NetworkAlgorithms.ppt
- 2. Network Performance Measures ? Two Performance Measures – Quantity of Service (Throughput) ? How much data travels across the net? ? How long does it take to transfer long files? – Quality of Service (Average packet delay) ? How long does it take for a packet to arrive at its destination? ? How responsive is the system to user commands? ? Can the network support real-time delivery such as audio and video?
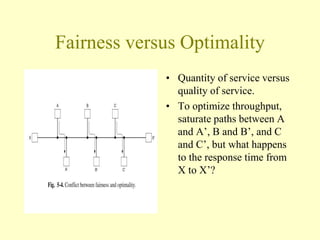
- 3. Fairness versus Optimality ? Quantity of service versus quality of service. ? To optimize throughput, saturate paths between A and A’, B and B’, and C and C’, but what happens to the response time from X to X’?
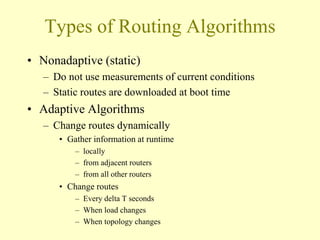
- 4. Types of Routing Algorithms ? Nonadaptive (static) – Do not use measurements of current conditions – Static routes are downloaded at boot time ? Adaptive Algorithms – Change routes dynamically ? Gather information at runtime – locally – from adjacent routers – from all other routers ? Change routes – Every delta T seconds – When load changes – When topology changes
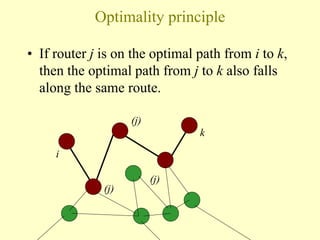
- 5. Optimality principle ? If router j is on the optimal path from i to k, then the optimal path from j to k also falls along the same route. i k (j) (j) (j)
- 6. Sink Trees ? The set of optimal routes to a particular node forms a sink tree. ? Sink trees are not necessarily unique ? Goal of all routing algorithms – Discover sink trees for all destinations
- 7. ? Given a network topology and a set of weights describing the cost to send data across each link in the network ? Find the shortest path from a specified source to all other destinations in the network. ? Shortest path algorithm first developed by E. W. Dijkstra Shortest Path Routing (a nonadaptive routing algorithm)
- 8. Shortest Path Routing (a nonadaptive routing algorithm) Mark the source node as permanent. Designate the source node as the working node. Set the tentative distance to all other nodes to infinity. While some nodes are not marked permanent Compute the tentative distance from the source to all nodes adjacent to the working node. If this is shorter than the current tentative distance replace the tentative distance of the destination and record the label of the working node there. Examine ALL tentatively labeled nodes in the graph. Select the node with the smallest value and make it the new working node. Designate the node permanent.
- 9. Example of Shortest Path Routing
- 10. Why the Shortest Path Algorithm Works ? Perhaps A*ZE is a better path to E than ABE ? nodes are made permanent when paths to them are the shortest paths in the graph ? All subsequent paths found to permanent nodes will be at least as long as previously found paths ? Two cases 1.) If Z is permanent, then we have already checked A*ZE 2.) If Z is tentatively labeled, paths to Z must be longer than paths to E, otherwise Z would have been made permanent A B E Z
- 11. ? Brute force routing – Every incoming packet is sent on every outgoing line – Always finds the shortest path quickly – Also finds many long paths – Time to live is set to size of subnet ? Selective Flooding – Flood only in the direction of the destination ? Practical in a few settings – Military Applications – Distributed Databases – Metric for comparison Flooding (a nonadaptive routing algorithm)
- 12. ? Bellman-Ford Routing ? Ford Fulkerson Algorithm ? Original ARPANET routing algorithm ? Previously used on Internet (RIP) ? Early version of DecNet and Novell’s IPX ? AppleTalk and Cisco routers use improved versions of this algorithm Distance Vector Routing (an adaptive routing algorithm)
- 13. ? Neighboring routers periodically exchange information from their routing tables. ? Routers replace routes in their own routing tables anytime that neighbors have found better routes. ? Information provided from neighbors – Outgoing line used for destination – Estimate of time or distance ? can be number of hops, time delay, packet queue length, etc. Distance Vector Routing (an adaptive routing algorithm)
- 14. Distance Vector Routing (an adaptive routing algorithm)
- 15. The Count to Infinity Problem
- 16. The Split Horizon Hack ? Actual distance to a destination is not reported on the line on which packets to that destination are sent. ? Instead these distances are reported as “infinity.” B D A C C tells D the truth about its distance to A, but lies to B and says the distance is infinity.
- 17. A topology where split horizon fails Suppose that D becomes unreachable from C. A and B are reporting infinite distances to C, but they are reporting distances of length 2 to each other. A and B will count to infinity.
- 18. ? Five Steps 1.) Discover your neighbors and learn their addresses. 2.) Measure the cost (delay) to each neighbor. 3.) Construct a packet containing all this information 4.) Send this packet to all other routers. 5.) Compute the shortest path to every other router. Link State Routing (an adaptive routing algorithm)
- 19. 1.) Discovering Your Neighbors ? Send “Hello” packet on each point-to-point line. Destination node replies with its address.
- 20. 2.) Measuring Line Cost ? Send an “ECHO” packet over the line. ? Destination is required to respond to “ECHO” packet immediately. ? Measure the time required for this operation. ? Question: Should we measure just the time it takes to transmit the packet, or should we include the time that the packet waits in the queue?
- 21. Argument 2: ? We should include the time that the packet spends in the queue, as this provides a more accurate picture of the real delays. ? We should only include the transmission times, otherwise the network is likely to oscillate between preferred paths.
- 22. Oscillating Paths F H L E A B C D G I J K Consider the situation where all nodes are sending to destination A. Each node must determine to either route clockwise or counter clockwise. The cost of routing clockwise is the number of other nodes routing clockwise.
- 23. Build Link State Packets
- 24. Distributing the Link State Packets ? Use selective flooding ? Sequence numbers prevent duplicate packets from being propagated ? Lower sequence numbers are rejected as obsolete
- 25. Computing the New Routes ? Dijkstra’s Shortest Path algorithm is used to determine the shortest path to each destination.
- 26. Hierarchical Routing ? Addresses the growth of routing tables ? Routers are divided into regions ? Routers know the routes for their own regions only ? Works like telephone routing ? Possible hierarchy – city, state, country, continent ? Optimal number of levels for an N router subnet is lnN
- 27. Routing Mobile Hosts ? Networking portable computers ? Tanenbaum’s proposed solution – All mobile agents are assumed to have a permanent home location – When a portable computer is attached to a remote network it contacts a process that acts as the local foreign agent. – Each home location has a process that acts as the home agent
- 28. The Agents on the Network
- 29. Registering a Mobile Agent ? Periodically the foreign agent broadcasts its address ? The mobile agent registers with the foreign agent and supplies its home address ? The foreign agent contacts the mobile agent’s home agent reporting the mobile agent’s location. – Security must be used to verify the identity of the mobile agent. ? The foreign agent registers the mobile agent
- 30. Routing Packets to a Mobile Agent ? Packets sent to the mobile agent are routed to the users home network ? The home agent routes the packets to the foreign agent ? The home agent provides the source of incoming packets with the remote address of the mobile agent
- 31. Broadcast Routing ? Send a separate packet to each destination ? Use flooding ? Use multidestination routing – Each packet contains a list of destinations – Routers duplicate packet for all matching outgoing lines ? Use spanning tree routing – a subset of the subnet that includes all routers but contains no loops.
- 32. Spanning Tree Broadcasting ? Uses the minimum number of packets necessary ? Routers must be able to compute spanning tree – Available with link state routing – Not available with distance vector routing
- 33. Broadcast Routing (continued) ? Reverse Path Forwarding – Use When knowledge of a spanning tree is not available – Provides an approximation of spanning tree routing – Routers check to see if incoming packet arrives from the same line that the router uses to route outgoing packets to the broadcast source ? If so, the router duplicates the packet on all other outgoing lines ? Otherwise, the router discards the packet
- 34. Reverse Path Forwarding Example This router routes packets bound for 128.173.41.41 to via line A. A B C D E Any broadcast from 128.173.41.41 that arrives from line A is broadcast on lines B, C, D, and E Any broadcast from 128.173.41.41 that arrives from line B, C, D, or E is discarded
- 35. Multicast Routing ? A method to broadcast packets to well- defined groups ? Hosts can join multicast groups. – They inform their routers – Routers send group information throughout the subnet ? Each router computes a spanning tree for each group. The spanning tree includes all the routers needed to broadcast data to the group
- 36. Spanning Trees for Multicast Routing
- 37. Multicast Routing (continued) ? With Link State Routing the routers are aware of network topology and the spanning tree can be computed ? With Distance Vector Routing reverse path forwarding is used. – When a router receives a packet for a multicast group for which it has no subscribers (hosts or other routers), the router sends a PRUNE message to the source router.
- 38. Congestion Control Algorithms ? Congestion - the situation in which too many packets are present in the subnet.
- 39. Causes of Congestion ? Congestion occurs when a router receives data faster than it can send it – Insufficient bandwidth – Slow hosts – Data simultaneously arriving from multiple lines destined for the same outgoing line. ? The system is not balanced – Correcting the problem at one router will probably just move the bottleneck to another router.
- 40. Congestion Causes More Congestion – Incoming messages must be placed in queues ? The queues have a finite size – Overflowing queues will cause packets to be dropped – Long queue delays will cause packets to be resent – Dropped packets will cause packets to be resent ? Senders that are trying to transmit to a congested destination also become congested – They must continually resend packets that have been dropped or that have timed-out – They must continue to hold outgoing/unacknowledged messages in memory.
- 41. Congestion Control versus Flow Control ? Flow control – controls point-to-point traffic between sender and receiver – e.g., a fast host sending to a slow host ? Congestion Control – controls the traffic throughout the network
- 42. Two Categories of Congestion Control ? Open loop solutions – Attempt to prevent problems rather than correct them – Does not utilize runtime feedback from the system ? Closed loop solutions – Uses feedback (measurements of system performance) to make corrections at runtime.
- 43. General Principles of Closed Loop Congestion Control ? Monitor the system to detect when and where congestion occurs. ? Pass this information to places where action can be taken. ? Adjust the system operation to correct the problem.
- 44. Metrics Used in Closed Loop Congestion Control ? Percentage of packets discarded due to buffer overflow ? Average queue length ? Percentage of packets that time-out ? Average packet delay ? Standard deviation of packet delay
- 45. Reducing Congestion ? Two Methods – Increase resources ? Get additional bandwidth – Use faster lines – Obtain additional lines – Utilize alternate pathways – Utilize “spare” routers – Decrease Traffic ? Send messages to senders telling them to slow down ? Deny service to some users ? Degrade service to some or all users ? Schedule usage to achieve better load balance

















































![Unit-3-Part-1 [Autosaved].ppt](https://cdn.slidesharecdn.com/ss_thumbnails/unit-3-part-1autosaved-230216062941-16596250-thumbnail.jpg?width=560&fit=bounds)