Punimi praktik?s Anyla Merjem Ademaj
- 1. UNIVERSITETI I PRISHTIN?S FAKULTETI I INXHINIERIS? ELEKTRIKE DHE KOMPJUTERIKE Seminari i pun?s praktike TEMA: VoIP (voice over-IP) Koordinatori : Kandidati: Dr.sc.Enver HAMITI , prof.ass. Anyla ADEMAJ 23 shkurt 2012 Prishtin?
- 2. P?rmbajtja ? Falenderim ? ?ka ?sht? VoIP ? Komponentet e VoIP-it ? Nyjet e qasj?s ? Pamja e pajisj?s ? VISCA ®C konfigurimi ? Konfigurimi i nj? porte
- 3. ? Falenderoj Post?n dhe Telekomin e Kosov?s q? na mund?soi mbajtjen e praktik?s profesionale ?Menxherin kryesor? t? PTK-s? : z.Kujtim G?rvalla ?Udh?heq?sit e praktik?s profesionale : inxh.dip. Agim Abdullahu inxh.dip. Hysni Gaxherri
- 4. ?ka ?sht? VoIP? ? IP Telefonia (VoIP), ?sht? teknologji q? mund?son thirrjet telefonike duke shfryt?zuar internetin ose rrjetet tjera me komunikim t? paketave [1],[5]
- 5. N? var?si t? sh?rbimit VoIP mund t? jet? : ? Prej Komjuterit n? 1 Kompjuter(PC to PC) ? Prej PC n? telefon dhe 2 anasjelltas ? Prej telefonit n? telefon 3 (Phone to Phone)
- 6. Komponentet e VOIP-it ? Terminalet P?rfshin? IP telefonat dhe aplikacionet softverike n? PC. ? Gatekeeper Jan? kompjuter t? cil?t mund?sojn? p?rkthimin e adresave,kontrollimin hyrjeve,menaxhimin e gj?resis? se brezit,menaxhimin e zon?s ? Ruteri Lidh? rrjetet n? mes vete,mund?son qasjen n? internet ? Portat(gateway) Paisje telekomunikuse t? cilat e sh?nderrojn? z?rin e pranuar nga pajisja telefonike n? paketa dhe Anasjelltas [2],[5]
- 7. NYJET E QASJES ?N? Nyje t? Qasj?s (Access Node) mund?sohet lidhja e konsumator?ve, konfigurimi dhe fshirja apo ?ky?ja e parapaguesve. ?Pajisja e instaluar n? PTK °∞MASN°±(Multi Service Access Node) Nyje e qasjes shum?sh?rbimshe ®Clidh? linjat telefonike t? konsumator?ve dhe rrjetin q?ndror baz?. ?MASN- ofron p?rfshirjen e shum? sh?rbime n? nj? pajisje q? mbulon rrjetat IP dhe ATM(asynchronous tranfer mode) ? Sh?rbimet brezngushta ( narrowband -NB ) (°‹ 2Mb) ku hyn? edhe VOIP ?Sh?rbimet brezgj?ra ( brodband -BB) (>2Mb)
- 8. Aplikacioni i p?rdorur n? nj? sistem menaxhues t? nyjes ?sht? : 1353 DN LMS Shpr?ndarja e nyjeve n? Kosov? (n? secilin qytet pastaj ka ndarje tjera ) P?r ta leht?suar ?asjen n? problemet e ndryshme paraqiten me ngjyra Nyj?s s? caktuar mund ti qasemi kur klikojm? Show Equipment ( trego pajisjen) [3]
- 9. Pamja e pajisjes ?Nj? raft (rack) mund ti ket? deri n? 4 n?nrafta (subrack) ?Pamja n? aplikacion i ?sht? p?rshtatur pamj?s fizike N ? ?MainSubrack ®C N?nrafti n R r kryesor A a f F t i ?Extension Subrack ®Cn?nrafti T shtes? q? mund t? jen? deri I n? 3 p?r kapacitet m? t? madh ? 22 module tek n?nrafti kryesor- mund t? suportohen sh?rbimet me brezgj?r? (BB) dhe brez?ngusht? (NB) [3]
- 10. VISCA- (Voice over IP Server Card A) Tek 22 modulet mund t? vendoset edhe VISCA ? VISCA mund?son kodimin e z?rit;operon si modem me 48 dhe 96 kanale ? Max : 960 parapagues ? Gjeneron t? gjitha llojet e toneve ? N? nj? Litespan p?r sh?rbime brez?ngushta(NB) mund t? jen? 1920 parapagues [2]
- 11. VISCA VoIP service card A1353 LMS005 ? Pamja e nj? n?nrafti Vendoset VISCA n? nj?rin modul(mund t? vendosen deri n? 4 p?r m? shum? parapagues) N? nj? n?nraft mund t? ket? edhe module p?r sh?rbime brezgj?r? [3]
- 12. Moduli shtes? p?r parapagues oATLC-E (Analog Telefon Line Card) ®CKarta p?r telefon(parapaguesit) analog Klikojm? n? cil?ndo prej k?tyre moduleve p?r ti par? parapaguesit e vendosur n? t? (deri 32 parapagues) [3],[4]
- 13. VISCA -VoIP service card konfigurimi ?Nd?rfaqja e portes s? mediave(Media Gateway Interface) Realizohet komunikimi n? mes t? Port?s s? Mediave(MG) dhe Kontrollerit t? Port?s s? Mediave(MGC) p?rmes IP adresave p?rkatese. User Datagram Protocol ®C UDP ®C protokolli i paketave t? p?rdoruesit [3],[5]
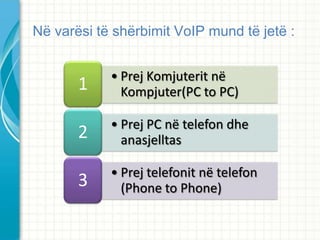
- 14. Konfigurimi i nj? porte Klikojm? n? nj?r?n prej portit p?r t? 32 portet me emrat konfiguruar nj?rin p?rkat?s t? parapaguesve
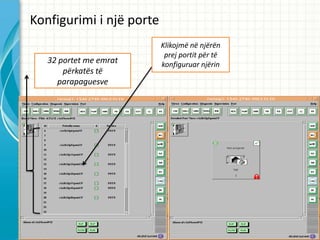
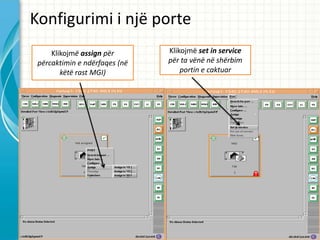
- 15. Konfigurimi i nj? porte Klikojm? assign p?r Klikojm? set in service p?rcaktimin e nd?rfaqes (n? p?r ta v?n? n? sh?rbim k?t? rast MGI) portin e caktuar
- 16. Referencat [1] www.voip-info.org [2] www.alcatel.com [3] Prt sc nga PTK-ja [korrik 2011] [4] http://www.answers.com/topic/voice-over-internet- protocol [5] Punim diplome - Besnik Terziu [Prishtin? ,n?ntor 2008]
Editor's Notes
- #5: VoIP konverton sinjalin e z?rit nga telefoni juaj n? nj??sinjal dixhital, t? reduktuar n? m?nyr? tipike n? norm? t? dh?nave duke p?rdorur teknikat e kompresimit,n?form?t?pakove t?t? dh?nave udh?ton n? internet.Voice over IP(Voip) ?sht?thjesht?transferimiibised?ss?z?ritsit?dh?nap?rmes IP rrjetit.ndryshenga PSTN, apobartjatradicionale e bisedeszenore ,tekVoiptelefonatat , tedhenatbartenpermes IP paketave.Tekkjoteknikepajisjeteshumtakompjuterikekaneteperbashketnjerrjettevetemtetedhenave. Ata komunikojn? me d?rgimin e paketave t? t? dh?nave n? nj? tjet?r,?do paket? q? p?rmban informaten q? p?rcakton burimin dhe objektivin ekompjutereve.Pakot brenda nj? transmetimi t? vet?m mund t? marrin rrug? t? ndryshme nga fillimi n?fund n?p?r nj? rrjet te te dh?nave.VoIP ?sht?b?r?jasht?zakonishtpopullorep?rshkakt?kursimevet?nj?individimundt?b?nithirrjen?distanc?t?gjat?, sidomosp?rthirrjetnd?rkomb?tareKomunikimi zanor n?p?rmjet protokollit IP, ?sht? nj? m?nyr?, e cila mund?son d?rgimin e z?rit n?p?rmjet internetit ose rrjetave tjera me komutim t? paketave
- #6: Ekzistojn? tri m?nyra e p?rdorimitt? VoIP. I pari?sht?t? PC PC, kut?dyjapal?tduhettaken?t?tyre u kthyenn?kompjuterp?rt?komunikuar. Dyt??sht?p?rt? Phone PC, kunj?partiduhett?kontaktojn?nj?telefonn?p?rmjetkompjuterittij. Numriitelefonitt?fundit?sht? Phone.
- #7: GatewaysPaisjetelekomunikuset?cilat e sh?ndrojn?z?ritq??sht?pranuarnganj?paisjetelefonikeaposistemtelekomunikuesn?paketaoseanasjelltas.Rregullonprotokoletnd?rmjetrrjetavedhetimingunGatekeepersJan?kompjuter?t?cil?tmir?mbajn?listat e adresave IP t?konsumator?vedheportave(gateway) , b?jn?procesimin e thirrjevedhekordinohen me portatt?cilatb?jn?konvertimin e thirrjevenga IP telefonian? PSTN.P?rkthimin e adres?sKontrollin e hyrjeveMenaxhimin e gjer?sis? s? brezitMenaxhimin e zon?sA VoIP system includes the following basic elements: terminals, which can include IP phones and software applications running on computers; the LAN infrastructure, consisting of wiring and switches; a gatekeeper which manages the terminals in a zone, providing address resolution, registration, authentication and regulating admission to the VoIP system; optional call manager software applications running on the gatekeeper or on a standalone platform; a router, which connects LAN segments together and to WAN circuits; gateways to perform format conversions between the VoIP world and the PSTN; and optional connections to the PSTN, the Internet and to managed IP WAN services or IP VPN services. A firewall is needed when connecting to the Internet. Gateway: A machine that exists on two networks, such as the Internet and BITNET,and that can transfer mail between them.Gateway: A network element (node) that performs conversions between differentcoding and transmission formats. The gateway does this by having many types ofcommonly used transmission equipment to provide a means for interconnection.
- #8: Ngjyrattregojneproblemet e ndryshme..P.sh me ngjyretekaltereshtekurqajsa ne ate lokacionosht e nderpreme. Me ngjyretekuqeeshtekurproblemetjanetenatyres me serioze, ndersaktotjeratjaneproblemeqezakonishtjaneprezente, sidomos ne vendin tone per shkaktetensionitetj.NGN : Njerrjetibazuar ne komutimtepaketave e afte per teofruarsherbimetelekomunikuesedhe e afte per teperdorurgjeresitemedhatebrezit , teknologjite e transportitimplikojnekualitettesherbimeve (QoS), dhe ne tecilenfunksionet e sherbimitjanetepavarurangateknlologjite e transportit .Karakteristikat : Nje multi-service network I afteteperkrahe : voice, data dhe video .Rrjetqeindanrrafshet e sinjalizimitdhetekontrollitngatransporti/komutimiRrjet me interface tehapurndermjetTransportit,kontrollitdheaplikacioneveRrjetqeperdorteknologjine e paketave per tetransportuarinformacioninRrjetqegarantonQoS per tiparetendryshmetetrafikutPse NGN ?Ka kostoteulet operative PlateformetehapurKerkon me pakhapsiredheenergjiQasje e re dhe me konkuruese
- #9: Fig.2



![?ka ?sht? VoIP?
? IP Telefonia (VoIP), ?sht? teknologji q? mund?son
thirrjet telefonike duke shfryt?zuar internetin ose
rrjetet tjera me komunikim t? paketave [1],[5]](https://image.slidesharecdn.com/punimipraktiks-anylamerjemademaj-120523052743-phpapp02/85/Punimi-praktikes-Anyla-Merjem-Ademaj-4-320.jpg)
![Komponentet e VOIP-it
? Terminalet
P?rfshin? IP telefonat dhe
aplikacionet softverike n? PC.
? Gatekeeper
Jan? kompjuter t? cil?t mund?sojn?
p?rkthimin e adresave,kontrollimin
hyrjeve,menaxhimin e gj?resis? se
brezit,menaxhimin e zon?s
? Ruteri
Lidh? rrjetet n? mes vete,mund?son
qasjen n? internet
? Portat(gateway)
Paisje telekomunikuse t? cilat e
sh?nderrojn? z?rin e pranuar nga
pajisja telefonike n? paketa dhe
Anasjelltas
[2],[5]](https://image.slidesharecdn.com/punimipraktiks-anylamerjemademaj-120523052743-phpapp02/85/Punimi-praktikes-Anyla-Merjem-Ademaj-6-320.jpg)

![Aplikacioni i p?rdorur n? nj?
sistem menaxhues t? nyjes
?sht? : 1353 DN LMS
Shpr?ndarja e nyjeve
n? Kosov? (n? secilin qytet
pastaj ka ndarje tjera )
P?r ta leht?suar ?asjen n?
problemet e ndryshme
paraqiten me ngjyra
Nyj?s s? caktuar mund ti
qasemi kur klikojm?
Show Equipment ( trego pajisjen)
[3]](https://image.slidesharecdn.com/punimipraktiks-anylamerjemademaj-120523052743-phpapp02/85/Punimi-praktikes-Anyla-Merjem-Ademaj-8-320.jpg)
![Pamja e pajisjes
?Nj? raft (rack) mund ti ket?
deri n? 4 n?nrafta (subrack)
?Pamja n? aplikacion i ?sht?
p?rshtatur pamj?s fizike
N
?
?MainSubrack ®C N?nrafti n
R r
kryesor A
a
f
F t
i
?Extension Subrack ®Cn?nrafti T
shtes? q? mund t? jen? deri I
n? 3 p?r kapacitet m? t? madh
? 22 module tek n?nrafti
kryesor- mund t? suportohen
sh?rbimet me brezgj?r? (BB)
dhe brez?ngusht? (NB)
[3]](https://image.slidesharecdn.com/punimipraktiks-anylamerjemademaj-120523052743-phpapp02/85/Punimi-praktikes-Anyla-Merjem-Ademaj-9-320.jpg)
![VISCA- (Voice over IP Server Card A)
Tek 22 modulet mund t?
vendoset edhe VISCA
? VISCA mund?son kodimin e
z?rit;operon si modem me 48
dhe 96 kanale
? Max : 960 parapagues
? Gjeneron t? gjitha llojet e
toneve
? N? nj? Litespan p?r sh?rbime
brez?ngushta(NB) mund t?
jen? 1920 parapagues
[2]](https://image.slidesharecdn.com/punimipraktiks-anylamerjemademaj-120523052743-phpapp02/85/Punimi-praktikes-Anyla-Merjem-Ademaj-10-320.jpg)
![VISCA VoIP service card
A1353 LMS005
? Pamja e nj? n?nrafti
Vendoset VISCA n? nj?rin
modul(mund t? vendosen
deri n? 4 p?r m? shum?
parapagues)
N? nj? n?nraft mund t?
ket? edhe module p?r
sh?rbime brezgj?r?
[3]](https://image.slidesharecdn.com/punimipraktiks-anylamerjemademaj-120523052743-phpapp02/85/Punimi-praktikes-Anyla-Merjem-Ademaj-11-320.jpg)
![Moduli shtes? p?r
parapagues
oATLC-E (Analog Telefon
Line Card) ®CKarta p?r
telefon(parapaguesit)
analog
Klikojm? n? cil?ndo prej
k?tyre moduleve p?r ti
par? parapaguesit e
vendosur n? t? (deri 32
parapagues)
[3],[4]](https://image.slidesharecdn.com/punimipraktiks-anylamerjemademaj-120523052743-phpapp02/85/Punimi-praktikes-Anyla-Merjem-Ademaj-12-320.jpg)
![VISCA -VoIP service card konfigurimi
?Nd?rfaqja e portes s?
mediave(Media Gateway
Interface)
Realizohet komunikimi
n? mes t? Port?s s?
Mediave(MG) dhe
Kontrollerit t? Port?s s?
Mediave(MGC) p?rmes IP
adresave p?rkatese.
User Datagram Protocol ®C
UDP ®C protokolli i
paketave t? p?rdoruesit
[3],[5]](https://image.slidesharecdn.com/punimipraktiks-anylamerjemademaj-120523052743-phpapp02/85/Punimi-praktikes-Anyla-Merjem-Ademaj-13-320.jpg)
![Referencat
[1] www.voip-info.org
[2] www.alcatel.com
[3] Prt sc nga PTK-ja [korrik 2011]
[4] http://www.answers.com/topic/voice-over-internet-
protocol
[5] Punim diplome - Besnik Terziu [Prishtin? ,n?ntor 2008]](https://image.slidesharecdn.com/punimipraktiks-anylamerjemademaj-120523052743-phpapp02/85/Punimi-praktikes-Anyla-Merjem-Ademaj-16-320.jpg)
