SSL Demystified
0 likes42 views
The document outlines the SSL handshake process between a client and a server, detailing how public and private keys are used for secure communication. It describes various steps including the generation and exchange of random numbers, the validation of digital certificates, and key exchange methods like Diffie-Hellman and RSA. Additionally, it emphasizes the importance of confidentiality, integrity, and authentication in securing data during transmission.
1 of 15
Download to read offline







Ad
Recommended
The last picks
The last picksNafiur Rahman Tuhin
╠²
The document provides an overview of the Secure Sockets Layer (SSL) protocol, which is used for establishing an encrypted link between a web server and a browser to ensure data privacy and integrity. It details the SSL architecture, the process of SSL communicationŌĆöincluding server and client authenticationŌĆöand the various versions of the protocol. Additionally, it explains the steps involved in SSL communication and the importance of using certificates for secure transactions, such as those made on e-commerce websites.Introduction to SSL/TLS
Introduction to SSL/TLSkeithrozario
╠²
1) The client connects to a website and the server responds with a certificate and public key.
2) The client verifies the certificate with a certificate authority (CA).
3) The client then sends a randomly generated symmetric key to the server, encrypted with the server's public key.
4) All further communications are now encrypted with the random symmetric key.SSL Secure Socket Layer
SSL Secure Socket Layeromkar bhagat
╠²
SSL is a cryptographic protocol that provides secure communication over the internet. It authenticates servers, allows negotiation of encryption algorithms, and establishes an encrypted connection to securely transmit data. The SSL handshake involves a client hello, server hello, exchange of certificates and encryption keys, and change cipher spec messages to authenticate servers and agree on encryption before transmitting encrypted data over the SSL connection.How ssl works
How ssl worksSaptarshi Basu
╠²
The document explains how SSL/TLS works, detailing encryption algorithms, digital certificates, and the role of certificate authorities in ensuring secure communications. It outlines the processes for creating and verifying digital signatures, which validate the integrity and authenticity of messages. The document further describes the client-server handshake in SSL/TLS, emphasizing the exchange of certificates and the establishment of shared symmetric keys for secure data transmission.SSL intro
SSL introThree Lee
╠²
SSL/TLS is a cryptographic protocol that provides security for network communications by encrypting segments of network connections at the transport layer. It uses asymmetric and symmetric encryption, as well as digital signatures, to authenticate servers and optionally clients, and to encrypt data transmission. The handshake process establishes a shared secret between client and server to derive encryption keys, through asymmetric encryption of a randomly generated symmetric key. Subsequent communications are encrypted using the negotiated cipher suite.SSL
SSLBadrul Alam bulon
╠²
The document discusses Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols for securing communications over a network. It explains that SSL uses certificates and keys to encrypt data between a client and server so only they can access it. It then describes the different versions of SSL, how SSL establishes encrypted connections, and provides diagrams of SSL and mutual authentication processes.Sniffing SSL Traffic
Sniffing SSL Trafficdkaya
╠²
The document discusses analyzing SSL traffic and decrypting SSL connections. It provides an overview of cryptographic techniques used in SSL like symmetric and asymmetric encryption, hashing, digital signatures, and certificates. It then covers the SSL/TLS protocol structure, analyzing SSL handshakes and record layers, decrypting SSL using private keys, and tools like SSLstrip for man-in-the-middle attacks.SSL
SSLtheekuchi
╠²
TLS (Transport Layer Security) is a protocol that provides secure communication over the Internet by addressing issues of privacy, integrity, and authentication. It uses encryption to ensure privacy, message authentication codes to ensure integrity, and X.509 certificates to perform authentication between clients and servers. TLS is commonly used with HTTPS to secure web browsing and can also be used by other applications like email, voice over IP, and file transfer.Secure Socket Layer (SSL)
Secure Socket Layer (SSL)Samip jain
╠²
SSL (Secure Socket Layer) is an internet protocol ensuring secure communication between web browsers and servers, providing authentication and confidentiality. Developed by Netscape in 1994, it consists of multiple protocols including the handshake, record, change cipher, and alert protocols, facilitating secure data exchange. The latest version, TLS, evolved from SSL 3.0, incorporating enhancements for secure data transmission.Ssl in a nutshell
Ssl in a nutshellFrank Kelly
╠²
SSL provides encryption and authentication for secure communication over networks. It uses certificates signed by a certificate authority to authenticate servers and establish an encrypted connection. The SSL handshake process involves the client sending a pre-master secret encrypted with the server's public key, both sides then derive encryption keys to encrypt the connection. Debugging SSL issues may require using tools like tcpdump to monitor network traffic or adding debug flags to examine the SSL handshake.secure socket layer
secure socket layerAmar Shah
╠²
SSL and TLS are cryptographic protocols that provide secure communication on the internet. They use public/private key encryption to authenticate servers and establish encrypted connections. While similar, TLS is the standardized successor to SSL. Key differences include TLS using HMAC for integrity checking and having additional alert codes not found in SSL. Both protocols operate at the transport layer and provide data confidentiality, integrity, and server authentication.SSL/TLS 101
SSL/TLS 101Chul-Woong Yang
╠²
SSL/TLS 101 provides an overview of SSL and TLS including:
1) SSL and TLS are cryptographic protocols that provide security for internet communications like HTTPS and HTTP/2. They provide confidentiality, integrity, and authentication.
2) Key concepts of SSL/TLS include symmetric encryption for confidentiality, public key cryptography for key exchange, digital signatures for authentication, and X.509 certificates issued by certificate authorities to verify identities.
3) The document reviews the history and versions of SSL/TLS, how the core requirements of confidentiality, integrity and authentication are achieved, and references for further reading on implementing SSL/TLS.SSL
SSLDuy Do Phan
╠²
This document summarizes SSL/TLS, including what it is, how it works, and where it fits. SSL/TLS uses cryptography like key exchange, privacy, and message integrity to encrypt network connections above the transport layer, securing protocols like HTTP, SMTP, and POP3. The handshake protocol is described, including the client hello, server hello, and key exchange steps. Applications that use SSL/TLS are discussed, such as HTTPS for secure web browsing and mail protocols like SSMTP and SPOP3.SSL TLS Protocol
SSL TLS ProtocolDevang Badrakiya
╠²
SSL (Secure Socket Layer) and TLS (Transport Layer Security) are cryptographic protocols that ensure secure communication over networks by providing features like integrity, confidentiality, and authentication. The document outlines the SSL/TLS handshake process, including client-server parameter exchange and certificate verification, alongside certificate validation methods like CRL and OCSP. It emphasizes the importance of these protocols for secure web browsing, email, and other applications, detailing the steps involved in establishing a secure connection.SSl/TLS Analysis
SSl/TLS AnalysisDuduman Bogdan Vlad
╠²
The document provides an overview of the TLS/SSL security protocol. It discusses the history and design of TLS/SSL, including how it provides encryption between a web browser and server. It also covers public key encryption, certificate authorities, and how they prevent man-in-the-middle attacks on TLS/SSL connections. Finally, it introduces the Scyther tool for analyzing security protocols and provides an example of modeling a simplified TLS key transport protocol in Scyther.SSL-image
SSL-imageRajat Toshniwal
╠²
SSL handshake involves the following steps:
1. The client sends a client hello with SSL version, random data, session ID, and cipher details.
2. The server responds with a server hello containing SSL version, random data, session ID, cipher, and certificate. It may also request client authentication.
3. If requested, the client sends its certificate and generates a premaster secret to establish encrypted communication.Ssl (Secure Socket Layer)
Ssl (Secure Socket Layer)Sandeep Gupta
╠²
This document summarizes a seminar that covered Secure Socket Layer (SSL). It discussed SSL's overview, architecture, components, protocols for records, alerts, and handshakes. The record protocol handles fragmentation, compression, message authentication, and encryption. The handshake protocol negotiates security parameters and exchanges keys. SSL supports RSA-based and Diffie-Hellman key exchanges and uses message authentication codes. While SSL provided a major improvement in secure internet communication when it was developed, the document notes there is still room for strengthening protections against traffic analysis and improving the handshake message authentication method.The Fundamental of Secure Socket Layer (SSL)
The Fundamental of Secure Socket Layer (SSL)Vishal Kumar
╠²
The document provides an in-depth overview of Secure Socket Layer (SSL), including its function, position in the TCP/IP suite, and the handshake protocol phases. SSL, developed by Netscape in 1994, serves to secure communication between web browsers and servers by providing authentication and confidentiality. The presentation details each phase of the SSL handshake, including security capabilities, server authentication, client authentication, and finalization of the secure connection.SSL Layer
SSL LayerTrinh Phuc Tho
╠²
The Secure Socket Layer (SSL) protocol provides transport layer security to TCP applications like web browsers and servers for e-commerce. It offers security services like server authentication, data encryption, and optional client authentication. During the SSL handshake, the client authenticates the server via a certificate signed by a Certificate Authority. A master secret key is then generated and used to derive separate encryption and MAC keys to securely transmit data in both directions.Ip Sec Rev1
Ip Sec Rev1Ram Dutt Shukla
╠²
IPSec provides a framework for securing communications over IP networks by authenticating and encrypting IP packets. It includes protocols for authentication headers and encapsulating security payloads to provide integrity, authentication, and confidentiality. Key management protocols like Oakley and ISAKMP are used to securely establish security associations between communicating parties to protect data flows.Cryptography by Afroz haider mir
Cryptography by Afroz haider mirAFROZ MIR
╠²
SSL (Secure Sockets Layer) is a protocol that provides secure communication between a web browser and server. It provides authentication of the server and encryption of data for confidentiality. SSL was developed by Netscape in 1994 and is now implemented as TLS (Transport Layer Security). The SSL/TLS handshake establishes an encrypted connection in a four step process using messages like client hello, server hello, and server key exchange.SSL overview
SSL overviewTodd Benson (I.T. SPECIALIST and I.T. SECURITY)
╠²
The document provides an extensive overview of SSL and TLS protocols, emphasizing common vulnerabilities, necessary remediation strategies, and configuration best practices for secure communications. It discusses the evolution of SSL versions, detailing their security shortcomings, and highlights specific vulnerabilities such as weak cipher suites, TLS compression attacks (CRIME), and padding attacks (Lucky Thirteen). Additionally, it outlines testing recommendations and resources for ensuring proper SSL/TLS implementation and security measures.TLS: Past, Present, Future
TLS: Past, Present, Futurevpnmentor
╠²
The document outlines the history and evolution of Transport Layer Security (TLS), detailing its development from SSL by Netscape through various versions, including notable attacks and vulnerabilities. It discusses the current state of TLS and ongoing concerns related to password recovery attacks against the RC4 cipher, illustrating the implications for secure communication online. Furthermore, it emphasizes the importance of TLS in safeguarding digital transactions across numerous applications and devices.ssl
sslsjyuva
╠²
The Secure Sockets Layer (SSL) protocol establishes an encrypted connection between a client and server through authentication and exchange of encryption keys. It uses public key encryption during the handshake to authenticate the server and optionally the client, and to generate a shared secret. This premaster secret is then used to derive the master secret and session keys to encrypt all following communication within the SSL session.Secure Socket Layer
Secure Socket LayerAbhishek Gupta
╠²
Secure Socket Layer (SSL) was first proposed and used by Netscape to transmit sensitive data over the internet by encapsulating it in a session on top of the TCP layer. SSL aims to authenticate parties, ensure data integrity, and maintain data privacy. Certain websites can only be accessed through SSL-enabled client software. SSL establishes an association between a client and server by authenticating them and then exchanging and encrypting data using suitable algorithms to keep the information secret. SSL has two layers - the record protocol, which handles data encryption, integrity, and encapsulation, and several subprotocols like the alert, change cipher spec, and handshake protocols, which initiate and negotiate secure sessions.Introduction to SSL and How to Exploit & Secure
Introduction to SSL and How to Exploit & SecureBrian Ritchie
╠²
The document discusses SSL/TLS, how it works to securely transmit data between endpoints, and potential vulnerabilities. It provides an overview of SSL/TLS protocols and how data is encrypted and transmitted. It then outlines several common endpoint issues that can compromise SSL/TLS, such as inconsistent DNS configurations, self-signed certificates, incomplete certificates, and mixing plain text and encrypted sessions. Exploiting these issues allows man-in-the-middle attacks that can intercept and decrypt encrypted traffic.SSL Secure socket layer
SSL Secure socket layerAhmed Elnaggar
╠²
The document provides an overview of the Secure Sockets Layer (SSL) protocol. It discusses SSL's goals of providing confidentiality, integrity, and authentication for network communications. It describes the SSL handshake process, where the client and server authenticate each other and negotiate encryption parameters before transmitting application data. It also discusses SSL applications like securing web traffic and online payments. The document concludes that SSL is vital for web security and ensures user confidentiality and integrity.presentation2-151203145018-lva1-app6891.pdf
presentation2-151203145018-lva1-app6891.pdfGumanSingh10
╠²
The document discusses Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols for securing communications over a network. It explains that SSL uses certificates and keys to encrypt data between a client and server so only they can access it. It then describes the different versions of SSL, how SSL establishes encrypted connections, and provides diagrams of both server authentication and mutual/two-way authentication between client and server during SSL communications.Transport Layer Security (TLS)
Transport Layer Security (TLS)Arun Shukla
╠²
Transport Layer Security (TLS) is a protocol that ensures privacy and security between communicating applications on the internet, succeeding the older Secure Sockets Layer (SSL). The TLS protocol consists of a handshake mechanism for authentication and key exchange, and a record protocol for securing application data. It allows for encrypted communication by negotiating cipher suites and generating session keys, thereby preventing eavesdropping and tampering.More Related Content
What's hot (20)
Secure Socket Layer (SSL)
Secure Socket Layer (SSL)Samip jain
╠²
SSL (Secure Socket Layer) is an internet protocol ensuring secure communication between web browsers and servers, providing authentication and confidentiality. Developed by Netscape in 1994, it consists of multiple protocols including the handshake, record, change cipher, and alert protocols, facilitating secure data exchange. The latest version, TLS, evolved from SSL 3.0, incorporating enhancements for secure data transmission.Ssl in a nutshell
Ssl in a nutshellFrank Kelly
╠²
SSL provides encryption and authentication for secure communication over networks. It uses certificates signed by a certificate authority to authenticate servers and establish an encrypted connection. The SSL handshake process involves the client sending a pre-master secret encrypted with the server's public key, both sides then derive encryption keys to encrypt the connection. Debugging SSL issues may require using tools like tcpdump to monitor network traffic or adding debug flags to examine the SSL handshake.secure socket layer
secure socket layerAmar Shah
╠²
SSL and TLS are cryptographic protocols that provide secure communication on the internet. They use public/private key encryption to authenticate servers and establish encrypted connections. While similar, TLS is the standardized successor to SSL. Key differences include TLS using HMAC for integrity checking and having additional alert codes not found in SSL. Both protocols operate at the transport layer and provide data confidentiality, integrity, and server authentication.SSL/TLS 101
SSL/TLS 101Chul-Woong Yang
╠²
SSL/TLS 101 provides an overview of SSL and TLS including:
1) SSL and TLS are cryptographic protocols that provide security for internet communications like HTTPS and HTTP/2. They provide confidentiality, integrity, and authentication.
2) Key concepts of SSL/TLS include symmetric encryption for confidentiality, public key cryptography for key exchange, digital signatures for authentication, and X.509 certificates issued by certificate authorities to verify identities.
3) The document reviews the history and versions of SSL/TLS, how the core requirements of confidentiality, integrity and authentication are achieved, and references for further reading on implementing SSL/TLS.SSL
SSLDuy Do Phan
╠²
This document summarizes SSL/TLS, including what it is, how it works, and where it fits. SSL/TLS uses cryptography like key exchange, privacy, and message integrity to encrypt network connections above the transport layer, securing protocols like HTTP, SMTP, and POP3. The handshake protocol is described, including the client hello, server hello, and key exchange steps. Applications that use SSL/TLS are discussed, such as HTTPS for secure web browsing and mail protocols like SSMTP and SPOP3.SSL TLS Protocol
SSL TLS ProtocolDevang Badrakiya
╠²
SSL (Secure Socket Layer) and TLS (Transport Layer Security) are cryptographic protocols that ensure secure communication over networks by providing features like integrity, confidentiality, and authentication. The document outlines the SSL/TLS handshake process, including client-server parameter exchange and certificate verification, alongside certificate validation methods like CRL and OCSP. It emphasizes the importance of these protocols for secure web browsing, email, and other applications, detailing the steps involved in establishing a secure connection.SSl/TLS Analysis
SSl/TLS AnalysisDuduman Bogdan Vlad
╠²
The document provides an overview of the TLS/SSL security protocol. It discusses the history and design of TLS/SSL, including how it provides encryption between a web browser and server. It also covers public key encryption, certificate authorities, and how they prevent man-in-the-middle attacks on TLS/SSL connections. Finally, it introduces the Scyther tool for analyzing security protocols and provides an example of modeling a simplified TLS key transport protocol in Scyther.SSL-image
SSL-imageRajat Toshniwal
╠²
SSL handshake involves the following steps:
1. The client sends a client hello with SSL version, random data, session ID, and cipher details.
2. The server responds with a server hello containing SSL version, random data, session ID, cipher, and certificate. It may also request client authentication.
3. If requested, the client sends its certificate and generates a premaster secret to establish encrypted communication.Ssl (Secure Socket Layer)
Ssl (Secure Socket Layer)Sandeep Gupta
╠²
This document summarizes a seminar that covered Secure Socket Layer (SSL). It discussed SSL's overview, architecture, components, protocols for records, alerts, and handshakes. The record protocol handles fragmentation, compression, message authentication, and encryption. The handshake protocol negotiates security parameters and exchanges keys. SSL supports RSA-based and Diffie-Hellman key exchanges and uses message authentication codes. While SSL provided a major improvement in secure internet communication when it was developed, the document notes there is still room for strengthening protections against traffic analysis and improving the handshake message authentication method.The Fundamental of Secure Socket Layer (SSL)
The Fundamental of Secure Socket Layer (SSL)Vishal Kumar
╠²
The document provides an in-depth overview of Secure Socket Layer (SSL), including its function, position in the TCP/IP suite, and the handshake protocol phases. SSL, developed by Netscape in 1994, serves to secure communication between web browsers and servers by providing authentication and confidentiality. The presentation details each phase of the SSL handshake, including security capabilities, server authentication, client authentication, and finalization of the secure connection.SSL Layer
SSL LayerTrinh Phuc Tho
╠²
The Secure Socket Layer (SSL) protocol provides transport layer security to TCP applications like web browsers and servers for e-commerce. It offers security services like server authentication, data encryption, and optional client authentication. During the SSL handshake, the client authenticates the server via a certificate signed by a Certificate Authority. A master secret key is then generated and used to derive separate encryption and MAC keys to securely transmit data in both directions.Ip Sec Rev1
Ip Sec Rev1Ram Dutt Shukla
╠²
IPSec provides a framework for securing communications over IP networks by authenticating and encrypting IP packets. It includes protocols for authentication headers and encapsulating security payloads to provide integrity, authentication, and confidentiality. Key management protocols like Oakley and ISAKMP are used to securely establish security associations between communicating parties to protect data flows.Cryptography by Afroz haider mir
Cryptography by Afroz haider mirAFROZ MIR
╠²
SSL (Secure Sockets Layer) is a protocol that provides secure communication between a web browser and server. It provides authentication of the server and encryption of data for confidentiality. SSL was developed by Netscape in 1994 and is now implemented as TLS (Transport Layer Security). The SSL/TLS handshake establishes an encrypted connection in a four step process using messages like client hello, server hello, and server key exchange.SSL overview
SSL overviewTodd Benson (I.T. SPECIALIST and I.T. SECURITY)
╠²
The document provides an extensive overview of SSL and TLS protocols, emphasizing common vulnerabilities, necessary remediation strategies, and configuration best practices for secure communications. It discusses the evolution of SSL versions, detailing their security shortcomings, and highlights specific vulnerabilities such as weak cipher suites, TLS compression attacks (CRIME), and padding attacks (Lucky Thirteen). Additionally, it outlines testing recommendations and resources for ensuring proper SSL/TLS implementation and security measures.TLS: Past, Present, Future
TLS: Past, Present, Futurevpnmentor
╠²
The document outlines the history and evolution of Transport Layer Security (TLS), detailing its development from SSL by Netscape through various versions, including notable attacks and vulnerabilities. It discusses the current state of TLS and ongoing concerns related to password recovery attacks against the RC4 cipher, illustrating the implications for secure communication online. Furthermore, it emphasizes the importance of TLS in safeguarding digital transactions across numerous applications and devices.ssl
sslsjyuva
╠²
The Secure Sockets Layer (SSL) protocol establishes an encrypted connection between a client and server through authentication and exchange of encryption keys. It uses public key encryption during the handshake to authenticate the server and optionally the client, and to generate a shared secret. This premaster secret is then used to derive the master secret and session keys to encrypt all following communication within the SSL session.Secure Socket Layer
Secure Socket LayerAbhishek Gupta
╠²
Secure Socket Layer (SSL) was first proposed and used by Netscape to transmit sensitive data over the internet by encapsulating it in a session on top of the TCP layer. SSL aims to authenticate parties, ensure data integrity, and maintain data privacy. Certain websites can only be accessed through SSL-enabled client software. SSL establishes an association between a client and server by authenticating them and then exchanging and encrypting data using suitable algorithms to keep the information secret. SSL has two layers - the record protocol, which handles data encryption, integrity, and encapsulation, and several subprotocols like the alert, change cipher spec, and handshake protocols, which initiate and negotiate secure sessions.Introduction to SSL and How to Exploit & Secure
Introduction to SSL and How to Exploit & SecureBrian Ritchie
╠²
The document discusses SSL/TLS, how it works to securely transmit data between endpoints, and potential vulnerabilities. It provides an overview of SSL/TLS protocols and how data is encrypted and transmitted. It then outlines several common endpoint issues that can compromise SSL/TLS, such as inconsistent DNS configurations, self-signed certificates, incomplete certificates, and mixing plain text and encrypted sessions. Exploiting these issues allows man-in-the-middle attacks that can intercept and decrypt encrypted traffic.SSL Secure socket layer
SSL Secure socket layerAhmed Elnaggar
╠²
The document provides an overview of the Secure Sockets Layer (SSL) protocol. It discusses SSL's goals of providing confidentiality, integrity, and authentication for network communications. It describes the SSL handshake process, where the client and server authenticate each other and negotiate encryption parameters before transmitting application data. It also discusses SSL applications like securing web traffic and online payments. The document concludes that SSL is vital for web security and ensures user confidentiality and integrity.Similar to SSL Demystified (20)
presentation2-151203145018-lva1-app6891.pdf
presentation2-151203145018-lva1-app6891.pdfGumanSingh10
╠²
The document discusses Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols for securing communications over a network. It explains that SSL uses certificates and keys to encrypt data between a client and server so only they can access it. It then describes the different versions of SSL, how SSL establishes encrypted connections, and provides diagrams of both server authentication and mutual/two-way authentication between client and server during SSL communications.Transport Layer Security (TLS)
Transport Layer Security (TLS)Arun Shukla
╠²
Transport Layer Security (TLS) is a protocol that ensures privacy and security between communicating applications on the internet, succeeding the older Secure Sockets Layer (SSL). The TLS protocol consists of a handshake mechanism for authentication and key exchange, and a record protocol for securing application data. It allows for encrypted communication by negotiating cipher suites and generating session keys, thereby preventing eavesdropping and tampering.What is SSL ? The Secure Sockets Layer (SSL) Protocol
What is SSL ? The Secure Sockets Layer (SSL) ProtocolMohammed Adam
╠²
SSL is a protocol that allows clients and servers to securely communicate over the internet. It uses public-key encryption to authenticate servers, optionally authenticate clients, and establish an encrypted connection to securely transmit data. The SSL handshake allows the client and server to negotiate encryption parameters to generate shared secrets and session keys, which are then used to encrypt all further communication during the SSL session. Common implementations of SSL include OpenSSL and Apache-SSL.Introduction to Secure Sockets Layer
Introduction to Secure Sockets LayerNascenia IT
╠²
The document discusses the Secure Sockets Layer (SSL) technology, detailing its importance for establishing encrypted links between web servers and browsers. It explains the SSL protocol phases, working mechanisms, and the evolution of SSL versions leading to the Transport Layer Security (TLS). Additionally, it addresses various encryption algorithms and the significance of certification authorities for secure online communication.SIP over TLS
SIP over TLSHossein Yavari
╠²
This document discusses SIP over TLS. It describes how SIP signaling can be secured using TLS instead of UDP or TCP. The TLS handshake process is explained in detail including the messages exchanged between the client and server. It also discusses how media can be encrypted using SRTP and the different key management protocols that can be used like SDES, DTLS, and ZRTP. Sample packet captures of SIP over TLS calls are also provided.cryptography and network security thid.ppt
cryptography and network security thid.pptubaidullah75790
╠²
The document provides an overview of web security, focusing on the vulnerabilities of the internet and the need for added security mechanisms like SSL/TLS. It explains the SSL/TLS architecture, the handshake protocol for authentication and key exchange, and the TLS record protocol for securing application data. Additionally, it highlights the transition from SSL to TLS and the importance of ensuring privacy between communicating applications.CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level Security
CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level SecurityJyothishmathi Institute of Technology and Science Karimnagar
╠²
The document discusses transport-level security, focusing on protocols like TLS and SSL, outlining their purpose in ensuring privacy and data integrity during internet communication. It details the TLS handshake and record protocols, highlighting how they authenticate parties and encrypt messages. Additionally, the document covers wireless network security concerns, vulnerabilities, and standards like IEEE 802.11i, recommending improvements for secure wireless communications.Web Security
Web SecurityRam Dutt Shukla
╠²
SSL and TLS provide secure communication over the internet using encryption. SSL uses public key encryption to establish a secure connection and exchange keys to encrypt data sent between a client and server. It defines sessions which allow parameters like encryption algorithms to be shared for multiple connections. TLS is an updated version of SSL that uses similar record and handshake protocols. SET is an open standard that uses digital certificates and dual signatures to securely conduct credit card transactions over the internet between cardholders, merchants, issuers and payment gateways.Ssl (Secure Sockets Layer)
Ssl (Secure Sockets Layer)Asad Ali
╠²
The document provides an overview of the Secure Sockets Layer (SSL) protocol, detailing its purpose, functionality, and implementation methods. It explains how SSL facilitates secure communication between clients and servers through authentication and encryption via the SSL record and handshake protocols. Additionally, it mentions various implementations of SSL, such as OpenSSL and Apache-SSL.ngrubksgj.pptdagji;jgisofjapfjagiahguhkg
ngrubksgj.pptdagji;jgisofjapfjagiahguhkgjayewi2029
╠²
The document discusses the Secure Sockets Layer (SSL), detailing its purpose of managing encryption for online communications and its implementation in web browsers and servers. It outlines key protocols involved, including the record, alert, and handshake protocols, emphasizing SSL's role in ensuring data confidentiality, integrity, and authentication. The document also touches on the Secure Electronic Transaction (SET) protocol, which further enhances transaction security through the use of both symmetric and asymmetric encryption techniques.SSL/TLS Handshake
SSL/TLS HandshakeArpit Agarwal
╠²
SSL/TLS are cryptographic protocols used to secure communications over a computer network. They employ both symmetric and asymmetric encryption methods, with a handshake process to establish secure connections. The document also discusses vulnerabilities such as the POODLE attack and includes details on various encryption algorithms and their implementations.SSL/TLS Introduction with Practical Examples Including Wireshark Captures
SSL/TLS Introduction with Practical Examples Including Wireshark CapturesJaroslavChmurny
╠²
The document provides a comprehensive overview of SSL/TLS protocols and public key infrastructure (PKI), covering the fundamentals of symmetric and asymmetric cryptography, digital signatures, and certificate management. It includes practical examples and hints related to cryptographic techniques and emphasizes the importance of certificate chains and trust stores for secure communication. Although it touches on advanced topics like perfect forward secrecy and revocation mechanisms, it intentionally excludes detailed historical context and cryptographic mathematics.SSL And TLS
SSL And TLS Ghanshyam Patel
╠²
SSL and TLS provide end-to-end security for applications using TCP. They operate at the transport layer and provide services like data encryption, message integrity, and client/server authentication. The key components are the handshake protocol for negotiating encryption parameters and exchanging keys, the record protocol for fragmenting and encrypting application data, and alert and change cipher spec protocols for signaling errors and key changes. Common algorithms include RSA and Diffie-Hellman for key exchange, RC4, 3DES and AES for encryption, and MD5 or SHA for hashing. Sessions define a connection's cryptographic settings while connections are the actual data streams.Ssl
SslAnandraj Kulkarni
╠²
This document provides an overview of SSL (Secure Sockets Layer) technology, including why it is used, how it works, and common troubleshooting tips. SSL addresses issues with communicating securely over the internet such as verifying identities, preventing eavesdropping, and modifying data. It uses public key cryptography where each party has a public and private key to encrypt data. The SSL handshake process negotiates encryption between client and server before transmitting encrypted data. Common SSL issues involve certificate validation errors, which can be debugged using stack traces and tools like Keytool and OpenSSL.Wireshark lab ssl v7 solution
Wireshark lab ssl v7 solutionUnited International University
╠²
The document outlines a Wireshark lab focused on analyzing SSL records through various Ethernet frames. It details the types and counts of SSL records exchanged between client and server, including expansion of certain records like Client Hello and Server Hello, and discusses aspects such as ciphers, nonces, and session IDs involved in the SSL handshake process. Additionally, it notes the transition from SSLv2 to SSLv3 during the handshake, highlighting variations in the process during session resumes.How does TLS work?
How does TLS work?Hyeonsu Lee
╠²
The document explains Transport Layer Security (TLS) and its predecessor, SSL, emphasizing their roles in secure communications over various protocols, including HTTP. It details the TLS handshake process, which involves client-server interactions for establishing secure connections, and the function of TLS certificates, including the significance of digital signatures and trusted authorities. Real-world examples of security threats such as Man-in-the-Middle (MITM) attacks and government censorship are also discussed.Certificate pinning in android applications
Certificate pinning in android applicationsArash Ramez
╠²
Certificate pinning is a security mechanism where an app specifies certificates from trusted authorities and only accepts connections signed by those certificates. This prevents man-in-the-middle attacks. The document discusses implementing certificate pinning in Android apps by configuring the network security configuration file or using third party libraries like OkHttp that have CertificatePinner classes to restrict which certificates an app will accept. It also describes how to retrieve a server's public key hashes to include in the pinning configuration.Indianapolis mule soft_meetup_30_jan_2021 (1)
Indianapolis mule soft_meetup_30_jan_2021 (1)ikram_ahamed
╠²
This document outlines an upcoming meetup organized by the Indianapolis MuleSoft Meetup Group on implementing one-way and two-way SSL with MuleSoft. The meetup will include presentations by Ikram Mohamed and Jitendra Bafna on setting up one-way and two-way SSL, including generating certificates and keystores. It will also include a live demonstration of implementing one-way and two-way SSL as well as HTTPS proxying with MuleSoft. References and a trivia quiz will conclude the meetup.Secure payment systems
Secure payment systemsAbdulaziz Mohd
╠²
The document discusses secure payment systems for electronic commerce. It outlines why security is important on the internet due to risks of snooping, alteration of information, and theft. It then covers various technologies used for secure transactions, including public key cryptography, SSL, digital signatures, and digital certificates. Finally, it discusses requirements for internet-based payments and different types of electronic payment systems like credit cards, electronic checks, anonymous payments and micropayments.Webinar SSL English
Webinar SSL English│¦│¦│ó247┬«
╠²
The document discusses SSL/TLS protocols, their purposes, history, and the role of SSL certificates in web application security. It outlines the process for TLS connections, including the steps of negotiation and encryption, as well as different certificate validation levels and their significance. Additionally, it highlights the impact and optimization of TLS on performance and how tools like HAProxy can be utilized for various deployment modes.CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level Security
CRYPTOGRAPHY AND NETWORK SECURITY- Transport-level SecurityJyothishmathi Institute of Technology and Science Karimnagar
╠²
Ad
Recently uploaded (20)
MATERIAL SCIENCE LECTURE NOTES FOR DIPLOMA STUDENTS
MATERIAL SCIENCE LECTURE NOTES FOR DIPLOMA STUDENTSSAMEER VISHWAKARMA
╠²
This PPT contains notes for taking lecture at diploma level.Data Structures Module 3 Binary Trees Binary Search Trees Tree Traversals AVL...
Data Structures Module 3 Binary Trees Binary Search Trees Tree Traversals AVL...resming1
╠²
This covers binary trees, binary search trees, BST insertion, deletion, tree traversals - inorder, preorder, postorder, AVL trees, AVL tree insertion, deletion, BTrees - insertion, deletion, hash tables etc.International Journal of Advanced Information Technology (IJAIT)
International Journal of Advanced Information Technology (IJAIT)ijait
╠²
International journal of advanced Information technology (IJAIT) is a bi monthly open access peer-
reviewed journal, will act as a major forum for the presentation of innovative ideas, approaches,
developments, and research projects in the area advanced information technology applications and
services. It will also serve to facilitate the exchange of information between researchers and industry
professionals to discuss the latest issues and advancement in the area of advanced IT. Core areas of
advanced IT and multi-disciplinary and its applications will be covered during the conferences.ž¬┘éž▒┘Ŗž▒ ž╣┘å ž¦┘䞬žŁ┘ä┘Ŗ┘ä ž¦┘äž»┘Ŗ┘垦┘ģ┘Ŗ┘ā┘Ŗ ┘䞬ž»┘ü┘é ž¦┘ä┘ć┘łž¦žĪ žŁ┘ł┘ä ž¼┘垦žŁ.pdf
ž¬┘éž▒┘Ŗž▒ ž╣┘å ž¦┘䞬žŁ┘ä┘Ŗ┘ä ž¦┘äž»┘Ŗ┘垦┘ģ┘Ŗ┘ā┘Ŗ ┘䞬ž»┘ü┘é ž¦┘ä┘ć┘łž¦žĪ žŁ┘ł┘ä ž¼┘垦žŁ.pdf┘ģžŁ┘ģž» ┘鞥žĄ ┘üž¬┘łž¬ž®
╠²
ž¬┘éž▒┘Ŗž▒ ž╣┘å ž¦┘䞬žŁ┘ä┘Ŗ┘ä ž¦┘äž»┘Ŗ┘垦┘ģ┘Ŗ┘ā┘Ŗ ┘䞬ž»┘ü┘é ž¦┘ä┘ć┘łž¦žĪ žŁ┘ł┘ä ž¼┘垦žŁ ┘ģž▒┘łžŁ┘ć ž▒┘ŖžŁ┘Ŗ┘ć Call For Papers - 17th International Conference on Wireless & Mobile Networks...
Call For Papers - 17th International Conference on Wireless & Mobile Networks...hosseinihamid192023
╠²
17th International Conference on Wireless & Mobile Networks (WiMoNe 2025) will provide
an excellent international forum for sharing knowledge and results in theory, methodology and
applications of Wireless & Mobile computing Environment. Current information age is witnessing
a dramatic use of digital and electronic devices in the workplace and beyond. Wireless, Mobile
Networks & its applications had received a significant and sustained research interest in terms of
designing and deploying large scale and high performance computational applications in real life.
The aim of the conference is to provide a platform to the researchers and practitioners from both
academia as well as industry to meet and share cutting-edge development in the field.Rapid Prototyping for XR: Lecture 6 - AI for Prototyping and Research Directi...
Rapid Prototyping for XR: Lecture 6 - AI for Prototyping and Research Directi...Mark Billinghurst
╠²
This is lecture 6 in the course on Rapid Prototyping for XR, taught on June 13th, 2025 by Mark Billinghurst. This lecture was about using AI for Prototyping and Research Directions. Rapid Prototyping for XR: Lecture 1 Introduction to Prototyping
Rapid Prototyping for XR: Lecture 1 Introduction to PrototypingMark Billinghurst
╠²
Lecture 1 of a course on Rapid Prototyping for XR taught by Mark Billinghurst at Oulu University on June 9th, 2025. This lecture presents an Introduction to Prototyping. Rapid Prototyping for XR: Lecture 5 - Cross Platform Development
Rapid Prototyping for XR: Lecture 5 - Cross Platform DevelopmentMark Billinghurst
╠²
This is lecture 5 in the course about Rapid Prototyping for XR, taught by Mark Billinghurst. This lecture is about Cross Platform Development.Proposal for folders structure division in projects.pdf
Proposal for folders structure division in projects.pdfMohamed Ahmed
╠²
Proposal for folders structure division in projectsRapid Prototyping for XR: Lecture 4 - High Level Prototyping.
Rapid Prototyping for XR: Lecture 4 - High Level Prototyping.Mark Billinghurst
╠²
This is lecture 4 in the course on Rapid Prototyping for XR, taught by Mark Billinghurst on June 11th, 2025. This lecture is about High Level Prototyping.Stability of IBR Dominated Grids - IEEE PEDG 2025 - short.pptx
Stability of IBR Dominated Grids - IEEE PEDG 2025 - short.pptxssuser307730
╠²
║▌║▌▀Żs from IEEE PEDG 2025 Conference in Nanajing. Addresses need for re-examining grid stability when using large numbers of inverter-based resources.Complete University of Calculus :: 2nd edition
Complete University of Calculus :: 2nd editionShabista Imam
╠²
Master the language of change with the Complete Guidance Book of CalculusŌĆöyour comprehensive resource for understanding the core concepts and applications of differential and integral calculus. Designed for high school, college, and self-study learners, this book takes a clear, intuitive approach to a subject often considered challenging.Rapid Prototyping for XR: Lecture 2 - Low Fidelity Prototyping.
Rapid Prototyping for XR: Lecture 2 - Low Fidelity Prototyping.Mark Billinghurst
╠²
This is lecture 2 on the Rapid Prototyping for XR course taught by Mark Billingurst on June 10th 2025. This lecture is about Low Fidelity Prototyping.Modern multi-proposer consensus implementations
Modern multi-proposer consensus implementationsFran├¦ois Garillot
╠²
Multi-proposer consensus protocols let multiple validators propose blocks in parallel, breaking the single-leader throughput bottleneck of classic designs. Yet the modern multi-proposer consensus implementation has grown a lot since HotStuff. THisworkshop will explore the implementation details of recent advances ŌĆō DAG-based approaches like Narwhal and SuiŌĆÖs Mysticeti ŌĆō and reveal how implementation details translate to real-world performance gains. We focus on the nitty-gritty: how network communication patterns and data handling affect throughput and latency. New techniques such as Turbine-like block propagation (inspired by SolanaŌĆÖs erasure-coded broadcast) and lazy push gossip broadcasting dramatically cut communication overhead. These optimizations arenŌĆÖt just theoretical ŌĆō they enable modern blockchains to process over 100,000 transactions per second with finality in mere millisecondsŌĆŗ redefining what is possible in decentralized systems.
How to Un-Obsolete Your Legacy Keypad Design
How to Un-Obsolete Your Legacy Keypad DesignEpec Engineered Technologies
╠²
For any number of circumstances, obsolescence risk is ever present in the electronics industry. This is especially true for human-to-machine interface hardware, such as keypads, touchscreens, front panels, bezels, etc. This industry is known for its high mix and low-volume builds, critical design requirements, and high costs to requalify hardware. Because of these reasons, many programs will face end-of-life challenges both at the component level as well as at the supplier level.
Redesigns and qualifications can take months or even years, so proactively managing this risk is the best way to deter this. If an LED is obsolete or a switch vendor has gone out of business, there are options to proceed.
In this webinar, we cover options to redesign and reverse engineer legacy keypad and touchscreen designs.
For more information on our HMI solutions, visit https://www.epectec.com/user-interfaces.
Tally.ERP 9 at a Glance.book - Tally Solutions .pdf
Tally.ERP 9 at a Glance.book - Tally Solutions .pdfShabista Imam
╠²
Tally.ERP 9 at a Glance.book, a fully completed guidance to learn tally erp 9.0ž¬┘éž▒┘Ŗž▒ ž╣┘å ž¦┘䞬žŁ┘ä┘Ŗ┘ä ž¦┘äž»┘Ŗ┘垦┘ģ┘Ŗ┘ā┘Ŗ ┘䞬ž»┘ü┘é ž¦┘ä┘ć┘łž¦žĪ žŁ┘ł┘ä ž¼┘垦žŁ.pdf
ž¬┘éž▒┘Ŗž▒ ž╣┘å ž¦┘䞬žŁ┘ä┘Ŗ┘ä ž¦┘äž»┘Ŗ┘垦┘ģ┘Ŗ┘ā┘Ŗ ┘䞬ž»┘ü┘é ž¦┘ä┘ć┘łž¦žĪ žŁ┘ł┘ä ž¼┘垦žŁ.pdf┘ģžŁ┘ģž» ┘鞥žĄ ┘üž¬┘łž¬ž®
╠²
Call For Papers - 17th International Conference on Wireless & Mobile Networks...
Call For Papers - 17th International Conference on Wireless & Mobile Networks...hosseinihamid192023
╠²
Ad
SSL Demystified
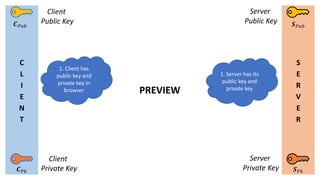
- 2. C L I E N T S E R V E R Øæ¬ ØæāØæś Øæ¬ ØæāØæóØæÅ Øæ║ ØæāØæóØæÅ Øæ║ ØæāØæś Client Public Key Client Private Key Server Public Key Server Private Key PREVIEW 1. Client has public key and private key in browser 1. Server has its public key and private key
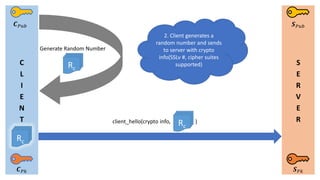
- 3. C L I E N T S E R V E R Øæ¬ ØæāØæś Øæ¬ ØæāØæóØæÅ Øæ║ ØæāØæóØæÅ Øæ║ ØæāØæś Generate Random Number Rc Rc client_hello(crypto info, )Rc 2. Client generates a random number and sends to server with crypto info(SSLv #, cipher suites supported)
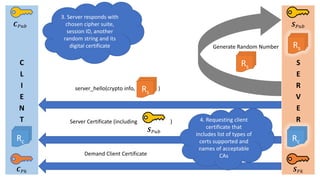
- 4. C L I E N T S E R V E R Øæ¬ ØæāØæś Øæ¬ ØæāØæóØæÅ Øæ║ ØæāØæóØæÅ Øæ║ ØæāØæś Generate Random Number Rs RcRc Rs Demand Client Certificate Server Certificate (including ) Øæ║ ØæāØæóØæÅ server_hello(crypto info, )Rs 3. Server responds with chosen cipher suite, session ID, another random string and its digital certificate 4. Requesting client certificate that includes list of types of certs supported and names of acceptable CAs
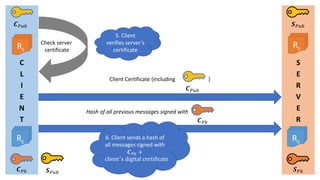
- 5. C L I E N T S E R V E R Øæ¬ ØæāØæś Øæ║ ØæāØæś Check server certificate Rc Rc Rs Øæ¬ ØæāØæóØæÅ Øæ║ ØæāØæóØæÅ Rs Client Certificate (including ) Øæ¬ ØæāØæóØæÅ Hash of all previous messages signed with Øæ¬ ØæāØæś Øæ║ ØæāØæóØæÅ 5. Client verifies serverŌĆÖs certificate 6. Client sends a hash of all messages signed with Øæ¬ ØæāØæś + clientŌĆ▓s digital certificate
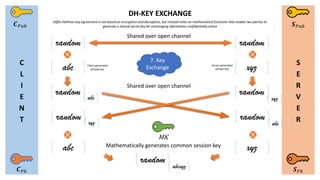
- 6. C L I E N T S E R V E R Øæ¬ ØæāØæś Øæ¬ ØæāØæóØæÅ Øæ║ ØæāØæóØæÅ Øæ║ ØæāØæś DH-KEY EXCHANGE random random abc xyz random abc random xyz random xyz random abc abc xyz random abcxyz Shared over open channel Shared over open channel Mathematically generates common session key Diffie-Hellman key agreement is not based on encryption and decryption, but instead relies on mathematical functions that enable two parties to generate a shared secret key for exchanging information confidentially online Client generated private key Server generated private key MK 7. Key Exchange
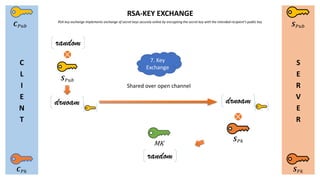
- 7. C L I E N T S E R V E R Øæ¬ ØæāØæś Øæ¬ ØæāØæóØæÅ Øæ║ ØæāØæóØæÅ Øæ║ ØæāØæś RSA-KEY EXCHANGE random Shared over open channel RSA key exchange implements exchange of secret keys securely online by encrypting the secret key with the intended recipient's public key Øæ║ ØæāØæóØæÅ drnoam drnoam Øæ║ ØæāØæś random MK 7. Key Exchange
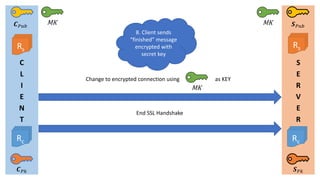
- 8. C L I E N T S E R V E R Øæ¬ ØæāØæś Øæ║ ØæāØæś Change to encrypted connection using as KEY MK End SSL Handshake Rc Rc Rs Øæ¬ ØæāØæóØæÅ Øæ║ ØæāØæóØæÅ Rs MK MK 8. Client sends ŌĆ£finishedŌĆØ message encrypted with secret key
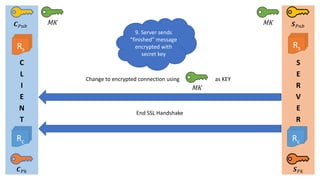
- 9. C L I E N T S E R V E R Øæ¬ ØæāØæś Øæ║ ØæāØæś Change to encrypted connection using as KEY MK End SSL Handshake Rc Rc Rs Øæ¬ ØæāØæóØæÅ Øæ║ ØæāØæóØæÅ Rs 9. Server sends ŌĆ£finishedŌĆØ message encrypted with secret key MK MK
- 11. C L I E N T S E R V E R Øæ¬ ØæāØæś Øæ¬ ØæāØæóØæÅ Øæ║ ØæāØæóØæÅ Øæ║ ØæāØæś CONFIDENTIALITY During the SSL handshake, the SSL client and SSL server agree on encryption algorithm and a shared secret key to be used for one session only. All messages transmitted between the SSL client and SSL server are encrypted using that algorithm and key, ensuring that the message remains private even if it is intercepted Because SSL uses asymmetric encryption when transporting the shared secret key, there is no key distribution problem with SSL SSL provides data integrity check by calculating the message digest. A message can be digitally signed by a message exit at the sending end of a channel. The digital signature can then be checked by a message exit at the receiving end of a channel to detect whether the message has been deliberately modified. Use of SSL or TLS does ensure data integrity, provided that the CipherSpec in your channel definition uses a hash algorithm. INTEGRITY
- 13. C L I E N T S E R V E R Øæ¬ ØæāØæś Øæ¬ ØæāØæóØæÅ Øæ║ ØæāØæóØæÅ Øæ║ ØæāØæś For SERVER authentication, the client uses the serverŌĆÖs PUBLIC KEY to ENCRYPT the data that is used to compute the secret key. The server can generate the secret key only if it can decrypt that data with the correct PRIVATE KEY. For CLIENT authentication, the server uses the PUBLIC KEY in the client certificate to VERIFY the data the client sends during of the handshake. The exchange of finished messages that are encrypted with the secret key confirms that authentication is complete. If any of the authentication steps fail, the handshake fails and the session terminates. AUTHENTICATION ŌĆó The digital signature is checked ŌĆó The certificate chain is checked ŌĆó The expiry and activation dates and the validity period are checked ŌĆó The revocation status of the certificate is checked CERTIFICATE VERIFICATION
- 15. The End
