of attack on network security is Denial of Service. This paper focuses on
fortifying the Linux server defence mechanisms resulting in an increase in reliability and availability of
services offered by the Linux server platforms. To meet this emerging scenario, most of the organizations
are adopting business models such as cloud computing that are dependant on reliable server platforms.
Linux servers are well ahead of other server platforms in terms of security. This brings network security
to the forefront of major concerns to an organization. The most common form of attacks is a Denial of
Service attack. This paper focuses on mechanisms to detect and immunize Linux servers from DoS .ENHANCING THE IMPREGNABILITY OF LINUX SERVERS



ENHANCING THE IMPREGNABILITY OF LINUX SERVERSIJNSA Journal
╠²
Worldwide IT industry is experiencing a rapid shift towards Service Oriented Architecture (SOA). As a response to the current trend, all the IT firms are adopting business models such as cloud based services which rely on reliable and highly available server platforms. Linux servers are known to be highly secure. Network security thus becomes a major concern to all IT organizations offering cloud based services. The fundamental form of attack on network security is Denial of Service. This paper focuses on fortifying the Linux server defence mechanisms resulting in an increase in reliability and availability of services offered by the Linux server platforms. To meet this emerging scenario, most of the organizations are adopting business models such as cloud computing that are dependant on reliable server platforms. Linux servers are well ahead of other server platforms in terms of security. This brings network security to the forefront of major concerns to an organization. The most common form of attacks is a Denial of Service attack. This paper focuses on mechanisms to detect and immunize Linux servers from DoS .
Denial of Service Attacks (DoS/DDoS)



Denial of Service Attacks (DoS/DDoS)Gaurav Sharma
╠²
This is a presentation i made about Denial of Service or a Distributed Denial of Service (DoS / DDoS) and the latest methods used to crash anything online and the future of such attacks which can disrupt the whole internet . Such attacks which are in TB's and can be launched from just single computer. And, there is not much that can be done to prevent them. Protection of server from syn flood attack



Protection of server from syn flood attackIAEME Publication
╠²
This document summarizes a research paper that proposes a method to protect servers from SYN flood attacks. The method uses an algorithm with a continuous self-detecting process to identify and update information about genuine clients, even in the presence of spoofed packets. It builds a repository of genuine client information that can then be used by security systems like intrusion detection systems and packet filtering to further protect the server. The performance of the SYN flood attack protection could also be improved by implementing the algorithm in hardware using an FPGA.Mattias eriksson



Mattias erikssonHai Nguyen
╠²
The document describes a man-in-the-middle attack against server-authenticated SSL sessions. It discusses how an attacker can: (1) redirect traffic by manipulating DNS or network topology; (2) sniff and modify traffic in real-time using a program; and (3) forward modified traffic while handling SSL/TLS encryption to avoid detection. The attack relies on flaws in SSL/TLS implementation and users' tendency to ignore security warnings to intercept secure connections without triggering alerts.DoS/DDoS



DoS/DDoSVihari Piratla
╠²
describes about DoS/DDoS attacks, popular methods of carrying the attack and some mitigation techniques.A10 issa d do s 5-2014



A10 issa d do s 5-2014Raleigh ISSA
╠²
This document discusses the growing threat of distributed denial of service (DDoS) attacks and strategies for mitigating them. It notes that DDoS attacks are increasing in size and sophistication, with some now reaching hundreds of gigabits per second. The document outlines different types of network layer and application layer DDoS attacks and examines methods that can be used to detect and prevent these attacks, such as packet anomaly checking, blacklisting, authentication, rate limiting, and protocol inspection. It also describes A10 Networks' Thunder TPS appliance for high-performance DDoS mitigation.Design and Implementation of Artificial Immune System for Detecting Flooding ...



Design and Implementation of Artificial Immune System for Detecting Flooding ...Kent State University
╠²
Recently uploaded (20)
UiPath Automation Developer Associate Training Series 2025 - Session 2



UiPath Automation Developer Associate Training Series 2025 - Session 2DianaGray10
╠²
In session 2, we will introduce you to Data manipulation in UiPath Studio.
Topics covered:
Data Manipulation
What is Data Manipulation
Strings
Lists
Dictionaries
RegEx Builder
Date and Time
Required Self-Paced Learning for this session:
Data Manipulation with Strings in UiPath Studio (v2022.10) 2 modules - 1h 30m - https://academy.uipath.com/courses/data-manipulation-with-strings-in-studio
Data Manipulation with Lists and Dictionaries in UiPath Studio (v2022.10) 2 modules - 1h - https:/academy.uipath.com/courses/data-manipulation-with-lists-and-dictionaries-in-studio
Data Manipulation with Data Tables in UiPath Studio (v2022.10) 2 modules - 1h 30m - https:/academy.uipath.com/courses/data-manipulation-with-data-tables-in-studio
Ōüē’ĖÅ For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. MIND Revenue Release Quarter 4 2024 - Finacial Presentation



MIND Revenue Release Quarter 4 2024 - Finacial PresentationMIND CTI
╠²
MIND Revenue Release Quarter 4 2024 - Finacial PresentationTechnology use over time and its impact on consumers and businesses.pptx



Technology use over time and its impact on consumers and businesses.pptxkaylagaze
╠²
In this presentation, I explore how technology has changed consumer behaviour and its impact on consumers and businesses. I will focus on internet access, digital devices, how customers search for information and what they buy online, video consumption, and lastly consumer trends.The Future of Repair: Transparent and Incremental by Botond Dénes



The Future of Repair: Transparent and Incremental by Botond DénesScyllaDB
╠²
Regularly run repairs are essential to keep clusters healthy, yet having a good repair schedule is more challenging than it should be. Repairs often take a long time, preventing running them often. This has an impact on data consistency and also limits the usefulness of the new repair based tombstone garbage collection. We want to address these challenges by making repairs incremental and allowing for automatic repair scheduling, without relying on external tools.Brave Browser Crack 1.45.133 Activated 2025



Brave Browser Crack 1.45.133 Activated 2025kherorpacca00126
╠²
https://ncracked.com/7961-2/
Note: >> Please copy the link and paste it into Google New Tab now Download link
Brave is a free Chromium browser developed for Win Downloads, macOS and Linux systems that allows users to browse the internet in a safer, faster and more secure way than its competition. Designed with security in mind, Brave automatically blocks ads and trackers which also makes it faster,
As Brave naturally blocks unwanted content from appearing in your browser, it prevents these trackers and pop-ups from slowing Download your user experience. It's also designed in a way that strips Downloaden which data is being loaded each time you use it. Without these components
Field Device Management Market Report 2030 - TechSci Research



Field Device Management Market Report 2030 - TechSci ResearchVipin Mishra
╠²
The Global Field Device Management (FDM) Market is expected to experience significant growth in the forecast period from 2026 to 2030, driven by the integration of advanced technologies aimed at improving industrial operations.
¤ōŖ According to TechSci Research, the Global Field Device Management Market was valued at USD 1,506.34 million in 2023 and is anticipated to grow at a CAGR of 6.72% through 2030. FDM plays a vital role in the centralized oversight and optimization of industrial field devices, including sensors, actuators, and controllers.
Key tasks managed under FDM include:
Configuration
Monitoring
Diagnostics
Maintenance
Performance optimization
FDM solutions offer a comprehensive platform for real-time data collection, analysis, and decision-making, enabling:
Proactive maintenance
Predictive analytics
Remote monitoring
By streamlining operations and ensuring compliance, FDM enhances operational efficiency, reduces downtime, and improves asset reliability, ultimately leading to greater performance in industrial processes. FDMŌĆÖs emphasis on predictive maintenance is particularly important in ensuring the long-term sustainability and success of industrial operations.
For more information, explore the full report: https://shorturl.at/EJnzR
Major companies operating in Global╠²Field Device Management Market are:
General Electric Co
Siemens AG
ABB Ltd
Emerson Electric Co
Aveva Group Ltd
Schneider Electric SE
STMicroelectronics Inc
Techno Systems Inc
Semiconductor Components Industries LLC
International Business Machines Corporation (IBM)
#FieldDeviceManagement #IndustrialAutomation #PredictiveMaintenance #TechInnovation #IndustrialEfficiency #RemoteMonitoring #TechAdvancements #MarketGrowth #OperationalExcellence #SensorsAndActuatorsWhat Makes "Deep Research"? A Dive into AI Agents



What Makes "Deep Research"? A Dive into AI AgentsZilliz
╠²
About this webinar:
Unless you live under a rock, you will have heard about OpenAIŌĆÖs release of Deep Research on Feb 2, 2025. This new product promises to revolutionize how we answer questions requiring the synthesis of large amounts of diverse information. But how does this technology work, and why is Deep Research a noticeable improvement over previous attempts? In this webinar, we will examine the concepts underpinning modern agents using our basic clone, Deep Searcher, as an example.
Topics covered:
Tool use
Structured output
Reflection
Reasoning models
Planning
Types of agentic memorySMART SENTRY CYBER THREAT INTELLIGENCE IN IIOT



SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTTanmaiArni
╠²
SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTEndpoint Backup: 3 Reasons MSPs Ignore It



Endpoint Backup: 3 Reasons MSPs Ignore ItMSP360
╠²
Many MSPs overlook endpoint backup, missing out on additional profit and leaving a gap that puts client data at risk.
Join our webinar as we break down the top challenges of endpoint backupŌĆöand how to overcome them.Unlocking DevOps Secuirty :Vault & Keylock



Unlocking DevOps Secuirty :Vault & KeylockHusseinMalikMammadli
╠²
DevOps i┼¤ t╔Öhl├╝k╔Ösizliyi sizi maraqland─▒r─▒r? ─░st╔Ör developer, ist╔Ör t╔Öhl├╝k╔Ösizlik m├╝h╔Öndisi, ist╔Örs╔Ö d╔Ö DevOps h╔Öv╔Öskar─▒ olun, bu t╔Ödbir ┼¤╔Öb╔Ök╔Öl╔Ö┼¤m╔Ök, bilikl╔Örinizi b├Čl├╝┼¤m╔Ök v╔Ö DevSecOps sah╔Ösind╔Ö ╔Ön son t╔Öcr├╝b╔Öl╔Öri ├Čyr╔Önm╔Ök ├╝├¦├╝n m├╝k╔Ömm╔Öl f├╝rs╔Ötdir!
Bu workshopda DevOps infrastrukturlar─▒n─▒n t╔Öhl├╝k╔Ösizliyini nec╔Ö art─▒rmaq bar╔Öd╔Ö dan─▒┼¤acay─▒q. DevOps sisteml╔Öri qurulark╔Ön avtomatla┼¤d─▒r─▒lm─▒┼¤, y├╝ks╔Ök ╔Öl├¦atan v╔Ö etibarl─▒ olmas─▒ il╔Ö yana┼¤─▒, h╔Öm d╔Ö t╔Öhl├╝k╔Ösizlik m╔Ös╔Öl╔Öl╔Öri n╔Öz╔Ör╔Ö al─▒nmal─▒d─▒r. Bu s╔Öb╔Öbd╔Ön, DevOps komandolar─▒n─▒n t╔Öhl├╝k╔Ösizliy╔Ö y├Čn╔Ölmi┼¤ praktikalara riay╔Öt etm╔Ösi vacibdir.DevNexus - Building 10x Development Organizations.pdf



DevNexus - Building 10x Development Organizations.pdfJustin Reock
╠²
Developer Experience is Dead! Long Live Developer Experience!
In this keynote-style session, weŌĆÖll take a detailed, granular look at the barriers to productivity developers face today and modern approaches for removing them. 10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, ŌĆśThe Coding War Games.ŌĆÖ
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method, we invent to deliver products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches works? DORA? SPACE? DevEx? What should we invest in and create urgency behind today so we donŌĆÖt have the same discussion again in a decade?Technology use over time and its impact on consumers and businesses.pptx



Technology use over time and its impact on consumers and businesses.pptxkaylagaze
╠²
In this presentation, I will discuss how technology has changed consumer behaviour and its impact on consumers and businesses. I will focus on internet access, digital devices, how customers search for information and what they buy online, video consumption, and lastly consumer trends.
Formal Methods: Whence and Whither? [Martin Fr├żnzle Festkolloquium, 2025]![Formal Methods: Whence and Whither? [Martin Fr├żnzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr├żnzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr├żnzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr├żnzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
Formal Methods: Whence and Whither? [Martin Fr├żnzle Festkolloquium, 2025]Jonathan Bowen
╠²
Alan Turing arguably wrote the first paper on formal methods 75 years ago. Since then, there have been claims and counterclaims about formal methods. Tool development has been slow but aided by MooreŌĆÖs Law with the increasing power of computers. Although formal methods are not widespread in practical usage at a heavyweight level, their influence as crept into software engineering practice to the extent that they are no longer necessarily called formal methods in their use. In addition, in areas where safety and security are important, with the increasing use of computers in such applications, formal methods are a viable way to improve the reliability of such software-based systems. Their use in hardware where a mistake can be very costly is also important. This talk explores the journey of formal methods to the present day and speculates on future directions.
BoxLang JVM Language : The Future is Dynamic



BoxLang JVM Language : The Future is DynamicOrtus Solutions, Corp
╠²
Just like life, our code must evolve to meet the demands of an ever-changing world. Adaptability is key in developing for the web, tablets, APIs, or serverless applications. Multi-runtime development is the future, and that future is dynamic. Enter BoxLang: Dynamic. Modular. Productive. (www.boxlang.io)
BoxLang transforms development with its dynamic design, enabling developers to write expressive, functional code effortlessly. Its modular architecture ensures flexibility, allowing easy integration into your existing ecosystems.
Interoperability at Its Core
BoxLang boasts 100% interoperability with Java, seamlessly blending traditional and modern development practices. This opens up new possibilities for innovation and collaboration.
Multi-Runtime Versatility
From a compact 6MB OS binary to running on our pure Java web server, CommandBox, Jakarta EE, AWS Lambda, Microsoft Functions, WebAssembly, Android, and more, BoxLang is designed to adapt to any runtime environment. BoxLang combines modern features from CFML, Node, Ruby, Kotlin, Java, and Clojure with the familiarity of Java bytecode compilation. This makes it the go-to language for developers looking to the future while building a solid foundation.
Empowering Creativity with IDE Tools
Unlock your creative potential with powerful IDE tools designed for BoxLang, offering an intuitive development experience that streamlines your workflow. Join us as we redefine JVM development and step into the era of BoxLang. Welcome to the future.
UiPath Automation Developer Associate Training Series 2025 - Session 1



UiPath Automation Developer Associate Training Series 2025 - Session 1DianaGray10
╠²
Welcome to UiPath Automation Developer Associate Training Series 2025 - Session 1.
In this session, we will cover the following topics:
Introduction to RPA & UiPath Studio
Overview of RPA and its applications
Introduction to UiPath Studio
Variables & Data Types
Control Flows
You are requested to finish the following self-paced training for this session:
Variables, Constants and Arguments in Studio 2 modules - 1h 30m - https://academy.uipath.com/courses/variables-constants-and-arguments-in-studio
Control Flow in Studio 2 modules - 2h 15m - https:/academy.uipath.com/courses/control-flow-in-studio
Ōüē’ĖÅ For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. Build with AI on Google Cloud Session #4



Build with AI on Google Cloud Session #4Margaret Maynard-Reid
╠²
This is session #4 of the 5-session online study series with Google Cloud, where we take you onto the journey learning generative AI. YouŌĆÖll explore the dynamic landscape of Generative AI, gaining both theoretical insights and practical know-how of Google Cloud GenAI tools such as Gemini, Vertex AI, AI agents and Imagen 3. L01 Introduction to Nanoindentation - What is hardness



L01 Introduction to Nanoindentation - What is hardnessRostislavDaniel
╠²
Introduction to Nanoindentation30B Images and Counting: Scaling Canva's Content-Understanding Pipelines by K...



30B Images and Counting: Scaling Canva's Content-Understanding Pipelines by K...ScyllaDB
╠²
Scaling content understanding for billions of images is no easy feat. This talk dives into building extreme label classification models, balancing accuracy & speed, and optimizing ML pipelines for scale. You'll learn new ways to tackle real-time performance challenges in massive data environments.How to mitigate tcp syn flood attacks
- 1. How to Mitigate TCP Syn Flood Attacks From a user perspective, signing onto the internet is so straightforward that most people donŌĆÖt even question it. When your computer or mobile device connects to the internet, the process of logging onto the network and obtaining your unique internet address for sending and receiving data is all thanks to something called the internet protocol suite. Of this set of protocols, among the most critical is the transmission Control Protocol (TCP), the internet standard when it comes to the successful exchanging of data packets over a network. Whether itŌĆÖs email applications, peer-to-peer apps, FTP, or web servers and websites, the ŌĆŗTCP protocol is what makes everything possible when it comes to online communication. To work, a TCP connection needs to make what is referred to as a three-way handshake, involving both the client and the server. To begin the handshake, the client sends the server an SYN packet connection request. The server then answers with an SYN/ACK packet, which acknowledges the connection request has been made. As the last step, the client ŌĆö having received the SYN/ACK packet ŌĆö responds with an ACK packet. This process is technically referred to as the SYN, SYN-ACK, ACK sequence. The three-way handshake might sound like a simple greeting (a bit like saying ŌĆ£helloŌĆØ to a buddy, getting a ŌĆ£hey!ŌĆØ back, and then responding with another message to confirm that you were initiating a conversation), but itŌĆÖs an important interaction ŌĆö not least because it adds an element of security that protects against spoofing.
- 2. TCP has its weaknesses Source: amazonaws.com But TCP isnŌĆÖt infallible. ItŌĆÖs vulnerable to several types of DDoS (distributed denial of service) attacks. The most common of these is an SYN flood. In a DDoS attack, the attacker targets the victim with large quantities of junk traffic with the aim of overwhelming their system and causing it to become inaccessible to legitimate traffic. An SYN flood takes place during the three-way handshake process described above. The difference is that, unlike a normal SYN, SYN-ACK, ACK sequence, in an SYN flood attack these ŌĆ£helloŌĆØ requests are sent by the attacker to every port on a victimŌĆÖs machine at a rate that is faster than itŌĆÖs able to process. Overloaded by trying to process too many fake SYN requests at once, the machine stops being able to respond to legitimate TCP requests. This type of attack is also known as a TCP State-Exhaustion Attack. While the premise of the attack might sound simple, an SYN flood can bring even the highest capacity devices, capable of millions of connections, to a standstill. While an SYN flood counts as a DDoS attack, it is different in one keyway. A regular DDoS attack aims to use up a targetŌĆÖs memory. An SYN flood instead works by overloading the open connections that are connected to a port. Every time an SYN packet connection request is made, the TCP goes into a ŌĆ£listenŌĆØ state. Exploiting this behavior, the SYN flood causes the host to enter this state, responding to fake
- 3. half- connections, until it has no resources left. SYN floods are sometimes referred to as ŌĆ£half-openŌĆØ attacks for this reason. Defending against SYN flood vulnerabilities Source: cloudflare.com The vulnerability that could lead to a TCP SYN flood was first discovered as far back as 1994 by security researchers Bill Cheswick and Steve Bellovin. At the time, there was no existing countermeasure that could protect against such an attack. Fortunately, things have advanced in the years since. Several methods of mitigating SYN floods now exist. One such example is an SYN cookie, in which the server utilizes cryptographic hashing in order to confirm as legitimate a TCP request before allotting any memory to it. With an SYN cookie, the recipient responds with an SYN-ACK, but without adding a fresh record to its SYN Queue. Instead, it does this only when the SYN-ACK has been responded to (something that doesnŌĆÖt happen in an SYN flood attack). Another approach is an RST cookie, whereby the server will purposely send an incorrect response after it receives the initiating SYN request. In the case of a genuine request, the server will receive an RST packet that alerts the server that something has gone awry.
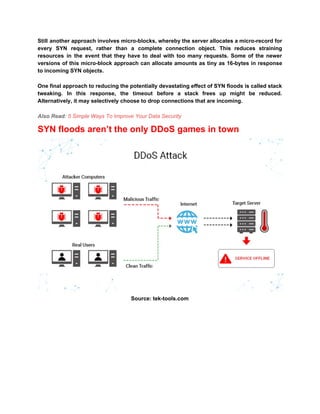
- 4. Still another approach involves micro-blocks, whereby the server allocates a micro-record for every SYN request, rather than a complete connection object. This reduces straining resources in the event that they have to deal with too many requests. Some of the newer versions of this micro-block approach can allocate amounts as tiny as 16-bytes in response to incoming SYN objects. One final approach to reducing the potentially devastating effect of SYN floods is called stack tweaking. In this response, the timeout before a stack frees up might be reduced. Alternatively, it may selectively choose to drop connections that are incoming. Also Read: ŌĆŗ5 Simple Ways To Improve Your Data Security SYN floods arenŌĆÖt the only DDoS games in town Source: tek-tools.com
- 5. Source: eetasia.com As noted, SYN floods are far from the only kind of DDoS attack users can face here in 2020. DDoS attacks can be extremely damaging, resulting in significant unwanted downtime and, potentially, financial and reputational losses in the event that it causes organizations to be able to service customers. DDoS attacks come in many forms, and each variant requires different approaches for dealing with them. As these attacks become more widespread and virulent, itŌĆÖs crucial that every organization is properly protected against them. Unless youŌĆÖre an authority on cybersecurity with a lot of time on your hands to keep up to date, itŌĆÖs a smart move to bring in the experts to help. There are plenty of things to occupy your time running a business or other organization. Adding ŌĆ£defending against all cyberattacksŌĆØ may be one task too many.
- 6. Contact Us : Website : ŌĆŗhttps://technographx.com Email IdŌĆŗ : ŌĆŗ ŌĆŗ ŌĆŗtechnographxofficial@gmail.com To Connect With Us Visit



