1 of 12
Download to read offline











Ad
Recommended
La nit del terror. Euclides
La nit del terror. Euclides joan
╠²
Gimcana de "la casa encantada" per a l'Institut Euclides de Pineda de Mar. Casa de col├▓nies La MolinaEls Cavallets De Mar Mesuram Els Dinosaures
Els Cavallets De Mar Mesuram Els DinosauresCP URBANITZACIONS LLUCMAJOR
╠²
Los ni├▒os de primaria y su proyectoJoc oca i preguntes bloom
Joc oca i preguntes bloomBeatriu PALAU
╠²
Text instructiu: Joc de l'oca.
Preguntes de diferents nivells de coneixement segons la Taxonomia de Bloom.Passat, perfet i futur (exercicis)
Passat, perfet i futur (exercicis)Dolors Matill├│
╠²
Exercicis de passat, perfet i futur.
Expressions temporals i adverbis de temps.Jocs tradicionals valencians
Jocs tradicionals valencianselmaestro juan
╠²
Una publicaci├│ de la Generalitat Valenciana amb l'autoria del meu benvolgut amic i mestre Angel G├│mez i Navarro.Pechakucha Els jocs a l'aula
Pechakucha Els jocs a l'aulaJOSE MART├ŹNEZ NAVARRO
╠²
Ac├Ł tenim una presentaci├│ resum que podem fer servir a l'aula d'educaci├│ f├Łsica a l'hora de treballar els jocs populars i tradicionals.Knowledge management prannoy
Knowledge management prannoyPrannoy Pande
╠²
Ericsson is a Swedish telecommunications company founded in 1876. It operates in India through Ericsson India Pvt. Ltd and Ericsson India Global, headquartered in Noida. Ericsson's vision is a networked society where everyone is empowered through mobility. The document discusses Ericsson's knowledge management process for incident management in its Network and Voice department in India. It follows an IT service management methodology with defined roles and hierarchy to generate, store, distribute and apply knowledge at each stage of the incident resolution process for benefits like standardized processes, reduced resolution times, and fewer recurring incidents.More Related Content
What's hot (19)
Joc oca i preguntes bloom
Joc oca i preguntes bloomBeatriu PALAU
╠²
Text instructiu: Joc de l'oca.
Preguntes de diferents nivells de coneixement segons la Taxonomia de Bloom.Passat, perfet i futur (exercicis)
Passat, perfet i futur (exercicis)Dolors Matill├│
╠²
Exercicis de passat, perfet i futur.
Expressions temporals i adverbis de temps.Jocs tradicionals valencians
Jocs tradicionals valencianselmaestro juan
╠²
Una publicaci├│ de la Generalitat Valenciana amb l'autoria del meu benvolgut amic i mestre Angel G├│mez i Navarro.Pechakucha Els jocs a l'aula
Pechakucha Els jocs a l'aulaJOSE MART├ŹNEZ NAVARRO
╠²
Ac├Ł tenim una presentaci├│ resum que podem fer servir a l'aula d'educaci├│ f├Łsica a l'hora de treballar els jocs populars i tradicionals.Viewers also liked (15)
Knowledge management prannoy
Knowledge management prannoyPrannoy Pande
╠²
Ericsson is a Swedish telecommunications company founded in 1876. It operates in India through Ericsson India Pvt. Ltd and Ericsson India Global, headquartered in Noida. Ericsson's vision is a networked society where everyone is empowered through mobility. The document discusses Ericsson's knowledge management process for incident management in its Network and Voice department in India. It follows an IT service management methodology with defined roles and hierarchy to generate, store, distribute and apply knowledge at each stage of the incident resolution process for benefits like standardized processes, reduced resolution times, and fewer recurring incidents.Aegis padlock manual
Aegis padlock manualAliaksei Naumovich
╠²
This document is the user manual for the Aegis Padlock portable secure hard drive. It describes how to set up and use the drive, including connecting it, entering the admin and user modes using passwords, changing passwords, resetting the drive, and formatting it. The drive uses hardware encryption and has features to protect against brute force password attacks, such as locking the keypad after a number of failed attempts.Dsp Presentation
Dsp PresentationPeeyush Pashine
╠²
This document discusses filtering noise from ECG signals. It examines power line noise at 50 Hz and other noises that can interfere with ECG readings. It explores using filters like IIR and FIR filters as well as Chebyshev filters to remove noise and isolate the pure ECG signal. It details using MATLAB to design a 4th order Butterworth-Squintz filter and generating Verilog code to simulate the filter on a Spartan 3E FPGA board by feeding coefficients from LUTs and implementing multiplication through recursive addition in the MAC operation.Skyway - ąóčĆą░ąĮčüą┐ąŠčĆčé 21 ą▓ąĄą║ą░
Skyway - ąóčĆą░ąĮčüą┐ąŠčĆčé 21 ą▓ąĄą║ą░Aliaksei Naumovich
╠²
ąöąŠą║čāą╝ąĄąĮčé ąŠą┐ąĖčüčŗą▓ą░ąĄčé ąĮąŠą▓čāčÄ čéčĆą░ąĮčüą┐ąŠčĆčéąĮčāčÄ čüąĖčüč鹥ą╝čā Sky Way, ą║ąŠč鹊čĆą░čÅ ą┤ą▓ąĖąČąĄčéčüčÅ ąĮą░ ą▓čŗčüąŠč鹥 ą┐ąŠ ą▓čŗčüąŠą║ąŠą┐čĆąŠčćąĮčŗą╝ čĆąĄą╗čīčüą░ą╝, ą┐čĆąĄą┤ą╗ą░ą│ą░čÅ ą▓čŗčüąŠą║čāčÄ čüą║ąŠčĆąŠčüčéčī, ą╝ąĖąĮąĖą╝ą░ą╗čīąĮčŗąĄ ąĘą░čéčĆą░čéčŗ ąĮą░ čüčéčĆąŠąĖč鹥ą╗čīčüčéą▓ąŠ ąĖ ą┤ąŠą╗ą│ąĖą╣ čüčĆąŠą║ čüą╗čāąČą▒čŗ. ąĪąĖčüč鹥ą╝ą░ ąĮą░ą┐čĆą░ą▓ą╗ąĄąĮą░ ąĮą░ čĆąĄčłąĄąĮąĖąĄ ą┐čĆąŠą▒ą╗ąĄą╝ ą│ąŠčĆąŠą┤čüą║ąŠą╣ ąĖąĮčäčĆą░čüčéčĆčāą║čéčāčĆčŗ, 菹║ąŠą╗ąŠą│ąĖąĖ ąĖ ą░ą▓ą░čĆąĖą╣ąĮąŠčüčéąĖ ąĮą░ ą┤ąŠčĆąŠą│ą░čģ, ą┐čĆąĄą┤ą╗ą░ą│ą░čÅ ąĘąĮą░čćąĖč鹥ą╗čīąĮčŗą╣ 菹║ąŠąĮąŠą╝ąĖč湥čüą║ąĖą╣ ą┐ąŠč鹥ąĮčåąĖą░ą╗ ąĮą░ ą╝ąĄąČą┤čāąĮą░čĆąŠą┤ąĮčŗčģ čĆčŗąĮą║ą░čģ. ąóą░ą║ąČąĄ ą░ą║čåąĄąĮčéąĖčĆčāąĄčéčüčÅ ą▓ąĮąĖą╝ą░ąĮąĖąĄ ąĮą░ ąĖąĮą▓ąĄčüčéąĖčåąĖąŠąĮąĮčŗčģ ą▓ąŠąĘą╝ąŠąČąĮąŠčüčéčÅčģ ąĖ ą┐ą╗ą░ąĮą░čģ ą┐ąŠ čĆąĄą░ą╗ąĖąĘą░čåąĖąĖ ą┐čĆąŠąĄą║čéą░ ą▓ ąæąĄą╗ą░čĆčāčüąĖ.Decimal arithmetic in Processors
Decimal arithmetic in ProcessorsPeeyush Pashine
╠²
To represent a binary floating-point number as an exact fraction, the number of decimal digits needed depends on the precision of the binary floating-point format. Higher precision formats like double precision may require on the order of 15-17 decimal digits.
To represent a binary floating-point number reversibly so that it can be converted back to the same binary value, the number of decimal digits needed depends on the precision as well as the desired rounding mode. For double precision numbers using round-to-nearest rounding, about 16-17 decimal digits are typically needed.zia_mehdi_cv
zia_mehdi_cvZia Mehdi
╠²
This document contains a summary of Zia Mehdi's work experience and technical skills. He has over 10 years of experience in cellular network optimization, including expertise in LTE, UMTS, GSM, and wireless technologies. His roles have included senior RF optimization engineer, 3G RNO, and LTE RF optimization engineer for various telecom companies in Saudi Arabia, Nigeria, Oman, UAE, and the United States. He is proficient in optimization tools from multiple vendors and has extensive experience monitoring and improving network KPIs.Present Simple To Be
Present Simple To BeNeus Puig
╠²
This document provides information about the present simple verb "to be" in English, including its affirmative and negative forms in both long and short versions for singular and plural subjects. It also covers question forms and short answers. Examples are given for uses of the verb "to be" such as introducing oneself and others, describing weather, time, places, and ages. Key rules are highlighted like not using "I amn't" and using short forms more commonly in speech.Verb to be past
Verb to be pastNeus Puig
╠²
Copyright information is provided for a document written by Juan Guzman and adapted by Neus Puig for Escola Alfred Mata on November 7, 2011. The document relates to copyright and was written for or adapted to a school.Past Simple To Be
Past Simple To BeNeus Puig
╠²
Copyright information is provided for a document written by Juan Guzman and adapted by Neus Puig for Escola Alfred Mata on November 7, 2011. The document relates to copyright and was written for or adapted to a school.My Report on adders
My Report on addersPeeyush Pashine
╠²
The document discusses various types of adders including 1-bit adders like half adders and full adders, multi-bit adders like ripple carry adders, carry lookahead adders, carry select/skip adders, and carry save adders. It provides details on the design, pros and cons, and Verilog code for each type of adder. The document aims to provide a comparative study of these adders through detailed analysis and descriptions.Kogge Stone Adder
Kogge Stone AdderPeeyush Pashine
╠²
The document discusses Kogge Stone adders, which are a type of prefix adder circuit. It provides details on:
1) How prefix adders work by computing the sum of inputs in parallel using an operation applied sequentially from the least significant to most significant bits.
2) The graph representation of prefix adders showing how partial sums are computed.
3) The Kogge Stone adder specifically, which is a variant of prefix adders that balances delay and hardware cost. Radix-2 and radix-4 Kogge Stone adders are shown.Telling the time
Telling the timeNeus Puig
╠²
The document provides examples of telling time in hours, minutes and periods of the day (am and pm). It lists times such as "three o'clock", "twenty to one", "ten past ten", and accompanies each with the question "What time is it?". It then prompts the reader to choose the correct clock face for times including "half past five", "a quarter past nine", and "midday".Ad
Similar to Treballem amb les ombres (7)
Ad
Treballem amb les ombres
- 1. LŌĆÖalumnat de Cicle Inicial TREBALLEM AMB LES OMBRES
- 2. Experimentem ’é¦ Sortim al pati i juguem a xafar-nos les ombres. ’é¦ A partir dŌĆÖaqu├Ł les observem i rumiem perqu├© hi ha ombra.
- 3. Volem mesurar les ombres ’é¦ Cada grup ha ideat una manera de mesurar les ombres. Ens voleu veure?
- 4. Preparem el materialŌĆ” Necessitem paper per poder mesurar lŌĆÖombra amb el nostre aparell
- 5. Posem lŌĆÖaparell al seu llocŌĆ” El grup 3 hem decidit que mesurar├Łem lŌĆÖombra amb el pal de la xarxa de ŌĆ£voleiŌĆØŌĆ”
- 6. ŌĆ”i lŌĆÖhem muntat entre tots
- 7. Ubiquem el nostre aparellŌĆ” A nosaltres, que som el grup 2, ens ha semblat que utilitzar un pal dins una galleda podria ser ├║til per mesurar les ombres .
- 8. ŌĆ” i ens hem posat a la feina
- 9. El nostre aparell ├®s aquestŌĆ” El grup 1, hem ideat un aparell que ├®s una base de plastilina amb un llapis enganxatŌĆ”
- 10. ŌĆ”i de seguida ens hem posat a mesurar!
- 11. ŌĆ£ProtegimŌĆØ els nostres aparellsŌĆ” Tots hem tingut cura dŌĆÖalertar a la resta de lŌĆÖescola que no ens toqu├®ssin els aparells i sort que ens han fet casŌĆ”gr├Ācies!
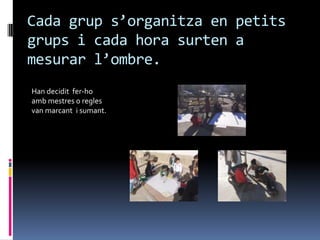
- 12. Cada grup sŌĆÖorganitza en petits grups i cada hora surten a mesurar lŌĆÖombre. Han decidit fer-ho amb mestres o regles van marcant i sumant.
