Hypothetical machine and instruction flow scenarios
Download as PPTX, PDF2 likes6,014 views
Hypothetical Machine. Components of hypothetical machine. Example of hypothetical machine. Instruction Flow Scenarios. Data flow fetch cycle. Data flow indirect cycle. Data flow interrupt cycle. Instruction cycle state diagram.
1 of 14
Downloaded 15 times













Recommended
Context switching



Context switchingDarakhshanNayyab
?
Context switching allows a system to switch between processes by saving the state of the current process and loading the saved state for a new process. This allows multiple processes to share resources like the CPU and gives the appearance of parallel processing. Context switching has advantages like enabling multitasking but also has disadvantages like requiring time for the switching process itself.Presentation on risc pipeline



Presentation on risc pipelineArijit Chakraborty
?
The document summarizes the RISC pipeline architecture. It discusses the five stages of the classic RISC pipeline: instruction fetch, instruction decode, execute, memory access, and writeback. Each stage is involved in processing one instruction at a time through the pipeline. The instruction fetch stage retrieves instructions from the instruction cache. The decode stage decodes the instruction and computes branch targets. The execute stage performs arithmetic and logical operations. The memory access stage handles data memory access. Finally, the writeback stage writes results back to registers. The document also discusses hazards like structural, data, and control hazards that can occur in pipelines.Harvard vs Von Neumann Architecture



Harvard vs Von Neumann ArchitectureProject Student
?
Computer Science - Harvard and Von Neumann Architecture
The aspects of both architectures are highlighted through the presentation along with their advantages and disadvantages.Computer architecture



Computer architectureRishabha Garg
?
This document provides an overview of the history and development of computer architecture. It begins with some of the earliest computing devices like the abacus and ENIAC, the first general-purpose electronic digital computer. It then discusses the evolution of CPU and memory architecture from vacuum tubes to integrated circuits and microprocessors. The document outlines different bus architectures like ISA, EISA, MCA, PCI, and AGP that were used to connect components. It also reviews memory hierarchies and I/O interfaces like IDE, SCSI, serial ports, USB, and parallel ports. The presentation aims to trace the progression of computer hardware technology over time.Chapter 13 - I/O Systems



Chapter 13 - I/O SystemsWayne Jones Jnr
?
I/O Hardware
Application I/O Interface
Kernel I/O Subsystem
Transforming I/O Requests to Hardware Operations
Streams
PerformanceMemory Organization



Memory OrganizationKamal Acharya
?
This slide contain the introduction to memory , hierarchy, types, virtual memory,associative memory and cache memory.Control Units : Microprogrammed and Hardwired:control unit



Control Units : Microprogrammed and Hardwired:control unitabdosaidgkv
?
The document discusses control units in CPUs. There are two main methods for implementing control units: hardwired and microprogrammed. A hardwired control unit generates control signals through circuitry using logic gates, while a microprogrammed control unit generates control signals by executing a stored microprogram. Overall, hardwired control units are faster but less flexible, while microprogrammed control units are slower but more flexible and modifiable.Computer Organization and Architecture.pptx



Computer Organization and Architecture.pptxAshokRachapalli1
?
Computer organization and architecture are related but distinct fields. Computer organization deals with how hardware components are interconnected and work together to realize the specifications set by computer architecture. Computer architecture determines attributes like instruction sets, memory organization, and input/output mechanisms. Studying computer organization and architecture is important for understanding how computers work at both the hardware and software levels. It provides knowledge about system design, components, and performance.Cpu organisation



Cpu organisationEr Sangita Vishwakarma
?
The CPU acts as the computer's brain and carries out instructions from programs. It has two main components: the control unit, which selects and coordinates instruction execution, and the arithmetic logic unit, which performs calculations. Registers temporarily store data during instruction processing, including special purpose registers like the program counter, memory address, and accumulator registers. The CPU communicates with main memory, where files and applications are stored, and executes instructions through a multi-step process controlled by the control unit.Computer registers



Computer registersJatin Grover
?
A register is a group of flip-flops that can each store one bit of information. A processor uses registers to hold instructions, addresses, and data for manipulating information. The document lists several common computer registers - the Data Register stores 16-bit operands from memory, the Address Register holds 12-bit memory addresses, the Accumulator is a general purpose 16-bit processing register, and the Program Counter contains the 12-bit address of the next instruction. Temporary and input/output registers are also used to store intermediate data and user input/output respectively.operating system lecture notes



operating system lecture notesAVC College of Engineering
?
This document provides course material for the subject of Operating Systems for 4th semester B.E. Computer Science Engineering students at A.V.C. College of Engineering. It includes information on the name and designation of the faculty teaching the course, the academic year, curriculum regulations, 5 units that make up the course content, textbook and reference details. The course aims to cover key topics in operating systems including processes, process scheduling, storage management, file systems and I/O systems.Processor Organization and Architecture



Processor Organization and ArchitectureVinit Raut
?
The document discusses processor organization and architecture. It covers the Von Neumann model, which stores both program instructions and data in the same memory. The Institute for Advanced Study (IAS) computer is described as the first stored-program computer, designed by John von Neumann to overcome limitations of previous computers like the ENIAC. The document also covers the Harvard architecture, instruction formats, register organization including general purpose, address, and status registers, and issues in instruction format design like instruction length and allocation of bits.IO Techniques in Computer Organization



IO Techniques in Computer OrganizationOm Prakash
?
The document discusses three different I/O techniques:
1. Programmed I/O - The CPU controls the entire I/O process and must periodically check device status, wasting CPU time.
2. Interrupt-driven I/O - The CPU issues a command and is freed up while the device operates. The device then interrupts the CPU when ready.
3. Direct memory access (DMA) - Allows devices to communicate directly with memory without involving the CPU, using a DMA controller. This overcomes CPU waiting and avoids repeated status checks. Arbitration in computer organization 



Arbitration in computer organization Amit kashyap
?
Buses are shared communication links that connect processors, memory, and input/output (I/O) devices. They allow new devices to be easily added and devices to be moved between systems using the same bus standard. However, buses can create communication bottlenecks and their maximum speed is limited by length and number of devices. Buses use control lines to signal requests/acknowledgments and indicate data type, while data lines carry addresses, data, and commands between devices. Devices controlling the bus are masters, while devices responding are slaves.Shared-Memory Multiprocessors



Shared-Memory MultiprocessorsSalvatore La Bua
?
The document discusses different types of parallel computer architectures, including shared-memory multiprocessors. It describes taxonomy of parallel computers including SISD, SIMD, MISD, and MIMD models. For shared-memory multiprocessors, it outlines consistency models including strict, sequential, processor, weak and release consistency. It also discusses UMA and NUMA architectures, cache coherence protocols like MESI, and examples of multiprocessors using crossbar switches or multistage networks.Data transfer and manipulation



Data transfer and manipulationSanjeev Patel
?
1) Data transfer instructions move data between processor registers and memory without changing the data. Common instructions include load, store, move, exchange, input, and output.
2) Data manipulation instructions perform arithmetic, logical, and bitwise operations on data to provide computational capabilities. Examples include add, subtract, multiply, divide, and, or, xor.
3) Program control instructions alter the program flow by branching, jumping, calling subroutines, handling interrupts, and returning from subroutines. Status bits track results of operations.Microprogrammed Control Unit



Microprogrammed Control UnitPreethiSureshkumar1
?
(Ref : Computer System Architecture by Morris Mano 3rd edition) : Microprogrammed Control unit, micro instructions, micro operations, symbolic and binary microprogram.Interrupts



InterruptsUrwa Shanza
?
The document discusses interrupts in a computer system. It defines an interrupt as a signal that breaks the normal sequence of program execution to handle an event that requires immediate attention, like input from a device. There are two main types of interrupts: hardware interrupts caused by external devices, and software interrupts caused by exceptional conditions in a program like division by zero. The document outlines how interrupts work, including how the processor saves the state of the interrupted program, services the interrupt, and then restores the original program context. It also discusses interrupt priorities and how interrupts can be disabled or deferred based on priority.Bus aribration



Bus aribrationSaiyam Agrawal
?
Bus arbitration is the process of determining which device will become the bus master when multiple devices request access to the bus simultaneously. There are two main types of bus arbitration: centralized arbitration and distributed arbitration. Centralized arbitration uses a single bus controller to manage arbitration, while distributed arbitration allows each device to perform self-arbitration without a central controller. Bus arbitration is needed to avoid conflicts when multiple devices like the CPU and DMA controllers need simultaneous access to the bus. Direct memory access (DMA) allows high-speed transfer of large blocks of data between peripherals and memory without using the CPU.System call



System callSumant Diwakar
?
System calls provide an interface between processes and the operating system. They allow programs to request services like reading/writing files or communicating over a network. Common system calls include opening/closing files, reading/writing data, process creation/termination, and requesting the current time/date. System calls are grouped into categories like process control, file management, device management, information maintenance, and communications.Computer system bus



Computer system busGoran W. Hama Ali
?
The main Objective of this presentation is to define computer buses , especially system bus . which is consists of data bus , address bus and control bus.Process scheduling



Process schedulingRiya Choudhary
?
Process scheduling involves assigning system resources like CPU time to processes. There are three levels of scheduling - long, medium, and short term. The goals of scheduling are to minimize turnaround time, waiting time, and response time for users while maximizing throughput, CPU utilization, and fairness for the system. Common scheduling algorithms include first come first served, priority scheduling, shortest job first, round robin, and multilevel queue scheduling. Newer algorithms like fair share scheduling and lottery scheduling aim to prevent starvation.Memory organization (Computer architecture)



Memory organization (Computer architecture)Sandesh Jonchhe
?
Memory is organized in a hierarchy with different levels providing trade-offs between speed and cost.
- Cache memory sits between the CPU and main memory for fastest access.
- Main memory (RAM) is where active programs and data reside and is faster than auxiliary memory but more expensive.
- Auxiliary memory (disks, tapes) provides backup storage and is slower than main memory but larger and cheaper.
Virtual memory manages this hierarchy through address translation techniques like paging that map virtual addresses to physical locations, allowing programs to access more memory than physically available. When data is needed from auxiliary memory a page fault occurs and page replacement algorithms determine what data to remove from main memory.Cache memory ppt 



Cache memory ppt Arpita Naik
?
Cache memory is a small, fast memory located close to the processor that stores frequently accessed data from main memory. When the processor requests data, the cache is checked first. If the data is present, there is a cache hit and the data is accessed quickly from the cache. If not present, there is a cache hit and the data must be fetched from main memory, which takes longer. Cache memory relies on principles of temporal and spatial locality, where frequently and nearby accessed data is likely to be needed again soon. Mapping functions like direct, associative, and set-associative mapping determine how data is stored in the cache. Replacement policies like FIFO, LRU, etc. determine which cached data gets replaced when newStorage management in operating system



Storage management in operating systemDeepikaT13
?
The document discusses memory management and file management in operating systems. Memory management tracks memory allocation and handles moving processes between main memory and disk. File management creates, locates, shares, modifies, and deletes files and organizes them into directories. It also specifies file attributes, operations, access permissions, and the logical storage of files in file systems. Caching stores recently accessed data in temporary memory to improve input/output performance. The input/output subsystem of the operating system's kernel manages various input/output devices and their differing functionality and speeds.I/O System



I/O SystemNagarajan
?
The document discusses input/output (I/O) processing and the role of the operating system in managing I/O operations and devices. It covers I/O hardware components like ports, buses, and controllers. It also describes the different models for interaction between I/O controllers and CPUs, including polling, interrupts, and direct memory access (DMA). Finally, it discusses I/O application interfaces and blocking vs non-blocking I/O.Computer architecture cache memory



Computer architecture cache memoryMazin Alwaaly
?
Cache memory is a small, high-speed memory located between the CPU and main memory. It stores copies of frequently used instructions and data from main memory in order to speed up processing. There are multiple levels of cache with L1 cache being the smallest and fastest located directly on the CPU chip. Larger cache levels like L2 and L3 are further from the CPU but can still provide faster access than main memory. The main purpose of cache is to accelerate processing speed while keeping computer costs low.Computer architecture input output organization



Computer architecture input output organizationMazin Alwaaly
?
Computer Architecture Input Output Organization seminar
Mustansiriya University
Department of Education
Computer Science3. IICT_Lecture 03_Computer Org Personal



3. IICT_Lecture 03_Computer Org PersonalNational College of Business Administration and Economics
?
3. IICT_Lecture 03_Computer Org.pdfcomputer Architecture



computer Architectureumardanjumamaiwada
?
This document discusses the basic concepts of computer architecture. It covers topics like data, instructions, the initial concept of the machine, the structure and functions of a computer, registers, the execution unit, system unit, CPU, bus, memory unit, input/output units, and the von Neumann model. The key points are:
1) A computer needs a CPU, storage, input/output devices, and connectors to manipulate and store data/instructions and keep track of operations.
2) The CPU contains an arithmetic logic unit, control unit, and registers to process data according to instructions.
3) The von Neumann model forms the basic design of a computer with memory to store data/instructions, input andMore Related Content
What's hot (20)
Cpu organisation



Cpu organisationEr Sangita Vishwakarma
?
The CPU acts as the computer's brain and carries out instructions from programs. It has two main components: the control unit, which selects and coordinates instruction execution, and the arithmetic logic unit, which performs calculations. Registers temporarily store data during instruction processing, including special purpose registers like the program counter, memory address, and accumulator registers. The CPU communicates with main memory, where files and applications are stored, and executes instructions through a multi-step process controlled by the control unit.Computer registers



Computer registersJatin Grover
?
A register is a group of flip-flops that can each store one bit of information. A processor uses registers to hold instructions, addresses, and data for manipulating information. The document lists several common computer registers - the Data Register stores 16-bit operands from memory, the Address Register holds 12-bit memory addresses, the Accumulator is a general purpose 16-bit processing register, and the Program Counter contains the 12-bit address of the next instruction. Temporary and input/output registers are also used to store intermediate data and user input/output respectively.operating system lecture notes



operating system lecture notesAVC College of Engineering
?
This document provides course material for the subject of Operating Systems for 4th semester B.E. Computer Science Engineering students at A.V.C. College of Engineering. It includes information on the name and designation of the faculty teaching the course, the academic year, curriculum regulations, 5 units that make up the course content, textbook and reference details. The course aims to cover key topics in operating systems including processes, process scheduling, storage management, file systems and I/O systems.Processor Organization and Architecture



Processor Organization and ArchitectureVinit Raut
?
The document discusses processor organization and architecture. It covers the Von Neumann model, which stores both program instructions and data in the same memory. The Institute for Advanced Study (IAS) computer is described as the first stored-program computer, designed by John von Neumann to overcome limitations of previous computers like the ENIAC. The document also covers the Harvard architecture, instruction formats, register organization including general purpose, address, and status registers, and issues in instruction format design like instruction length and allocation of bits.IO Techniques in Computer Organization



IO Techniques in Computer OrganizationOm Prakash
?
The document discusses three different I/O techniques:
1. Programmed I/O - The CPU controls the entire I/O process and must periodically check device status, wasting CPU time.
2. Interrupt-driven I/O - The CPU issues a command and is freed up while the device operates. The device then interrupts the CPU when ready.
3. Direct memory access (DMA) - Allows devices to communicate directly with memory without involving the CPU, using a DMA controller. This overcomes CPU waiting and avoids repeated status checks. Arbitration in computer organization 



Arbitration in computer organization Amit kashyap
?
Buses are shared communication links that connect processors, memory, and input/output (I/O) devices. They allow new devices to be easily added and devices to be moved between systems using the same bus standard. However, buses can create communication bottlenecks and their maximum speed is limited by length and number of devices. Buses use control lines to signal requests/acknowledgments and indicate data type, while data lines carry addresses, data, and commands between devices. Devices controlling the bus are masters, while devices responding are slaves.Shared-Memory Multiprocessors



Shared-Memory MultiprocessorsSalvatore La Bua
?
The document discusses different types of parallel computer architectures, including shared-memory multiprocessors. It describes taxonomy of parallel computers including SISD, SIMD, MISD, and MIMD models. For shared-memory multiprocessors, it outlines consistency models including strict, sequential, processor, weak and release consistency. It also discusses UMA and NUMA architectures, cache coherence protocols like MESI, and examples of multiprocessors using crossbar switches or multistage networks.Data transfer and manipulation



Data transfer and manipulationSanjeev Patel
?
1) Data transfer instructions move data between processor registers and memory without changing the data. Common instructions include load, store, move, exchange, input, and output.
2) Data manipulation instructions perform arithmetic, logical, and bitwise operations on data to provide computational capabilities. Examples include add, subtract, multiply, divide, and, or, xor.
3) Program control instructions alter the program flow by branching, jumping, calling subroutines, handling interrupts, and returning from subroutines. Status bits track results of operations.Microprogrammed Control Unit



Microprogrammed Control UnitPreethiSureshkumar1
?
(Ref : Computer System Architecture by Morris Mano 3rd edition) : Microprogrammed Control unit, micro instructions, micro operations, symbolic and binary microprogram.Interrupts



InterruptsUrwa Shanza
?
The document discusses interrupts in a computer system. It defines an interrupt as a signal that breaks the normal sequence of program execution to handle an event that requires immediate attention, like input from a device. There are two main types of interrupts: hardware interrupts caused by external devices, and software interrupts caused by exceptional conditions in a program like division by zero. The document outlines how interrupts work, including how the processor saves the state of the interrupted program, services the interrupt, and then restores the original program context. It also discusses interrupt priorities and how interrupts can be disabled or deferred based on priority.Bus aribration



Bus aribrationSaiyam Agrawal
?
Bus arbitration is the process of determining which device will become the bus master when multiple devices request access to the bus simultaneously. There are two main types of bus arbitration: centralized arbitration and distributed arbitration. Centralized arbitration uses a single bus controller to manage arbitration, while distributed arbitration allows each device to perform self-arbitration without a central controller. Bus arbitration is needed to avoid conflicts when multiple devices like the CPU and DMA controllers need simultaneous access to the bus. Direct memory access (DMA) allows high-speed transfer of large blocks of data between peripherals and memory without using the CPU.System call



System callSumant Diwakar
?
System calls provide an interface between processes and the operating system. They allow programs to request services like reading/writing files or communicating over a network. Common system calls include opening/closing files, reading/writing data, process creation/termination, and requesting the current time/date. System calls are grouped into categories like process control, file management, device management, information maintenance, and communications.Computer system bus



Computer system busGoran W. Hama Ali
?
The main Objective of this presentation is to define computer buses , especially system bus . which is consists of data bus , address bus and control bus.Process scheduling



Process schedulingRiya Choudhary
?
Process scheduling involves assigning system resources like CPU time to processes. There are three levels of scheduling - long, medium, and short term. The goals of scheduling are to minimize turnaround time, waiting time, and response time for users while maximizing throughput, CPU utilization, and fairness for the system. Common scheduling algorithms include first come first served, priority scheduling, shortest job first, round robin, and multilevel queue scheduling. Newer algorithms like fair share scheduling and lottery scheduling aim to prevent starvation.Memory organization (Computer architecture)



Memory organization (Computer architecture)Sandesh Jonchhe
?
Memory is organized in a hierarchy with different levels providing trade-offs between speed and cost.
- Cache memory sits between the CPU and main memory for fastest access.
- Main memory (RAM) is where active programs and data reside and is faster than auxiliary memory but more expensive.
- Auxiliary memory (disks, tapes) provides backup storage and is slower than main memory but larger and cheaper.
Virtual memory manages this hierarchy through address translation techniques like paging that map virtual addresses to physical locations, allowing programs to access more memory than physically available. When data is needed from auxiliary memory a page fault occurs and page replacement algorithms determine what data to remove from main memory.Cache memory ppt 



Cache memory ppt Arpita Naik
?
Cache memory is a small, fast memory located close to the processor that stores frequently accessed data from main memory. When the processor requests data, the cache is checked first. If the data is present, there is a cache hit and the data is accessed quickly from the cache. If not present, there is a cache hit and the data must be fetched from main memory, which takes longer. Cache memory relies on principles of temporal and spatial locality, where frequently and nearby accessed data is likely to be needed again soon. Mapping functions like direct, associative, and set-associative mapping determine how data is stored in the cache. Replacement policies like FIFO, LRU, etc. determine which cached data gets replaced when newStorage management in operating system



Storage management in operating systemDeepikaT13
?
The document discusses memory management and file management in operating systems. Memory management tracks memory allocation and handles moving processes between main memory and disk. File management creates, locates, shares, modifies, and deletes files and organizes them into directories. It also specifies file attributes, operations, access permissions, and the logical storage of files in file systems. Caching stores recently accessed data in temporary memory to improve input/output performance. The input/output subsystem of the operating system's kernel manages various input/output devices and their differing functionality and speeds.I/O System



I/O SystemNagarajan
?
The document discusses input/output (I/O) processing and the role of the operating system in managing I/O operations and devices. It covers I/O hardware components like ports, buses, and controllers. It also describes the different models for interaction between I/O controllers and CPUs, including polling, interrupts, and direct memory access (DMA). Finally, it discusses I/O application interfaces and blocking vs non-blocking I/O.Computer architecture cache memory



Computer architecture cache memoryMazin Alwaaly
?
Cache memory is a small, high-speed memory located between the CPU and main memory. It stores copies of frequently used instructions and data from main memory in order to speed up processing. There are multiple levels of cache with L1 cache being the smallest and fastest located directly on the CPU chip. Larger cache levels like L2 and L3 are further from the CPU but can still provide faster access than main memory. The main purpose of cache is to accelerate processing speed while keeping computer costs low.Computer architecture input output organization



Computer architecture input output organizationMazin Alwaaly
?
Computer Architecture Input Output Organization seminar
Mustansiriya University
Department of Education
Computer ScienceSimilar to Hypothetical machine and instruction flow scenarios (20)
3. IICT_Lecture 03_Computer Org Personal



3. IICT_Lecture 03_Computer Org PersonalNational College of Business Administration and Economics
?
3. IICT_Lecture 03_Computer Org.pdfcomputer Architecture



computer Architectureumardanjumamaiwada
?
This document discusses the basic concepts of computer architecture. It covers topics like data, instructions, the initial concept of the machine, the structure and functions of a computer, registers, the execution unit, system unit, CPU, bus, memory unit, input/output units, and the von Neumann model. The key points are:
1) A computer needs a CPU, storage, input/output devices, and connectors to manipulate and store data/instructions and keep track of operations.
2) The CPU contains an arithmetic logic unit, control unit, and registers to process data according to instructions.
3) The von Neumann model forms the basic design of a computer with memory to store data/instructions, input andL-1 BCE computer fundamentals final kirti.ppt



L-1 BCE computer fundamentals final kirti.pptKirti Verma
?
The document defines a computer and describes its key advantages such as speed, accuracy, storage capability, diligence, and versatility. It then discusses some disadvantages like lack of intelligence, dependency on humans, and lack of feelings. The document also provides overviews of several topics related to computing including e-business, bioinformatics, healthcare applications, remote sensing, geographic information systems, meteorology/climatology, and computer gaming. Finally, it describes the fundamental components of a computer including the CPU, memory subsystem, I/O subsystem, and how they are connected via buses. It provides details on registers, instruction format, and the instruction cycle.Chs demo



Chs demodavid david
?
1. The document discusses the basic data processing cycle in a computer system, which involves input, processing, and output units.
2. The central processing unit (CPU) is the most important part and directs all processing, containing an arithmetic logic unit, control unit, and main memory.
3. The two main types of memory are random access memory (RAM), which is temporary, and read-only memory (ROM), which permanently stores basic startup programs.CPU and memory



CPU and memoryWajiha Muhammad Ismail
?
This document provides explanations of various components of a computer system including the CPU, ALU, control unit, memory unit, and cache memory. It describes the CPU as the brain of the computer that performs tasks like arithmetic, logical and I/O operations. The ALU is where data processing occurs through arithmetic and logical operations. The control unit controls operations in the CPU and directs traffic, synchronizing the entire system. The memory unit refers to both primary memory like RAM and ROM, as well as secondary memory for long-term storage.Ch 01 os8e



Ch 01 os8eSyed Faisal
?
This document provides an overview of basic computer system components and their functions. It discusses the main components including the processor, main memory, I/O modules, and system bus. It also describes how instructions are executed in a fetch-execute cycle and how interrupts can alter the normal sequencing. The memory hierarchy is introduced, including caches and different levels of memory. Common I/O techniques like programmed I/O, interrupt-driven I/O, and direct memory access are summarized. Finally, symmetric multiprocessors and multicore computers are defined.PROGRAMMABLE LOGIC CONTROLLER



PROGRAMMABLE LOGIC CONTROLLERarunkumar6836
?
This document provides an overview of programmable logic controllers (PLCs). It discusses that a PLC uses a programmable memory to store instructions to implement logic and control machines. A PLC consists of a central processing unit, memory, and input/output processing devices. The central processing unit contains an arithmetic logic unit and control unit to perform operations. Memory in a PLC includes random access memory to store the operating system and programs in use, and read only memory to store essential boot up instructions. Input/output processing devices provide an interface between the PLC and external devices like sensors and motors to input and output signals.Basic of operating system



Basic of operating systempriyanka jain
?
This document provides an overview of the basic components and operations of a computer system. It discusses how a computer system is composed of input, output, processing, memory, and controlling units. The central processing unit (CPU) acts as the brain and contains the arithmetic logic unit (ALU) and control unit to process data. Memory, including primary memory like RAM and ROM, is used to store programs and data both temporarily for processing and more permanently. Input and output devices allow the user to interface with the computer system by entering and receiving data. The five basic operations of a computer system are inputting, storing, processing, outputting, and controlling data.co1_aiml_new.pptx



co1_aiml_new.pptxKUNTALADAS5
?
The document discusses the Von Neumann computer architecture. It describes the basic structure of a Von Neumann computer which includes a central processing unit (CPU), main memory, and input/output devices. The CPU contains a control unit, arithmetic logic unit, and registers. The main memory stores both programs and data. The architecture specifies that all components are connected via buses that transfer data, addresses, and control signals. It also notes that the Von Neumann design processes instructions sequentially, which can create a performance bottleneck.Intro to cao &store program



Intro to cao &store programMahesh Kumar Attri
?
The document provides information about the key components and architecture of computers. It discusses:
- The main components of a computer including the central processing unit (CPU), memory, and input/output devices. The CPU contains an arithmetic logic unit and program control unit.
- How digital computers represent and process information using binary digits (bits) representing 0s and 1s.
- Computer organization and architecture, and how they are concerned with how hardware components are connected and structured.
- The evolution of early computers from mechanical to electronic stored-program computers like the ENIAC, EDVAC, and IAS machine.Lecture 3 Computer architecture-cpu.pptx



Lecture 3 Computer architecture-cpu.pptxsamgamingofficial01
?
The document provides an overview of computer system architecture and hardware. It defines computer architecture as the structure and behavior of a computer system, including its components and how they interact. The historical background section describes how computers evolved from simple calculation machines during World War II to the modern computers we use today. The document then discusses the main internal and external hardware components of a computer system and provides details on the central processing unit (CPU), including its main parts like the arithmetic logic unit and control unit, as well as the CPU instruction cycle.Microprocessor



Microprocessoraaina_katyal
?
The document provides an overview of microprocessors, including what they are, their basic components and functions. It discusses how a microprocessor:
- Acts as the central processing unit (CPU) of a computer to provide computational control
- Can be programmed to perform functions on data by writing instructions into its memory
- Has components like an arithmetic logic unit, registers, cache memory and bus interfaces to transfer data and addressesChapter 1.pdf



Chapter 1.pdfAnisZahirahAzman
?
1. The document discusses the components and architecture of computers, including microprocessors, CPUs, memory, and I/O devices.
2. It describes the main components of a microcomputer as the CPU, memory, parallel I/O, serial I/O, programmable interrupt, and direct memory access. The CPU contains an arithmetic logic unit, control unit, and registers.
3. Memory types include cache memory, main memory, and secondary memory. Most computers use static random access memory for cache, dynamic random access memory for main memory, and hard disks for secondary memory.Introduction to-microprocessor



Introduction to-microprocessorankitnav1
?
The document provides an introduction to microprocessors, including:
- The basic components of a computer system using block diagrams including the CPU, memory, and input/output units.
- The evolution of microprocessors from 4 to 64 bytes.
- The internal structure and basic operation of a microprocessor including the arithmetic logic unit, control unit, register sets, accumulator, condition code register, program counter, and stack pointer.
- Examples of microprocessors such as the Intel 8085 and 8086.Introduction to-microprocessor



Introduction to-microprocessorankitnav1
?
The document provides an introduction to microprocessors, including:
1. The basic components of a computer system including the CPU, memory, and input/output units.
2. The evolution of microprocessors from 4-bit to 64-bit sizes.
3. An overview of the internal structure of a microprocessor, including the arithmetic logic unit, control unit, register sets, accumulator, program counter, and condition code register.
4. A description of the bus system including the data bus, address bus, and control bus that allow communication between the microprocessor and other computer components.Comp App Lect 2 System Unit.pptx



Comp App Lect 2 System Unit.pptxMehwishKanwal14
?
The CPU is the central processing unit of the computer that acts as its brain. It contains two main components - the control unit and the arithmetic logic unit. The control unit fetches instructions from memory and directs the overall flow of data by orchestrating the operation of all other parts of the CPU. It decodes and executes instructions by determining the sequence of operations. The arithmetic logic unit performs arithmetic and logical operations and contains registers for temporary data storage. It executes the instructions by performing calculations on data stored in registers. The CPU follows an instruction cycle of fetching, decoding, executing and storing instructions to process data according to programs.1834902155 aka asgn 313



1834902155 aka asgn 313FatemaYesminAka
?
The document discusses the basic components and workings of a computer system. It describes the main components as the input, output, storage, and central processing units. It then explains how each component functions and how the computer operates from powering on through loading the operating system and allowing hardware devices to communicate.Chap 3 CA.pptx



Chap 3 CA.pptxSahalAhmed4
?
The document discusses the components inside a CPU. It describes the motherboard, power supply, cooling fan, and drive bays that are inside the computer case. On the motherboard are the system clock, microprocessor, memory, chipset, and input/output buses. The CPU is made up of a control unit, instruction unit with ALU and FPU, registers, caches, and buses that connect the components. Common CPU components like the clock, control unit, and cache are also explained in detail.APznzaboj9CF_9DQRT2HR-lWEYeLjr197Vw_ZUktUfDvP5Qqd8SL2ZSNwpIwVoC6MN9lqvglTXM11...



APznzaboj9CF_9DQRT2HR-lWEYeLjr197Vw_ZUktUfDvP5Qqd8SL2ZSNwpIwVoC6MN9lqvglTXM11...rohithzach
?
computer organization and architectureRecently uploaded (20)
[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
![[Webinar] Scaling Made Simple: Getting Started with No-Code Web Apps](https://cdn.slidesharecdn.com/ss_thumbnails/webinarscalingmadesimplegettingstartedwithno-codewebapps-mar52025-250305183437-f03c78a3-thumbnail.jpg?width=560&fit=bounds)
[Webinar] Scaling Made Simple: Getting Started with No-Code Web AppsSafe Software
?
Ready to simplify workflow sharing across your organization without diving into complex coding? With FME Flow Apps, you can build no-code web apps that make your data work harder for you ¡ª fast.
In this webinar, we¡¯ll show you how to:
Build and deploy Workspace Apps to create an intuitive user interface for self-serve data processing and validation.
Automate processes using Automation Apps. Learn to create a no-code web app to kick off workflows tailored to your needs, trigger multiple workspaces and external actions, and use conditional filtering within automations to control your workflows.
Create a centralized portal with Gallery Apps to share a collection of no-code web apps across your organization.
Through real-world examples and practical demos, you¡¯ll learn how to transform your workflows into intuitive, self-serve solutions that empower your team and save you time. We can¡¯t wait to show you what¡¯s possible!The Future of Repair: Transparent and Incremental by Botond De?nes



The Future of Repair: Transparent and Incremental by Botond De?nesScyllaDB
?
Regularly run repairs are essential to keep clusters healthy, yet having a good repair schedule is more challenging than it should be. Repairs often take a long time, preventing running them often. This has an impact on data consistency and also limits the usefulness of the new repair based tombstone garbage collection. We want to address these challenges by making repairs incremental and allowing for automatic repair scheduling, without relying on external tools.How Discord Indexes Trillions of Messages: Scaling Search Infrastructure by V...



How Discord Indexes Trillions of Messages: Scaling Search Infrastructure by V...ScyllaDB
?
This talk shares how Discord scaled their message search infrastructure using Rust, Kubernetes, and a multi-cluster Elasticsearch architecture to achieve better performance, operability, and reliability, while also enabling new search features for Discord users.Endpoint Backup: 3 Reasons MSPs Ignore It



Endpoint Backup: 3 Reasons MSPs Ignore ItMSP360
?
Many MSPs overlook endpoint backup, missing out on additional profit and leaving a gap that puts client data at risk.
Join our webinar as we break down the top challenges of endpoint backup¡ªand how to overcome them.Backstage Software Templates for Java Developers



Backstage Software Templates for Java DevelopersMarkus Eisele
?
As a Java developer you might have a hard time accepting the limitations that you feel being introduced into your development cycles. Let's look at the positives and learn everything important to know to turn Backstag's software templates into a helpful tool you can use to elevate the platform experience for all developers.THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIA



THE BIG TEN BIOPHARMACEUTICAL MNCs: GLOBAL CAPABILITY CENTERS IN INDIASrivaanchi Nathan
?
This business intelligence report, "The Big Ten Biopharmaceutical MNCs: Global Capability Centers in India", provides an in-depth analysis of the operations and contributions of the Global Capability Centers (GCCs) of ten leading biopharmaceutical multinational corporations in India. The report covers AstraZeneca, Bayer, Bristol Myers Squibb, GlaxoSmithKline (GSK), Novartis, Sanofi, Roche, Pfizer, Novo Nordisk, and Eli Lilly. In this report each company's GCC is profiled with details on location, workforce size, investment, and the strategic roles these centers play in global business operations, research and development, and information technology and digital innovation.Revolutionizing-Government-Communication-The-OSWAN-Success-Story



Revolutionizing-Government-Communication-The-OSWAN-Success-Storyssuser52ad5e
?
? ????? ??????? ????? ?
???????? ??????????? is proud to be a part of the ?????? ????? ???? ???? ??????? (?????) success story! By delivering seamless, secure, and high-speed connectivity, OSWAN has revolutionized e-?????????? ?? ??????, enabling efficient communication between government departments and enhancing citizen services.
Through our innovative solutions, ???????? ?????????? has contributed to making governance smarter, faster, and more transparent. This milestone reflects our commitment to driving digital transformation and empowering communities.
? ?????????? ??????, ?????????? ??????????!
UiPath Automation Developer Associate Training Series 2025 - Session 1



UiPath Automation Developer Associate Training Series 2025 - Session 1DianaGray10
?
Welcome to UiPath Automation Developer Associate Training Series 2025 - Session 1.
In this session, we will cover the following topics:
Introduction to RPA & UiPath Studio
Overview of RPA and its applications
Introduction to UiPath Studio
Variables & Data Types
Control Flows
You are requested to finish the following self-paced training for this session:
Variables, Constants and Arguments in Studio 2 modules - 1h 30m - https://academy.uipath.com/courses/variables-constants-and-arguments-in-studio
Control Flow in Studio 2 modules - 2h 15m - https:/academy.uipath.com/courses/control-flow-in-studio
?? For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. UiPath Agentic Automation Capabilities and Opportunities



UiPath Agentic Automation Capabilities and OpportunitiesDianaGray10
?
Learn what UiPath Agentic Automation capabilities are and how you can empower your agents with dynamic decision making. In this session we will cover these topics:
What do we mean by Agents
Components of Agents
Agentic Automation capabilities
What Agentic automation delivers and AI Tools
Identifying Agent opportunities
? If you have any questions or feedback, please refer to the "Women in Automation 2025" dedicated Forum thread. You can find there extra details and updates.DealBook of Ukraine: 2025 edition | AVentures Capital



DealBook of Ukraine: 2025 edition | AVentures CapitalYevgen Sysoyev
?
The DealBook is our annual overview of the Ukrainian tech investment industry. This edition comprehensively covers the full year 2024 and the first deals of 2025. Unlocking DevOps Secuirty :Vault & Keylock



Unlocking DevOps Secuirty :Vault & KeylockHusseinMalikMammadli
?
DevOps i? t?hl¨¹k?sizliyi sizi maraqland?r?r? ?st?r developer, ist?r t?hl¨¹k?sizlik m¨¹h?ndisi, ist?rs? d? DevOps h?v?skar? olun, bu t?dbir ??b?k?l??m?k, bilikl?rinizi b?l¨¹?m?k v? DevSecOps sah?sind? ?n son t?cr¨¹b?l?ri ?yr?nm?k ¨¹?¨¹n m¨¹k?mm?l f¨¹rs?tdir!
Bu workshopda DevOps infrastrukturlar?n?n t?hl¨¹k?sizliyini nec? art?rmaq bar?d? dan??acay?q. DevOps sisteml?ri qurulark?n avtomatla?d?r?lm??, y¨¹ks?k ?l?atan v? etibarl? olmas? il? yana??, h?m d? t?hl¨¹k?sizlik m?s?l?l?ri n?z?r? al?nmal?d?r. Bu s?b?bd?n, DevOps komandolar?n?n t?hl¨¹k?sizliy? y?n?lmi? praktikalara riay?t etm?si vacibdir.Unlock AI Creativity: Image Generation with DALL¡¤E



Unlock AI Creativity: Image Generation with DALL¡¤EExpeed Software
?
Discover the power of AI image generation with DALL¡¤E, an advanced AI model that transforms text prompts into stunning, high-quality visuals. This presentation explores how artificial intelligence is revolutionizing digital creativity, from graphic design to content creation and marketing. Learn about the technology behind DALL¡¤E, its real-world applications, and how businesses can leverage AI-generated art for innovation. Whether you're a designer, developer, or marketer, this guide will help you unlock new creative possibilities with AI-driven image synthesis.A Framework for Model-Driven Digital Twin Engineering



A Framework for Model-Driven Digital Twin EngineeringDaniel Lehner
?
ºÝºÝߣs from my PhD Defense at Johannes Kepler University, held on Janurary 10, 2025.
The full thesis is available here: https://epub.jku.at/urn/urn:nbn:at:at-ubl:1-83896Transform Your Future with Front-End Development Training



Transform Your Future with Front-End Development TrainingVtechlabs
?
Kickstart your career in web development with our front-end web development course in Vadodara. Learn HTML, CSS, JavaScript, React, and more through hands-on projects and expert mentorship. Our front-end development course with placement includes real-world training, mock interviews, and job assistance to help you secure top roles like Front-End Developer, UI/UX Developer, and Web Designer.
Join VtechLabs today and build a successful career in the booming IT industry!Future-Proof Your Career with AI Options



Future-Proof Your Career with AI OptionsDianaGray10
?
Learn about the difference between automation, AI and agentic and ways you can harness these to further your career. In this session you will learn:
Introduction to automation, AI, agentic
Trends in the marketplace
Take advantage of UiPath training and certification
In demand skills needed to strategically position yourself to stay ahead
? If you have any questions or feedback, please refer to the "Women in Automation 2025" dedicated Forum thread. You can find there extra details and updates.Fl studio crack version 12.9 Free Download



Fl studio crack version 12.9 Free Downloadkherorpacca127
?
Google the copied link ???? https://activationskey.com/download-latest-setup/
????
The ultimate guide to FL Studio 12.9 Crack, the revolutionary digital audio workstation that empowers musicians and producers of all levels. This software has become a cornerstone in the music industry, offering unparalleled creative capabilities, cutting-edge features, and an intuitive workflow.
With FL Studio 12.9 Crack, you gain access to a vast arsenal of instruments, effects, and plugins, seamlessly integrated into a user-friendly interface. Its signature Piano Roll Editor provides an exceptional level of musical expression, while the advanced automation features empower you to create complex and dynamic compositions.L01 Introduction to Nanoindentation - What is hardness



L01 Introduction to Nanoindentation - What is hardnessRostislavDaniel
?
Introduction to NanoindentationBrave Browser Crack 1.45.133 Activated 2025



Brave Browser Crack 1.45.133 Activated 2025kherorpacca00126
?
https://ncracked.com/7961-2/
Note: >> Please copy the link and paste it into Google New Tab now Download link
Brave is a free Chromium browser developed for Win Downloads, macOS and Linux systems that allows users to browse the internet in a safer, faster and more secure way than its competition. Designed with security in mind, Brave automatically blocks ads and trackers which also makes it faster,
As Brave naturally blocks unwanted content from appearing in your browser, it prevents these trackers and pop-ups from slowing Download your user experience. It's also designed in a way that strips Downloaden which data is being loaded each time you use it. Without these components
TrustArc Webinar - Building your DPIA/PIA Program: Best Practices & Tips



TrustArc Webinar - Building your DPIA/PIA Program: Best Practices & TipsTrustArc
?
Understanding DPIA/PIAs and how to implement them can be the key to embedding privacy in the heart of your organization as well as achieving compliance with multiple data protection / privacy laws, such as GDPR and CCPA. Indeed, the GDPR mandates Privacy by Design and requires documented Data Protection Impact Assessments (DPIAs) for high risk processing and the EU AI Act requires an assessment of fundamental rights.
How can you build this into a sustainable program across your business? What are the similarities and differences between PIAs and DPIAs? What are the best practices for integrating PIAs/DPIAs into your data privacy processes?
Whether you're refining your compliance framework or looking to enhance your PIA/DPIA execution, this session will provide actionable insights and strategies to ensure your organization meets the highest standards of data protection.
Join our panel of privacy experts as we explore:
- DPIA & PIA best practices
- Key regulatory requirements for conducting PIAs and DPIAs
- How to identify and mitigate data privacy risks through comprehensive assessments
- Strategies for ensuring documentation and compliance are robust and defensible
- Real-world case studies that highlight common pitfalls and practical solutionsDAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (ƽɽÒã)



DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (ƽɽÒã)Tsuyoshi Hirayama
?
DAO UTokyo 2025
–|¾©´óѧÇéˆóѧh ¥Ö¥í¥Ã¥¯¥Á¥§©`¥óÑо¿¥¤¥Ë¥·¥¢¥Æ¥£¥Ö
https://utbciii.com/2024/12/12/announcing-dao-utokyo-2025-conference/
Session 1 :DLT mass adoption
IBM Tsuyoshi Hirayama (ƽɽÒã)Hypothetical machine and instruction flow scenarios
- 2. INTRODUCTION The hypothetical computer described here serves as a model, or abstraction, of the step-by-step behavior of a real-life digital computer. Being only a model (and thus a simplification of reality), the hypothetical computer does not possess all the capabilities of a (typical) real-life general-purpose computer; however, it operates in, essentially, the same way. Thus, by coming to an understanding of this model, you will have come also to a better understanding of what goes on "under the hood" of your laptop computer, or smart phone, or other digital data processing device that you may happen to use.
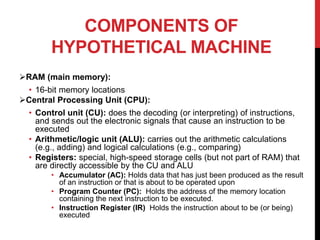
- 3. COMPONENTS OF HYPOTHETICAL MACHINE ?RAM (main memory): ? 16-bit memory locations ?Central Processing Unit (CPU): ? Control unit (CU): does the decoding (or interpreting) of instructions, and sends out the electronic signals that cause an instruction to be executed ? Arithmetic/logic unit (ALU): carries out the arithmetic calculations (e.g., adding) and logical calculations (e.g., comparing) ? Registers: special, high-speed storage cells (but not part of RAM) that are directly accessible by the CU and ALU ? Accumulator (AC): Holds data that has just been produced as the result of an instruction or that is about to be operated upon ? Program Counter (PC): Holds the address of the memory location containing the next instruction to be executed. ? Instruction Register (IR) Holds the instruction about to be (or being) executed
- 4. COMPONENTS OF HYPOTHETICAL MACHINE ?I/O Devices: ? keyboard, at which the user can enter integer values ? screen, on which integer values can be displayed
- 5. EXAMPLE: Step 1: Step 2:
- 6. Step 3: Step 4:
- 7. Step 5: Step 6:
- 8. INSTRUCTION FLOW SCENARIOS ?Fetch the instruction ? The CPU sends the PC to the MAR and sends a read command on the address bus ? In response to the read command, the memory returns the data stored at the memory location indicated by PC on the data bus ? The CPU copies the data from the data bus into its MBR ? A fraction of a second later, the CPU copies the data from the MDR to the instruction register (IR) ? The PC is incremented so that it points to the following instruction in memory. This step prepares the CPU for the next cycle. ?Decode the instruction ? The opcode fetched from the memory is decoded for the next steps and moved to the appropriate registers.
- 9. INSTRUCTION FLOW ?Reading the effective address ? Direct memory instruction - Nothing is being done. ? Indirect memory instruction - The effective address is being read from the memory. ?Execute Instruction ? Here, the function of the instruction is performed. If the instruction involves arithmetic or logic, the Arithmetic Logic Unit is utilized.
- 10. DATA FLOW FETCH CYCLE
- 11. DATA FLOW INDIRECT CYCLE
- 12. DATA FLOW INTERRUPT CYCLE
