Network secuirty & encryption techniques
Download as PPSX, PDF1 like672 views
This Project has been developed to demonstrate Network Security and Encryption Techniques and It¡¯s Various Methods. Now a days IT security is most required thing in even of daily routine life like sending emails or even text messages. because we are not aware of security risks and keep our valuable data like our personal details, Our Bank Account Details or even Our Net Banking Passwords & ATM Pins on public mail/mail server. That is not enough secure. That¡¯s why we require some security algorithms that can secure our data. In this project we have studied most of them and implemented the basic things in our project.
1 of 11
Downloaded 10 times











Recommended
Profile-Arvind



Profile-ArvindArvind Raaz
?
Arvind K. Singh is an information security expert with over 15 years of experience in areas such as website monitoring, data privacy, network maintenance, security training, and more. He has delivered many live training sessions and workshops on topics such as information security, ethical hacking, and network security. Currently, he works as an Information Security Advisor for various corporations and is also the Chief Executive Officer of Nirmal World Pvt Ltd in Varanasi, India. He has a PhD in Information Assurance and Security from Colorado Technical University and holds other technical degrees.Cryptography in Blockchain



Cryptography in BlockchainEC-Council
?
This document discusses cryptography in blockchain. It begins by introducing blockchain and cryptography separately. It then defines important cryptography terminology like encryption, decryption, cipher, and key. It describes the main types of cryptography as symmetric-key, asymmetric-key, and hash functions. It explains how blockchain uses asymmetric-key algorithms and hash functions. Hash functions are used to link blocks and maintain integrity. Cryptography provides benefits like the avalanche effect and uniqueness to blockchain. Finally, it discusses an application of cryptography in cryptocurrency, where public-private key pairs maintain user addresses and digital signatures approve transactions.Terence_McLeod_ResumeupdateITandnetworksupport



Terence_McLeod_ResumeupdateITandnetworksupportTerence Mcleod
?
Terrence McLeod has over 10 years of experience in IT support, network administration, and information security. He has a degree in Network Administration and Computer Technology as well as experience managing networks, security systems, and information assets for companies in various industries. His skills include network and system security, risk management, vulnerability assessments, authentication, access control, system monitoring, and regulatory compliance. He is currently seeking a full-time role utilizing his technical and customer service experience.Gets cisco security training



Gets cisco security trainingqosnetworking
?
The Cisco network with threat selection analysis (SCYBER) course teaches cyber security concepts and how to recognize network threats and attacks. Students will learn how a network security operation center works and how to respond to security incidents. The course is part of Cisco security training to prepare network security engineers to protect data on public networks. Students will gain experience configuring and troubleshooting remote access and site-to-site VPN solutions using Cisco IOS routers. The training describes VPN technologies and deployment as well as security protocols. More information is available at www.qosnetworking.com.Information and network security ins



Information and network security insAstha Parihar
?
This document outlines information and network security. It discusses security goals of confidentiality, integrity and availability. It defines information and information security. Information security aims to prevent unauthorized access, use, disclosure or modification of information. The document also discusses encryption and the symmetric cipher model. Encryption scrambles data using an encryption key so that only authorized parties can access the information. The symmetric cipher model involves plain text being encrypted into cipher text using a secret key, which is then decrypted back into the original plain text.Cryptography and attacks ins



Cryptography and attacks insAstha Parihar
?
The document defines different types of attacks on cryptography systems including passive and active attacks. Passive attacks attempt to learn information without affecting system resources, while active attacks try to alter system operations. The document also discusses cryptography, defining it as the practice of hiding information and converting plain text into unintelligible cipher text. Symmetric key cryptography uses a shared key for encryption and decryption, while asymmetric key cryptography uses public and private key pairs.JowilGallenito (UPDATED)



JowilGallenito (UPDATED)jowil gallenito
?
This document contains a resume for Jowil S. Gallenito. It lists his contact information, personal statement, employment history including roles as a Junior IT Specialist and IT Support, education including a Bachelor's degree in Computer Science, internship experience, skills and training. His experience includes roles in technical support, networking, systems administration and software configuration.Cybersecurity - Mobile Application Security



Cybersecurity - Mobile Application SecurityEryk Budi Pratama
?
The document discusses several common mobile application security risks including lack of binary protection, weak server-side controls, insecure data storage, insufficient transport layer protection, unintended data leakage, poor authorization and authentication, broken cryptography, client-side injection, and improper session handling. It provides recommendations to address each of these risks such as using obfuscation, secure data storage techniques, TLS, strong authentication, secure cryptography, input validation, and secure session management.Encryption Techniques



Encryption TechniquesDel Elson
?
As data security becomes of paramount importance, we are going to need to have a reasonable understanding of encryption and encryption techniques. We will discuss the different types of encryption techniques and understand the difference between hashing (one way encryption) and encryption (designed to be two way). We will look at what is industry best practice for encryption today, and why. We will also look at some issues relating to performance of encryption.Cryptography



CryptographySidharth Mohapatra
?
Cryptography is the science of using mathematics to encrypt and decrypt data.
Cryptography enables you to store sensitive information or transmit it across insecure networks so that it cannot be read by anyone except the intended recipient.
Network Security and Cryptography



Network Security and CryptographyAdam Reagan
?
A brief discussion of network security and an introduction to cryptography. We end the presentation with a discussion of the RSA algorithm, and show how it works with a basic example.Encryption and Key Distribution Methods



Encryption and Key Distribution MethodsGulcin Yildirim Jelinek
?
This presentation is created for Applied Data Communication lecture of Computer Systems Engineering master programme at Tallinn University of TechnologyEncryption basics



Encryption basicsKevin OBrien
?
Encryption is key to safety online, but also important offline. But how does it work? This presentation will cover the basics and help you to be safer.EvasionTechniques



EvasionTechniquesCandan BOLUKBAS
?
This document discusses various techniques for evading antivirus, firewalls, and intrusion prevention systems (IPS). It begins with techniques for antivirus evasion using tools like msfvenom, veil-evasion, shellter, and unicorn to obfuscate payloads. Next it discusses firewall and IPS evasion techniques like stage encoding/encryption, zombie scanning, tunneling over protocols like ICMP, DNS, and using a custom Tor configuration. The document provides examples and links to demonstrate these evasion techniques.Network security & cryptography



Network security & cryptographyRahulprasad Yadav
?
This document summarizes a presentation on network security and cryptography. The presentation covers the objectives of security, password auditing, data security, and authentication. It also discusses encryption, decryption, public and private key cryptography, digital signatures, and the RSA algorithm. The presentation includes a demonstration of a public key system and concludes by emphasizing the importance of securing data through cryptography and network security techniques.Classical Encryption Techniques



Classical Encryption Techniquesuniversity of education,Lahore
?
The document discusses classical encryption techniques, including symmetric encryption which uses the same key for encryption and decryption. It describes ciphers like the Caesar cipher which substitutes letters by shifting the alphabet, the monoalphabetic cipher with one substitution table, and the polyalphabetic Vigen¨¨re cipher which uses multiple substitution alphabets. The document also covers the Playfair cipher which encrypts letters in pairs using a 5x5 keyword matrix, and discusses cryptanalysis techniques for breaking classical ciphers.Cryptography



Cryptographygueste4c97e
?
Cryptography involves secret writing and encrypting messages so that only authorized parties can read them. It uses algorithms and keys to encrypt plaintext into ciphertext. Cryptanalysis involves breaking ciphers, while cryptography is designing ciphers. Cryptology encompasses both cryptography and cryptanalysis. Common encryption models involve plaintext being encrypted into ciphertext using a key, which is then transmitted and decrypted by the intended receiver using the same key.Classical Encryption Techniques in Network Security



Classical Encryption Techniques in Network Securitybabak danyal
?
The document provides an overview of classical encryption techniques, including: symmetric ciphers that use the same key for encryption and decryption (such as the Caesar cipher, monoalphabetic ciphers like the Playfair cipher, and polyalphabetic ciphers like the Vigen¨¨re cipher) as well as transposition techniques that rearrange plaintext; rotor machines like the Enigma that implemented complex polyalphabetic substitution; and steganography that hides messages within other files or messages. The goal is to introduce basic concepts and terminology of encryption to prepare for studying modern cryptography.Cryptography



CryptographyShivanand Arur
?
This PPT explains about the term "Cryptography - Encryption & Decryption". This PPT is for beginners and for intermediate developers who want to learn about Cryptography. I have also explained about the various classes which .Net provides for encryption and decryption and some other terms like "AES" and "DES".Cryptography.ppt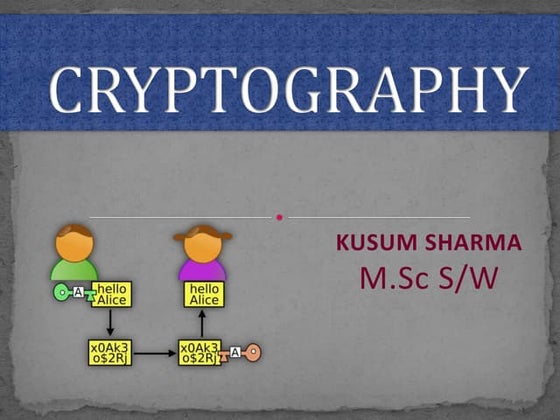



Cryptography.pptkusum sharma
?
This document provides an overview of cryptography. It defines cryptography as the science of securing messages from attacks. It discusses basic cryptography terms like plain text, cipher text, encryption, decryption, and keys. It describes symmetric key cryptography, where the same key is used for encryption and decryption, and asymmetric key cryptography, which uses different public and private keys. It also covers traditional cipher techniques like substitution and transposition ciphers. The document concludes by listing some applications of cryptography like e-commerce, secure data, and access control.Antivirus Evasion Techniques and Countermeasures



Antivirus Evasion Techniques and Countermeasuressecurityxploded
?
This presentation throws light on innovative techniques for bypassing antivirus detection. This will be useful for researchers and pen testers to develop successful post exploitation techniques. Cryptography and network security



Cryptography and network securitypatisa
?
This document provides an overview of cryptography including:
1. Cryptography is the process of encoding messages to protect information and ensure confidentiality, integrity, authentication and other security goals.
2. There are symmetric and asymmetric encryption algorithms that use the same or different keys for encryption and decryption. Examples include AES, RSA, and DES.
3. Other techniques discussed include digital signatures, visual cryptography, and ways to implement cryptography like error diffusion and halftone visual cryptography.Literature Survey: Secure transmitting of data using RSA public key implement...



Literature Survey: Secure transmitting of data using RSA public key implement...Editor IJCATR
?
This document discusses techniques for secure and fast transmission of data in mobile ad hoc networks (MANETs). It proposes using identity-based cryptography with visual cryptography. For identity-based cryptography, the RSA cryptosystem is used to generate public and private keys, with Vedic mathematics adopted for fast calculations. Vedic mathematics allows for faster prime number calculations compared to modern mathematics. Visual cryptography allows images to be encrypted and decrypted by the human visual system without computation. The techniques aim to securely and efficiently transmit encrypted images and data in MANETs.International Refereed Journal of Engineering and Science (IRJES)



International Refereed Journal of Engineering and Science (IRJES)irjes
?
International Refereed Journal of Engineering and Science (IRJES) is a leading international journal for publication of new ideas, the state of the art research results and fundamental advances in all aspects of Engineering and Science. IRJES is a open access, peer reviewed international journal with a primary objective to provide the academic community and industry for the submission of half of original research and applicationsJ017667582



J017667582IOSR Journals
?
This document proposes a method for preventing cheating of messages based on block cipher using a digital envelope. It begins with an introduction to the need for data security during storage and transmission. It then discusses the AES encryption algorithm and related work involving encryption for wireless devices. The proposed method uses AES key expansion techniques to generate multiple keys for encryption and decryption of messages using a digital envelope, packing the encrypted message and key into a single packet. It claims this prevents attackers from accessing sensitive data. Future work could expand this to image encryption and decryption applications.Prevention of Cheating Message based on Block Cipher using Digital Envelope



Prevention of Cheating Message based on Block Cipher using Digital Envelopeiosrjce
?
IOSR Journal of Computer Engineering (IOSR-JCE) is a double blind peer reviewed International Journal that provides rapid publication (within a month) of articles in all areas of computer engineering and its applications. The journal welcomes publications of high quality papers on theoretical developments and practical applications in computer technology. Original research papers, state-of-the-art reviews, and high quality technical notes are invited for publications.E-commerce & Security



E-commerce & SecurityNetstarterSL
?
This document summarizes security issues and threats facing e-businesses. It discusses how computerization and networking have increased security risks by exposing private networks to public threats. Technical attacks like hacking, malware, and denial of service as well as non-technical social engineering pose major risks. The document recommends tools like passwords, firewalls, and encryption to protect data and transactions. Regular security audits and testing are also advised to evaluate vulnerabilities and safeguard e-commerce over the long run as threats continue evolving.Color Image Encryption for Secure Transfer over Internet: A survey



Color Image Encryption for Secure Transfer over Internet: A surveyIRJET Journal
?
This document summarizes several studies on color image encryption techniques for secure transmission over the internet. It discusses the need for encrypting images due to privacy concerns when transmitting data over insecure networks. Several encryption methods are summarized, including approaches using hyper chaos, pixel bit scrambling, sharing matrices combined with encryption, logistic mapping with phase encoding, multiple image encryption using compressive imaging, and a fast encryption scheme using environmental noise. The techniques aimed to improve security, efficiency, speed and resistance to attacks. While most achieved their goals, future work is needed to address transmission speed, protection against all attack types, and reducing computational costs for some algorithms.Image and text Encryption using RSA algorithm in java 



Image and text Encryption using RSA algorithm in java PiyushPatil73
?
This document provides an overview and implementation details of an image and text encryption/decryption project using RSA encryption. It includes chapters on introduction/background, hardware/software specifications, feasibility study, preliminary design including ER diagram and data flow diagram, screen layouts, testing approach including white and black box testing, and implementation details of the modules. The implementation utilizes Java and generates RSA public/private key pairs to encrypt and decrypt text and images.Secrity project keyvan



Secrity project keyvanitrraincity
?
1. Cryptography is used to provide security in electronic commerce by ensuring privacy, authenticity, and preventing forgery, alteration, eavesdropping and tracing of messages.
2. There are two main types of cryptography - symmetric which uses the same key for encryption and decryption, and asymmetric (public key) which uses different keys for encryption and decryption.
3. Common symmetric algorithms are DES and AES while RSA is an example of an asymmetric algorithm commonly used for digital signatures and encryption.More Related Content
Viewers also liked (14)
Encryption Techniques



Encryption TechniquesDel Elson
?
As data security becomes of paramount importance, we are going to need to have a reasonable understanding of encryption and encryption techniques. We will discuss the different types of encryption techniques and understand the difference between hashing (one way encryption) and encryption (designed to be two way). We will look at what is industry best practice for encryption today, and why. We will also look at some issues relating to performance of encryption.Cryptography



CryptographySidharth Mohapatra
?
Cryptography is the science of using mathematics to encrypt and decrypt data.
Cryptography enables you to store sensitive information or transmit it across insecure networks so that it cannot be read by anyone except the intended recipient.
Network Security and Cryptography



Network Security and CryptographyAdam Reagan
?
A brief discussion of network security and an introduction to cryptography. We end the presentation with a discussion of the RSA algorithm, and show how it works with a basic example.Encryption and Key Distribution Methods



Encryption and Key Distribution MethodsGulcin Yildirim Jelinek
?
This presentation is created for Applied Data Communication lecture of Computer Systems Engineering master programme at Tallinn University of TechnologyEncryption basics



Encryption basicsKevin OBrien
?
Encryption is key to safety online, but also important offline. But how does it work? This presentation will cover the basics and help you to be safer.EvasionTechniques



EvasionTechniquesCandan BOLUKBAS
?
This document discusses various techniques for evading antivirus, firewalls, and intrusion prevention systems (IPS). It begins with techniques for antivirus evasion using tools like msfvenom, veil-evasion, shellter, and unicorn to obfuscate payloads. Next it discusses firewall and IPS evasion techniques like stage encoding/encryption, zombie scanning, tunneling over protocols like ICMP, DNS, and using a custom Tor configuration. The document provides examples and links to demonstrate these evasion techniques.Network security & cryptography



Network security & cryptographyRahulprasad Yadav
?
This document summarizes a presentation on network security and cryptography. The presentation covers the objectives of security, password auditing, data security, and authentication. It also discusses encryption, decryption, public and private key cryptography, digital signatures, and the RSA algorithm. The presentation includes a demonstration of a public key system and concludes by emphasizing the importance of securing data through cryptography and network security techniques.Classical Encryption Techniques



Classical Encryption Techniquesuniversity of education,Lahore
?
The document discusses classical encryption techniques, including symmetric encryption which uses the same key for encryption and decryption. It describes ciphers like the Caesar cipher which substitutes letters by shifting the alphabet, the monoalphabetic cipher with one substitution table, and the polyalphabetic Vigen¨¨re cipher which uses multiple substitution alphabets. The document also covers the Playfair cipher which encrypts letters in pairs using a 5x5 keyword matrix, and discusses cryptanalysis techniques for breaking classical ciphers.Cryptography



Cryptographygueste4c97e
?
Cryptography involves secret writing and encrypting messages so that only authorized parties can read them. It uses algorithms and keys to encrypt plaintext into ciphertext. Cryptanalysis involves breaking ciphers, while cryptography is designing ciphers. Cryptology encompasses both cryptography and cryptanalysis. Common encryption models involve plaintext being encrypted into ciphertext using a key, which is then transmitted and decrypted by the intended receiver using the same key.Classical Encryption Techniques in Network Security



Classical Encryption Techniques in Network Securitybabak danyal
?
The document provides an overview of classical encryption techniques, including: symmetric ciphers that use the same key for encryption and decryption (such as the Caesar cipher, monoalphabetic ciphers like the Playfair cipher, and polyalphabetic ciphers like the Vigen¨¨re cipher) as well as transposition techniques that rearrange plaintext; rotor machines like the Enigma that implemented complex polyalphabetic substitution; and steganography that hides messages within other files or messages. The goal is to introduce basic concepts and terminology of encryption to prepare for studying modern cryptography.Cryptography



CryptographyShivanand Arur
?
This PPT explains about the term "Cryptography - Encryption & Decryption". This PPT is for beginners and for intermediate developers who want to learn about Cryptography. I have also explained about the various classes which .Net provides for encryption and decryption and some other terms like "AES" and "DES".Cryptography.ppt



Cryptography.pptkusum sharma
?
This document provides an overview of cryptography. It defines cryptography as the science of securing messages from attacks. It discusses basic cryptography terms like plain text, cipher text, encryption, decryption, and keys. It describes symmetric key cryptography, where the same key is used for encryption and decryption, and asymmetric key cryptography, which uses different public and private keys. It also covers traditional cipher techniques like substitution and transposition ciphers. The document concludes by listing some applications of cryptography like e-commerce, secure data, and access control.Antivirus Evasion Techniques and Countermeasures



Antivirus Evasion Techniques and Countermeasuressecurityxploded
?
This presentation throws light on innovative techniques for bypassing antivirus detection. This will be useful for researchers and pen testers to develop successful post exploitation techniques. Cryptography and network security



Cryptography and network securitypatisa
?
This document provides an overview of cryptography including:
1. Cryptography is the process of encoding messages to protect information and ensure confidentiality, integrity, authentication and other security goals.
2. There are symmetric and asymmetric encryption algorithms that use the same or different keys for encryption and decryption. Examples include AES, RSA, and DES.
3. Other techniques discussed include digital signatures, visual cryptography, and ways to implement cryptography like error diffusion and halftone visual cryptography.Similar to Network secuirty & encryption techniques (20)
Literature Survey: Secure transmitting of data using RSA public key implement...



Literature Survey: Secure transmitting of data using RSA public key implement...Editor IJCATR
?
This document discusses techniques for secure and fast transmission of data in mobile ad hoc networks (MANETs). It proposes using identity-based cryptography with visual cryptography. For identity-based cryptography, the RSA cryptosystem is used to generate public and private keys, with Vedic mathematics adopted for fast calculations. Vedic mathematics allows for faster prime number calculations compared to modern mathematics. Visual cryptography allows images to be encrypted and decrypted by the human visual system without computation. The techniques aim to securely and efficiently transmit encrypted images and data in MANETs.International Refereed Journal of Engineering and Science (IRJES)



International Refereed Journal of Engineering and Science (IRJES)irjes
?
International Refereed Journal of Engineering and Science (IRJES) is a leading international journal for publication of new ideas, the state of the art research results and fundamental advances in all aspects of Engineering and Science. IRJES is a open access, peer reviewed international journal with a primary objective to provide the academic community and industry for the submission of half of original research and applicationsJ017667582



J017667582IOSR Journals
?
This document proposes a method for preventing cheating of messages based on block cipher using a digital envelope. It begins with an introduction to the need for data security during storage and transmission. It then discusses the AES encryption algorithm and related work involving encryption for wireless devices. The proposed method uses AES key expansion techniques to generate multiple keys for encryption and decryption of messages using a digital envelope, packing the encrypted message and key into a single packet. It claims this prevents attackers from accessing sensitive data. Future work could expand this to image encryption and decryption applications.Prevention of Cheating Message based on Block Cipher using Digital Envelope



Prevention of Cheating Message based on Block Cipher using Digital Envelopeiosrjce
?
IOSR Journal of Computer Engineering (IOSR-JCE) is a double blind peer reviewed International Journal that provides rapid publication (within a month) of articles in all areas of computer engineering and its applications. The journal welcomes publications of high quality papers on theoretical developments and practical applications in computer technology. Original research papers, state-of-the-art reviews, and high quality technical notes are invited for publications.E-commerce & Security



E-commerce & SecurityNetstarterSL
?
This document summarizes security issues and threats facing e-businesses. It discusses how computerization and networking have increased security risks by exposing private networks to public threats. Technical attacks like hacking, malware, and denial of service as well as non-technical social engineering pose major risks. The document recommends tools like passwords, firewalls, and encryption to protect data and transactions. Regular security audits and testing are also advised to evaluate vulnerabilities and safeguard e-commerce over the long run as threats continue evolving.Color Image Encryption for Secure Transfer over Internet: A survey



Color Image Encryption for Secure Transfer over Internet: A surveyIRJET Journal
?
This document summarizes several studies on color image encryption techniques for secure transmission over the internet. It discusses the need for encrypting images due to privacy concerns when transmitting data over insecure networks. Several encryption methods are summarized, including approaches using hyper chaos, pixel bit scrambling, sharing matrices combined with encryption, logistic mapping with phase encoding, multiple image encryption using compressive imaging, and a fast encryption scheme using environmental noise. The techniques aimed to improve security, efficiency, speed and resistance to attacks. While most achieved their goals, future work is needed to address transmission speed, protection against all attack types, and reducing computational costs for some algorithms.Image and text Encryption using RSA algorithm in java 



Image and text Encryption using RSA algorithm in java PiyushPatil73
?
This document provides an overview and implementation details of an image and text encryption/decryption project using RSA encryption. It includes chapters on introduction/background, hardware/software specifications, feasibility study, preliminary design including ER diagram and data flow diagram, screen layouts, testing approach including white and black box testing, and implementation details of the modules. The implementation utilizes Java and generates RSA public/private key pairs to encrypt and decrypt text and images.Secrity project keyvan



Secrity project keyvanitrraincity
?
1. Cryptography is used to provide security in electronic commerce by ensuring privacy, authenticity, and preventing forgery, alteration, eavesdropping and tracing of messages.
2. There are two main types of cryptography - symmetric which uses the same key for encryption and decryption, and asymmetric (public key) which uses different keys for encryption and decryption.
3. Common symmetric algorithms are DES and AES while RSA is an example of an asymmetric algorithm commonly used for digital signatures and encryption.Encryption Algorithms for Cloud



Encryption Algorithms for CloudMphasis
?
In this presentation, Amali introduces the topic of SMAC and moves on to the problem area of storage in cloud. Her interest area lies in developing algorithms that make cloud storage safer.Chapter 2 System Security.pptx



Chapter 2 System Security.pptxRushikeshChikane2
?
It provides information about Desktop Security, Email Security,Web security,Web Authentication, SSL, SET, Database Security and etcInscibe and Squeeze



Inscibe and SqueezeAyush Kejriwal
?
The document provides an overview of an Android application for encrypting text and images. It describes the algorithms used for encryption and decryption. The encryption algorithm takes in text or an image file, a random key, and stores the encrypted output in a file. The decryption algorithm recovers the original text or image by decrypting the file with the key. The application implements these algorithms to allow users to securely encrypt and decrypt files on their Android devices. Testing procedures are also outlined to ensure proper functionality and security.Fundamental difference between cyber security and network security



Fundamental difference between cyber security and network securitySample Assignment
?
The "essential difference between cyber security and network security," as most students find it difficult to distinguish between the two, become confused, and are unable to finish assignments that match the mandated level, are the most prevalent and reflecting question asked by I.T students. Many students struggle to write structural assignments that meet the professor's requirements, so they seek assignment writing services to improve their scores and learn the difference between them.Ew25914917



Ew25914917IJERA Editor
?
IJERA (International journal of Engineering Research and Applications) is International online, ... peer reviewed journal. For more detail or submit your article, please visit www.ijera.comIRJET - A Novel Approach Implementing Deduplication using Message Locked Encr...



IRJET - A Novel Approach Implementing Deduplication using Message Locked Encr...IRJET Journal
?
This document proposes a novel approach to implementing data deduplication on the cloud using message locked encryption. It aims to overcome limitations of existing deduplication techniques like convergent encryption by using erasure code technology, encryption algorithms like DES and MD5 hashing, and tokenization to securely store and protect client data on the cloud. The proposed system gives clients proof of ownership of their data by allowing them to choose who can access their files and see any changes made over time. The system architecture involves a client uploading encrypted data to the cloud, and recipients selected by the client being able to access and retrieve encrypted pieces of the data.Execution Analysis of Different Cryptographic Encryption Algorithms on Differ...



Execution Analysis of Different Cryptographic Encryption Algorithms on Differ...IRJET Journal
?
This document analyzes and compares the performance of different cryptographic encryption algorithms (AES, DES, and Blowfish) on different file sizes when encrypting data on the cloud versus off the cloud. It first provides background on the increasing threat of cyberattacks and importance of encrypting data stored in the cloud. It then describes symmetric encryption algorithms and the specific algorithms to be analyzed. The document reviews previous related studies that have compared the performance of encryption algorithms. It also outlines different cloud storage delivery models. The proposed model is described which will analyze encryption time of the selected algorithms on different file sizes both on and off the cloud.Big data security_issues_research_paper



Big data security_issues_research_paperLuisa Francisco
?
This document discusses big data security issues and encryption techniques. It begins with introducing the authors and providing an abstract about addressing security issues related to data integrity, confidentiality and availability. The main body then covers authentication, data, network and generic security challenges with big data as well as proposed solutions like encryption, logging and honeypot nodes. The document focuses on describing symmetric and asymmetric encryption algorithms including DES, AES, RSA and ECC. It compares the algorithms and concludes that encryption techniques can help secure big data stored in clouds, though current security levels may be improved.Ben Hay CV External - 14.02.15



Ben Hay CV External - 14.02.15Ben Hay
?
Ben Hay has over 10 years of experience in IT roles including network administration, desktop support, and security solution architecture. He currently works as an Enterprise Technology Consultant for Hewlett Packard, where he has led projects implementing secure mobility solutions, Windows 7 deployments, and virtual desktop infrastructure. Ben has a Bachelor's degree in Computer Security and various technical certifications. He is proficient in networking, operating systems, security, and programming languages.IRJET- Cloud Computing with Encryption



IRJET- Cloud Computing with EncryptionIRJET Journal
?
This document discusses using encryption to securely store data in the cloud. It focuses on implementing the Advanced Encryption Standard (AES) algorithm to encrypt data before uploading it to a cloud server. AES is a strong encryption standard that has not been practically cracked. The project aims to create a website that allows users to register, upload encrypted files to the cloud, download and decrypt files using a password, and perform basic calculations on data files. Administrators can view users and files. By encrypting data with AES before storage, the project aims to address security and privacy concerns of cloud computing.Security Issues related with cloud computing



Security Issues related with cloud computingIJERA Editor
?
The term CLOUD means Common Location Independent Online Utility on Demand. It?s an emerging technology in IT industries. Cloud technologies are improving day by day and now it become a need for all small and large scale industries. Companies like Google, Amazon, Microsoft etc. is providing virtualized environment for user by which it omits the need for physical storage and others. But as the advantage of cloud computing is increasing day by day the issues are also threatening the IT industries. These issues related with the security of the data. The basic idea of this review paper is to elaborate the security issues related with cloud computing and what methods are implemented to improve these security. Certain algorithms like RSA, DES, and Ceaser Cipher etc. implemented to improve the security issues. In this paper we have implemented Identity based mRSA algorithm in this paper for improving security of data.Ncct Software Projects Intro & Presentation



Ncct Software Projects Intro & Presentationncct
?
Final Year Projects, Final Year Projects in Chennai, Software Projects, Embedded Projects, Microcontrollers Projects, DSP Projects, VLSI Projects, Matlab Projects, Java Projects, .NET Projects, IEEE Projects, IEEE 2009 Projects, IEEE 2009 Projects, Software, IEEE 2009 Projects, Embedded, Software IEEE 2009 Projects, Embedded IEEE 2009 Projects, Final Year Project Titles, Final Year Project Reports, Final Year Project Review, Robotics Projects, Mechanical Projects, Electrical Projects, Power Electronics Projects, Power System Projects, Model Projects, Java Projects, J2EE Projects, Engineering Projects, Student Projects, Engineering College Projects, MCA Projects, BE Projects, BTech Projects, ME Projects, MTech Projects, Wireless Networks Projects, Network Security Projects, Networking Projects, final year projects, ieee projects, student projects, college projects, ieee projects in chennai, java projects, software ieee projects, embedded ieee projects, "ieee2009projects", "final year projects", "ieee projects", "Engineering Projects", "Final Year Projects in Chennai", "Final year Projects at Chennai"Recently uploaded (20)
Endpoint Backup: 3 Reasons MSPs Ignore It



Endpoint Backup: 3 Reasons MSPs Ignore ItMSP360
?
Many MSPs overlook endpoint backup, missing out on additional profit and leaving a gap that puts client data at risk.
Join our webinar as we break down the top challenges of endpoint backup¡ªand how to overcome them.THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIA



THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIASrivaanchi Nathan
?
This business intelligence report, "The Big Ten Biopharmaceutical MNCs: Global Capability Centers in India", provides an in-depth analysis of the operations and contributions of the Global Capability Centers (GCCs) of ten leading biopharmaceutical multinational corporations in India. The report covers AstraZeneca, Bayer, Bristol Myers Squibb, GlaxoSmithKline (GSK), Novartis, Sanofi, Roche, Pfizer, Novo Nordisk, and Eli Lilly. In this report each company's GCC is profiled with details on location, workforce size, investment, and the strategic roles these centers play in global business operations, research and development, and information technology and digital innovation.30B Images and Counting: Scaling Canva's Content-Understanding Pipelines by K...



30B Images and Counting: Scaling Canva's Content-Understanding Pipelines by K...ScyllaDB
?
Scaling content understanding for billions of images is no easy feat. This talk dives into building extreme label classification models, balancing accuracy & speed, and optimizing ML pipelines for scale. You'll learn new ways to tackle real-time performance challenges in massive data environments.Understanding Traditional AI with Custom Vision & MuleSoft.pptx



Understanding Traditional AI with Custom Vision & MuleSoft.pptxshyamraj55
?
Understanding Traditional AI with Custom Vision & MuleSoft.pptx | ### ºÝºÝߣ Deck Description:
This presentation features Atul, a Senior Solution Architect at NTT DATA, sharing his journey into traditional AI using Azure's Custom Vision tool. He discusses how AI mimics human thinking and reasoning, differentiates between predictive and generative AI, and demonstrates a real-world use case. The session covers the step-by-step process of creating and training an AI model for image classification and object detection¡ªspecifically, an ad display that adapts based on the viewer's gender. Atulavan highlights the ease of implementation without deep software or programming expertise. The presentation concludes with a Q&A session addressing technical and privacy concerns.Field Device Management Market Report 2030 - TechSci Research



Field Device Management Market Report 2030 - TechSci ResearchVipin Mishra
?
The Global Field Device Management (FDM) Market is expected to experience significant growth in the forecast period from 2026 to 2030, driven by the integration of advanced technologies aimed at improving industrial operations.
? According to TechSci Research, the Global Field Device Management Market was valued at USD 1,506.34 million in 2023 and is anticipated to grow at a CAGR of 6.72% through 2030. FDM plays a vital role in the centralized oversight and optimization of industrial field devices, including sensors, actuators, and controllers.
Key tasks managed under FDM include:
Configuration
Monitoring
Diagnostics
Maintenance
Performance optimization
FDM solutions offer a comprehensive platform for real-time data collection, analysis, and decision-making, enabling:
Proactive maintenance
Predictive analytics
Remote monitoring
By streamlining operations and ensuring compliance, FDM enhances operational efficiency, reduces downtime, and improves asset reliability, ultimately leading to greater performance in industrial processes. FDM¡¯s emphasis on predictive maintenance is particularly important in ensuring the long-term sustainability and success of industrial operations.
For more information, explore the full report: https://shorturl.at/EJnzR
Major companies operating in Global?Field Device Management Market are:
General Electric Co
Siemens AG
ABB Ltd
Emerson Electric Co
Aveva Group Ltd
Schneider Electric SE
STMicroelectronics Inc
Techno Systems Inc
Semiconductor Components Industries LLC
International Business Machines Corporation (IBM)
#FieldDeviceManagement #IndustrialAutomation #PredictiveMaintenance #TechInnovation #IndustrialEfficiency #RemoteMonitoring #TechAdvancements #MarketGrowth #OperationalExcellence #SensorsAndActuatorsWorld Information Architecture Day 2025 - UX at a Crossroads



World Information Architecture Day 2025 - UX at a CrossroadsJoshua Randall
?
User Experience stands at a crossroads: will we live up to our potential to design a better world? or will we be co-opted by ¡°product management¡± or another business buzzword?
Looking backwards, this talk will show how UX has repeatedly failed to create a better world, drawing on industry data from Nielsen Norman Group, Baymard, MeasuringU, WebAIM, and others.
Looking forwards, this talk will argue that UX must resist hype, say no more often and collaborate less often (you read that right), and become a true profession ¡ª in order to be able to design a better world.DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (ƽɽÒã)



DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (ƽɽÒã)Tsuyoshi Hirayama
?
DAO UTokyo 2025
–|¾©´óѧÇéˆóѧh ¥Ö¥í¥Ã¥¯¥Á¥§©`¥óÑо¿¥¤¥Ë¥·¥¢¥Æ¥£¥Ö
https://utbciii.com/2024/12/12/announcing-dao-utokyo-2025-conference/
Session 1 :DLT mass adoption
IBM Tsuyoshi Hirayama (ƽɽÒã)DealBook of Ukraine: 2025 edition | AVentures Capital



DealBook of Ukraine: 2025 edition | AVentures CapitalYevgen Sysoyev
?
The DealBook is our annual overview of the Ukrainian tech investment industry. This edition comprehensively covers the full year 2024 and the first deals of 2025. Replacing RocksDB with ScyllaDB in Kafka Streams by Almog Gavra



Replacing RocksDB with ScyllaDB in Kafka Streams by Almog GavraScyllaDB
?
Learn how Responsive replaced embedded RocksDB with ScyllaDB in Kafka Streams, simplifying the architecture and unlocking massive availability and scale. The talk covers unbundling stream processors, key ScyllaDB features tested, and lessons learned from the transition.The Future of Repair: Transparent and Incremental by Botond De?nes



The Future of Repair: Transparent and Incremental by Botond De?nesScyllaDB
?
Regularly run repairs are essential to keep clusters healthy, yet having a good repair schedule is more challenging than it should be. Repairs often take a long time, preventing running them often. This has an impact on data consistency and also limits the usefulness of the new repair based tombstone garbage collection. We want to address these challenges by making repairs incremental and allowing for automatic repair scheduling, without relying on external tools.DevNexus - Building 10x Development Organizations.pdf



DevNexus - Building 10x Development Organizations.pdfJustin Reock
?
Developer Experience is Dead! Long Live Developer Experience!
In this keynote-style session, we¡¯ll take a detailed, granular look at the barriers to productivity developers face today and modern approaches for removing them. 10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, ¡®The Coding War Games.¡¯
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method, we invent to deliver products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches works? DORA? SPACE? DevEx? What should we invest in and create urgency behind today so we don¡¯t have the same discussion again in a decade?MIND Revenue Release Quarter 4 2024 - Finacial Presentation



MIND Revenue Release Quarter 4 2024 - Finacial PresentationMIND CTI
?
MIND Revenue Release Quarter 4 2024 - Finacial PresentationSMART SENTRY CYBER THREAT INTELLIGENCE IN IIOT



SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTTanmaiArni
?
SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOT[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
[Webinar] Scaling Made Simple: Getting Started with No-Code Web AppsSafe Software
?
Ready to simplify workflow sharing across your organization without diving into complex coding? With FME Flow Apps, you can build no-code web apps that make your data work harder for you ¡ª fast.
In this webinar, we¡¯ll show you how to:
Build and deploy Workspace Apps to create an intuitive user interface for self-serve data processing and validation.
Automate processes using Automation Apps. Learn to create a no-code web app to kick off workflows tailored to your needs, trigger multiple workspaces and external actions, and use conditional filtering within automations to control your workflows.
Create a centralized portal with Gallery Apps to share a collection of no-code web apps across your organization.
Through real-world examples and practical demos, you¡¯ll learn how to transform your workflows into intuitive, self-serve solutions that empower your team and save you time. We can¡¯t wait to show you what¡¯s possible!UiPath Automation Developer Associate Training Series 2025 - Session 1



UiPath Automation Developer Associate Training Series 2025 - Session 1DianaGray10
?
Welcome to UiPath Automation Developer Associate Training Series 2025 - Session 1.
In this session, we will cover the following topics:
Introduction to RPA & UiPath Studio
Overview of RPA and its applications
Introduction to UiPath Studio
Variables & Data Types
Control Flows
You are requested to finish the following self-paced training for this session:
Variables, Constants and Arguments in Studio 2 modules - 1h 30m - https://academy.uipath.com/courses/variables-constants-and-arguments-in-studio
Control Flow in Studio 2 modules - 2h 15m - https:/academy.uipath.com/courses/control-flow-in-studio
?? For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. Revolutionizing-Government-Communication-The-OSWAN-Success-Story



Revolutionizing-Government-Communication-The-OSWAN-Success-Storyssuser52ad5e
?
? ????? ??????? ????? ?
???????? ??????????? is proud to be a part of the ?????? ????? ???? ???? ??????? (?????) success story! By delivering seamless, secure, and high-speed connectivity, OSWAN has revolutionized e-?????????? ?? ??????, enabling efficient communication between government departments and enhancing citizen services.
Through our innovative solutions, ???????? ?????????? has contributed to making governance smarter, faster, and more transparent. This milestone reflects our commitment to driving digital transformation and empowering communities.
? ?????????? ??????, ?????????? ??????????!
Wondershare Dr.Fone Crack Free Download 2025



Wondershare Dr.Fone Crack Free Download 2025maharajput103
?
copy & paste ? ???? https://filedownloadx.com/download-link/
Wondershare Dr.Fone Crack is a comprehensive mobile phone management and recovery software designed to help users recover lost data, repair system issues, and manage mobile devices. It supports both Android and iOS platforms, offering a wide range of features aimed at restoring files, repairing software problems, and backing up or transferring data.FinTech - US Annual Funding Report - 2024.pptx



FinTech - US Annual Funding Report - 2024.pptxTracxn
?
US FinTech 2024, offering a comprehensive analysis of key trends, funding activities, and top-performing sectors that shaped the FinTech ecosystem in the US 2024. The report delivers detailed data and insights into the region's funding landscape and other developments. We believe this report will provide you with valuable insights to understand the evolving market dynamics.UiPath Agentic Automation Capabilities and Opportunities



UiPath Agentic Automation Capabilities and OpportunitiesDianaGray10
?
Learn what UiPath Agentic Automation capabilities are and how you can empower your agents with dynamic decision making. In this session we will cover these topics:
What do we mean by Agents
Components of Agents
Agentic Automation capabilities
What Agentic automation delivers and AI Tools
Identifying Agent opportunities
? If you have any questions or feedback, please refer to the "Women in Automation 2025" dedicated Forum thread. You can find there extra details and updates.What Makes "Deep Research"? A Dive into AI Agents



What Makes "Deep Research"? A Dive into AI AgentsZilliz
?
About this webinar:
Unless you live under a rock, you will have heard about OpenAI¡¯s release of Deep Research on Feb 2, 2025. This new product promises to revolutionize how we answer questions requiring the synthesis of large amounts of diverse information. But how does this technology work, and why is Deep Research a noticeable improvement over previous attempts? In this webinar, we will examine the concepts underpinning modern agents using our basic clone, Deep Searcher, as an example.
Topics covered:
Tool use
Structured output
Reflection
Reasoning models
Planning
Types of agentic memoryNetwork secuirty & encryption techniques
- 1. Network Security & Encryption Techniques Thesis and Project Work for IT Students Get Reports on Tips Creative Software Solution ?www.cssambala.com ? info@cssambala.com ? +91-9896566399
- 3. This Project has been developed to demonstrate Network Security and Encryption Techniques and It¡¯s Various Methods. Now a days IT security is most required thing in even of daily routine life like sending emails or even text messages. because we are not aware of security risks and keep our valuable data like our personal details, Our Bank Account Details or even Our Net Banking Passwords & ATM Pins on public mail/mail server. That is not enough secure. That¡¯s why we require some security algorithms that can secure our data. In this project we have studied most of them and implemented the basic things in our project.
- 4. ? Cryptography encryption ? Public-Key Cryptography- RSA, ECC ? Symmetric Cryptography -DES, Triple-DES, AES ? Digital Signatures-DSA ? Authentication and Key Exchange ? Data Encryption Standard (DES) ? Public-Key Cryptography Standards (PKCS) ? Undeniable Digital Signatures ? One-Way Hash Functions ? MD4, MD5, SHA, RIPE-MD, MAC
- 6. Creative Software Solution ?www.cssambala.com ? info@cssambala.com ? +91-9896566399
- 7. Creative Software Solution ?www.cssambala.com ? info@cssambala.com ? +91-9896566399 Encrypting a File
- 8. Creative Software Solution ?www.cssambala.com ? info@cssambala.com ? +91-9896566399
- 9. Creative Software Solution ?www.cssambala.com ? info@cssambala.com ? +91-9896566399
- 10. Creative Software Solution ?www.cssambala.com ? info@cssambala.com ? +91-9896566399
- 11. Thanks Visit us for more IT Projects and download complete source code and project report file. Creative Software Solution ?www.cssambala.com ?info@cssambala.com ?? +91-9896566399
