CyberChefの使い方(HamaCTF2019 WriteUp編)
- 2. HamaCTFとは ? HamaCTFはセキュリティ勉強会HamaSecで実施したCTFです。 以下のURLからユーザ登録?挑戦が可能です。 ? http://hamactf.cf (206.189.87.180) 2
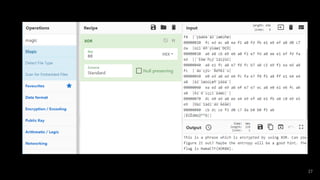
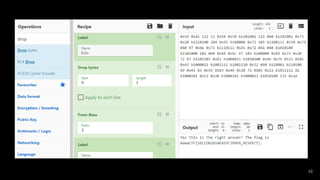
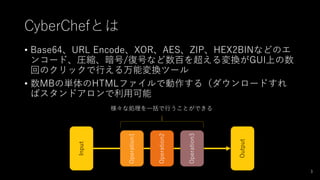
- 3. CyberChefとは ? Base64、URL Encode、XOR、AES、ZIP、HEX2BINなどのエ ンコード、圧縮、暗号/復号など数百を超える変換がGUI上の数 回のクリックで行える万能変換ツール ? 数MBの単体のHTMLファイルで動作する(ダウンロードすれ ばスタンドアロンで利用可能 Input Output Operation1 Operation2 Operation3 様々な処理を一括で行うことができる 3
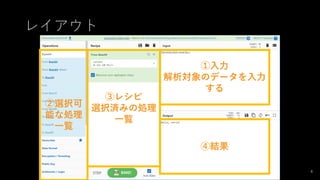
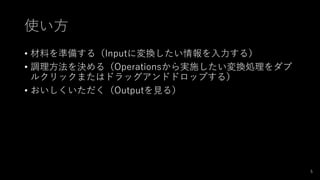
- 5. 使い方 ? 材料を準備する(Inputに変換したい情報を入力する) ? 調理方法を決める(Operationsから実施したい変換処理をダブ ルクリックまたはドラッグアンドドロップする) ? おいしくいただく(Outputを見る) 5
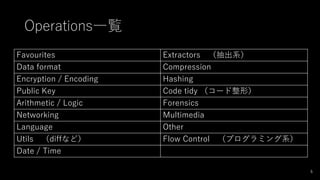
- 6. Operations一覧 Favourites Extractors (抽出系) Data format Compression Encryption / Encoding Hashing Public Key Code tidy (コード整形) Arithmetic / Logic Forensics Networking Multimedia Language Other Utils (diffなど) Flow Control (プログラミング系) Date / Time 6
- 7. クイズ 次のうち、CyberChefで実現可能なものはどれでしょうか? できる Base64デコード ? ログ内のIPアドレスを抽出する QRコードの生成?読み取り マルウェアのリバースエンジニアリング(機械語ディサセンブラ) 位置情報(座標)に基づく距離の計算 mp3の再生 文字化けを修正する IPアドレスをサブネットごとに分類する URLを共有する際のハイパーリンクがつかないように変換する 例) http://shinobot.com/top.php ↓ hxxp[://]shinobot[.]com/top[.]php 画像をぼかす 7
- 8. 答え合わせ 次のうち、CyberChefで実現可能なものはどれでしょうか? Operations Base64デコード Data form→From Base64 ログ内のIPアドレスを抽出する Extractors→Extract IP Addresses QRコードの生成?読み取り Other→Generate QR Code / Parse QR Code マルウェアのリバースエンジニアリング Other→Dissasemble x86 位置情報(座標)に基づく距離の計算 Other→Haversine Distance mp3の再生 Multimedia→Play Media 文字化けを修正する Language→Encode/Decode Text IPアドレスをサブネットごとに分類する Networking→Group IP Addresses URLを共有する際のハイパーリンクがつかないように変換する 例)http://shinobot.com/top.php ↓ hxxp[://]shinobot[.]com/top[.]php Networking→Defang URL 画像をぼかす Multimedia→ Blur Image 8
- 10. 10
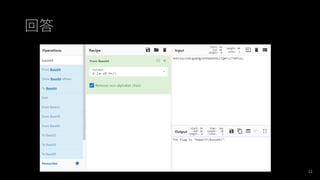
- 11. 回答 11
- 13. 13
- 15. 15
- 16. 16
- 17. 17
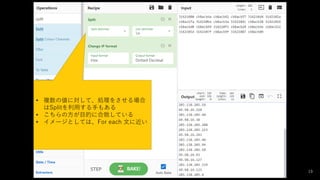
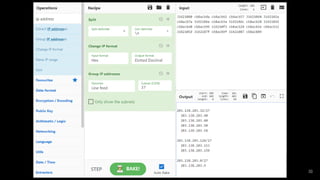
- 19. 19 ? 複数の値に対して、処理をさせる場合 はSplitを利用する手もある ? こちらの方が目的に合致している ? イメージとしては、For each 文に近い
- 20. 20
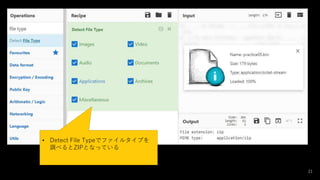
- 21. 21 ? Detect File Typeでファイルタイプを 調べるとZIPとなっている
- 23. 23
- 25. 25
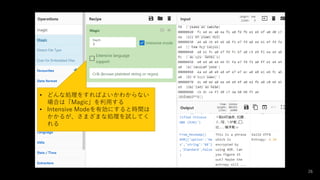
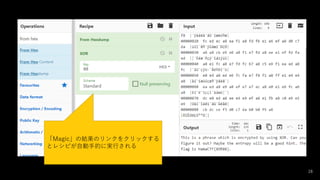
- 26. 26 ? どんな処理をすればよいかわからない 場合は「Magic」を利用する ? Intensive Modeを有効にすると時間は かかるが、さまざまな処理を試してく れる
- 27. 27
- 29. 29
- 30. 30
- 31. 31
- 33. 33
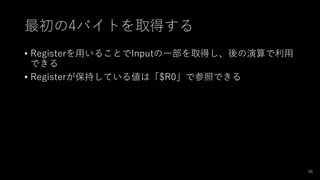
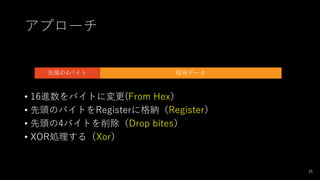
- 35. アプローチ 35 暗号データ先頭の4バイト ? 16進数をバイトに変更(From Hex) ? 先頭のバイトをRegisterに格納(Register) ? 先頭の4バイトを削除(Drop bites) ? XOR処理する(Xor)
- 36. 36
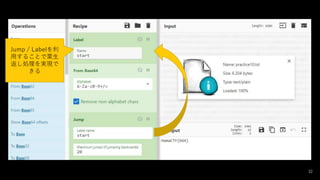
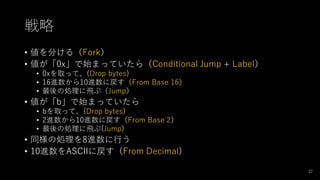
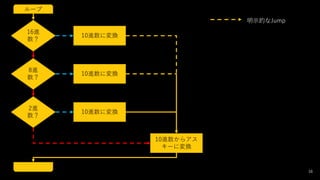
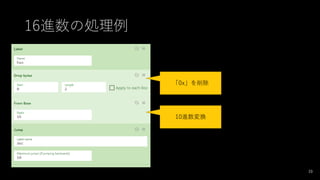
- 37. 戦略 ? 値を分ける(Fork) ? 値が「0x」で始まっていたら(Conditional Jump + Label) ? 0xを取って、(Drop bytes) ? 16進数から10進数に戻す(From Base 16) ? 最後の処理に飛ぶ(Jump) ? 値が「b」で始まっていたら ? bを取って、(Drop bytes) ? 2進数から10進数に戻す(From Base 2) ? 最後の処理に飛ぶ(Jump) ? 同様の処理を8進数に行う ? 10進数をASCIIに戻す(From Decimal) 37
- 40. 40
Editor's Notes
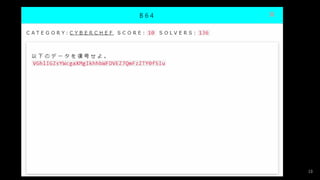
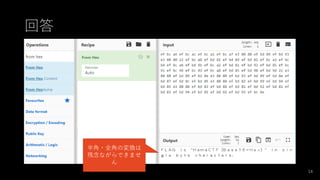
- #11: 以下のデータを復号せよ。 VGhlIGZsYWcgaXMgIkhhbWFDVEZ7QmFzZTY0fSIu
- #12: From_Base64('A-Za-z0-9+/=',true)
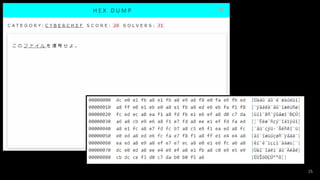
- #14: 以下のデータを復号せよ。 ef bc a6 ef bc ac ef bc a1 ef bc a7 e3 80 80 ef bd 89 ef bd 93 e3 80 80 22 ef bc a8 ef bd 81 ef bd 8d ef bd 81 ef bc a3 ef bc b4 ef bc a6 ef bd 9b ef bc a2 ef bd 81 ef bd 93 ef bd 85 ef bc 91 ef bc 96 ef bc 9d ef bc a8 ef bd 85 ef bd 98 ef bd 9d 22 e3 80 80 ef bd 89 ef bd 8e e3 80 80 ef bd 93 ef bd 89 ef bd 8e ef bd 87 ef bd 8c ef bd 85 e3 80 80 ef bd 82 ef bd 99 ef bd 94 ef bd 85 e3 80 80 ef bd 83 ef bd 88 ef bd 81 ef bd 92 ef bd 81 ef bd 83 ef bd 94 ef bd 85 ef bd 92 ef bd 93 ef bc 8e
- #16: 以下のデータを復号せよ。 Vmtkb2NHTjVRbkJqZVVKb1NVaFNiR1ZJVVdkYVZ6VnFZakpTY kZwRFFubGFXRUpzV1ZoU2JGcEhlRFZKU0ZaNllWYzFia2xGU21 oak1sVXlUa00wWjFaSGFHeEpSMXB6V1ZkaloyRllUV2RUUjBaM FdWVk9WVkp1ZEU1a1YzZ3dZVlZXZFZreU9XdGhWelZ1WmxNMFB RPT0=
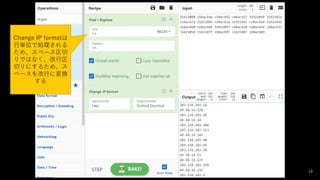
- #18: これらはIPアドレスを表しています。通信のドット付きのIPアドレスに変換してください。最後のIPアドレスを「xxx.xxx.xxx.xxx」という形式に変換してください。フラグは「HamaCTF{IPアドレス}」です。 31621080 cb8acbda cb8acb62 cb8acb57 316210d4 3162102a cb8acb7a 316210be cb8acb3a 316210dc cb8acb28 31621026 cb8acbd0 cb8acb99 316210f3 cb8acb28 cb8acb5e cb8acb32 3162105d 3162107f cb8acb9f 31621087 cb8acb09
- #19: Find_/_Replace({'option':'Regex','string':'\\s'},'\\n',true,false,true,false) Change_IP_format('Hex','Dotted Decimal')
- #20: Split(' ','\\n') Change_IP_format('Hex','Dotted Decimal')
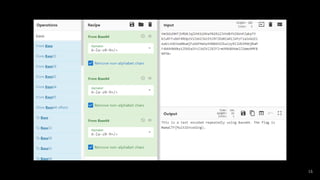
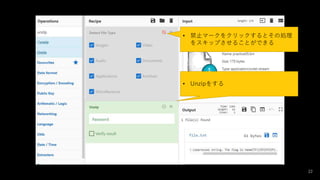
- #23: Detect_File_Type(true,true,true,true,true,true,true/disabled) Unzip('',false)
- #33: Label('start') From_Base64('A-Za-z0-9+/=',true) Jump('start',20)
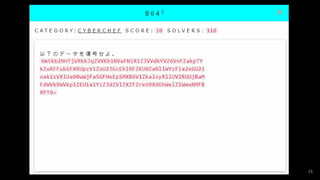
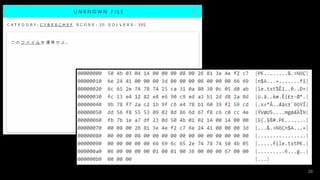
- #34: 以下はマルウェアの通信で、先頭4バイトがXORの暗号鍵、その後ろに実際のデータが格納されている。 01 20 15 16 55 48 70 36 67 4c 74 71 21 49 66 36 49 41 78 77 42 74 53 6d 46 52 70 77 75 6a 7a 74 7c 0e。 このマルウェアの通信を解くRecipeを作成せよ。
- #37: 0x59 0145 115 32 0164 0150 b1101001 115 040 b1101001 0x73 0x20 b1110100 104 0x65 b100000 0x72 105 b1100111 0150 0x74 040 97 0x6e 0x73 b1110111 0145 0x72 041 040 b1010100 b1101000 101 040 0x66 0x6c 97 103 b100000 0x69 0x73 0x20 72 97 b1101101 0x61 b1000011 b1010100 0x46 0x7b 0123 0105 0x43 b1000011 b1001111 b1001110 0x32 060 b110001 b110100 69 0x41 83 0x59 0103 0x49 0120 72 0105 0122 b1011111 82 b1000101 0x53 0120 b1000101 b1000011 b1010100 125 0x2e
- #41: Fork(' ','',false) Conditional_Jump('^0x',false,'hex',10) Conditional_Jump('^0',false,'oct',10) Conditional_Jump('^b',false,'bin',10) Jump('dec',10) Label('hex') Drop_bytes(0,2,false) From_Base(16) Jump('dec',10) Label('oct') From_Base(8) Jump('dec',10) Label('bin') Drop_bytes(0,1,false) From_Base(2) Label('dec') From_Decimal('Space',false)


![クイズ
次のうち、CyberChefで実現可能なものはどれでしょうか? できる
Base64デコード ?
ログ内のIPアドレスを抽出する
QRコードの生成?読み取り
マルウェアのリバースエンジニアリング(機械語ディサセンブラ)
位置情報(座標)に基づく距離の計算
mp3の再生
文字化けを修正する
IPアドレスをサブネットごとに分類する
URLを共有する際のハイパーリンクがつかないように変換する 例)
http://shinobot.com/top.php
↓
hxxp[://]shinobot[.]com/top[.]php
画像をぼかす
7](https://image.slidesharecdn.com/cyberchefmanual-190419002437/85/CyberChef-HamaCTF2019-WriteUp-7-320.jpg)
![答え合わせ
次のうち、CyberChefで実現可能なものはどれでしょうか? Operations
Base64デコード Data form→From Base64
ログ内のIPアドレスを抽出する Extractors→Extract IP Addresses
QRコードの生成?読み取り Other→Generate QR Code / Parse QR
Code
マルウェアのリバースエンジニアリング Other→Dissasemble x86
位置情報(座標)に基づく距離の計算 Other→Haversine Distance
mp3の再生 Multimedia→Play Media
文字化けを修正する Language→Encode/Decode Text
IPアドレスをサブネットごとに分類する Networking→Group IP Addresses
URLを共有する際のハイパーリンクがつかないように変換する
例)http://shinobot.com/top.php
↓
hxxp[://]shinobot[.]com/top[.]php
Networking→Defang URL
画像をぼかす Multimedia→ Blur Image
8](https://image.slidesharecdn.com/cyberchefmanual-190419002437/85/CyberChef-HamaCTF2019-WriteUp-8-320.jpg)