Rfid 3.hafta
- 1. RFID Teknolojisi Zinnur YeÅilyurt TuÄba Dal Ãmer IÅÄḟker 3.Hafta
- 2. RFID GÃỳvenlik Problemleri RFID ile taÅÄḟnan bilgilerin iletiÅim anÄḟnda çalÄḟnmasÄḟnÄḟ saÄlayan bir kaç saldÄḟrÄḟ çeÅidi ÅunlardÄḟr: * Fiziksel Ataklar * Denial Of Service (DoS) * Spoofing * Kulak Misafiri Olmak * Trafik Analizi
- 3. 1.Fiziksel Ataklar Etiketin fiziksel olarak etkilenmesiyle yapÄḟlan atak çeÅididir. BazÄḟ tÃỳrleri ÅunlarÄḟdÄḟr: * Probe Attacks * Material Removal Through Shaped Charges * Water Etching * Radiation Imprinting * Circuit Disruption * Clock Glitching
- 5. 2.Denial of Service (DoS) Bu saldÄḟrÄḟya en iyi örnek RF kanallarÄḟndan gelen sinyal bozma sinyalleridir. AlÄḟcÄḟnÄḟn duyarlÄḟ olduÄu band aralÄḟÄÄḟnda yÃỳksek gÃỳçte sinyal yayÄḟnÄḟ yaparak alÄḟcÄḟnÄḟn giriÅ katÄḟnÄḟn tÃỳm band için baskÄḟlanmasÄḟnÄḟ saÄlar ve alÄḟcÄḟyÄḟ âsaÄÄḟrlaÅtÄḟrÄḟrâ. Sinyal bozucu alÄḟcÄḟda seçicilik ve duyarlÄḟlÄḟk özelliklerini hedef alÄḟr.
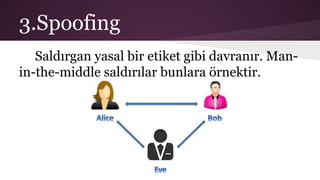
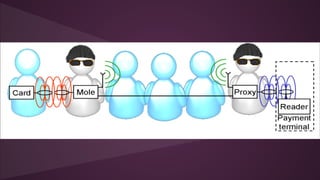
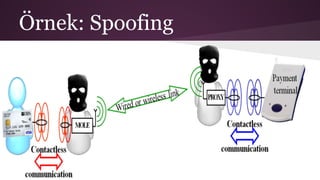
- 6. 3.Spoofing SaldÄḟrgan yasal bir etiket gibi davranÄḟr. Man- in-the-middle saldÄḟrÄḟlar bunlara örnektir.
- 10. 4.Kulak Misafiri Olmak YanlÄḟÅlÄḟkla alÄḟcÄḟ haline gelen taraf radyo sinyalini yakalayÄḟp okuyabilir.
- 11. 5.Trafik Analizi Yakalanan sinyallerde iletiÅim deÄiÅkenlerinden çÄḟkartÄḟlarak dÃỳzenlenen bilgi sayesinde mesajlarÄḟn incelenmesidir. ÄḞletiÅimde gönderilen mesajlar Åifreli olursa karÅÄḟ taraftan korunabilir.
- 12. RFID SaldÄḟrÄḟlarÄḟndan Korunmak * Kill Command * Faraday Kafesi * Aktif Sinyal Engelleme * Blocker Tag * Bill of Rights
- 13. RFID Hacking DEF CON 21 - Francis Brown - RFID Hacking Live Free or RFID Hard: https://www.youtube.com/watch? v=duzpEtkmAnI https://www.defcon.org/
- 14. RFID ÃarpÄḟÅma Problemi â Tek etiket çok okuyucu â Ãok etiket tek okuyucu â Birden fazla okuyucunun aynÄḟ frekans aralÄḟÄÄḟnÄḟ kullanmasÄḟ En yaygÄḟn olanÄḟ birincisi
- 15. ÃarpÄḟÅma önleme protokolÃỳ âbelirleyici protokoller(aÄaç temelli) âolasÄḟlÄḟÄa dayanan protokoller
- 16. Belirleyici Protokol Okuyucunun menziline giren tÃỳm etiketlerin belirlenmesi ve tek tek tanÄḟmlanmasÄḟ yani (tekilleme) tekniÄine dayanÄḟr
- 17. OlasÄḟlÄḟÄa dayalÄḟ protokol â veri ne zaman gönderilmesi gerekiyorsa o zaman gönderilir âveri yolda carpÄḟÅmaya yada bozulmaya uÄradÄḟysa rastgele secilen bir zamanda tekrar gönderilir
- 18. XML arayÃỳzÃỳ âḃProgramlama arayÃỳzÃỳ, iletiÅim için komut-cevap mesajlaÅma protokolÃỳnÃỳ kullanan xml tabanlÄḟ bir mesajlaÅma arayÃỳzÃỳdÃỳr âḃKomutun doÄru çalÄḟÅmasÄḟna baÄlÄḟ olmayarak client tarafÄḟndan gönderilen her komut, reader tarafÄḟndan cevaplanÄḟr âḃHata varsa cevap olarak nedeni döndÃỳrÃỳlÃỳr
- 19. XML arayÃỳzÃỳ âḃHer komut, reader tarafÄḟnda uygun bir karÅÄḟlÄḟÄÄḟ olan unique bir ID kullanmak zorundadÄḟr âḃArayÃỳz senkronik çalÄḟÅmÄḟyorsa bile cevaplarÄḟn doÄru bir Åekilde döndÃỳrÃỳlmesi saÄlanÄḟr
- 20. XML arayÃỳzÃỳ âḃCevap dönmesini beklemeden birden çok komut gönderebiliriz âḃReader dÃỳzenli bir Åekilde cevap döndÃỳrme iÅini Ãỳstlenir âḃClient tarafÄḟ uniq IDâ leri kullanarak cevaplarÄḟ iliÅkilendirmek zorundadÄḟr
- 21. XML arayÃỳzÃỳ âḃNormal bir komutun cevap döndÃỳrme sÃỳresi 5 saniyedir âḃBu zaman aÅÄḟmÄḟ oluÅursa client uygulamasÄḟ bir uyarÄḟ mesajÄḟ döndÃỳrebilir âḃsetConfiguration ve readTaglds gibi komutlara cevap döndÃỳrÃỳlmesi 5 saniyeden fazla sÃỳrebilir
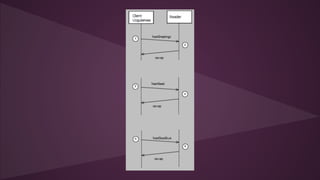
- 23. hostGreetings-hostGoodbye âḃXml kullanÄḟcÄḟ arayÃỳzÃỳnÃỳn readerâ a tanÄḟtÄḟlmasÄḟ için her iletiÅim hostGreetings komutu ile baÅlamalÄḟ âḃÄḞletiÅimi durdurmak ve Ethernetâ i kapatmak için hostGoodbye komutu kullanÄḟlÄḟr
- 24. hostGreetings Komut <frame> <cmd> <id> value_id</id> <hostGreetings> <readerType> v_readerType</readerType> <readerMode> v_ReaderMode</readerMode> <supportedVersions> <version> value_version</version> <version> value_version</version> </supportedVersions> </hostGreetings> </cmd> </frame> Cevap <frame> <reply> <id> value_id</id> <resultCode> 0</resultCode> <hostGreetings> <returnValue> <version> value_version</version> <configType> value_configType</configType> <configID> value_configID</configID> </returnValue> </hostGreetings> </reply> </frame>
- 25. hostGoodbye Komut <frame> <cmd> <id> value_id</id> <hostGoodbye> <readerMode> value_ReaderMode </readerMode> </hostGoodbye> </cmd> </frame> Cevap <frame> <reply> <id> value_id</id> <resultCode> 0</resultCode> <hostGoodbye/> </reply> </frame>
- 26. setIPConfig Komut <frame> <cmd> <id> value_id</id> <setIPConfig> <iPAddress> value</iPAddress> <subNetMask> value</subNetMask> <dHCPEnable> value</dHCPEnable> <gateway> value</gateway> </setIPConfig> </cmd> </frame> Cevap <frame> <reply> <id> value_id</id> <resultCode> 0</resultCode> <setIPConfig/> </reply> </frame>