One conference 2019 the vulnerability management on steroids
- 1. Jaya Baloo Victor Gevers Michiel Steltman One conference 2019 The compelling case for vulnerability management
- 3. Why are we vulnerable ? Ī░We are vulnerable, because hard- and software has vulnerabilities. The bad guys find them and use them for themselves. So we need good guys to find them too, and then fix those leaks. ItĪ»s all we haveĪ▒ Bruce Schneier
- 4. So, why donĪ»t we just patch? 4
- 5. The patching process for companies explained 5 ?
- 6. Sounds easy but hard to achieve 100% 6 ?
- 7. Too much to deal with 7
- 8. 8 Digital Infrastructure, Including LIRs Companies with digital presence Financial servicesManufacturing Logistics Healthcare Retail MobilityGovernment Digital Services Plan B: Coordinated responsible disclosure / Bug bounties Common approach: Ī░MotivateĪ▒ Add: Actual Information
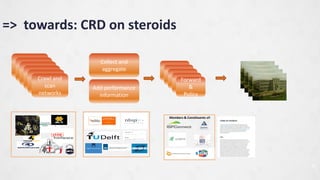
- 10. => towards: CRD on steroids 10 Crawl and scan Crawl and scan Crawl and scan Crawl and scan Crawl and scan Crawl and scan networks Add performance information Collect and aggregate Forward & Policy Members & Constituents of:
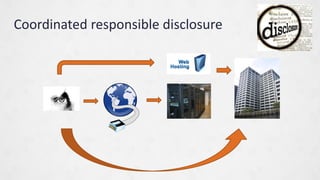
- 11. What can and should LIRs do? 11 ** Where does LIR responsibility start and stop **? -> LIR is NOT responsible, but is (as other intermediaries) a key actor in getting this going This goes way beyond ISP abuse mitigation! -LIR ( as ISP, hoster, CSP) is a key actor , the essential Ī░middle manĪ▒: - Monitor: Which badness is visible in my networks: vulnerabilities and abuse - Receive: Subscribe to feeds, receive abuse- and vulnerability information - Triage: Who has the actual problem, which user or cusromer? - Forward: Who can and should fix this? - Policy: Ī░motivateĪ▒ users / customers to act, or act yourself
- 12. Key Question to RIPE community and LIRs? 12 - Do you agree that this Ī░actual vulnerabilityĪ▒approach can be very effective? - Do you agree that the LIR is a key middleman in this approach? Concrete actions for such LIRs, what can you already do NOW: - Start with this mindset - Update your policies, accept code of conduct NtD and Abuse - Be reachable ! - Subscribe to offered aggregated feeds - Forward info and act , to customers / users - Using standard OSS systems such as Abuse-IO ? If this initiative will start, are YOU prepared to participate ?
- 13. 13 The current approach : motivate companies to patch 100%, is insufficient The solution: Find ACTUAL leaks, aggregate, add performance info, then forward the info to those who can fix©C or who can make someone fix In NL: All we need is already there! Just need to go on steroids Gov: (NCSC): take the lead, organize the PPP, connect the dots. Providers / LIRS: Adopt the CoC and start make the difference Time to act, Now!