Medico di famiglia e stroke
Download as POT, PDF1 like114 views
Medico di famiglia e stroke
1 of 47
Download to read offline


























Recommended
1.8 notes



1.8 notesnglaze10
╠²
This document provides examples of solving equations by using properties of equality. It gives the identity property and shows that multiplying or dividing both sides of an equation by the same nonzero number preserves equality. It then has two examples of using these properties to solve equations: one set involves solving for x and y, and another set involves solving equations with fractions for t and l.G3 Social Media Security



G3 Social Media SecurityJerry Gamblin
╠²
Jerry Gamblin, a network security specialist for the Missouri House of Representatives, gave a presentation on social media security at the G3 Conference on April 2nd. He discussed what social media is and some popular sites, noting that over 500 million people use Facebook and 80 million use Twitter. Gamblin then covered some of the pitfalls of social media like cyberbullying and how employers and colleges now check profiles, before giving tips for improving security such as only friending people you know, removing old posts, using long passwords, and thinking before posting information online.The Display Ad of the Future: It's all about you - Marketing Land Summit 2014



The Display Ad of the Future: It's all about you - Marketing Land Summit 2014Tim Mayer
╠²
What does the future of online display advertising look like? A landscape very different than todayŌĆÖs, and one that disrupts current advertiser practices and beliefs. Ads will evolve from interruptions in other activities to voluntary views that users seek out. Ads will be more interactive, and beautiful. Ads will be connected across devices and time, and thanks to better retargeting will be more useful to your personal life. And measurement of ads will be much more complex and accurate, allowing advertisers to even more precisely tune messages to individuals ŌĆō at scale. Learn how to prepare for this exciting new world of display ads like youŌĆÖve never seen.05Mar14 - Missing 90 year olds



05Mar14 - Missing 90 year oldsILC- UK
╠²
During 2014, ILC-UK, supported by specialist insurance company, Partnership Assurance Group plc (Partnership), is undertaking a series of events to explore the relationship between our changing demography and public policy.
The second event in the series will explore how much we really know about life expectancy at the highest ages. How many of us are living to 90 and beyond? Why have estimates of life expectancy required revision? What does this tell us about increasing longevity? And what does this trend mean for public policy and long-term population planning?New week 10



New week 10nglaze10
╠²
This document contains a multi-part math problem about using similar triangles to estimate heights and distances. Part A asks students to use similar triangles to find the height of a building from given measurements. Part B asks students to use the mirror method with their group to estimate the height of an object and provide their measurements and explanation. Part C compares the estimates from Parts A and B and asks if they seem reasonable. Follow-up questions involve pooling the class data and comparing estimates from the two methods.Algebra 1 Semester 1 Review



Algebra 1 Semester 1 Reviewnglaze10
╠²
The document describes a classroom review game where:
1) The class will be split into two teams who will take turns answering review questions at the board.
2) The first student from each team to answer a question correctly will get to shoot a basket worth 1, 2, or 3 points.
3) The team with the most total points at the end will win a prize.5 Ways To Get Your Emails Opened First



5 Ways To Get Your Emails Opened FirstEmail Delivered
╠²
Email can be the most powerful, profitable, and inexpensive marketing tool out there, but the problem is that all of your competitors know this too. And with the amount of emails people get these days your message can easily go unopened, or even to spam. The goal is to get your emails opened right from the moment the subscribers sees it, and there are five steps to get that done. First, regard your subscribers as people instead of wallets, second, make your promotions help solve problems, third, make your email feel like content but also encourage a sale, fourth, write your emails so YOU would open them, and lastly, stay in touch.Chapter 2.4



Chapter 2.4nglaze10
╠²
This textbook section discusses the properties of multiplication, including rules for multiplying integers and properties (axioms) of multiplication such as commutativity, associativity, and distributivity. It also covers identifying properties through more algebraic proof and provides examples to use for homework problems 29 through 37.Chapter2.1



Chapter2.1nglaze10
╠²
The document provides examples and explanations for converting between fractions and decimals. It discusses terminating decimals, which end, and repeating decimals, which have a repeating pattern after the decimal point. Examples are given for writing fractions as decimals and decimals as fractions in simplest form. The steps shown include dividing the numerator by the denominator to write a fraction as a decimal, and identifying the place value of the decimal's final digit to write the decimal as a fraction.Creative superbclub concept dossier



Creative superbclub concept dossiercracktivo
╠²
Creative Superbclub es educaci├│n + entertainment = edutainmentWhy your password sucks



Why your password sucksJerry Gamblin
╠²
The document discusses the importance of strong passwords and passphrases and provides tips to improve password security. It notes that short passwords can now be cracked within minutes using cloud computing services. It recommends using passphrases that are at least 15 characters long instead of passwords, and enabling two-factor authentication for additional security. The document aims to educate readers on how to better protect their online accounts by using more robust credentials that are difficult for hackers to guess or crack through brute force attacks.New week 6



New week 6nglaze10
╠²
This document provides instructions and materials for a math lesson on similarity and scale factors. It includes examples of similar figures with questions about their side lengths, scale factors, and areas. It also discusses how police use measurements and similar figures to determine characteristics like a criminal's height from surveillance photos. Students are asked to use a photo of a teacher holding an object of known size to calculate the teacher's height, and to explain how police may have used a similar technique to determine a robber's height from a store surveillance photo.Can Spam Act: What You Should Know



Can Spam Act: What You Should KnowEmail Delivered
╠²
The CAN SPAM Act establishes seven key requirements for businesses sending commercial emails: 1) Don't use false or misleading header information. 2) Don't use deceptive subject lines. 3) Identify messages as advertisements. 4) Include your physical address. 5) Tell recipients how to opt out of future emails. 6) Honor opt-out requests promptly. 7) Monitor how others use your brand in emails.Spam Traps 101



Spam Traps 101Email Delivered
╠²
Spam Traps can cause big problems in your email program. In this article, we discuss what exactly spam traps ARE, the different types of spam traps, and the impact of spam traps on your sender reputation. There are essentially 3 different types of spam traps that you must be aware of - and pay attention to - in your email marketing program. It's also important to understand how they play a role in the overall health of your email program. Learn how spam traps make their way into your list, where spam traps come from, and how to prevent spam traps from getting onto your email list in the first place. Action aid child labor



Action aid child laborElpida Paf
╠²
╬Ā╬▒Žü╬┐ŽģŽā╬»╬▒Žā╬Ę Žä╬ĘŽé ActionAid ╬│╬╣╬▒ Žä╬▒ ╬┤╬╣╬║╬▒╬╣ŽÄ╬╝╬▒Žä╬▒ Žä╬┐Žģ ŽĆ╬▒╬╣╬┤╬╣╬┐ŽŹ.Email Reputation



Email ReputationEmail Delivered
╠²
Your email reputation is essential to establish and maintain. You need to have an "A" rating with a score over 90 on scales like SenderScore. Authenticate your email IP address by publishing SPF, SenderID, DKIM, and possibly separate transactional and promotional emails. Pay attention to complaints and adjust campaigns accordingly. Stay off blacklists by regularly scanning IPs and domains. Only send emails to subscribers who have opted in for that specific type of email.Why Were We Created? - Dr. Bilal Philips



Why Were We Created? - Dr. Bilal PhilipsFirdaus Wong Wai Hung
╠²
Not just Muslims, but every single human being has to answer the most fundamental question at some point in his or her lifetime:
"Why was I created? Why am I here? What am I doing in this world? Why did God create me?"
These questions are questions which each and everyone of us reflects on at some point during their life. We have some answers, which are given generally but usually these answers don't satisfy us - seeming somewhat simplistic. So, we still wonder: "Why me? Why here?". I know all of you (Muslims), are saying, "To worship Allah, khallas (finish). What more is there to say? Why do we need to have a big long talk on why we were created when we all know it is to worship Allah?!"
But wait. If this is presented to a non-Muslim, the next logical question would be, "Why does Allah want us to worship Him?" Then your stuck, which can only mean that in our own minds it is not really clear. Why did Allah create us to worship Him?Public service and demographic change: an ILC-UK/Actuarial Profession joint d...



Public service and demographic change: an ILC-UK/Actuarial Profession joint d...ILC- UK
╠²
Full details of the event are available here: http://www.ilcuk.org.uk/index.php/events/ilc_uk_and_the_actuarial_profession_debate_public_service_and_demographic_c
The live blog for this event is available here: http://blog.ilcuk.org.uk/2013/04/23/live-blog-public-service-and-demographic-change/New week 4



New week 4nglaze10
╠²
The students traveled from Lewes, Delaware to Chincoteague Island on day 3, stopping in Ocean City, Maryland along the way. On day 4 they traveled from Chincoteague Island to Norfolk, Virginia. Malcolm and Sarah forgot to record the distance traveled each half hour but took notes. On day 5 the last stop was Williamsburg, Virginia, where Theo participated in a 90-minute bike race and had his speed recorded every 10 minutes by his electronic speedometer.Get Social Twitter and Facebook Basics 2012 



Get Social Twitter and Facebook Basics 2012 White Sheep Social Marketing
╠²
This document provides an overview of using Twitter and Facebook for business purposes. It includes tours of the Twitter and Facebook pages that describe the basic page components and functions. It also discusses tactics for using social media, such as scheduling tweets, using hashtags on Twitter, and encouraging customer check-ins on Facebook. The goal is to help businesses connect with and grow their audience on social networks.9.9



9.9nglaze10
╠²
The document provides examples of factoring polynomials completely. It begins by outlining guidelines for factoring polynomials completely, such as factoring out the greatest common monomial factor, looking for differences of squares or perfect square trinomials, and factoring trinomials and polynomials with four terms by grouping. It then works through examples of factoring various polynomials completely by applying these guidelines. These include factoring trinomials, solving a polynomial equation, and solving a multi-step problem involving factoring a polynomial to find dimensions.Mike wagoner slideshow



Mike wagoner slideshowdebhig
╠²
Walla Faces' first slideshow! Check out pictures from the Mike Wagoner Duo last weekend!LŌĆÖautismo degli adulti nello studio del medico di famiglia



LŌĆÖautismo degli adulti nello studio del medico di famigliaGiovanni Pagana
╠²
LŌĆÖautismo degli adulti nello studio del medico di famigliaMore Related Content
Viewers also liked (18)
Chapter 2.4



Chapter 2.4nglaze10
╠²
This textbook section discusses the properties of multiplication, including rules for multiplying integers and properties (axioms) of multiplication such as commutativity, associativity, and distributivity. It also covers identifying properties through more algebraic proof and provides examples to use for homework problems 29 through 37.Chapter2.1



Chapter2.1nglaze10
╠²
The document provides examples and explanations for converting between fractions and decimals. It discusses terminating decimals, which end, and repeating decimals, which have a repeating pattern after the decimal point. Examples are given for writing fractions as decimals and decimals as fractions in simplest form. The steps shown include dividing the numerator by the denominator to write a fraction as a decimal, and identifying the place value of the decimal's final digit to write the decimal as a fraction.Creative superbclub concept dossier



Creative superbclub concept dossiercracktivo
╠²
Creative Superbclub es educaci├│n + entertainment = edutainmentWhy your password sucks



Why your password sucksJerry Gamblin
╠²
The document discusses the importance of strong passwords and passphrases and provides tips to improve password security. It notes that short passwords can now be cracked within minutes using cloud computing services. It recommends using passphrases that are at least 15 characters long instead of passwords, and enabling two-factor authentication for additional security. The document aims to educate readers on how to better protect their online accounts by using more robust credentials that are difficult for hackers to guess or crack through brute force attacks.New week 6



New week 6nglaze10
╠²
This document provides instructions and materials for a math lesson on similarity and scale factors. It includes examples of similar figures with questions about their side lengths, scale factors, and areas. It also discusses how police use measurements and similar figures to determine characteristics like a criminal's height from surveillance photos. Students are asked to use a photo of a teacher holding an object of known size to calculate the teacher's height, and to explain how police may have used a similar technique to determine a robber's height from a store surveillance photo.Can Spam Act: What You Should Know



Can Spam Act: What You Should KnowEmail Delivered
╠²
The CAN SPAM Act establishes seven key requirements for businesses sending commercial emails: 1) Don't use false or misleading header information. 2) Don't use deceptive subject lines. 3) Identify messages as advertisements. 4) Include your physical address. 5) Tell recipients how to opt out of future emails. 6) Honor opt-out requests promptly. 7) Monitor how others use your brand in emails.Spam Traps 101



Spam Traps 101Email Delivered
╠²
Spam Traps can cause big problems in your email program. In this article, we discuss what exactly spam traps ARE, the different types of spam traps, and the impact of spam traps on your sender reputation. There are essentially 3 different types of spam traps that you must be aware of - and pay attention to - in your email marketing program. It's also important to understand how they play a role in the overall health of your email program. Learn how spam traps make their way into your list, where spam traps come from, and how to prevent spam traps from getting onto your email list in the first place. Action aid child labor



Action aid child laborElpida Paf
╠²
╬Ā╬▒Žü╬┐ŽģŽā╬»╬▒Žā╬Ę Žä╬ĘŽé ActionAid ╬│╬╣╬▒ Žä╬▒ ╬┤╬╣╬║╬▒╬╣ŽÄ╬╝╬▒Žä╬▒ Žä╬┐Žģ ŽĆ╬▒╬╣╬┤╬╣╬┐ŽŹ.Email Reputation



Email ReputationEmail Delivered
╠²
Your email reputation is essential to establish and maintain. You need to have an "A" rating with a score over 90 on scales like SenderScore. Authenticate your email IP address by publishing SPF, SenderID, DKIM, and possibly separate transactional and promotional emails. Pay attention to complaints and adjust campaigns accordingly. Stay off blacklists by regularly scanning IPs and domains. Only send emails to subscribers who have opted in for that specific type of email.Why Were We Created? - Dr. Bilal Philips



Why Were We Created? - Dr. Bilal PhilipsFirdaus Wong Wai Hung
╠²
Not just Muslims, but every single human being has to answer the most fundamental question at some point in his or her lifetime:
"Why was I created? Why am I here? What am I doing in this world? Why did God create me?"
These questions are questions which each and everyone of us reflects on at some point during their life. We have some answers, which are given generally but usually these answers don't satisfy us - seeming somewhat simplistic. So, we still wonder: "Why me? Why here?". I know all of you (Muslims), are saying, "To worship Allah, khallas (finish). What more is there to say? Why do we need to have a big long talk on why we were created when we all know it is to worship Allah?!"
But wait. If this is presented to a non-Muslim, the next logical question would be, "Why does Allah want us to worship Him?" Then your stuck, which can only mean that in our own minds it is not really clear. Why did Allah create us to worship Him?Public service and demographic change: an ILC-UK/Actuarial Profession joint d...



Public service and demographic change: an ILC-UK/Actuarial Profession joint d...ILC- UK
╠²
Full details of the event are available here: http://www.ilcuk.org.uk/index.php/events/ilc_uk_and_the_actuarial_profession_debate_public_service_and_demographic_c
The live blog for this event is available here: http://blog.ilcuk.org.uk/2013/04/23/live-blog-public-service-and-demographic-change/New week 4



New week 4nglaze10
╠²
The students traveled from Lewes, Delaware to Chincoteague Island on day 3, stopping in Ocean City, Maryland along the way. On day 4 they traveled from Chincoteague Island to Norfolk, Virginia. Malcolm and Sarah forgot to record the distance traveled each half hour but took notes. On day 5 the last stop was Williamsburg, Virginia, where Theo participated in a 90-minute bike race and had his speed recorded every 10 minutes by his electronic speedometer.Get Social Twitter and Facebook Basics 2012 



Get Social Twitter and Facebook Basics 2012 White Sheep Social Marketing
╠²
This document provides an overview of using Twitter and Facebook for business purposes. It includes tours of the Twitter and Facebook pages that describe the basic page components and functions. It also discusses tactics for using social media, such as scheduling tweets, using hashtags on Twitter, and encouraging customer check-ins on Facebook. The goal is to help businesses connect with and grow their audience on social networks.9.9



9.9nglaze10
╠²
The document provides examples of factoring polynomials completely. It begins by outlining guidelines for factoring polynomials completely, such as factoring out the greatest common monomial factor, looking for differences of squares or perfect square trinomials, and factoring trinomials and polynomials with four terms by grouping. It then works through examples of factoring various polynomials completely by applying these guidelines. These include factoring trinomials, solving a polynomial equation, and solving a multi-step problem involving factoring a polynomial to find dimensions.Mike wagoner slideshow



Mike wagoner slideshowdebhig
╠²
Walla Faces' first slideshow! Check out pictures from the Mike Wagoner Duo last weekend!More from Giovanni Pagana (11)
LŌĆÖautismo degli adulti nello studio del medico di famiglia



LŌĆÖautismo degli adulti nello studio del medico di famigliaGiovanni Pagana
╠²
LŌĆÖautismo degli adulti nello studio del medico di famigliaInfezioni delle vie urinarie nello studio del medico di famiglia



Infezioni delle vie urinarie nello studio del medico di famigliaGiovanni Pagana
╠²
Infezioni delle vie urinarie nello studio del medico di famigliaLa fibrillazione atriale e il medico di famiglia



La fibrillazione atriale e il medico di famigliaGiovanni Pagana
╠²
La fibrillazione atriale e medico di famigliaMmg e tromboembolismo nel malato oncologico



Mmg e tromboembolismo nel malato oncologicoGiovanni Pagana
╠²
Il medico di famiglia e il tromboembolismo nel malato oncologicoLinfoadenopatie e Medico di Famiglia



Linfoadenopatie e Medico di FamigliaGiovanni Pagana
╠²
Linfoadenopatie nello studio del Medico di Famiglia. Benigne nella maggior parte dei casi.Trattamento percutaneo delle valvulopatie.



Trattamento percutaneo delle valvulopatie.Giovanni Pagana
╠²
Trattamento percutaneo delle valvulopatie aortica e mitrale: il punto di vista del Medico di Famiglia. Dott. Giovanni Pagana - CataniaMedico di famiglia e stroke
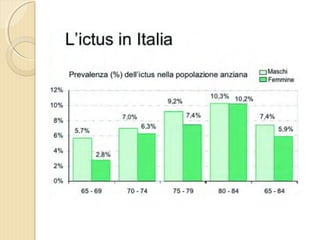
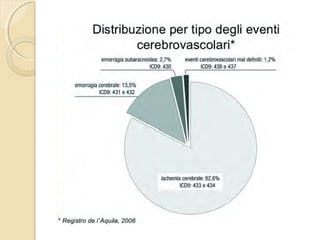
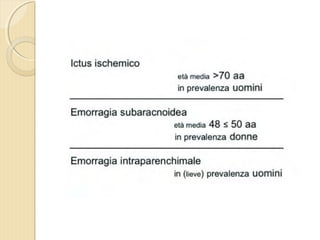
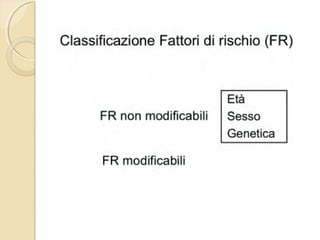
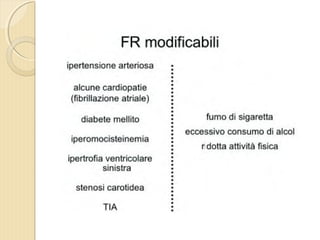
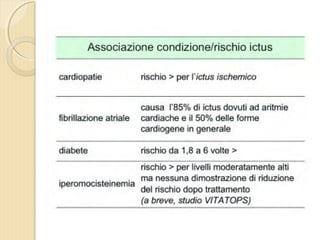
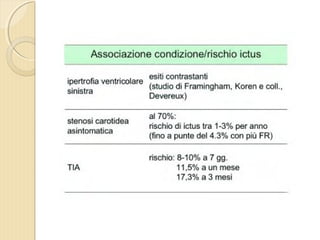
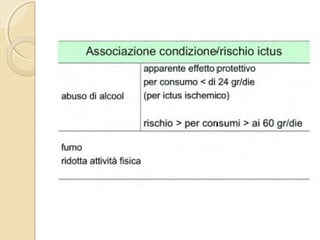
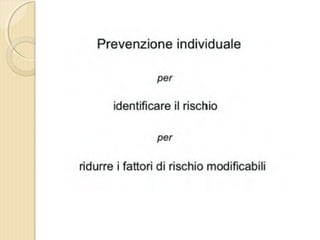
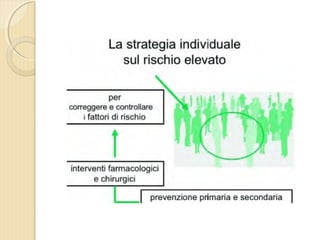
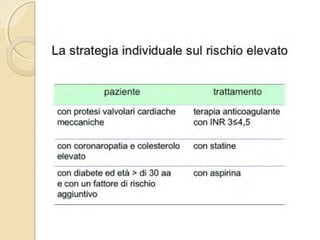
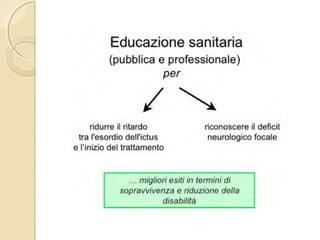
- 1. DOTT. GIOVANNI PAGANA MEDICO DI FAMIGLIA - CATANIA IL MEDICO DI FAMIGLIA E LŌĆÖ ICTUS
- 2. DOTT. GIOVANNI PAGANA MEDICO DI FAMIGLIA
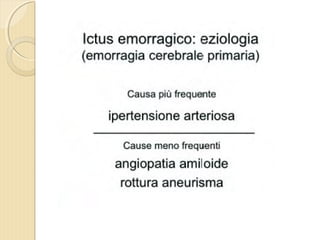
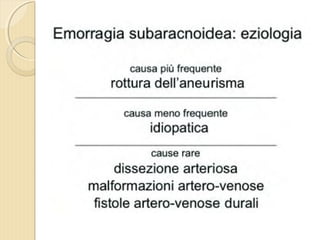
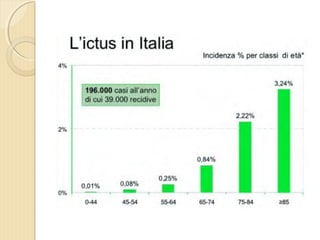
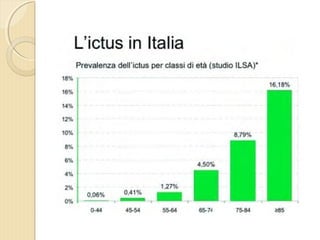
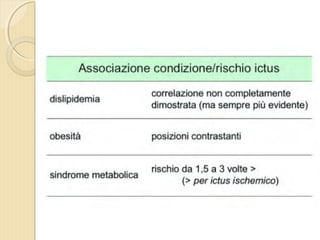
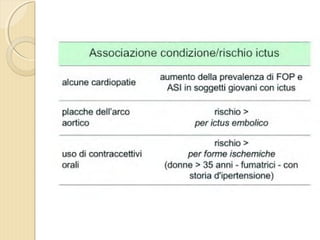
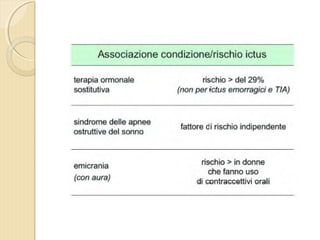
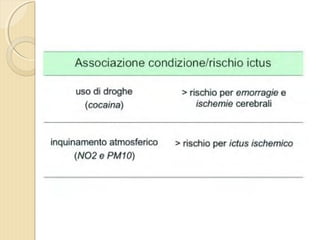
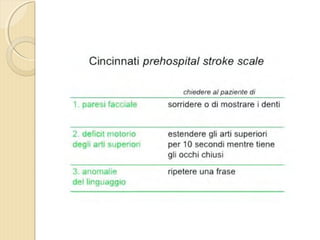
- 4. ’éŚ Wikipedia in lingua ’éŚ inglese, alla voce Stroke, ’éŚ ┬½Sezione di cervello di un ’éŚ soggetto colpito da ictus ’éŚ acuto dellŌĆÖarteria ’éŚ cerebrale media┬╗
- 47. ’éŚGRAZIE PER A CORTESE ATTENZIONE









