presentationbymohakjainonviruses-150215032337-conversion-gate01 (1).pptx
Download as pptx, pdf0 likes8 views
This document discusses different types of computer viruses and harmful programs. It describes viruses as programs that attach themselves to other programs and spread across systems. There are macro viruses, file infectors, resident viruses, network viruses, logic bombs, boot sector viruses, multipartite viruses, and stealth viruses. It also discusses Trojan horse programs and worms. The document provides tips on how to protect systems by installing and updating antivirus software, being careful when downloading files, scanning removable media, using firewalls, and avoiding pirated software.
1 of 18
Download to read offline














Ad
Recommended
Presentation on Computer Viruses
Presentation on Computer Viruses Mohak Jain
Ėý
The document discusses computer viruses, defining them as programs that infiltrate systems by attaching themselves to legitimate software. It distinguishes between hackers, who explore systems legally, and crackers, who cause harm by stealing or corrupting data. Additionally, it outlines types of viruses, including macro, file infector, and boot sector viruses, and offers protection tips like using updated antivirus software and being cautious with downloads.Computer viruses
Computer virusesAlishba ijaz Muhammad Ijaz
Ėý
This document summarizes information about computer viruses presented by a student group. It discusses the history of computer viruses beginning with John von Neumann's theory of self-replicating programs in the 1940s. It describes how computer viruses are similar to biological viruses in needing a host, being capable of self-replication, and causing harm. The typical lifecycle of a computer virus is explained as waiting in an infected file until it is transmitted to another computer and spreads. Different types of viruses are outlined such as macro, boot sector, worms, Trojan horses, and logic bombs. Methods for detecting viruses using signature-based and behavior-based techniques are summarized. The document concludes with recommendations for prevention including password protecting drives, using antivirus softwareComputer Virus
Computer VirusOECLIB Odisha Electronics Control Library
Ėý
Computer viruses are malicious programs that can damage systems and erase data. There are different types like viruses, worms, and Trojan horses. Viruses piggyback on other programs to replicate, worms use networks to spread, while Trojans masquerade as useful programs but have hidden harms. Signs of infection include slow performance, crashes, and missing files. Regular antivirus updates, secure practices like avoiding untrusted sources can help prevent damage from viruses.Viruses andthreats@dharmesh
Viruses andthreats@dharmeshDharmesh Kumar Sharma
Ėý
Computer viruses and related threats were presented. Malware is defined as software designed to harm computers without the owner's consent. Common malware types were discussed including viruses, trojans, spyware, and worms. Viruses can replicate and spread, infecting files and corrupting data. Antivirus software uses signature detection, behavior monitoring, and heuristic analysis to identify and remove viruses and prevent infection. Regular antivirus updates and safe computing practices were recommended to protect against evolving malware threats.Virus bashdar
Virus bashdarBashdar Rahman
Ėý
This document discusses computer viruses including their similarities to biological viruses, what they do, types of computer viruses, sources of virus attacks, symptoms of virus infection, prevention and cures, antivirus software, and reasons why people create computer viruses. It covers main types of viruses like macro viruses, boot sector viruses, worms, Trojan horses, and logic bombs. It also discusses how viruses spread and the damage they can cause. Prevention methods include installing antivirus software and being cautious of email attachments and downloads from untrusted sources.DISHA PATEL COMPUTER VIRUS PPT.pptx
DISHA PATEL COMPUTER VIRUS PPT.pptxCENTRAL INSTITUTE OF PETROCHEMICALS ENGINEENRING AND TECHNOLOGY
Ėý
This document discusses different types of computer viruses and how to prevent them. It defines viruses and explains how they spread by attaching to other program files or through external storage devices. Common symptoms of a virus are slow computer performance, low memory, and files being deleted. The presentation recommends using up-to-date antivirus software, enabling firewalls, and being cautious of email attachments to prevent virus infection. Various virus types are outlined, including boot sector viruses, program file viruses, macro viruses, and malware like worms and spyware.Presentation related to COMPUTER VIRUS.pptx
Presentation related to COMPUTER VIRUS.pptxrubabnishwa
Ėý
The document provides an overview of computer viruses, detailing their definition, symptoms, types, and methods of spread. It emphasizes the destructive nature of viruses and offers prevention tips, including the use of antivirus software and regular data backups. The conclusion stresses the importance of staying informed about new threats and taking precautionary measures.Computer virus
Computer virusUtchi
Ėý
This document defines a computer virus and discusses how viruses spread and the types of damage they can cause. It outlines symptoms of a virus infection and types of viruses like boot sector viruses, macro viruses, and script viruses. The document recommends installing antivirus software from reputable companies, backing up files regularly, being cautious of email attachments, and avoiding unknown programs as ways to prevent virus infections.Antivirus security
Antivirus securitymPower Technology
Ėý
This document introduces the importance of antivirus security systems in safeguarding computers against various types of computer viruses, which can arise from actions like downloading files and opening email attachments. It details the mechanism of different viruses, including file infectors, boot sector viruses, trojan viruses, and worms, outlining how they spread and the potential damage they can cause. Emphasizing the need for antivirus protection, the document suggests preventive measures such as regular software updates and cautious handling of email attachments to mitigate the risk of infection.Computer Virus.pptx
Computer Virus.pptxZainAli955566
Ėý
This document defines computer viruses and their characteristics. It discusses how viruses spread and the damage they can cause. Examples like Melissa and I Love You viruses are provided. The key differences between viruses and worms are outlined. Signs of virus infection and important prevention methods like using antivirus software and avoiding unknown programs are also summarized.Virus.pptx
Virus.pptxEimerejDlcrz
Ėý
A computer virus is a malicious program that infects other programs by modifying them to replicate the virus. Viruses can spread by downloading or opening infected files from networks, email attachments, disks, or documents. Once active, viruses can damage systems by deleting files, corrupting data, or using system resources. To prevent infection, users should maintain antivirus software and scan any files from external sources.Virus
VirusTukaram Gundoor
Ėý
Computer viruses are programs that damage or disrupt normal computer functions. They attach themselves to files and replicate, spreading infection. Viruses can be transmitted via email, downloads, disks, and networks. Different types of malware include viruses, worms, Trojan horses, and hoaxes. To protect against viruses, users should install antivirus software, regularly update definitions and scan for viruses, avoid opening suspicious email attachments, and use firewalls.Computer viruses
Computer virusesSimiAttri
Ėý
The document extensively discusses computer viruses, including their definitions, types, and methods of operation and spread. It highlights the increasing prevalence of viruses due to internet usage and provides insights into common entry points and symptoms of virus attacks. Additionally, it details various techniques used by viruses and antivirus software methods to combat them, alongside preventive measures for users.Computer virus
Computer virusRahul Baghla
Ėý
This document provides information about computer viruses presented by a student group. It defines a computer virus, describes common types of viruses like Trojans and worms, and explains how viruses infect systems. The document also outlines signs of a virus attack, how to create a virus for educational purposes only, and methods for protecting against and removing viruses like installing antivirus software and deleting suspicious files. The presentation aims to educate users about computer viruses and promoting safe computing practices.Computer Viruses
Computer VirusesAman Chaudhary
Ėý
A computer virus is a malicious software program that spreads by copying itself to other computers. It can corrupt or delete data on a computer. Viruses are often spread through email attachments, downloads, and removable media. There are several types of viruses including boot viruses, program viruses, macro viruses, and polymorphic viruses. Symptoms of a virus infection include programs not working properly, critical files being deleted, and the computer running slower. It is important to have antivirus software installed and keep it updated to protect computers from virus infections.Computer virus
Computer virusRohit Nayak
Ėý
Computer viruses can infect computers through infected floppy disks or programs. There are two main types: file viruses, which infect executable files, and boot sector viruses, which infect the boot sector of disks. Viruses spread by replicating themselves and transferring to other disks or files. They can damage systems by corrupting or deleting files and programs. Users can prevent viruses by avoiding untrusted disks and files, updating antivirus software, and being wary of email attachments. Once infected, antivirus software must be used to detect and remove the virus.Computer virus
Computer virusSammer Khizer
Ėý
Computer viruses are programs that spread by infecting other programs and files. They spread through infected data or programs copied from one system to another, or through email and internet files. There are different types of viruses like boot sector viruses, file infecting viruses, and program viruses. Viruses can damage systems by corrupting and deleting files, slowing performance, and erasing data. It is important to use antivirus software to scan for and remove viruses, keep backups, and avoid opening unknown files.Computer virus & its cure
Computer virus & its cure shubhamverma2711
Ėý
This document discusses computer viruses and antivirus software. It defines a computer virus as a type of malicious software program that replicates itself and spreads from one computer to another. It explains that viruses are created by hackers, criminals, and others seeking profit or revenge. The document outlines several major types of viruses like worms, file infectors, macro viruses, and Trojan horses. It emphasizes the importance of using antivirus software to prevent viruses from infecting systems and causing data loss or other harm. The conclusion is that computers should always be protected with up-to-date antivirus security before transferring or opening any files.Computer Viruses and Classification lecture slides ppt
Computer Viruses and Classification lecture slides pptOsama Yousaf
Ėý
This document discusses different types of computer viruses and malware, including macro viruses, logic bombs, boot sector viruses, multipartite viruses, polymorphic viruses, file infectors, Trojan horses, and worms. It provides examples of each type and describes how they infect systems and spread. The document also discusses famous viruses like Melissa and I Love You, as well as methods of protection like antivirus software and firewalls.Computer Viruses
Computer Viruses Tanu Basoiya
Ėý
The document discusses computer viruses, which are malicious programs that damage data and files on a system. It outlines the types of viruses, how they spread through infected emails, removable media, and internet downloads, as well as the damage they cause, including slow performance and data loss. It also emphasizes virus prevention methods, such as using antivirus software and practicing safe computing habits.PPT on information technology laws description
PPT on information technology laws descriptionranaanish11062001
Ėý
The document discusses computer viruses, defining them as malicious software that spreads and damages data on computers, with legal implications outlined in the Information Technology Act. It details how viruses operate, their symptoms, types, including boot sector and polymorphic viruses, and notable virus outbreaks like MyDoom and ILOVEYOU. The conclusion emphasizes the need for robust cybersecurity measures to combat evolving malware threats. Computer virus
Computer virusKawsar Ahmed
Ėý
The document discusses computer viruses, how they spread and affect systems. It describes how the first virus, called "Creeper, was created in 1970s and outlines common ways viruses enter systems like through email attachments. Different virus types are outlined like memory resident viruses, boot sector viruses and macro viruses that hide in various parts of the system. Symptoms of virus infection and basic prevention tips are provided.computer virus Report
computer virus Reportrawaabdullah
Ėý
This document provides an introduction and overview of computer viruses. It defines computer viruses and explains how they work, discussing how viruses actively infect systems and spread. It categorizes common types of computer viruses such as macro viruses, memory resident viruses, overwrite viruses, and more. Specific virus names are listed as examples for each category. The document also discusses how to protect systems from computer viruses and describes some problems caused by viruses.Computer viruses
Computer virusesaagmansaini
Ėý
Computer viruses are programs that can replicate themselves and spread from one computer to another. They can corrupt files, crash systems, and steal private information. There are several types of viruses including program viruses, boot viruses, macro viruses, malware, worms, Trojan horses, spyware, and spam. It is important to have antivirus software installed and keep it updated to protect against new viruses, and to be cautious of external devices and downloads that could introduce viruses.Computer viruses
Computer virusesMDAZAD53
Ėý
This document discusses computer viruses and anti-virus packages. It defines malware and viruses, explaining that viruses attach themselves to files and programs to spread. It describes different types of viruses like boot viruses, macro viruses, multipartite viruses, and file infecting viruses. Viruses can damage systems in various ways like interrupting use, modifying settings, and destroying data. The document recommends using antivirus software, firewalls, strong passwords, and updating systems to prevent virus infections.Computer virus
Computer virusAnkita Shirke
Ėý
This document defines and describes various types of computer viruses and malware. It explains that viruses are malicious programs that spread from device to device and can damage systems or steal data. Common types of viruses mentioned include boot sector viruses, file-infecting viruses, and macro viruses. The document also discusses malware, worms, Trojans, spyware, ransomware, rootkits, and backdoors. It provides tips for protecting systems with antivirus software, firewalls, and safe computing practices.Computer Viruses
Computer Virusesadni_shadah
Ėý
Computer viruses are programs designed to spread from computer to computer and interfere with operations. The first virus appeared in 1982 as a prank. Viruses are often spread through email attachments and downloads. To protect against viruses, only open attachments from trusted sources, backup files frequently, and use antivirus software. Common types of malware include viruses, worms, Trojan horses, and boot sector viruses.informatique1as_project-virus.pptx
informatique1as_project-virus.pptxNORTHCUSTOMS
Ėý
؊؊ŲاŲŲ اŲŲØŦŲŲØĐ Ų
ØđŲŲŲ
ا؊ ØđŲ اŲŲŲØąŲØģا؊ اŲØĻØąŲ
ØŽŲØĐØ ØĻØŊØĄŲا Ų
Ų ØļŲŲØąŲا ŲŲ اŲØŦŲ
اŲŲŲا؊ ŲØŊŲØąŲا ŲŲ ØŠØŊاØŪŲ اŲØĻŲاŲا؊ ŲØŠŲØŊŲØŊ اŲØĢŲ
Ų اŲŲ
ØđŲŲŲ
ا؊Ų. ØŠØģŲØ· اŲØķŲØĄ ØđŲŲ Ø·ØĻŲØđØĐ Ø§ŲŲŲØąŲØģØ§ØŠØ Ø§ŲŲØŊØąØĐ ØđŲŲ اŲØŠŲاØģØŪØ ŲاŲØŠŲاŲŲا ØĻŲŲ اŲØĢØŽŲØēØĐØ ŲØŠŲØŊŲŲ
ŲØĩاØĶØ ŲŲØŲ
اŲØĐ Ų
ŲŲا. ØŠØīŲ
Ų اŲŲØŦŲŲØĐ ØĢŲØķŲا ØŠŲØķŲØا؊ ØŲŲ اØģØŠØŪØŊاŲ
ØŠŲŲŲا؊ اŲØŲ
اŲØĐ Ų
ØŦŲ ØĻØąØ§Ų
ØŽ Ų
ŲاŲØØĐ Ø§ŲŲŲØąŲØģا؊ ŲØŠØØ°ŲØąØ§ØŠ Ų
ØģØŠØŪØŊŲ
Ų اŲŲŲ
ØĻŲŲØŠØą.d8a7d984d981d98ad8b1d988d8b3d8a7d8aa (1).ppt
d8a7d984d981d98ad8b1d988d8b3d8a7d8aa (1).pptNORTHCUSTOMS
Ėý
ŲØŠŲاŲŲ اŲŲØŦŲŲØĐ ØĢŲŲاØđ اŲŲŲØąŲØģا؊ ŲاŲØŊŲØŊاŲ ŲاŲØĻØąŲ
ØŽŲا؊ اŲØŪØĻŲØŦØĐØ Ų
Øđ ØīØąØ ŲŲŲŲØĐ ØŠØĢØŦŲØąŲا ØđŲŲ اŲØĢØŽŲØēØĐ ŲاŲØĻŲاŲا؊. ŲŲ
ا ŲŲØķØ Ø·ØąŲ اŲØŠŲاŲ اŲŲŲØąŲØģا؊ ŲŲØģاØĶŲ اŲŲŲاŲØĐ ŲاŲØđŲا؎ Ų
ŲŲا ØĻاØģØŠØŪØŊاŲ
ØĻØąØ§Ų
ØŽ Ų
ŲاŲØØĐ Ø§ŲŲŲØąŲØģا؊. ØŠØīŲØą اŲŲØŦŲŲØĐ ØĢŲØķŲا ØĨŲŲ ØĢŲŲ
ŲØĐ Ø§ŲØŠØØŊŲØŦ اŲŲ
ØģØŠŲ
Øą ŲŲØĻØąØ§Ų
ØŽ ŲŲØŲاØļ ØđŲŲ ØĢŲ
اŲ اŲŲØļاŲ
.More Related Content
Similar to presentationbymohakjainonviruses-150215032337-conversion-gate01 (1).pptx (20)
Computer virus
Computer virusUtchi
Ėý
This document defines a computer virus and discusses how viruses spread and the types of damage they can cause. It outlines symptoms of a virus infection and types of viruses like boot sector viruses, macro viruses, and script viruses. The document recommends installing antivirus software from reputable companies, backing up files regularly, being cautious of email attachments, and avoiding unknown programs as ways to prevent virus infections.Antivirus security
Antivirus securitymPower Technology
Ėý
This document introduces the importance of antivirus security systems in safeguarding computers against various types of computer viruses, which can arise from actions like downloading files and opening email attachments. It details the mechanism of different viruses, including file infectors, boot sector viruses, trojan viruses, and worms, outlining how they spread and the potential damage they can cause. Emphasizing the need for antivirus protection, the document suggests preventive measures such as regular software updates and cautious handling of email attachments to mitigate the risk of infection.Computer Virus.pptx
Computer Virus.pptxZainAli955566
Ėý
This document defines computer viruses and their characteristics. It discusses how viruses spread and the damage they can cause. Examples like Melissa and I Love You viruses are provided. The key differences between viruses and worms are outlined. Signs of virus infection and important prevention methods like using antivirus software and avoiding unknown programs are also summarized.Virus.pptx
Virus.pptxEimerejDlcrz
Ėý
A computer virus is a malicious program that infects other programs by modifying them to replicate the virus. Viruses can spread by downloading or opening infected files from networks, email attachments, disks, or documents. Once active, viruses can damage systems by deleting files, corrupting data, or using system resources. To prevent infection, users should maintain antivirus software and scan any files from external sources.Virus
VirusTukaram Gundoor
Ėý
Computer viruses are programs that damage or disrupt normal computer functions. They attach themselves to files and replicate, spreading infection. Viruses can be transmitted via email, downloads, disks, and networks. Different types of malware include viruses, worms, Trojan horses, and hoaxes. To protect against viruses, users should install antivirus software, regularly update definitions and scan for viruses, avoid opening suspicious email attachments, and use firewalls.Computer viruses
Computer virusesSimiAttri
Ėý
The document extensively discusses computer viruses, including their definitions, types, and methods of operation and spread. It highlights the increasing prevalence of viruses due to internet usage and provides insights into common entry points and symptoms of virus attacks. Additionally, it details various techniques used by viruses and antivirus software methods to combat them, alongside preventive measures for users.Computer virus
Computer virusRahul Baghla
Ėý
This document provides information about computer viruses presented by a student group. It defines a computer virus, describes common types of viruses like Trojans and worms, and explains how viruses infect systems. The document also outlines signs of a virus attack, how to create a virus for educational purposes only, and methods for protecting against and removing viruses like installing antivirus software and deleting suspicious files. The presentation aims to educate users about computer viruses and promoting safe computing practices.Computer Viruses
Computer VirusesAman Chaudhary
Ėý
A computer virus is a malicious software program that spreads by copying itself to other computers. It can corrupt or delete data on a computer. Viruses are often spread through email attachments, downloads, and removable media. There are several types of viruses including boot viruses, program viruses, macro viruses, and polymorphic viruses. Symptoms of a virus infection include programs not working properly, critical files being deleted, and the computer running slower. It is important to have antivirus software installed and keep it updated to protect computers from virus infections.Computer virus
Computer virusRohit Nayak
Ėý
Computer viruses can infect computers through infected floppy disks or programs. There are two main types: file viruses, which infect executable files, and boot sector viruses, which infect the boot sector of disks. Viruses spread by replicating themselves and transferring to other disks or files. They can damage systems by corrupting or deleting files and programs. Users can prevent viruses by avoiding untrusted disks and files, updating antivirus software, and being wary of email attachments. Once infected, antivirus software must be used to detect and remove the virus.Computer virus
Computer virusSammer Khizer
Ėý
Computer viruses are programs that spread by infecting other programs and files. They spread through infected data or programs copied from one system to another, or through email and internet files. There are different types of viruses like boot sector viruses, file infecting viruses, and program viruses. Viruses can damage systems by corrupting and deleting files, slowing performance, and erasing data. It is important to use antivirus software to scan for and remove viruses, keep backups, and avoid opening unknown files.Computer virus & its cure
Computer virus & its cure shubhamverma2711
Ėý
This document discusses computer viruses and antivirus software. It defines a computer virus as a type of malicious software program that replicates itself and spreads from one computer to another. It explains that viruses are created by hackers, criminals, and others seeking profit or revenge. The document outlines several major types of viruses like worms, file infectors, macro viruses, and Trojan horses. It emphasizes the importance of using antivirus software to prevent viruses from infecting systems and causing data loss or other harm. The conclusion is that computers should always be protected with up-to-date antivirus security before transferring or opening any files.Computer Viruses and Classification lecture slides ppt
Computer Viruses and Classification lecture slides pptOsama Yousaf
Ėý
This document discusses different types of computer viruses and malware, including macro viruses, logic bombs, boot sector viruses, multipartite viruses, polymorphic viruses, file infectors, Trojan horses, and worms. It provides examples of each type and describes how they infect systems and spread. The document also discusses famous viruses like Melissa and I Love You, as well as methods of protection like antivirus software and firewalls.Computer Viruses
Computer Viruses Tanu Basoiya
Ėý
The document discusses computer viruses, which are malicious programs that damage data and files on a system. It outlines the types of viruses, how they spread through infected emails, removable media, and internet downloads, as well as the damage they cause, including slow performance and data loss. It also emphasizes virus prevention methods, such as using antivirus software and practicing safe computing habits.PPT on information technology laws description
PPT on information technology laws descriptionranaanish11062001
Ėý
The document discusses computer viruses, defining them as malicious software that spreads and damages data on computers, with legal implications outlined in the Information Technology Act. It details how viruses operate, their symptoms, types, including boot sector and polymorphic viruses, and notable virus outbreaks like MyDoom and ILOVEYOU. The conclusion emphasizes the need for robust cybersecurity measures to combat evolving malware threats. Computer virus
Computer virusKawsar Ahmed
Ėý
The document discusses computer viruses, how they spread and affect systems. It describes how the first virus, called "Creeper, was created in 1970s and outlines common ways viruses enter systems like through email attachments. Different virus types are outlined like memory resident viruses, boot sector viruses and macro viruses that hide in various parts of the system. Symptoms of virus infection and basic prevention tips are provided.computer virus Report
computer virus Reportrawaabdullah
Ėý
This document provides an introduction and overview of computer viruses. It defines computer viruses and explains how they work, discussing how viruses actively infect systems and spread. It categorizes common types of computer viruses such as macro viruses, memory resident viruses, overwrite viruses, and more. Specific virus names are listed as examples for each category. The document also discusses how to protect systems from computer viruses and describes some problems caused by viruses.Computer viruses
Computer virusesaagmansaini
Ėý
Computer viruses are programs that can replicate themselves and spread from one computer to another. They can corrupt files, crash systems, and steal private information. There are several types of viruses including program viruses, boot viruses, macro viruses, malware, worms, Trojan horses, spyware, and spam. It is important to have antivirus software installed and keep it updated to protect against new viruses, and to be cautious of external devices and downloads that could introduce viruses.Computer viruses
Computer virusesMDAZAD53
Ėý
This document discusses computer viruses and anti-virus packages. It defines malware and viruses, explaining that viruses attach themselves to files and programs to spread. It describes different types of viruses like boot viruses, macro viruses, multipartite viruses, and file infecting viruses. Viruses can damage systems in various ways like interrupting use, modifying settings, and destroying data. The document recommends using antivirus software, firewalls, strong passwords, and updating systems to prevent virus infections.Computer virus
Computer virusAnkita Shirke
Ėý
This document defines and describes various types of computer viruses and malware. It explains that viruses are malicious programs that spread from device to device and can damage systems or steal data. Common types of viruses mentioned include boot sector viruses, file-infecting viruses, and macro viruses. The document also discusses malware, worms, Trojans, spyware, ransomware, rootkits, and backdoors. It provides tips for protecting systems with antivirus software, firewalls, and safe computing practices.Computer Viruses
Computer Virusesadni_shadah
Ėý
Computer viruses are programs designed to spread from computer to computer and interfere with operations. The first virus appeared in 1982 as a prank. Viruses are often spread through email attachments and downloads. To protect against viruses, only open attachments from trusted sources, backup files frequently, and use antivirus software. Common types of malware include viruses, worms, Trojan horses, and boot sector viruses.More from NORTHCUSTOMS (7)
informatique1as_project-virus.pptx
informatique1as_project-virus.pptxNORTHCUSTOMS
Ėý
؊؊ŲاŲŲ اŲŲØŦŲŲØĐ Ų
ØđŲŲŲ
ا؊ ØđŲ اŲŲŲØąŲØģا؊ اŲØĻØąŲ
ØŽŲØĐØ ØĻØŊØĄŲا Ų
Ų ØļŲŲØąŲا ŲŲ اŲØŦŲ
اŲŲŲا؊ ŲØŊŲØąŲا ŲŲ ØŠØŊاØŪŲ اŲØĻŲاŲا؊ ŲØŠŲØŊŲØŊ اŲØĢŲ
Ų اŲŲ
ØđŲŲŲ
ا؊Ų. ØŠØģŲØ· اŲØķŲØĄ ØđŲŲ Ø·ØĻŲØđØĐ Ø§ŲŲŲØąŲØģØ§ØŠØ Ø§ŲŲØŊØąØĐ ØđŲŲ اŲØŠŲاØģØŪØ ŲاŲØŠŲاŲŲا ØĻŲŲ اŲØĢØŽŲØēØĐØ ŲØŠŲØŊŲŲ
ŲØĩاØĶØ ŲŲØŲ
اŲØĐ Ų
ŲŲا. ØŠØīŲ
Ų اŲŲØŦŲŲØĐ ØĢŲØķŲا ØŠŲØķŲØا؊ ØŲŲ اØģØŠØŪØŊاŲ
ØŠŲŲŲا؊ اŲØŲ
اŲØĐ Ų
ØŦŲ ØĻØąØ§Ų
ØŽ Ų
ŲاŲØØĐ Ø§ŲŲŲØąŲØģا؊ ŲØŠØØ°ŲØąØ§ØŠ Ų
ØģØŠØŪØŊŲ
Ų اŲŲŲ
ØĻŲŲØŠØą.d8a7d984d981d98ad8b1d988d8b3d8a7d8aa (1).ppt
d8a7d984d981d98ad8b1d988d8b3d8a7d8aa (1).pptNORTHCUSTOMS
Ėý
ŲØŠŲاŲŲ اŲŲØŦŲŲØĐ ØĢŲŲاØđ اŲŲŲØąŲØģا؊ ŲاŲØŊŲØŊاŲ ŲاŲØĻØąŲ
ØŽŲا؊ اŲØŪØĻŲØŦØĐØ Ų
Øđ ØīØąØ ŲŲŲŲØĐ ØŠØĢØŦŲØąŲا ØđŲŲ اŲØĢØŽŲØēØĐ ŲاŲØĻŲاŲا؊. ŲŲ
ا ŲŲØķØ Ø·ØąŲ اŲØŠŲاŲ اŲŲŲØąŲØģا؊ ŲŲØģاØĶŲ اŲŲŲاŲØĐ ŲاŲØđŲا؎ Ų
ŲŲا ØĻاØģØŠØŪØŊاŲ
ØĻØąØ§Ų
ØŽ Ų
ŲاŲØØĐ Ø§ŲŲŲØąŲØģا؊. ØŠØīŲØą اŲŲØŦŲŲØĐ ØĢŲØķŲا ØĨŲŲ ØĢŲŲ
ŲØĐ Ø§ŲØŠØØŊŲØŦ اŲŲ
ØģØŠŲ
Øą ŲŲØĻØąØ§Ų
ØŽ ŲŲØŲاØļ ØđŲŲ ØĢŲ
اŲ اŲŲØļاŲ
.901130_computer1.ppt
901130_computer1.pptNORTHCUSTOMS
Ėý
ØŠØģØŠØđØąØķ اŲŲØŦŲŲØĐ Ų
ŲŲŲŲ
اŲØاØģŲØĻ ŲØĢØŽØēاØĶŲ اŲØąØĶŲØģŲØĐ Ų
ØŦŲ اŲŲ
ØđØŊا؊ ŲاŲØĻØąŲ
ØŽŲØ§ØŠØ ØĻاŲØĨØķاŲØĐ ØĨŲŲ ØŊŲØą اŲØŲاØģŲØĻ ŲŲ ØŠØØģŲŲ ØĨŲ؊ا؎ŲØĐ Ø§ŲŲ
ØĪØģØģا؊. ŲŲ
ا ØŠŲØķØ Ø§ŲØĢŲŲاØđ اŲŲ
ØŪØŠŲŲØĐ Ų
Ų اŲØŲاØģŲØĻ Ų
ØŦŲ اŲØŲاØģŲØĻ اŲŲØĻŲØąØĐ ŲاŲŲ
ØŠŲØģØ·ØĐ ŲاŲØīØŪØĩŲØĐØ ŲØŠØĢØŦŲØąŲا ŲŲ اŲØŲاØĐ Ø§ŲŲŲŲ
ŲØĐ. ØŠØŠØ·ØąŲ اŲŲØŦŲŲØĐ ØĢŲØķŲا ØĨŲŲ ØĢŲŲ
ŲØĐ ØŠŲŲŲŲŲØŽŲا اŲŲ
ØđŲŲŲ
ا؊ ŲŲ ØŠØĻاØŊŲ ŲŲ
ØđاŲØŽØĐ Ø§ŲØĻŲاŲا؊.virus-part2-150726093824-lva1-app6891.pdf
virus-part2-150726093824-lva1-app6891.pdfNORTHCUSTOMS
Ėý
This document provides an introduction to different types of computer viruses and malware. It defines viruses as self-replicating programs that can spread to other files and describes how they and other malware can negatively impact computers by deleting or corrupting files, interfering with operations, and compromising security. The document outlines various malware types including trojans, worms, joke programs, droppers, and backdoors. It provides examples of how each type can function and the potential dangers they pose to infected systems.Viruses.ppt
Viruses.pptNORTHCUSTOMS
Ėý
This document defines viruses and worms, and outlines their history. It discusses how viruses spread by inserting copies of themselves into other programs, while worms are self-contained programs that spread across networks. The Morris worm of 1988 was one of the first major worms. Later, viruses spread via email with examples like Melissa and ILOVEYOU. Denial of service attacks also became an issue, like with MyDoom in 2004. Prevention methods include software updates, antivirus programs, and more secure operating systems.d8a7d984d981d98ad8b1d988d8b3d8a7d8aa.ppt
d8a7d984d981d98ad8b1d988d8b3d8a7d8aa.pptNORTHCUSTOMS
Ėý
؊؊ŲاŲŲ اŲŲØŦŲŲØĐ ØĢŲŲاØđ اŲŲŲØąŲØģا؊ اŲØاØģŲØĻŲØĐØ ØĻŲ
ا ŲŲ Ø°ŲŲ اŲŲŲØąŲØģا؊ ŲاŲØŊŲØŊ ŲاŲØĻØąØ§Ų
ØŽ اŲØķØ§ØąØĐ Ų
ØŦŲ ØØĩاŲ Ø·ØąŲاØŊØĐØ ŲØ·ØąŲ اŲØŠØīØ§ØąŲا ŲØĢØķØąØ§ØąŲا. ŲŲ
ا ØŠØģŲØ· اŲØķŲØĄ ØđŲŲ ØĢŲŲ
ŲØĐ ØĻØąØ§Ų
ØŽ اŲØŲ
اŲØĐ ŲŲØģاØĶŲ اŲŲŲاŲØĐ ØķØŊ ŲØ°Ų اŲŲŲØąŲØģØ§ØŠØ ØĻاŲØĨØķاŲØĐ ØĨŲŲ ŲŲŲŲØĐ ØŠØīØŪŲØĩ اŲØĨØĩاØĻØĐ ØĻŲا.ØŠØØąŲØą اŲŲØŠØĻ اŲØąØģŲ
ŲØĐ ŲŲ؊اØĻØĐ Ø§ŲŲ
ØŪØŠØĩØą .pptx
ØŠØØąŲØą اŲŲØŠØĻ اŲØąØģŲ
ŲØĐ ŲŲ؊اØĻØĐ Ø§ŲŲ
ØŪØŠØĩØą .pptxNORTHCUSTOMS
Ėý
اŲŲ؊اØĻ ŲØŠŲاŲŲ اŲŲ
ØĻاØŊØĶ اŲØĢØģاØģŲØĐ ŲŲ؊اØĻØĐ Ø§ŲØąØģاØĶŲ اŲØąØģŲ
ŲØĐ ØĻŲŲ اŲŲ
ØĪØģØģا؊ ŲاŲØĢŲØąØ§ØŊØ Ų
ŲØķØŲا ŲŲŲŲŲØĐ Ø§ŲØąØģاŲØĐ ŲŲ
؊طŲØĻا؊ Ų؊اØĻØŠŲا. ŲØØŠŲŲ اŲŲ؊اØĻ ØđŲŲ ØĨØąØīاØŊا؊ ØŲŲ ØŠØķŲ
ŲŲ Ų
ØđŲŲŲ
ا؊ Ų
ØŦŲ اŲØĢØģŲ
Ø§ØĄØ Ø§ŲØŠØ§ØąŲØŪØ ŲاŲØīØđØ§ØąØ ØĻاŲØĨØķاŲØĐ ØĨŲŲ ŲŲŲŲØĐ ØŠŲØļŲŲ
اŲŲ
ØØŠŲŲ ØĻØīŲŲ ØŊŲŲŲ ŲŲاØķØ. ŲØąŲØē ØđŲŲ ØĢŲŲ
ŲØĐ Ø§ØģØŠØŪØŊاŲ
اŲŲØšØĐ Ø§ŲØđØąØĻŲØĐ Ø§ŲŲØĩØŲ ŲاŲØŠŲŲØŊ ØĻاŲŲŲاØđØŊ اŲŲØšŲŲØĐ ŲŲ اŲŲ؊اØĻØĐ Ø§ŲØąØģŲ
ŲØĐ.Ad
Recently uploaded (20)
Romanticism in Love and Sacrifice An Analysis of Oscar Wildeâs The Nightingal...
Romanticism in Love and Sacrifice An Analysis of Oscar Wildeâs The Nightingal...KaryanaTantri21
Ėý
The story revolves around a college student who despairs not having a red rose as a condition for dancing with the girl he loves. The nightingale hears his complaint and offers to create the red rose at the cost of his life. He sang a love song all night with his chest stuck to the thorns of the rose tree. Finally, the red rose grew, but his sacrifice was in vain. The girl rejected the flower because it didnât match her outfit and preferred a jewellery gift. The student threw the flower on the street and returned to studying philosophyBirnagar High School Platinum Jubilee Quiz.pptx
Birnagar High School Platinum Jubilee Quiz.pptxSourav Kr Podder
Ėý
Birnagar High School Platinum Jubilee Celebration QuizPeer Teaching Observations During School Internship
Peer Teaching Observations During School InternshipAjayaMohanty7
Ėý
FOR B.ED,M.ED,M.A.EDUCATION AND ANY STUDENT OF TEACHER EDUCATIONLDMMIA Yoga S10 Free Workshop Grad Level
LDMMIA Yoga S10 Free Workshop Grad LevelLDM & Mia eStudios
Ėý
This is complete for June 17th. For the weekend of Summer Solstice
June 20th-22nd.
6/17/25: âMy now Grads, Youâre doing well. I applaud your efforts to continue. We all are shifting to new paradigm realities. Its rough, thereâs good and bad days/weeks. However, Reiki with Yoga assistance, does work.â
6/18/25: "For those planning the Training Program Do Welcome. Happy Summer 2k25. You are not ignored and much appreciated. Our updates are ongoing and weekly since Spring. I Hope you Enjoy the Practitioner Grad Level. There's more to come. We will also be wrapping up Level One. So I can work on Levels 2 topics. Please see documents for any news updates. Also visit our websites. Every decade I release a Campus eMap. I will work on that for summer 25. We have 2 old libraries online thats open. https://ldmchapels.weebly.com "
Our Monthly Class Roster is 7,141 for 6/21.
ALL students get privacy naturally. Thx Everyone.
As a Guest Student,
You are now upgraded to Grad Level.
See Uploads for âStudent Checkinsâ & âS9â. Thx.
Happy Summer 25.
These are also timeless.
Thank you for attending our workshops.
If you are new, do welcome.
For visual/Video style learning see our practitioner student status.
This is listed under our new training program. Updates ongoing levels 1-3 this summer. We just started Session 1 for level 1.
These are optional programs. I also would like to redo our library ebooks about Hatha and Money Yoga. THe Money Yoga was very much energy healing without the Reiki Method. An updated ebook/course will be done this year. These Projects are for *all fans, followers, teams, and Readers. TY for being presenting.THE PSYCHOANALYTIC OF THE BLACK CAT BY EDGAR ALLAN POE (1).pdf
THE PSYCHOANALYTIC OF THE BLACK CAT BY EDGAR ALLAN POE (1).pdfnabilahk908
Ėý
Psychoanalytic Analysis of The Black Cat by Edgar Allan Poe explores the deep psychological dimensions of the narratorâs disturbed mind through the lens of Sigmund Freudâs psychoanalytic theory. According to Freud (1923), the human psyche is structured into three components: the Id, which contains primitive and unconscious desires; the Ego, which operates on the reality principle and mediates between the Id and the external world; and the Superego, which reflects internalized moral standards.
In this story, Poe presents a narrator who experiences a psychological breakdown triggered by repressed guilt, aggression, and internal conflict. This analysis focuses not only on the gothic horror elements of the narrative but also on the narratorâs mental instability and emotional repression, demonstrating how the imbalance of these three psychic forces contributes to his downfall.Aprendendo Arquitetura Framework Salesforce - Dia 02
Aprendendo Arquitetura Framework Salesforce - Dia 02Mauricio Alexandre Silva
Ėý
Aprendendo Arquitetura Framework Salesforce - Dia 02
F-BLOCK ELEMENTS POWER POINT PRESENTATIONS
F-BLOCK ELEMENTS POWER POINT PRESENTATIONSmprpgcwa2024
Ėý
F-block elements are a group of elements in the periodic table that have partially filled f-orbitals. They are also known as inner transition elements. F-block elements are divided into two series:
1.Lanthanides (La- Lu) These elements are also known as rare earth elements.
2.Actinides (Ac- Lr): These elements are radioactive and have complex electronic configurations.
F-block elements exhibit multiple oxidation states due to the availability of f-orbitals.
2. Many f-block compounds are colored due to f-f transitions.
3. F-block elements often exhibit paramagnetic or ferromagnetic behavior.4. Actinides are radioactive.
F-block elements are used as catalysts in various industrial processes.
Actinides are used in nuclear reactors and nuclear medicine.
F-block elements are used in lasers and phosphors due to their luminescent properties.
F-block elements have unique electronic and magnetic properties.LDMMIA Shop & Student News Summer Solstice 25
LDMMIA Shop & Student News Summer Solstice 25LDM & Mia eStudios
Ėý
6/18/25
Shop, Upcoming: Final Notes to Review as we Close Level One. Make sure to review the orientation and videos as well. Thereâs more to come and material to cover in Levels 2-3. The content will be a combination of Reiki and Yoga. Also energy topics of our spiritual collective.
Thanks again all future Practitioner Level Students. Our Levels so far are: Guest, Grad, and Practitioner. We have had over 5k Spring Views.
https://ldm-mia.creator-spring.comGladiolous Cultivation practices by AKL.pdf
Gladiolous Cultivation practices by AKL.pdfkushallamichhame
Ėý
This includes the overall cultivation practices of Rose prepared by:
Kushal Lamichhane (AKL)
Instructor
Shree Gandhi Adarsha Secondary School
Kageshowri Manohara-09, Kathmandu, Nepal
INDUCTIVE EFFECT slide for first prof pharamacy students
INDUCTIVE EFFECT slide for first prof pharamacy studentsSHABNAM FAIZ
Ėý
The inductive effect is the electron-withdrawing or electron-donating effect transmitted through sigma (Ï) bonds in a molecule due to differences in electronegativity between atoms.
---
ðđ Definition:
The inductive effect is the permanent shifting of electrons in a sigma bond caused by the electronegativity difference of atoms, resulting in partial charges within the molecule.CRYPTO TRADING COURSE BY FINANCEWORLD.IO
CRYPTO TRADING COURSE BY FINANCEWORLD.IOAndrewBorisenko3
Ėý
Unlock the Secrets of Crypto Trading with FinanceWorld.io!
Are you ready to dive into the exciting world of cryptocurrency trading? This comprehensive course by FinanceWorld.io is designed for beginners and intermediate traders who want to master the fundamentals of crypto markets, technical analysis, risk management, and trading strategies.
What youâll learn:
Introduction to blockchain and cryptocurrencies
How crypto markets work
Setting up wallets and trading accounts securely
Understanding exchanges and order types
Reading charts and technical analysis basics
Essential indicators and market signals
Risk management and portfolio diversification
Real-life trading strategies and case studies
Common mistakes and how to avoid them
Who should view this course?
Aspiring crypto traders
Investors seeking additional income sources
Anyone curious about the future of decentralized finance
Why FinanceWorld.io?
Our experts make complex concepts simple, helping you gain the confidence to navigate volatile markets and capitalize on opportunities.
Ready to start your crypto journey?
View this slide deck now and take your first step towards becoming a successful crypto trader with FinanceWorld.io!How to use search fetch method in Odoo 18
How to use search fetch method in Odoo 18Celine George
Ėý
The search_fetch is a powerful ORM method used in Odoo for some specific addons to combine the functionality of search and read for more efficient data fetching. It might be used to search for records and fetch specific fields in a single call. It stores the result in the cache memory.OBSESSIVE COMPULSIVE DISORDER.pptx IN 5TH SEMESTER B.SC NURSING, 2ND YEAR GNM...
OBSESSIVE COMPULSIVE DISORDER.pptx IN 5TH SEMESTER B.SC NURSING, 2ND YEAR GNM...parmarjuli1412
Ėý
OBSESSIVE COMPULSIVE DISORDER INCLUDED TOPICS ARE INTRODUCTION, DEFINITION OF OBSESSION, DEFINITION OF COMPULSION, MEANING OF OBSESSION AND COMPULSION, DEFINITION OF OBSESSIVE COMPULSIVE DISORDER, EPIDERMIOLOGY OF OCD, ETIOLOGICAL FACTORS OF OCD, CLINICAL SIGN AND SYMPTOMS OF OBSESSION AND COMPULSION, MANAGEMENT INCLUDED PHARMACOTHERAPY(ANTIDEPRESSANT DRUG+ANXIOLYTIC DRUGS), PSYCHOTHERAPY, NURSING MANAGEMENT(ASSESSMENT+DIAGNOSIS+NURSING INTERVENTION+EVALUATION)) List View Components in Odoo 18 - Odoo šÝšÝßĢs
List View Components in Odoo 18 - Odoo šÝšÝßĢsCeline George
Ėý
In Odoo, there are many types of views possible like List view, Kanban view, Calendar view, Pivot view, Search view, etc.
The major change that introduced in the Odoo 18 technical part in creating views is the tag <tree> got replaced with the <list> for creating list views. How to Add New Item in CogMenu in Odoo 18
How to Add New Item in CogMenu in Odoo 18Celine George
Ėý
In Odoo 18, CogMenu (or Configuration Menu) is a feature typically found in various modules that allows users to configure settings related to that specific module. It has a cogwheel like icon usually located on the top left side of the screen. By default, the features for Importing and Exporting will be available inside the menu.Ad
presentationbymohakjainonviruses-150215032337-conversion-gate01 (1).pptx
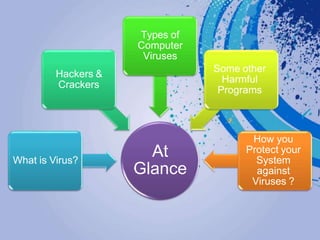
- 2. At Glance What is Virus? Hackers & Crackers Types of Computer Viruses Some other Harmful Programs How you Protect your System against Viruses ?
- 3. A virus is a program that enters the computer system by attacking itself to another program and then spreads itself across the system.
- 4. There are two different types of people who write computer virus programs â ï§Hackers ï§Crackers Hackers refers to the people who use their skills to enter into computer system without authorization. Hackers are computer enthusiasts, who break into secure systems to gain knowledge about them and possibly use their knowledge to play pranks. A Cracker is malicious programmer who gain unauthorized access to computer system for the purpose of stealing, altering or corrupting information.
- 5. There are so many types of computer viruses. Some of them are : Macro Virus File Infector Resident Virus Network Virus Logic Bomb Boot Sector Virus Multipartite Virus Stealth Virus
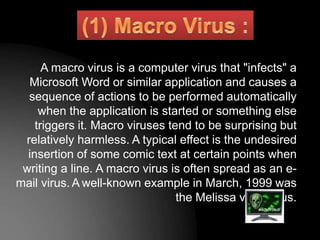
- 6. A macro virus is a computer virus that "infects" a Microsoft Word or similar application and causes a sequence of actions to be performed automatically when the application is started or something else triggers it. Macro viruses tend to be surprising but relatively harmless. A typical effect is the undesired insertion of some comic text at certain points when writing a line. A macro virus is often spread as an e- mail virus. A well-known example in March, 1999 was the Melissa virus virus.
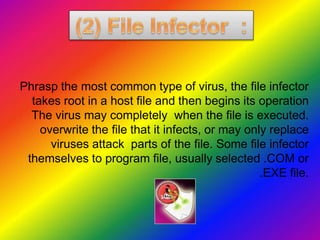
- 7. Phrasp the most common type of virus, the file infector takes root in a host file and then begins its operation when the file is executed. The virus may completely overwrite the file that it infects, or may only replace parts of the file. Some file infector viruses attack themselves to program file, usually selected .COM or .EXE file.
- 8. A board virus definition applies to any virus that inserts itself into a systemâs memory
- 9. A kind of virus spreads across networks in computers, for example, Nimda and SQL SLAMMER worms are viruses which spread over corporated networks or the internet via e-mails.
- 10. A logic Bomb is a program that get executed only when specific condition is met. The virus: Friday the 13th, , was so programmed so as to get executed on that perticular date.
- 11. A boot sector virus hides in the boot sector of hard disk. The boot sector is where your operating system is. So every time you boot your computer the virus gets loaded into the computer memory. Examples of boot-sector viruses are Polyboot B, AntiEXE.
- 12. This virus is spread by infected floppies and CDs. These viruses first infect the boot sector of hard drive and then infect the executable files stored in it. For ex.- Ywinz.
- 13. These are some virus which try to hide themselves from Anti-virus software by resorting some tricks. Stealth virus can safely show an anti-virus software that a certain file is uninfected.
- 14. A Trojan Horse program is a file that appears harmless unless it has executed. The Trojan Horse program disguises itself as a game or a utility program but when executed it can destroy the data stored in the computer. The name Trojan Horse has been derived from Greek mythology.
- 15. Worms are small pieces of software that use computer network and security holes to replicate itself. Worms on the internet spread by e-mail it searches for all the address book of the mailing system. It then mails to all recipients.
- 16. ï Install a good Anti-Virus software on your computer. ï Update Anti-Virus regularly. ï Be careful while Downloading files or programs from the internet.
- 17. ï Always scan your floppies, CDs, flash drives before using them. ï Do not use pirated software. ï Turn on firewall of your computer operating system.
- 18. Presented By: