Ssh brute force sald?r?lar?
Download as docx, pdf1 like2,179 views
Ssh Brute Force Attacks - Documentation
1 of 7
Downloaded 18 times

![Zay?f ?ifrelere sahip oldu?unuzda rastgele ?ifreler denenerek brute force sald?r?lar?
ger?ekle?tirilebilmektedir. ?nternette wordlist diye adland?r?lan kelime listeleri ile otomatize
ara?lar ile brute force sald?r?lar? denenebilmektedir.
Genel olarak brute force sald?r?lar? olsun, ya da ssh brute force sald?r?lar? olsun bu saldr? tipleri
ile ilgili bir ?ok ara? bulunmaktad?r.
Hydra, Medusa, Ncrack, Metasploit, HttpBrute gibi daha bir ?ok farkl? sald?r? yapmam?za imkan
tan?yan ara? bulunmaktad?r.
?imdi ?rnek bir senaryo ile ssh brute force sald?r?s?n? ger?ekle?tirelim ve bunu tespit edelim.
Lab ortam? i?in ©╣? farkl? da??t?m gerekmektedir.
** Ubuntu Desktop(Sald?r? yap?lacak s©╣r©╣m ?nemli de?il)
** Kali linux Atak ama?l? kullan?lacak
**Seurity onion sald?r? tespit ama?l?
Sald?r? i?leyi? bi?imine gelicek olursak;
?ncelikle vmware sanal makinalarda bulunan da??t?mlar?m?z aktif edilir. Daha sonra ubuntu
desktop makinam?z?n ifconfig komutu ile ip adresini ??reniriz. [ 192.168.221.133 ip adresimiz ]](https://image.slidesharecdn.com/sshbruteforcesaldrlar-141117105015-conversion-gate02/85/Ssh-brute-force-saldirilari-4-320.jpg)
Ad
Recommended
Microsoft Sentinel- a?cloud native SIEM & SOAR.pdf
Microsoft Sentinel- a?cloud native SIEM & SOAR.pdfKranthi Aragonda
?
This document provides an overview of Microsoft Sentinel, a cloud-native SIEM and SOAR solution. It discusses what SOAR is, important SOAR capabilities like security orchestration and automation. It also covers the benefits of SOAR like faster incident detection and boosting analyst productivity. The document then explains how Microsoft Sentinel collects data at cloud scale, responds to incidents with automation, and detects threats using analytics. It describes features like data connectors, workbooks, hunting, notebooks and certifications related to Microsoft Sentinel.DCS - Distributed Control System
DCS - Distributed Control System Pratheep M
?
The document discusses distributed control systems (DCS), including their evolution, architecture, components, and applications in power plants. A DCS decentralizes control of an entire plant or manufacturing system across multiple controllers that communicate with each other. It allows for monitoring and control of all processes, identification of faults, and improved safety. A typical DCS architecture includes servers to collect and share data, archives for data storage, operator stations to monitor processes and alarms, engineering stations to configure the system, master controllers to supervise devices and modules, and field devices where the actual processes take place. DCS systems are hierarchical with lower-level controllers handling basic functions and higher-level controllers coordinating plant-wide control.Allen Bradley- Micrologix PLC Instructions
Allen Bradley- Micrologix PLC InstructionsNFI - Industrial Automation Training Academy
?
This document provides comprehensive instructions on programming Allen Bradley MicroLogix PLCs, detailing input/output addressing, timer and counter configurations, logic programming, and flow control instructions. It includes examples for various programming functions such as scaling, negating, and file operations, as well as advanced topics like sequencers and error handling. Additionally, it promotes training courses and resources for learning PLC programming.Zero trust deck 2020
Zero trust deck 2020Guido Marchetti
?
The document outlines a strategy for implementing a modern zero-trust security framework over 30 days, emphasizing the need for a security perimeter that adapts to evolving threats. Key principles include always verifying user identity and device health, minimizing access based on necessity, and utilizing adaptive policies for risk management. It highlights the increasing risks from identity attacks and recommends integrating strong authentication measures and robust identity and access management solutions. HITCON FreeTalk 2022 - Zero Trust Architecture ūxĢ°╣Pėø
HITCON FreeTalk 2022 - Zero Trust Architecture ūxĢ°╣Pėø Hacks in Taiwan (HITCON)
?
The document discusses implementing a zero trust architecture (ZTA) based on the guidance from NIST SP 1800-35. It describes how NIST SP 1800-35 uses enhanced identity governance (EIG) as the first step towards a ZTA. It outlines the physical and information architecture of the ZTA lab described in NIST SP 1800-35, including the use of Okta, Ivanti, and other identity and access management tools. It also summarizes the future directions discussed in NIST SP 1800-35, such as using micro-segmentation and software-defined perimeters to further a ZTA.DOC-LIST.pdf
DOC-LIST.pdfKumarn Ggs
?
This document provides a list of documentation available from Compressor Controls Corporation (CCC) for their Total Train Control Release (TTCR) 13.1. It includes documents covering new features, change history, search functionality, navigation tips, and links to documentation for various CCC controller products, software, and topics. Technical notes, application notes, forms, specifications and other documentation types are organized under headings like "Sales Support Documentation", "TrainTools Software Documentation", and more.Industrial control systems cybersecurity.ppt
Industrial control systems cybersecurity.pptDelforChacnCornejo
?
This document discusses industrial control system (ICS) cybersecurity. It begins with an introduction to ICS, including supervisory control and data acquisition (SCADA) systems, distributed control systems (DCS), and programmable logic controllers (PLC). It then compares ICS and IT security, discussing risks specific to ICS. The document outlines the risk management process and describes ICS security architecture, including network segmentation. It also covers authentication, firewall implementation, and applying the six steps of the NIST risk management framework to implement security controls for ICS.Juraci Paix?o Kr?hling - All you need to know about OpenTelemetry
Juraci Paix?o Kr?hling - All you need to know about OpenTelemetryJuliano Costa
?
The document presents an overview of the OpenTelemetry framework, emphasizing its origins, specifications, and components like instrumentation and the collector. It highlights the evolution from OpenTracing and OpenCensus to OpenTelemetry, and notes the future developments in distributed tracing and metrics. Key takeaways include the importance of the OTLP data specification and the varying interests of developers, site reliability engineers, and vendors in the OpenTelemetry ecosystem.Insight into SOAR
Insight into SOARDNIF
?
The document outlines the concept of SOAR (Security Orchestration, Automation and Response), emphasizing its components, integration capabilities, and the benefits it brings to security operations centers (SOCs). It highlights issues faced by current SOCs, such as alert fatigue and operational inefficiencies, and contrasts standalone SOAR solutions with SIEM+SOAR configurations. The content also discusses the increase in efficiency and improved incident response times afforded by the implementation of SOAR technologies. PPT on INDUSTRIAL AUTOMATION, PLC, SCADA
PPT on INDUSTRIAL AUTOMATION, PLC, SCADAAakashkumar276
?
The document discusses industrial automation, focusing on technologies like PLC (Programmable Logic Controller) and SCADA (Supervisory Control and Data Acquisition) used in manufacturing and process control. It outlines various components, types, and brands of PLCs, along with their advantages and disadvantages in industrial applications. Additionally, it highlights the necessity for designing, maintaining, and troubleshooting automation systems across different industries.Cyber threat intelligence: maturity and metrics
Cyber threat intelligence: maturity and metricsMark Arena
?
The document discusses the components and processes of cyber threat intelligence, emphasizing the importance of defining intelligence requirements, production, and collection to address potential threats effectively. It outlines the maturity of intelligence programs based on their ability to assess business risks and produce relevant intelligence outputs. Additionally, it highlights the need for continual updates to requirements, collaboration with other organizations, and measures for evaluating the effectiveness of intelligence products.MITRE ATT&CK Framework
MITRE ATT&CK Frameworkn|u - The Open Security Community
?
The document discusses the MITRE ATT&CK framework, which is a knowledge base of adversary behaviors and tactics collected from real-world observations. It describes how the framework categorizes behaviors using tactics, techniques, and procedures. The framework can be used for threat intelligence, detection and analytics, adversary emulation, and assessment and engineering. The document provides examples of how organizations can map their detection capabilities and data sources to techniques in the framework to improve visibility of attacks. It cautions against misusing the framework as a checklist rather than taking a threat-informed approach.ISO 27004- Information Security Metrics Implementation
ISO 27004- Information Security Metrics ImplementationNetwork Intelligence India
?
The document discusses the implementation of information security metrics based on ISO 27004, providing guidance on measuring the effectiveness of information security management systems (ISMS) and associated controls as specified in ISO 27001. It outlines the necessity for measurement to manage security effectively, detailing the process of selecting measures, collecting data, and interpreting results to improve security posture. The advantages of adhering to ISO 27004 include better management decision-making, enhanced accountability, and improved visibility of security risks.TRITON: The Next Generation of ICS Malware
TRITON: The Next Generation of ICS MalwareThomas Roccia
?
The document provides an overview of the Triton malware, which targets industrial control systems, specifically safety instrumented systems (SIS) used in critical infrastructure. It discusses the history of ICS malware, details the Triton attack's execution and components, and emphasizes the sophisticated nature of the attackers, alongside lessons learned regarding improved security measures. Key insights include the importance of robust IT/OT security integration and vulnerabilities in legacy systems exacerbated by increased connectivity.The Current ICS Threat Landscape
The Current ICS Threat LandscapeDragos, Inc.
?
The document discusses the evolving threats to industrial control systems (ICS) and the challenges in addressing these risks, highlighting the increase in cyber attacks targeting ICS from 1998 to present. It emphasizes the lack of adequate threat intelligence, training, and technology dedicated to ICS, alongside specific milestones of attacks that caused physical damage. Recommendations for improving ICS security include enabling two-factor authentication, monitoring systems, and managing third-party risks.Computer Security | Types of Computer Security | Cybersecurity Course | Edureka
Computer Security | Types of Computer Security | Cybersecurity Course | EdurekaEdureka!
?
The document outlines a cybersecurity certification course, detailing various aspects of computer security including confidentiality, data integrity, and availability. It emphasizes the importance of securing systems and networks through methods such as antivirus software, firewalls, and physical security measures. Potential losses from security attacks and best practices for maintaining security, such as keeping software updated and regular backups, are also discussed.Plc
PlcShrikant Kumbhare
?
The presentation provides an overview of programmable logic controllers (PLCs). It discusses the history and origins of PLCs, the components and operation of PLCs, programming PLCs using ladder logic, examples of PLC programming, advantages of PLCs over other control systems, and applications of PLCs in various industries. The presentation also lists some leading PLC brands and popular PLC programming software.Understanding the NIST Risk Management Framework: 800-37 Rev. 2
Understanding the NIST Risk Management Framework: 800-37 Rev. 2Denise Tawwab
?
The NIST Risk Management Framework (RMF) outlined in SP 800-37 Revision 2 provides a structured approach for managing information security and privacy risks within organizations. It emphasizes the integration of security measures throughout the system development lifecycle and involves all organizational levels in risk management. The RMF consists of eight goals and seven key steps, facilitating effective risk assessment, control, and monitoring processes to maintain security and privacy compliance.Pr©”sentation AzureAD ( Identit©” hybrides et securit©”)??Seyfallah Tagrerout? [MVP]
?
Le document traite de l'extension d'un Active Directory local vers Azure Active Directory, en mettant l'accent sur des sujets tels que l'architecture, les m©”thodes d'authentification, et les fonctionnalit©”s avanc©”es de s©”curit©”. Il aborde ©”galement des solutions comme Azure B2B, Azure MFA, et les diff©”rentes options de gestion des identit©”s. Le contenu souligne les consid©”rations n©”cessaires lors de la migration vers une identit©” hybride, ainsi que les outils disponibles pour la s©”curisation et la gestion des acc©©s. Real Life Examples of Cybersecurity with Neo4j
Real Life Examples of Cybersecurity with Neo4jNeo4j
?
The document discusses graph databases as a solution for cybersecurity challenges. It presents real-life examples of how graph databases can be used by law enforcement to connect suspect data and by banks to detect fraud rings. The document concludes by demonstrating how a company's IT infrastructure and employees could be modeled as a graph to help with cybersecurity monitoring.Industrial training presentation
Industrial training presentationisamhasbi
?
BP Chemicals (M) Sdn. Bhd hosts industrial trainees to expose them to the chemical production industry. The trainee spent 6 months learning about BPCM's Purified Terephthalic Acid production process, maintenance practices, and health and safety standards. The trainee gained hands-on experience servicing electrical equipment like motors, breakers, and generators. They also learned instrumentation skills including transmitter calibration and installed new equipment. The extensive training program helped prepare the trainee for a future career as an electrical and instrumentation technician in chemical production.Fingerprintattendancesystem 131016052949-phpapp01
Fingerprintattendancesystem 131016052949-phpapp01Muhammad Tahir Mehmood
?
This document describes a fingerprint attendance system that uses biometric fingerprint recognition for access control and attendance monitoring. The system utilizes an embedded microcontroller, fingerprint sensor module, GSM module, LCD display and other components. It is designed to accurately identify authorized individuals through their fingerprints in order to maintain attendance records, prevent manipulation, and make cheating impossible. Potential applications of the system include monitoring employee attendance in offices, industries, and other organizations.external logbook gdc
external logbook gdcJeff taly
?
The document is a log book for students completing an external attachment at JKUAT. It provides instructions for students to record their daily activities, submit weekly reports summarizing their work, and submit a final report at the end of the attachment. It details the requirements for log book contents, including recording the departments and sections worked in each day and weekly summaries of theory and practical work covered. Students must get the log book signed weekly by their industry supervisor and the log book will be reviewed when the training supervisor visits.Microsoft 365 Security and Compliance
Microsoft 365 Security and ComplianceDavid J Rosenthal
?
The document discusses the evolving landscape of cybersecurity, highlighting the critical shortage of security skills and the increasing reliance on advanced technologies like machine learning for threat detection and prevention. It emphasizes the importance of protecting users' identities, data management, and adopting a zero-trust security posture as a response to emerging threats in the mobile workforce. Additionally, it outlines various Microsoft security products and strategies aimed at mitigating vulnerabilities and securing organizational assets against cyberattacks.Cloud computing in iot seminar report
Cloud computing in iot seminar reportSKS
?
This document provides an overview of cloud computing and its role in IoT. It discusses key cloud computing concepts like SaaS, PaaS, and IaaS and how cloud services allow for cost savings, global access, and other benefits. The document also introduces IoT, describing how embedded devices connect things to the internet and how an IoT platform bridges devices and applications. Decision frameworks and architectures for IoT are outlined which involve areas like user experience, data, security and more. Finally, popular IoT platforms from Amazon, Microsoft, IBM and others are highlighted.Hacking Question and Answer
Hacking Question and Answer Greater Noida Institute Of Technology
?
This document provides an overview of hacking, including definitions of common hacking terms, a brief history of hacking, types of hacking activities, reasons why people hack, and tips for protecting systems from hackers. It defines hackers and crackers, describes early forms of hacking like phone and computer hacking. It also outlines common hacker activities after gaining access like installing backdoors, and how system administrators can help prevent hacking by patching systems, using encryption, and installing firewalls and intrusion detection systems.Internship final presentation
Internship final presentationMeme Whisper
?
This document summarizes an internship at Abu Dhabi EHS (Abu Dhabi Environment Health and Safety Center) where the intern engaged in tasks like writing emails and calls, creating PowerPoints and proposals, research, design work, translation, and more. The internship helped them learn about asking questions when unsure, being professional, organizing work, learning through observation, and presentation techniques. The environment and employees were described positively and the intern believes the experience will help them get a job in the future. Suggestions are made for Zayed University to provide more internship preparation and job application support.Building Security Operation Center
Building Security Operation CenterS.E. CTS CERT-GOV-MD
?
The document discusses building a security operations center (SOC) and provides information on why an organization would build a SOC, how to establish the necessary skills and processes, and technology solutions like HP ArcSight that can be used. It describes how HP consultants have experience building SOCs for major companies and can help customers establish an effective SOC to monitor for security events, ensure compliance, and protect the organization. It provides details on how to structure a SOC, including defining roles and processes, implementing a security information and event management (SIEM) system, and establishing performance metrics to improve over time.PAROLA KIRMA SALDIRILARI
PAROLA KIRMA SALDIRILARIBGA Cyber Security
?
S?zma testi ?al??malar? i?in BGA Bilgi G©╣venli?i A.? olarak haz?rlad???m?z uygulama kitab?
Pentest E?itimi Uygulama Kitab? [B?l©╣m 5]Beyaz ?apkal? Hacker CEH E?itimi - Parola K?rma Sald?r?lar?
Beyaz ?apkal? Hacker CEH E?itimi - Parola K?rma Sald?r?lar?PRISMA CSI
?
Bu sunum, Prisma taraf?ndan verilen Ī░Uygulamal? Beyaz ?apkal? Hacker E?itimi v1Ī▒ de anlat?lan bir ©╣niteye aittir.
PRISMA CSI ? Cyber Security and Intelligence www.prismacsi.com
Bu dok©╣man, al?nt? vererek kullan?labilir ya da payla??labilir ancak de?i?tirilemez ve ticari ama?la kullan?lamaz. Detayl? bilgiye https://creativecommons.org/licenses/by-nc-nd/4.0/legalcode.tr ba?lant?s?ndan eri?ebilirsiniz.More Related Content
What's hot (20)
Insight into SOAR
Insight into SOARDNIF
?
The document outlines the concept of SOAR (Security Orchestration, Automation and Response), emphasizing its components, integration capabilities, and the benefits it brings to security operations centers (SOCs). It highlights issues faced by current SOCs, such as alert fatigue and operational inefficiencies, and contrasts standalone SOAR solutions with SIEM+SOAR configurations. The content also discusses the increase in efficiency and improved incident response times afforded by the implementation of SOAR technologies. PPT on INDUSTRIAL AUTOMATION, PLC, SCADA
PPT on INDUSTRIAL AUTOMATION, PLC, SCADAAakashkumar276
?
The document discusses industrial automation, focusing on technologies like PLC (Programmable Logic Controller) and SCADA (Supervisory Control and Data Acquisition) used in manufacturing and process control. It outlines various components, types, and brands of PLCs, along with their advantages and disadvantages in industrial applications. Additionally, it highlights the necessity for designing, maintaining, and troubleshooting automation systems across different industries.Cyber threat intelligence: maturity and metrics
Cyber threat intelligence: maturity and metricsMark Arena
?
The document discusses the components and processes of cyber threat intelligence, emphasizing the importance of defining intelligence requirements, production, and collection to address potential threats effectively. It outlines the maturity of intelligence programs based on their ability to assess business risks and produce relevant intelligence outputs. Additionally, it highlights the need for continual updates to requirements, collaboration with other organizations, and measures for evaluating the effectiveness of intelligence products.MITRE ATT&CK Framework
MITRE ATT&CK Frameworkn|u - The Open Security Community
?
The document discusses the MITRE ATT&CK framework, which is a knowledge base of adversary behaviors and tactics collected from real-world observations. It describes how the framework categorizes behaviors using tactics, techniques, and procedures. The framework can be used for threat intelligence, detection and analytics, adversary emulation, and assessment and engineering. The document provides examples of how organizations can map their detection capabilities and data sources to techniques in the framework to improve visibility of attacks. It cautions against misusing the framework as a checklist rather than taking a threat-informed approach.ISO 27004- Information Security Metrics Implementation
ISO 27004- Information Security Metrics ImplementationNetwork Intelligence India
?
The document discusses the implementation of information security metrics based on ISO 27004, providing guidance on measuring the effectiveness of information security management systems (ISMS) and associated controls as specified in ISO 27001. It outlines the necessity for measurement to manage security effectively, detailing the process of selecting measures, collecting data, and interpreting results to improve security posture. The advantages of adhering to ISO 27004 include better management decision-making, enhanced accountability, and improved visibility of security risks.TRITON: The Next Generation of ICS Malware
TRITON: The Next Generation of ICS MalwareThomas Roccia
?
The document provides an overview of the Triton malware, which targets industrial control systems, specifically safety instrumented systems (SIS) used in critical infrastructure. It discusses the history of ICS malware, details the Triton attack's execution and components, and emphasizes the sophisticated nature of the attackers, alongside lessons learned regarding improved security measures. Key insights include the importance of robust IT/OT security integration and vulnerabilities in legacy systems exacerbated by increased connectivity.The Current ICS Threat Landscape
The Current ICS Threat LandscapeDragos, Inc.
?
The document discusses the evolving threats to industrial control systems (ICS) and the challenges in addressing these risks, highlighting the increase in cyber attacks targeting ICS from 1998 to present. It emphasizes the lack of adequate threat intelligence, training, and technology dedicated to ICS, alongside specific milestones of attacks that caused physical damage. Recommendations for improving ICS security include enabling two-factor authentication, monitoring systems, and managing third-party risks.Computer Security | Types of Computer Security | Cybersecurity Course | Edureka
Computer Security | Types of Computer Security | Cybersecurity Course | EdurekaEdureka!
?
The document outlines a cybersecurity certification course, detailing various aspects of computer security including confidentiality, data integrity, and availability. It emphasizes the importance of securing systems and networks through methods such as antivirus software, firewalls, and physical security measures. Potential losses from security attacks and best practices for maintaining security, such as keeping software updated and regular backups, are also discussed.Plc
PlcShrikant Kumbhare
?
The presentation provides an overview of programmable logic controllers (PLCs). It discusses the history and origins of PLCs, the components and operation of PLCs, programming PLCs using ladder logic, examples of PLC programming, advantages of PLCs over other control systems, and applications of PLCs in various industries. The presentation also lists some leading PLC brands and popular PLC programming software.Understanding the NIST Risk Management Framework: 800-37 Rev. 2
Understanding the NIST Risk Management Framework: 800-37 Rev. 2Denise Tawwab
?
The NIST Risk Management Framework (RMF) outlined in SP 800-37 Revision 2 provides a structured approach for managing information security and privacy risks within organizations. It emphasizes the integration of security measures throughout the system development lifecycle and involves all organizational levels in risk management. The RMF consists of eight goals and seven key steps, facilitating effective risk assessment, control, and monitoring processes to maintain security and privacy compliance.Pr©”sentation AzureAD ( Identit©” hybrides et securit©”)??Seyfallah Tagrerout? [MVP]
?
Le document traite de l'extension d'un Active Directory local vers Azure Active Directory, en mettant l'accent sur des sujets tels que l'architecture, les m©”thodes d'authentification, et les fonctionnalit©”s avanc©”es de s©”curit©”. Il aborde ©”galement des solutions comme Azure B2B, Azure MFA, et les diff©”rentes options de gestion des identit©”s. Le contenu souligne les consid©”rations n©”cessaires lors de la migration vers une identit©” hybride, ainsi que les outils disponibles pour la s©”curisation et la gestion des acc©©s. Real Life Examples of Cybersecurity with Neo4j
Real Life Examples of Cybersecurity with Neo4jNeo4j
?
The document discusses graph databases as a solution for cybersecurity challenges. It presents real-life examples of how graph databases can be used by law enforcement to connect suspect data and by banks to detect fraud rings. The document concludes by demonstrating how a company's IT infrastructure and employees could be modeled as a graph to help with cybersecurity monitoring.Industrial training presentation
Industrial training presentationisamhasbi
?
BP Chemicals (M) Sdn. Bhd hosts industrial trainees to expose them to the chemical production industry. The trainee spent 6 months learning about BPCM's Purified Terephthalic Acid production process, maintenance practices, and health and safety standards. The trainee gained hands-on experience servicing electrical equipment like motors, breakers, and generators. They also learned instrumentation skills including transmitter calibration and installed new equipment. The extensive training program helped prepare the trainee for a future career as an electrical and instrumentation technician in chemical production.Fingerprintattendancesystem 131016052949-phpapp01
Fingerprintattendancesystem 131016052949-phpapp01Muhammad Tahir Mehmood
?
This document describes a fingerprint attendance system that uses biometric fingerprint recognition for access control and attendance monitoring. The system utilizes an embedded microcontroller, fingerprint sensor module, GSM module, LCD display and other components. It is designed to accurately identify authorized individuals through their fingerprints in order to maintain attendance records, prevent manipulation, and make cheating impossible. Potential applications of the system include monitoring employee attendance in offices, industries, and other organizations.external logbook gdc
external logbook gdcJeff taly
?
The document is a log book for students completing an external attachment at JKUAT. It provides instructions for students to record their daily activities, submit weekly reports summarizing their work, and submit a final report at the end of the attachment. It details the requirements for log book contents, including recording the departments and sections worked in each day and weekly summaries of theory and practical work covered. Students must get the log book signed weekly by their industry supervisor and the log book will be reviewed when the training supervisor visits.Microsoft 365 Security and Compliance
Microsoft 365 Security and ComplianceDavid J Rosenthal
?
The document discusses the evolving landscape of cybersecurity, highlighting the critical shortage of security skills and the increasing reliance on advanced technologies like machine learning for threat detection and prevention. It emphasizes the importance of protecting users' identities, data management, and adopting a zero-trust security posture as a response to emerging threats in the mobile workforce. Additionally, it outlines various Microsoft security products and strategies aimed at mitigating vulnerabilities and securing organizational assets against cyberattacks.Cloud computing in iot seminar report
Cloud computing in iot seminar reportSKS
?
This document provides an overview of cloud computing and its role in IoT. It discusses key cloud computing concepts like SaaS, PaaS, and IaaS and how cloud services allow for cost savings, global access, and other benefits. The document also introduces IoT, describing how embedded devices connect things to the internet and how an IoT platform bridges devices and applications. Decision frameworks and architectures for IoT are outlined which involve areas like user experience, data, security and more. Finally, popular IoT platforms from Amazon, Microsoft, IBM and others are highlighted.Hacking Question and Answer
Hacking Question and Answer Greater Noida Institute Of Technology
?
This document provides an overview of hacking, including definitions of common hacking terms, a brief history of hacking, types of hacking activities, reasons why people hack, and tips for protecting systems from hackers. It defines hackers and crackers, describes early forms of hacking like phone and computer hacking. It also outlines common hacker activities after gaining access like installing backdoors, and how system administrators can help prevent hacking by patching systems, using encryption, and installing firewalls and intrusion detection systems.Internship final presentation
Internship final presentationMeme Whisper
?
This document summarizes an internship at Abu Dhabi EHS (Abu Dhabi Environment Health and Safety Center) where the intern engaged in tasks like writing emails and calls, creating PowerPoints and proposals, research, design work, translation, and more. The internship helped them learn about asking questions when unsure, being professional, organizing work, learning through observation, and presentation techniques. The environment and employees were described positively and the intern believes the experience will help them get a job in the future. Suggestions are made for Zayed University to provide more internship preparation and job application support.Building Security Operation Center
Building Security Operation CenterS.E. CTS CERT-GOV-MD
?
The document discusses building a security operations center (SOC) and provides information on why an organization would build a SOC, how to establish the necessary skills and processes, and technology solutions like HP ArcSight that can be used. It describes how HP consultants have experience building SOCs for major companies and can help customers establish an effective SOC to monitor for security events, ensure compliance, and protect the organization. It provides details on how to structure a SOC, including defining roles and processes, implementing a security information and event management (SIEM) system, and establishing performance metrics to improve over time.Similar to Ssh brute force sald?r?lar? (20)
PAROLA KIRMA SALDIRILARI
PAROLA KIRMA SALDIRILARIBGA Cyber Security
?
S?zma testi ?al??malar? i?in BGA Bilgi G©╣venli?i A.? olarak haz?rlad???m?z uygulama kitab?
Pentest E?itimi Uygulama Kitab? [B?l©╣m 5]Beyaz ?apkal? Hacker CEH E?itimi - Parola K?rma Sald?r?lar?
Beyaz ?apkal? Hacker CEH E?itimi - Parola K?rma Sald?r?lar?PRISMA CSI
?
Bu sunum, Prisma taraf?ndan verilen Ī░Uygulamal? Beyaz ?apkal? Hacker E?itimi v1Ī▒ de anlat?lan bir ©╣niteye aittir.
PRISMA CSI ? Cyber Security and Intelligence www.prismacsi.com
Bu dok©╣man, al?nt? vererek kullan?labilir ya da payla??labilir ancak de?i?tirilemez ve ticari ama?la kullan?lamaz. Detayl? bilgiye https://creativecommons.org/licenses/by-nc-nd/4.0/legalcode.tr ba?lant?s?ndan eri?ebilirsiniz.Uygulamali Sizma Testi (Pentest) Egitimi Sunumu - 1
Uygulamali Sizma Testi (Pentest) Egitimi Sunumu - 1BTRisk Bilgi G©╣venli?i ve BT Y?neti?im Hizmetleri
?
Uygulamali Sizma Testi (Pentest) Egitimi Sunumu - 1LINUX, WINDOWS VE A? S?STEMLER? SIZMA TESTLER?
LINUX, WINDOWS VE A? S?STEMLER? SIZMA TESTLER? BGA Cyber Security
?
S?zma testi ?al??malar? i?in BGA Bilgi G©╣venli?i A.? olarak haz?rlad???m?z uygulama kitab?
Pentest E?itimi Uygulama Kitab? [B?l©╣m 6]2010 Kocaeli Linux G©╣nleri - Linux G©╣venlik Uygulamalar?Linux
2010 Kocaeli Linux G©╣nleri - Linux G©╣venlik Uygulamalar?Linux Burak O?uz
?
Linux istemciler ve sunuculardag©╣venlik uygulamalar? Hacklenmis Linux Sistem Analizi
Hacklenmis Linux Sistem AnaliziBGA Cyber Security
?
Hacklenmi? Linux Sistem Analizi @BGASecurity | Uygar K?ro?lu - Samet Sazak Beyaz ?apkal? Hacker ba?lang?? noktas? e?itimi
Beyaz ?apkal? Hacker ba?lang?? noktas? e?itimiKurtulu? Karasu
?
Beyaz ?apkal? Hacker e?itimlerine gitmeden ?nce
e?itimin daha verimli ge?mesi i?in haz?rl?k yap?lmas?
amac?yla haz?rlanm?? bir ?al??mad?r.G?VENL?K S?STEMLER?N? ATLATMA
G?VENL?K S?STEMLER?N? ATLATMABGA Cyber Security
?
S?zma testi ?al??malar? i?in BGA Bilgi G©╣venli?i A.? olarak haz?rlad???m?z uygulama kitab?
Pentest E?itimi Uygulama Kitab? [B?l©╣m 4]Buffer overflow
Buffer overflowOkan YILDIZ
?
??rencilik y?llar?nda Buffer OverFlow Attacklar? i?in haz?rlanm?? basic d©╣zeyde bir d?k©╣mandir.Beyaz ?apkal? Hacker CEH E?itimi - B?l©╣m 4, 5, 6
Beyaz ?apkal? Hacker CEH E?itimi - B?l©╣m 4, 5, 6BGA Cyber Security
?
Beyaz ?apkal? Hacker CEH E?itimi - B?l©╣m 4, 5 ve 6 @BGASecurityBilge adam be?ikta? ?ube ethical hacking ve s?zma y?ntemleri etkinli?i
Bilge adam be?ikta? ?ube ethical hacking ve s?zma y?ntemleri etkinli?iEPICROUTERS
?
Bilge Adam Bilgi Teknolojileri Akademisi - Be?ikta? ?ube'sinde Sn. Neslihan T©╣rkeri'nin katk?lar? ile 22.04.2012 tarihinde ger?ekle?tirilen Ethical Hacking ve S?zma Y?ntemleri konu ba?l?kl? e?itime ait etkinlik foto?raflar? ve etkinlik sunumu.Beyaz ?apkal? Hacker CEH E?itimi - B?l©╣m 7, 8, 9
Beyaz ?apkal? Hacker CEH E?itimi - B?l©╣m 7, 8, 9BGA Cyber Security
?
Beyaz ?apkal? Hacker CEH E?itimi - B?l©╣m 7, 8 ve 9 @BGASecurity
EXPLOIT POST EXPLOITATION
EXPLOIT POST EXPLOITATIONBGA Cyber Security
?
Pentest E?itimi Uygulama Kitab? [B?l©╣m 10]
S?zma testi ?al??malar? i?in BGA Bilgi G©╣venli?i A.? olarak haz?rlad???m?z uygulama kitab?Uygulamali Sizma Testi (Pentest) Egitimi Sunumu - 1
Uygulamali Sizma Testi (Pentest) Egitimi Sunumu - 1BTRisk Bilgi G©╣venli?i ve BT Y?neti?im Hizmetleri
?
Ad
More from Ahmet Han (11)
Proje Risklerinin Tan?mlanmas?
Proje Risklerinin Tan?mlanmas?Ahmet Han
?
Yaz?l?m Proje Y?netimi dersinde yapm?? oldu?um risklerin tan?mlanmas? sunumu. Software project management lesson "Risk Definition".Bilgi g©╣venli?i ve Kriptografi Sorular?
Bilgi g©╣venli?i ve Kriptografi Sorular?Ahmet Han
?
"Bu d?k©╣man bilgi g©╣venli?i ve kriptografi dersinde haz?rlanm?? olan ?oktan se?meli sorular? i?ermektedir."Mobil Programlama Sorular?
Mobil Programlama Sorular?Ahmet Han
?
" Bu d?k©╣man 2015-2016" e?itim ??retim y?l?nda Kocaeli ?niversitesi Bilgisayar M©╣h." verilen Mobil programlama dersi ile ilgili ??renciler taraf?ndan haz?rlanm?? sorular? i?ermektedir. Baz? sorularda yanl??l?k olabilir.Her y?n©╣yle linux sistem ve network g©╣venli?i
Her y?n©╣yle linux sistem ve network g©╣venli?iAhmet Han
?
Linux, sistem ve network g©╣venli?i ©╣zerine yazm?? oldu?um ?al??malar?n baz?lar?n? bu e-book'ta toplad?m. e-book ile ilgili geri d?n©╣?lerinizi yapabilirsiniz.Bilgisayar M©╣hendisli?inde Kariyer
Bilgisayar M©╣hendisli?inde Kariyer Ahmet Han
?
Bir Sosyal Sorumluluk Projesi- Kocaeli'de Bulunan Liselere bilgisayar m©╣hendisli?inde kariyer olanaklar? ile ilgili ?al??ma
( Bilenler bilmeyenlere yol g?steriyor, bu ?ekilde di?erleri de ??reniyor.) Do?ru Tercih ile Bilgisayar M©╣hendisli?inde KariyerCentos 6.5 minimal i?so s©╣r©╣m©╣ oracle virtual box Ī«a kurulmas?
Centos 6.5 minimal i?so s©╣r©╣m©╣ oracle virtual box Ī«a kurulmas?Ahmet Han
?
Centos 6.5 minimal i?so s©╣r©╣m©╣ oracle virtual box Ī«a kurulmas?Linux sunucularda bandwitch monitoring ara?lar?
Linux sunucularda bandwitch monitoring ara?lar?Ahmet Han
?
Linux sunucularda bandwitch monitoring ara?lar?Nicola tesla
Nicola teslaAhmet Han
?
Nicola Tesla Sunumu- Kocaeli ?niversitesi Bilgisayar M©╣hendisli?i Edebiyat Dersi Sunumlar?Ad
Ssh brute force sald?r?lar?
- 1. SSH Brute Force Sald?r?lar? Ssh iki cihaz aras?nda g©╣venlik kanal?yla veri de?i?imine imkan sa?layan, izin veren bir network protokol©╣d©╣r. Birincil olarak linux ve unix gibi protokollerin kabuk hesaplar?na ula?abilmek i?in kullan?lm??t?r. Telnet gibi g©╣vensiz protokollerin yerini almak amac?yla dizayn edilmi?tir. Telnet protokol©╣ ?ifresiz bir bi?imde veri al??verisinde paralolar?n?z g?r©╣lebilecek ?ekilde tasarlanm??t?r. Ssh protokol©╣ ile veriler ?ifrelenerek g?nderildi?i i?in daha g©╣venli veri aktar?m?na olanak tan?maktad?r. Ssh sunucusu default olarak tcp port 22 ©╣zeriden haberle?me sa?lamkatad?r. Ssh client - ssh server aras?nda ger?ekle?en haberle?me sonucu ba?lant? kurulmaktad?r. Bir ?ok i?letim sistemi taraf?ndan desteklenmektedir. ssh bir ?ok uygulama ile beraber kullan?lan bir protokold©╣r. Baz? uygulamalar sadece ssh serer ve ssh client programlar?na ihtiya? duyarak ?al???rlar. Bu noktada sssh ba?lant?lar?n?n ?nemi b©╣y©╣kt©╣r.
- 2. ** Port y?nlendirme i?in kullan?labilir. ** Uzak kullan?c? ile kabu?a ba?lan?labilmektedir. ** Lokal bilgisayardan uzak bilgisayara dosya g?nderilebilmektedir. ** Ftp ile dosya g?nderimine alternatif bir g©╣venlik ?nlemi sa?lanm?? olur. ** Openssh ile ?ifrelenmi? vpn ba?lant?lar?n?n olu?mas?na imkan tan?r. ** Uzaktan sunucu kontrol©╣n©╣n sa?lanmas?na imkan tan?maktad?r.
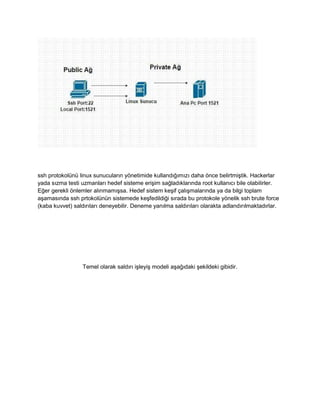
- 3. ssh protokol©╣n©╣ linux sunucular?n y?netimide kulland???m?z? daha ?nce belirtmi?tik. Hackerlar yada s?zma testi uzmanlar? hedef sisteme eri?im sa?lad?klar?nda root kullan?c? bile olabilirler. E?er gerekli ?nlemler al?nmam??sa. Hedef sistem ke?if ?al??malar?nda ya da bilgi toplam a?amas?nda ssh prtokol©╣n©╣n sistemede ke?fedildi?i s?rada bu protokole y?nelik ssh brute force (kaba kuvvet) sald?r?lar? deneyebilir. Deneme yan?lma sald?r?lar? olarakta adland?r?lmaktad?rlar. Temel olarak sald?r? i?leyi? modeli a?a??daki ?ekildeki gibidir.
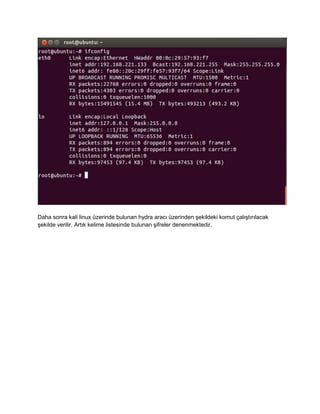
- 4. Zay?f ?ifrelere sahip oldu?unuzda rastgele ?ifreler denenerek brute force sald?r?lar? ger?ekle?tirilebilmektedir. ?nternette wordlist diye adland?r?lan kelime listeleri ile otomatize ara?lar ile brute force sald?r?lar? denenebilmektedir. Genel olarak brute force sald?r?lar? olsun, ya da ssh brute force sald?r?lar? olsun bu saldr? tipleri ile ilgili bir ?ok ara? bulunmaktad?r. Hydra, Medusa, Ncrack, Metasploit, HttpBrute gibi daha bir ?ok farkl? sald?r? yapmam?za imkan tan?yan ara? bulunmaktad?r. ?imdi ?rnek bir senaryo ile ssh brute force sald?r?s?n? ger?ekle?tirelim ve bunu tespit edelim. Lab ortam? i?in ©╣? farkl? da??t?m gerekmektedir. ** Ubuntu Desktop(Sald?r? yap?lacak s©╣r©╣m ?nemli de?il) ** Kali linux Atak ama?l? kullan?lacak **Seurity onion sald?r? tespit ama?l? Sald?r? i?leyi? bi?imine gelicek olursak; ?ncelikle vmware sanal makinalarda bulunan da??t?mlar?m?z aktif edilir. Daha sonra ubuntu desktop makinam?z?n ifconfig komutu ile ip adresini ??reniriz. [ 192.168.221.133 ip adresimiz ]
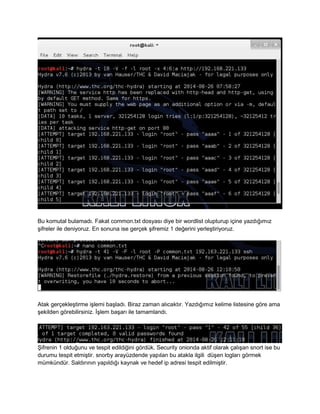
- 5. Daha sonra kali linux ©╣zerinde bulunan hydra arac? ©╣zerinden ?ekildeki komut ?al??t?r?lacak ?ekilde verilir. Art?k kelime listesinde bulunan ?ifreler denenmektedir.
- 6. Bu komutal bulamad?. Fakat common.txt dosyas? diye bir wordlist olupturup i?ine yazd???m?z ?ifreler ile deniyoruz. En sonuna ise ger?ek ?ifremiz 1 de?erini yerle?tiriyoruz. Atak ger?ekle?tirme i?lemi ba?lad?. Biraz zaman al?cakt?r. Yazd???m?z kelime listesine g?re ama ?ekilden g?rebilirsiniz. ??lem ba?ar? ile tamamland?. ?ifrenin 1 oldu?unu ve tespit edildi?ini g?rd©╣k. Security onionda aktif olarak ?al??an snort ise bu durumu tespit etmi?tir. snorby aray©╣zdende yap?lan bu atakla ilgili d©╣?en loglar? g?rmek m©╣mk©╣nd©╣r. Sald?r?n?n yap?ld??? kaynak ve hedef ip adresi tespit edilmi?tir.
- 7. Referanslar: http://rimuhosting.com/knowledgebase/linux/misc/preventing-brute-force-ssh-attacks http://blog.sucuri.net/2013/07/ssh-brute-force-the-10-year-old-attack-that-still-persists.html http://www.rebex.net/sample/terminal-client-winform/default.aspx http://doctus.org/showthread.php?t=8880 http://en.wikipedia.org/wiki/Brute-force_attack http://www.syslogs.org/centos-uzerinde-fail2ban-ile-brute-force-onlemi/ http://people.clarkson.edu/~jmatthew/publications/leet08.pdf
