NUMERICAL & STATISTICAL METHODS FOR COMPUTER ENGINEERING
- 1. G H PATEL COLLEGE OF ENGINEERING AND TECHNOLOGY DEPARTMENT OF INFORMATION TECHNOLOGY GUIDED BY: Prof. Krupal Parikh Preparad By: Pruthvi Bhagat (150113116001) Anu Bhatt (150113116002) Meet Mehta (150113116004) Hiral Patel (150113116005) Janvi Patel (150113116006) Semester: 4 Subject : Numerical and Statistical Methods for Computer Engineering (2140706)
- 2. BISECTION METHOD or BRACKETING METHOD
- 3. WHAT IS BISECTION METHOD? Bisection method is one of the closed methods (bracketing method) to determine the root of a nonlinear equation f(x) = 0, with the following main principles: ŌĆó Using two initial values ŌĆŗŌĆŗto confine one or more roots of non-linear equations. ŌĆó Root value is estimated by the midpoint between two existing initial values.
- 4. WHY BISECTION METHOD? ŌĆó Bisection or Binary Search Method is based on the intermediate value theorem. ŌĆó It is a very simple and robust method to find the roots of any given equation. ŌĆó The method is guaranteed to converge to a root of f, if f is a continuous function on the interval [a, b] and f(a) and f(b) have opposite signs. The absolute error is halved at each step so the method converges linearly.
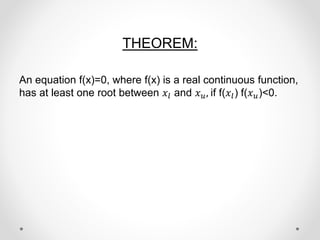
- 5. THEOREM: An equation f(x)=0, where f(x) is a real continuous function, has at least one root between ØæźØæÖ and Øæź Øæó, if f(ØæźØæÖ) f(Øæź Øæó)<0.
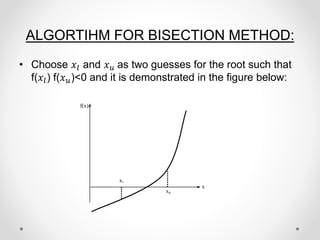
- 6. ALGORTIHM FOR BISECTION METHOD: ŌĆó Choose ØæźØæÖ and Øæź Øæó as two guesses for the root such that f(ØæźØæÖ) f(Øæź Øæó)<0 and it is demonstrated in the figure below: x’ü¼ f(x) xu x
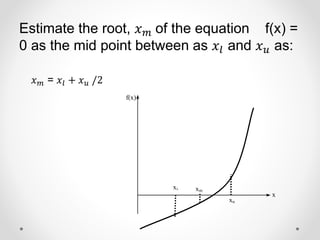
- 7. Estimate the root, Øæź ØæÜ of the equation f(x) = 0 as the mid point between as ØæźØæÖ and Øæź Øæó as: Øæź ØæÜ = ØæźØæÖ + Øæź Øæó /2 x’ü¼ f(x) xu x xm
- 8. Now check the following: ŌĆó If f(ØæźØæÖ)f(Øæź ØæÜ)<0, then the root lies between ØæźØæÖ and Øæź ØæÜ; then ØæźØæÖ = ØæźØæÖ ; Øæź Øæó = xm. ŌĆó If f(ØæźØæÖ)f(Øæź ØæÜ)>0 , then the root lies between xm and Øæź Øæó; then ØæźØæÖ = Øæź ØæÜ; Øæź Øæó = Øæź Øæó. ŌĆó If f(ØæźØæÖ)f(Øæź ØæÜ)=0 ; then the root is Øæź ØæÜ. Stop the algorithm if this is true.
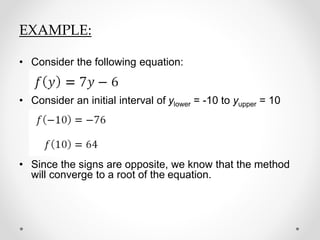
- 10. EXAMPLE: ŌĆó Consider the following equation: ŌĆó Consider an initial interval of ylower = -10 to yupper = 10 ŌĆó Since the signs are opposite, we know that the method will converge to a root of the equation.
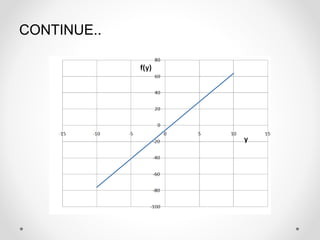
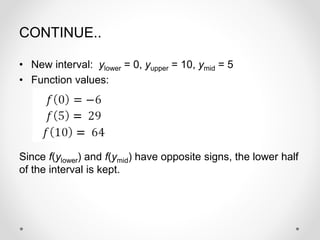
- 11. CONTINUE.. ŌĆó The value of the function at the midpoint of the interval is: ŌĆó The method can be better understood by looking at a graph of the function:
- 12. CONTINUE..
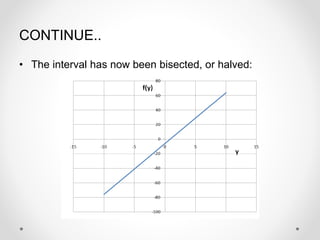
- 13. CONTINUE.. ŌĆó Now we eliminate half of the interval, keeping the half where the sign of f(midpoint) is opposite the sign of f(endpoint). ŌĆó In this case, since f(ymid) = -6 and f(yupper) = 64, we keep the upper half of the interval, since the function crosses zero in this interval.
- 14. CONTINUE.. ŌĆó The interval has now been bisected, or halved:
- 15. CONTINUE.. ŌĆó New interval: ylower = 0, yupper = 10, ymid = 5 ŌĆó Function values: Since f(ylower) and f(ymid) have opposite signs, the lower half of the interval is kept.
- 16. CONTINUE.. ŌĆó At each step, the difference between the high and low values of y is compared to 2*(allowable error). ŌĆó If the difference is greater, than the procedure continues. ŌĆó Suppose we set the allowable error at 0.0005. As long as the width of the interval is greater than 0.001, we will continue to halve the interval. ŌĆó When the width is less than 0.001, then the midpoint of the range becomes our answer.
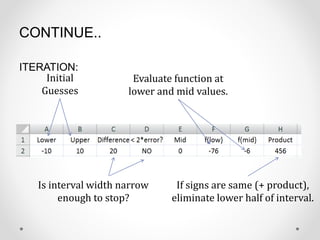
- 17. CONTINUE.. ITERATION: Initial Guesses Is interval width narrow enough to stop? Evaluate function at lower and mid values. If signs are same (+ product), eliminate lower half of interval.
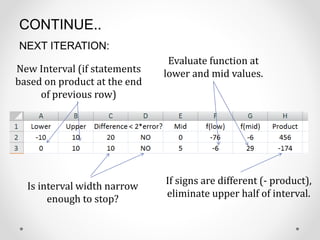
- 18. CONTINUE.. NEXT ITERATION: New Interval (if statements based on product at the end of previous row) Is interval width narrow enough to stop? Evaluate function at lower and mid values. If signs are different (- product), eliminate upper half of interval.
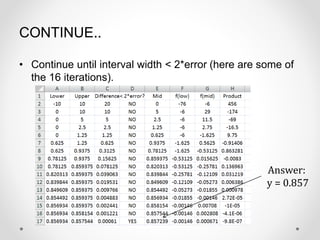
- 19. CONTINUE.. ŌĆó Continue until interval width < 2*error (here are some of the 16 iterations). Answer: y = 0.857
- 20. CONTINUE.. ŌĆó Of course, we know that the exact answer is 6/7 (0.857143). ŌĆó If we want our answer accurate to 5 decimal places, we could set the allowable error to 0.000005. ŌĆó This increases the number of iterations only from 16 to 22 ŌĆō the halving process quickly reduces the interval to very small values. ŌĆó Even if the initial guesses are set to -10,000 and 10000, only 32 iterations are required to get a solution accurate to 5 decimal places.
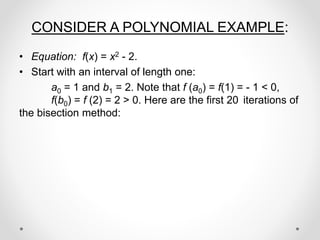
- 21. CONSIDER A POLYNOMIAL EXAMPLE: ŌĆó Equation: f(x) = x2 - 2. ŌĆó Start with an interval of length one: a0 = 1 and b1 = 2. Note that f (a0) = f(1) = - 1 < 0, f(b0) = f (2) = 2 > 0. Here are the first 20 iterations of the bisection method:
- 22. CONTINUE..
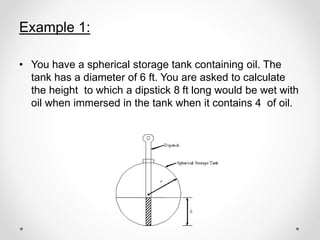
- 24. Example 1: ŌĆó You have a spherical storage tank containing oil. The tank has a diameter of 6 ft. You are asked to calculate the height to which a dipstick 8 ft long would be wet with oil when immersed in the tank when it contains 4 of oil.
- 25. CONTINUE.. ŌĆó The equation that gives the height, , of the liquid in the spherical tank for the given volume and radius is given by ŌĆó Use the bisection method of finding roots of equations to find the height, to which the dipstick is wet with oil. Conduct three iterations to estimate the root of the above equation. ŌĆó Find the absolute relative approximate error at the end of each iteration and the number of significant digits at least correct at the end of each iteration. ’Ć© ’Ć® 08197.39 23 ’ĆĮ’Ć½’ĆŁ’ĆĮ hhhf
- 26. CONTINUE.. ŌĆó Solution: ŌĆó From the physics of the problem, the dipstick would be wet between h=0 and h=2r , where r = radius of the tank, i.e.; 60 )3(20 20 ’éŻ’éŻ ’éŻ’éŻ ’éŻ’éŻ h h rh
- 27. CONTINUE.. ŌĆó Let us assume, ŌĆó Check if the function changes sign between ŌäÄØæÖ and ŌäÄ Øæó. ŌĆó Hence , ŌĆó So there is at least one root between ŌäÄØæÖ & ŌäÄ Øæó that is between 0 and 6. 6,0 ’ĆĮ’ĆĮ uhh’ü¼ ’Ć© ’Ć® ’Ć© ’Ć® ’Ć© ’Ć® 8197.38197.30900)( 23 ’ĆĮ’Ć½’ĆŁ’ĆĮ’ĆĮ fhf ’ü¼ 18.1048197.3)6(9)6()6() 23 ’ĆŁ’ĆĮ’Ć½’ĆŁ’ĆĮ’ĆĮ ff(hu ’Ć© ’Ć® ’Ć© ’Ć® ’Ć© ’Ć® ’Ć© ’Ć® ’Ć© ’Ć®’Ć© ’Ć® 018.1048197.360 ’Ć╝’ĆŁ’ĆĮ’ĆĮ ffhfhf u’ü¼
- 28. CONTINUE.. ŌĆó Iteration 1: ŌĆó The estimate of the root is =3 Hence the root is bracketed between ŌäÄØæÖand ŌäÄ ØæÜ, that is, between 0 and 3. So, the lower and upper limits of the new bracket are 2 u m hh h ’Ć½ ’ĆĮ ’ü¼ 3’ĆĮ ’Ć© ’Ć® ’Ć© ’Ć® ’Ć© ’Ć® ’Ć© ’Ć® 180.501897.33933 23 ’ĆŁ’ĆĮ’Ć½’ĆŁ’ĆĮ’ĆĮ fhf m ’Ć© ’Ć® ’Ć© ’Ć® ’Ć© ’Ć® ’Ć© ’Ć® ’Ć© ’Ć®’Ć© ’Ć® 0180.501897.330 ’Ć╝’ĆŁ’ĆĮ’ĆĮ ffhfhf m’ü¼ 3,0 ’ĆĮ’ĆĮ uhh’ü¼
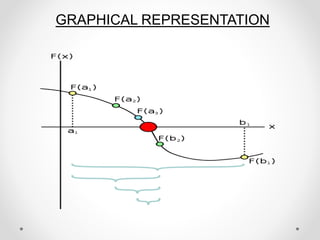
- 29. CONTINUE.. ŌĆó At this point, the absolute relative approximate error cannot be calculated, as we do not have a previous approximation. ŌĆó Root of f(x)=0 as a function of the number of iterations for bisection method. Iteration ’ü¼h uh mh %a’āÄ ’Ć© ’Ć®mhf 1 2 3 4 5 6 7 8 9 10 0.00 0.00 0.00 0.00 0.375 0.5625 0.65625 0.65625 0.65625 0.66797 6 3 1.5 0.75 0.75 0.75 0.75 0.70313 0.67969 0.67969 3 1.5 0.75 0.375 0.5625 0.65625 0.70313 0.67969 0.66797 0.67383 ---------- 100 100 100 33.333 14.286 6.6667 3.4483 1.7544 0.86957 ŌłÆ50.180 ŌłÆ13.055 ŌłÆ0.82093 2.6068 1.1500 0.22635 ŌłÆ0.28215 ŌłÆ0.024077 0.10210 0.039249
- 30. CONTINUE.. ŌĆó At the end of the 10th iteration, ŌĆó Hence the number of significant digits at least correct is given by the largest value of m for which %86957.0’ĆĮ’āÄa m a ’ĆŁ ’é┤’鯒āÄ 2 105.0 m’ĆŁ ’éŻ 2 107391.1 ’Ć© ’Ć® m’ĆŁ’éŻ 27391.1log ’Ć© ’Ć® 759.17391.1log2 ’ĆĮ’ĆŁ’éŻm m’ĆŁ ’é┤’éŻ 2 105.086957.0
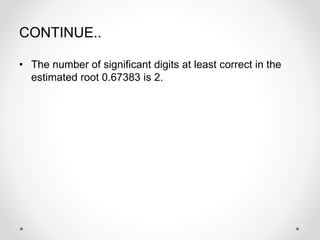
- 31. CONTINUE.. ŌĆó The number of significant digits at least correct in the estimated root 0.67383 is 2.
- 32. ADVANTAGES OF BISECTION METHOD: ŌĆó The bisection method is always convergent. Since the method brackets the root, the method is guaranteed to converge. ŌĆó As iterations are conducted, the interval gets halved. So one can guarantee the error in the solution of the equation.
- 33. DISADVANTAGES OF BISECTION METHOD: ŌĆó The convergence of the bisection method is slow as it is simply based on halving the interval. ŌĆó If one of the initial guesses is closer to the root, it will take larger number of iterations to reach the root. ŌĆó If f(x) is such that it just touches the x ŌĆōaxis, it will be unable to find the lower guess & upper guess.
- 34. CONCLUSION: ’āś Bisection method is the safest and it always converges. The bisection method is the simplest of all other methods and is guaranteed to converge for a continuous function. ’āś It is always possible to find the number of steps required for a given accuracy and the new methods can also be developed from bisection method and bisection method plays a very crucial role in computer science research.
- 35. THANK YOU




![WHY BISECTION METHOD?
ŌĆó Bisection or Binary Search Method is based on the
intermediate value theorem.
ŌĆó It is a very simple and robust method to find the roots of
any given equation.
ŌĆó The method is guaranteed to converge to a root
of f, if f is a continuous function on the interval [a, b]
and f(a) and f(b) have opposite signs. The absolute
error is halved at each step so the method converges
linearly.](https://image.slidesharecdn.com/final1-160501181042/85/NUMERICAL-STATISTICAL-METHODS-FOR-COMPUTER-ENGINEERING-4-320.jpg)