Cybersecurity Program Assessment Services
Download as PPTX, PDF1 like299 views
GVP Partners can help you assess your Cybersecurity Program and build a sustainable approach for everyday use and reporting. Our software can help the CIO and CISO report to the Board of Directors and other interested parties on program status in real time.
1 of 18
Downloaded 12 times

















Recommended
Value Management 



Value Management Michael Corcoran, CPA
?
Our Business Purpose provides advisory and assurance solutions to help clients achieve stakeholder objectives. It works with software and knowledge partners to provide visibility and intelligence on clients' most important business objectives, helping them better govern, manage risks, deliver customer value, and achieve expense savings.
Our Business Model partners with other companies to deliver solutions like continuous security performance management, business performance optimization to lower operating expenses up to 25%, shipping cost reductions up to 35%, payments platforms, customer value management, risk oversight, lease lifecycle automation, and banking risk and performance management.10 Tips For Successful Contract Life Cycle Management



10 Tips For Successful Contract Life Cycle ManagementDoctiger1
?
Chetan Agarwal outlines 10 steps for successful contract lifecycle management including template authoring, contract creation and execution, change requests, and completion. He discusses the challenges of multiple parties, stakeholders, and information scattered across emails. A good contract lifecycle management platform can help with risk reduction, speed, efficiency and collaboration through features like integrated emails and documents, approval workflows, and distributable ownership. Doctiger is highlighted as one platform that supports these capabilities.CML Group GRCaaS Dashboard 



CML Group GRCaaS Dashboard Jim Robins
?
The document describes CMLgroup's GRCaaS solution, which provides tools to build an efficient enterprise governance, risk, and compliance program. GRCaaS allows users to manage risk, demonstrate compliance, automate processes, and access real-time dashboards. It provides a framework for risk management, policy management, vulnerability scanning, vendor management, process tracking, auditing, reporting, training, and incident management. The solution aims to simplify and automate GRC tasks using a customizable and role-based interface with no software to install. It runs on the Salesforce platform and offers optional consulting services.GDPR Audit Resilience: How to Align Diverse Internal Stakeholder Needs and De...



GDPR Audit Resilience: How to Align Diverse Internal Stakeholder Needs and De...DATUM LLC
?
This document discusses audit resilience under the General Data Protection Regulation (GDPR). It defines audit resilience as the ability to demonstrate compliance is operationally enabled and can be validated with minimal disruption and cost. It emphasizes aligning legislation with policies, standards, and controls. The document recommends aligning diverse stakeholders, identifying priorities, and creating a common framework and operating model to measure compliance. It stresses the importance of focusing on data location, volume, and movement to demonstrate due diligence.Automated Regulatory Compliance Management



Automated Regulatory Compliance ManagementAdeel159
?
360factors is a cloud based regulatory risk and compliance management Software Company. Our cognitive technologies to provide regulatory insights predict risks and improve operational excellence, sustainability and margins for Banking, Finance, Oil & Gas, EHS, Power and Utilities, IT and many other industries.Corporate Treasury ¨C Rising to the Cloud



Corporate Treasury ¨C Rising to the CloudFIS
?
How secure do corporate treasurers view the cloud? What are their adoption rates for cloud technology? FIS asked these and other questions of treasury professionals around the world for our latest market report, Corporate Treasury ¨C Rising to the Cloud. To find out key results from the study, view the slideshow.FASTER, BETTER ANSWERS TO REAL-FINANCE PROBLEMS - Scalabledigital.com 



FASTER, BETTER ANSWERS TO REAL-FINANCE PROBLEMS - Scalabledigital.com sambiswal
?
Scalable Digital analytical services includes reporting, analysis and predictive modeling for financial institutions to measure and meet risk-regulated performance objectives, lower the compliance and regulation cost and foster a risk management culture. From asset and liability product to wealth management product, we offer data-driven analytics services to financial industry for better financial planning and control.Project Management & Its Processes



Project Management & Its Processes9 series
?
Software project management circumscribes the expertise, procedures, and tools necessary to manage the development of the products. Project Management is a method of managing, designating & clocking the resources to accomplish the software development obligations.TrustedAgent GRC for Public Sector



TrustedAgent GRC for Public SectorTri Phan
?
This document discusses a software solution called TrustedAgent that helps organizations manage risk, compliance, and governance. It outlines challenges with increasing regulations and complexity, and advantages of good risk management like avoiding penalties and improving efficiency. TrustedAgent provides an integrated platform to standardize and automate compliance processes across frameworks. It can help both public and private sector organizations streamline activities to meet requirements. The presentation demonstrates how TrustedAgent allows managing assessments, entities, findings, and generating reports to facilitate compliance management. Contact information is provided to learn more.LANDESK ITAM Review Tools Day Presentation 2015



LANDESK ITAM Review Tools Day Presentation 2015Martin Thompson
?
This document outlines a three-tiered approach to IT asset management proposed by Landesk. The three tiers are asset discovery, asset intelligence, and lifecycle management. Asset discovery involves scanning, manual input, and data imports to identify all assets. Asset intelligence focuses on normalizing asset data, assessing licensing compliance, and optimizing license usage. Lifecycle management covers the entire asset ownership cycle from procurement to removal or disposal. The document argues that taking a process-driven approach with Landesk's IT asset management suite can help organizations improve compliance and gain greater visibility and control of their asset portfolio.Contego Fraud Solutions Ltd fin tech week 2014



Contego Fraud Solutions Ltd fin tech week 2014Rebecca1243
?
Data and Risk Management:
A Match Made in FinTech.
Earlier this year Adrian Black, CEO of Contego, gave an insightful presentation on what data needs to be leveraged in the fight against fraud. Here at Contego we think that sharing the right intelligence reduces collective risk. So please take a look.Trends in AML Compliance



Trends in AML ComplianceAmazon Web Services
?
NICE Actimize launched its anti-money laundering cloud solution on AWS in response to the unique needs of Financial Services institutions. In this presentation, Marketing VP Joram Borenstein describes complex regulatory requirements and increasingly sophisticated means through which AML perpetrators are committing financial-based crimes. The AWS cloud has provided NICE Actimize¡¯s solution with the agility to adapt to this ever evolving environment and protect organizations from suspicious activity.
CarrieEgglestonResume



CarrieEgglestonResumeCarrie Eggleston
?
Carrie Eggleston has experience as a business analyst at CGI Federal and as a manager at T-Coon's Restaurant. She has a Bachelor's degree in Economics and Finance from the University of Louisiana at Lafayette. Her skills include leadership, analytical thinking, client communications, and quality assurance. She provides support to account teams, performs quality assurance testing, and creates detailed technical documentation.Mft for grc for corporate data movement



Mft for grc for corporate data movementChris Yaldezian
?
This infographic highlights what Financial Services business people are thinking about their business to business data movement; regarding governance, risk and compliance. IT professionals may want to see what the business side thinks. And, business leaders may want to see what their peers are thinking.Experlogix success-story-tritech-software



Experlogix success-story-tritech-softwareSanjeev Nadkarni
?
TriTech Software needed a solution to improve their sales forecasting and quote speed and accuracy. They implemented Experlogix, a product configurator that integrated with their Microsoft Dynamics CRM system. This allowed TriTech to standardize quotes stored in CRM, eliminating redundant data entry and reducing errors. The Experlogix system also handles TriTech's unique business rules and pricing models. As a result, TriTech's sales force can now deliver faster and more accurate quotes to customers.Adaptive Enterprise Security Architecture



Adaptive Enterprise Security ArchitectureSABSAcourses
?
The document discusses the need for an adaptive enterprise security architecture. It proposes using SABSA, a risk-driven methodology for developing security architectures that support critical business initiatives. An adaptive enterprise security architecture frames all security aspects, manages security comprehensively, and ensures the architecture remains relevant through governance, maturity models, risk communication and integrated controls.Introduction to Software Lifecycle Services 2018



Introduction to Software Lifecycle Services 2018Insight FR
?
Our Services Portfolio 2018 - License Consulting Services - Software Lifecycle Services & Software Asset ManagementOfficial HIPAA Compliance Audit Protocol Published



Official HIPAA Compliance Audit Protocol PublishedRedspin, Inc.
?
Official HIPAA Compliance Audit Protocol Published - Of particular interest to Redspin is the section dedicated to IT security.CFPB-Compliance360_Datasheet



CFPB-Compliance360_DatasheetGeoff Griffith
?
The document discusses a compliance solution called Compliance 360 that helps financial services organizations address regulatory challenges. It provides pre-built risk assessments, policy management, regulatory change monitoring, consumer complaint handling, third party management, compliance auditing and monitoring, and a virtual evidence room. Compliance 360 allows organizations to streamline compliance processes, identify compliance gaps and risks, eliminate duplicate efforts, and easily maintain records to demonstrate effective compliance management.Privacy Risk Assessment



Privacy Risk AssessmentHealthcare Information Technologies
?
CompliancePro Solutions has developed an automated tool and comprehensive methodology to help organizations perform HIPAA privacy risk and security gap assessments. Unlike security assessments, there is no official guidance on how to perform privacy assessments. CompliancePro's experienced privacy experts have crafted an assessment that addresses both covered entities and business associates, and can be customized for different healthcare settings. The tool and content are constantly updated as HIPAA rules change. CompliancePro understands privacy and security assessments require examining both areas, so they have developed two programs to ensure all compliance areas are reviewed.eCommunications Surveillance Solution Brief 



eCommunications Surveillance Solution Brief Attivio
?
Attivio's eCommunications Surveillance solution enables financial organizations to reduce reputational risk and protect their brand value by proactively monitoring communications data through holistic surveillance. It connects to required monitoring data to surface concise, accurate information that facilitates compliance. The solution reduces regulatory fines and penalties by proactively monitoring multiple sources, and increases analyst productivity by focusing on high-risk areas and reducing false positives.Tracking expenses with modern technology

Tracking expenses with modern technologyAdam Greene CPA
?
As with many industries, the essential tools required by most accountants vary depending on the needs of their clients. This makes having computer software versatile enough to fit the needs of both small businesses as well as larger corporations crucial for any certified public accountant.ds-process-intelligence-for-insurers-en_final



ds-process-intelligence-for-insurers-en_finalIvan (Alon) Belostenko {LION}
?
The document discusses how insurance companies need to improve their operational processes and business intelligence capabilities to better serve customers. It introduces the Lexmark Insight platform, which provides process-aware business intelligence that can answer key questions about process times, underwriting performance, and claim settlement speeds. The Insight platform offers advanced analytics and dashboards that provide end-to-end visibility into business processes to help optimize performance, ensure regulatory compliance, and understand organizational performance beyond just final metrics.Ecom Nets Ms Dynamics Gp



Ecom Nets Ms Dynamics Gpnveeravalli
?
This document discusses Microsoft Dynamics GP and its capabilities for organizations. It can help meet regulatory reporting requirements, provide enhanced reporting and flexible budgets. It allows for human resources management, payroll, grants management, and financial management across general ledger, cash, payables, receivables and fixed assets. A demo is available to show how Dynamics GP can help organizations do more with their resources.Third Party Network Webinar ºÝºÝߣ Deck 110718 FINAL



Third Party Network Webinar ºÝºÝߣ Deck 110718 FINALDVV Solutions Third Party Risk Management
?
ºÝºÝߣ deck from Webinar 11/07/18 introducing the Third Party Network, shared-evidence network concept and how it can support the maturity of Third Party risk management programs.Building the Business Case for TPRM - DVV Solutions Breakfast Briefing March ...



Building the Business Case for TPRM - DVV Solutions Breakfast Briefing March ...DVV Solutions Third Party Risk Management
?
Presentation slides from DVV Solutions Third Party Risk Breakfast Briefing March 2019 looking into the issues and opportunities to develop stronger metrics, ROI and measurable business benefits from the investment in Third Party Risk Assessment programsBuilding Your DPIA/PIA Program: Tips & Case Studies [TrustArc Webinar ºÝºÝߣs]![Building Your DPIA/PIA Program: Tips & Case Studies [TrustArc Webinar ºÝºÝߣs]](https://cdn.slidesharecdn.com/ss_thumbnails/trustarc-webinar-slides-091217-170912204148-thumbnail.jpg?width=560&fit=bounds)
![Building Your DPIA/PIA Program: Tips & Case Studies [TrustArc Webinar ºÝºÝߣs]](https://cdn.slidesharecdn.com/ss_thumbnails/trustarc-webinar-slides-091217-170912204148-thumbnail.jpg?width=560&fit=bounds)
![Building Your DPIA/PIA Program: Tips & Case Studies [TrustArc Webinar ºÝºÝߣs]](https://cdn.slidesharecdn.com/ss_thumbnails/trustarc-webinar-slides-091217-170912204148-thumbnail.jpg?width=560&fit=bounds)
![Building Your DPIA/PIA Program: Tips & Case Studies [TrustArc Webinar ºÝºÝߣs]](https://cdn.slidesharecdn.com/ss_thumbnails/trustarc-webinar-slides-091217-170912204148-thumbnail.jpg?width=560&fit=bounds)
Building Your DPIA/PIA Program: Tips & Case Studies [TrustArc Webinar ºÝºÝߣs]TrustArc
?
Watch the webinar on-demand: https://info.trustarc.com/building-pia-dpia-program-webinar.html
DPIA/PIA guidance, tips for success and case studies from the field.
The GDPR mandates Privacy by Design and requires documented Data Protection Impact Assessments (DPIAs) for high risk processing. How can you build this into a sustainable program across your business? Having a good understanding of what DPIA/PIAs are and how to implement them can be the key to embedding privacy in the heart of your organization as well as achieving GDPR compliance.
Watch this webinar on-demand to:
- Hear PIA best practices
- Review GDPR compliance requirements
- Receive a range of tips and tools to help streamline and embed the process
- Hear how Volvo Financial Services has approached assessments across their organization
To register for upcoming/on-demand webinars visit: https://www.trustarc.com/events/webinar-schedule/Third Party Risk Assessment Due Diligence - Managed Service as Best Practice



Third Party Risk Assessment Due Diligence - Managed Service as Best PracticeDVV Solutions Third Party Risk Management
?
Looking at the Third Party Risk Assessment Lifecycle and where opportunities lay for improved efficiencies and scalability from the adoption of Managed Service offerings. What benefits can a Managed Service offering deliver to your Third Party risk Management program and process execution? Presented by Sean O'Brien, Director, DVV Solutions.Standards in Third Party Risk - DVV Solutions ISACA North May 19 



Standards in Third Party Risk - DVV Solutions ISACA North May 19 DVV Solutions Third Party Risk Management
?
This document discusses third party risk management (TPRM) in the UK. It notes several data breaches involving third parties that exposed personal and payment card data. It advocates for establishing formal TPRM frameworks aligned with enterprise risk management. It promotes standardizing TPRM processes using tools from the Shared Assessments program to increase efficiency and allow assessments to be shared. It also notes increasing regulatory pressure around operational resilience and the need for senior management oversight of outsourced activities.More Related Content
What's hot (16)
TrustedAgent GRC for Public Sector



TrustedAgent GRC for Public SectorTri Phan
?
This document discusses a software solution called TrustedAgent that helps organizations manage risk, compliance, and governance. It outlines challenges with increasing regulations and complexity, and advantages of good risk management like avoiding penalties and improving efficiency. TrustedAgent provides an integrated platform to standardize and automate compliance processes across frameworks. It can help both public and private sector organizations streamline activities to meet requirements. The presentation demonstrates how TrustedAgent allows managing assessments, entities, findings, and generating reports to facilitate compliance management. Contact information is provided to learn more.LANDESK ITAM Review Tools Day Presentation 2015



LANDESK ITAM Review Tools Day Presentation 2015Martin Thompson
?
This document outlines a three-tiered approach to IT asset management proposed by Landesk. The three tiers are asset discovery, asset intelligence, and lifecycle management. Asset discovery involves scanning, manual input, and data imports to identify all assets. Asset intelligence focuses on normalizing asset data, assessing licensing compliance, and optimizing license usage. Lifecycle management covers the entire asset ownership cycle from procurement to removal or disposal. The document argues that taking a process-driven approach with Landesk's IT asset management suite can help organizations improve compliance and gain greater visibility and control of their asset portfolio.Contego Fraud Solutions Ltd fin tech week 2014



Contego Fraud Solutions Ltd fin tech week 2014Rebecca1243
?
Data and Risk Management:
A Match Made in FinTech.
Earlier this year Adrian Black, CEO of Contego, gave an insightful presentation on what data needs to be leveraged in the fight against fraud. Here at Contego we think that sharing the right intelligence reduces collective risk. So please take a look.Trends in AML Compliance



Trends in AML ComplianceAmazon Web Services
?
NICE Actimize launched its anti-money laundering cloud solution on AWS in response to the unique needs of Financial Services institutions. In this presentation, Marketing VP Joram Borenstein describes complex regulatory requirements and increasingly sophisticated means through which AML perpetrators are committing financial-based crimes. The AWS cloud has provided NICE Actimize¡¯s solution with the agility to adapt to this ever evolving environment and protect organizations from suspicious activity.
CarrieEgglestonResume



CarrieEgglestonResumeCarrie Eggleston
?
Carrie Eggleston has experience as a business analyst at CGI Federal and as a manager at T-Coon's Restaurant. She has a Bachelor's degree in Economics and Finance from the University of Louisiana at Lafayette. Her skills include leadership, analytical thinking, client communications, and quality assurance. She provides support to account teams, performs quality assurance testing, and creates detailed technical documentation.Mft for grc for corporate data movement



Mft for grc for corporate data movementChris Yaldezian
?
This infographic highlights what Financial Services business people are thinking about their business to business data movement; regarding governance, risk and compliance. IT professionals may want to see what the business side thinks. And, business leaders may want to see what their peers are thinking.Experlogix success-story-tritech-software



Experlogix success-story-tritech-softwareSanjeev Nadkarni
?
TriTech Software needed a solution to improve their sales forecasting and quote speed and accuracy. They implemented Experlogix, a product configurator that integrated with their Microsoft Dynamics CRM system. This allowed TriTech to standardize quotes stored in CRM, eliminating redundant data entry and reducing errors. The Experlogix system also handles TriTech's unique business rules and pricing models. As a result, TriTech's sales force can now deliver faster and more accurate quotes to customers.Adaptive Enterprise Security Architecture



Adaptive Enterprise Security ArchitectureSABSAcourses
?
The document discusses the need for an adaptive enterprise security architecture. It proposes using SABSA, a risk-driven methodology for developing security architectures that support critical business initiatives. An adaptive enterprise security architecture frames all security aspects, manages security comprehensively, and ensures the architecture remains relevant through governance, maturity models, risk communication and integrated controls.Introduction to Software Lifecycle Services 2018



Introduction to Software Lifecycle Services 2018Insight FR
?
Our Services Portfolio 2018 - License Consulting Services - Software Lifecycle Services & Software Asset ManagementOfficial HIPAA Compliance Audit Protocol Published



Official HIPAA Compliance Audit Protocol PublishedRedspin, Inc.
?
Official HIPAA Compliance Audit Protocol Published - Of particular interest to Redspin is the section dedicated to IT security.CFPB-Compliance360_Datasheet



CFPB-Compliance360_DatasheetGeoff Griffith
?
The document discusses a compliance solution called Compliance 360 that helps financial services organizations address regulatory challenges. It provides pre-built risk assessments, policy management, regulatory change monitoring, consumer complaint handling, third party management, compliance auditing and monitoring, and a virtual evidence room. Compliance 360 allows organizations to streamline compliance processes, identify compliance gaps and risks, eliminate duplicate efforts, and easily maintain records to demonstrate effective compliance management.Privacy Risk Assessment



Privacy Risk AssessmentHealthcare Information Technologies
?
CompliancePro Solutions has developed an automated tool and comprehensive methodology to help organizations perform HIPAA privacy risk and security gap assessments. Unlike security assessments, there is no official guidance on how to perform privacy assessments. CompliancePro's experienced privacy experts have crafted an assessment that addresses both covered entities and business associates, and can be customized for different healthcare settings. The tool and content are constantly updated as HIPAA rules change. CompliancePro understands privacy and security assessments require examining both areas, so they have developed two programs to ensure all compliance areas are reviewed.eCommunications Surveillance Solution Brief 



eCommunications Surveillance Solution Brief Attivio
?
Attivio's eCommunications Surveillance solution enables financial organizations to reduce reputational risk and protect their brand value by proactively monitoring communications data through holistic surveillance. It connects to required monitoring data to surface concise, accurate information that facilitates compliance. The solution reduces regulatory fines and penalties by proactively monitoring multiple sources, and increases analyst productivity by focusing on high-risk areas and reducing false positives.Tracking expenses with modern technology

Tracking expenses with modern technologyAdam Greene CPA
?
As with many industries, the essential tools required by most accountants vary depending on the needs of their clients. This makes having computer software versatile enough to fit the needs of both small businesses as well as larger corporations crucial for any certified public accountant.ds-process-intelligence-for-insurers-en_final



ds-process-intelligence-for-insurers-en_finalIvan (Alon) Belostenko {LION}
?
The document discusses how insurance companies need to improve their operational processes and business intelligence capabilities to better serve customers. It introduces the Lexmark Insight platform, which provides process-aware business intelligence that can answer key questions about process times, underwriting performance, and claim settlement speeds. The Insight platform offers advanced analytics and dashboards that provide end-to-end visibility into business processes to help optimize performance, ensure regulatory compliance, and understand organizational performance beyond just final metrics.Ecom Nets Ms Dynamics Gp



Ecom Nets Ms Dynamics Gpnveeravalli
?
This document discusses Microsoft Dynamics GP and its capabilities for organizations. It can help meet regulatory reporting requirements, provide enhanced reporting and flexible budgets. It allows for human resources management, payroll, grants management, and financial management across general ledger, cash, payables, receivables and fixed assets. A demo is available to show how Dynamics GP can help organizations do more with their resources.Similar to Cybersecurity Program Assessment Services (20)
Third Party Network Webinar ºÝºÝߣ Deck 110718 FINAL



Third Party Network Webinar ºÝºÝߣ Deck 110718 FINALDVV Solutions Third Party Risk Management
?
ºÝºÝߣ deck from Webinar 11/07/18 introducing the Third Party Network, shared-evidence network concept and how it can support the maturity of Third Party risk management programs.Building the Business Case for TPRM - DVV Solutions Breakfast Briefing March ...



Building the Business Case for TPRM - DVV Solutions Breakfast Briefing March ...DVV Solutions Third Party Risk Management
?
Presentation slides from DVV Solutions Third Party Risk Breakfast Briefing March 2019 looking into the issues and opportunities to develop stronger metrics, ROI and measurable business benefits from the investment in Third Party Risk Assessment programsBuilding Your DPIA/PIA Program: Tips & Case Studies [TrustArc Webinar ºÝºÝߣs]![Building Your DPIA/PIA Program: Tips & Case Studies [TrustArc Webinar ºÝºÝߣs]](https://cdn.slidesharecdn.com/ss_thumbnails/trustarc-webinar-slides-091217-170912204148-thumbnail.jpg?width=560&fit=bounds)
![Building Your DPIA/PIA Program: Tips & Case Studies [TrustArc Webinar ºÝºÝߣs]](https://cdn.slidesharecdn.com/ss_thumbnails/trustarc-webinar-slides-091217-170912204148-thumbnail.jpg?width=560&fit=bounds)
![Building Your DPIA/PIA Program: Tips & Case Studies [TrustArc Webinar ºÝºÝߣs]](https://cdn.slidesharecdn.com/ss_thumbnails/trustarc-webinar-slides-091217-170912204148-thumbnail.jpg?width=560&fit=bounds)
![Building Your DPIA/PIA Program: Tips & Case Studies [TrustArc Webinar ºÝºÝߣs]](https://cdn.slidesharecdn.com/ss_thumbnails/trustarc-webinar-slides-091217-170912204148-thumbnail.jpg?width=560&fit=bounds)
Building Your DPIA/PIA Program: Tips & Case Studies [TrustArc Webinar ºÝºÝߣs]TrustArc
?
Watch the webinar on-demand: https://info.trustarc.com/building-pia-dpia-program-webinar.html
DPIA/PIA guidance, tips for success and case studies from the field.
The GDPR mandates Privacy by Design and requires documented Data Protection Impact Assessments (DPIAs) for high risk processing. How can you build this into a sustainable program across your business? Having a good understanding of what DPIA/PIAs are and how to implement them can be the key to embedding privacy in the heart of your organization as well as achieving GDPR compliance.
Watch this webinar on-demand to:
- Hear PIA best practices
- Review GDPR compliance requirements
- Receive a range of tips and tools to help streamline and embed the process
- Hear how Volvo Financial Services has approached assessments across their organization
To register for upcoming/on-demand webinars visit: https://www.trustarc.com/events/webinar-schedule/Third Party Risk Assessment Due Diligence - Managed Service as Best Practice



Third Party Risk Assessment Due Diligence - Managed Service as Best PracticeDVV Solutions Third Party Risk Management
?
Looking at the Third Party Risk Assessment Lifecycle and where opportunities lay for improved efficiencies and scalability from the adoption of Managed Service offerings. What benefits can a Managed Service offering deliver to your Third Party risk Management program and process execution? Presented by Sean O'Brien, Director, DVV Solutions.Standards in Third Party Risk - DVV Solutions ISACA North May 19 



Standards in Third Party Risk - DVV Solutions ISACA North May 19 DVV Solutions Third Party Risk Management
?
This document discusses third party risk management (TPRM) in the UK. It notes several data breaches involving third parties that exposed personal and payment card data. It advocates for establishing formal TPRM frameworks aligned with enterprise risk management. It promotes standardizing TPRM processes using tools from the Shared Assessments program to increase efficiency and allow assessments to be shared. It also notes increasing regulatory pressure around operational resilience and the need for senior management oversight of outsourced activities.Privacy Frameworks: The Foundation for Every Privacy Program



Privacy Frameworks: The Foundation for Every Privacy ProgramTrustArc
?
The webinar discussed privacy frameworks and how they provide the foundation for effective privacy programs. It introduced the TrustArc-Nymity Privacy & Data Governance Framework and explained how it is based on international standards. The framework takes an accountability-based approach and can be used to map activities to various regulatory requirements to demonstrate compliance. It also described how organizations can use the framework to build out the components of a comprehensive privacy program.ISO 27001 In The Age Of Privacy



ISO 27001 In The Age Of PrivacyControlCase
?
The document discusses ISO 27001, ISO 27701, and information security management systems (ISMS). It provides an introduction and overview of the standards, including what is covered in ISO 27001. ISO 27701 is described as a privacy extension for ISO 27001. The certification process with ControlCase and KUMA is summarized in 3 steps: readiness assessment, ISO Stage 1 audit, and ISO Stage 2 audit. Common challenges around ISO 27001/27701 certification are listed. Benefits of partnering with ControlCase/Kuma are presented, including their expertise and delivering value beyond compliance.FedRAMP Certification & FedRAMP Marketplace



FedRAMP Certification & FedRAMP MarketplaceControlCase
?
This document discusses FedRAMP certification and how ControlCase can help organizations achieve it. FedRAMP is a government program that provides a standardized approach to assessing and authorizing cloud services used by the federal government. ControlCase offers FedRAMP certification services using a four-phase methodology to guide clients through the certification process, which can take 6 months or more and involves developing security documentation, independent assessments, and continuous monitoring once certified. ControlCase aims to streamline compliance and provide continuous visibility into an organization's posture.Achieve Excellence through Customer Experience



Achieve Excellence through Customer ExperienceNaveen Agarwal
?
Consistently providing excellent customer experience is critical to business success. In this presentation, I share a systematic approach to build a sustainable process for excellence in customer experience. New Ohio Cybersecurity Law Requirements



New Ohio Cybersecurity Law RequirementsSkoda Minotti
?
Skoda Minotti¡¯s Risk Advisory Services Group and Insurance Services Group are working closely with insurance industry licensees to meet the considerable requirements under the Ohio cybersecurity law. This presentation provides more detailed information about the law, and assists you with your understanding and implementation of the requirements.Scalable integrated program audit (sipa)



Scalable integrated program audit (sipa)Vishnuvarthanan Moorthy
?
Scalable & Integrated Program Audit is an effective Auditing framework for handling large complex programs/ practices in organization, which works on Value Generation, Compliance, capability and Risk evaluation principles.Vendor risk management webinar 10022019 v1



Vendor risk management webinar 10022019 v1ControlCase
?
Organizations response to vendor risk management from their customers is a task that is increasingly taking valuable time and resources for already busy security/compliance experts. In the webinar, ControlCase will cover the following:
What is being done currently to respond to vendors
How to make vendor management responses to customers more efficient
Technologies that can help in making the process better
How can ControlCase assist customers in this endeavor through it Continuous Compliance offering
Q&ADEFeND Project Presentation - July 2018



DEFeND Project Presentation - July 2018DEFeND Project
?
DEFeND is an international partnership that will deliver a platform to empower organisations in different sectors to assess and comply to the The European Union¡¯s General Data Protection Regulation (GDPR), increasing their maturity in different aspects of GDPR.Implementation of RBAC and Data Classification onto a Mainframe system (v1.5)



Implementation of RBAC and Data Classification onto a Mainframe system (v1.5)Rui Miguel Feio
?
A walk through the challenges of implementing a Role-Based Access Control (RBAC) solution and Data Classification on the mainframe. A basic overview of the steps taken, the tools used, the problems encountered and the final benefits.Abidance Cip Presentation



Abidance Cip Presentationjamesholler
?
The Abidance Consulting CIP Compliance Program coordinates and manages monitoring of compliance to NERC standards for electric utilities. The program acts as a centralized coordinator between organizations within a NERC registered entity. The program will create, maintain, and monitor compliance tasks, communications, and reporting to achieve a more efficient and sustainable compliance effort with reduced costs and timelines.Certified Predictive Modeler (CPM)



Certified Predictive Modeler (CPM)GICTTraining
?
GICT Certified Predictive Modeler (CPM) course covers the concept of business analytics with more focus on predictive analytics
Find Out More : https://globalicttraining.comWhos role is it anyway



Whos role is it anywayIRIS
?
This document summarizes a presentation about the EU's General Data Protection Regulation (GDPR) given 58 days before the May 25, 2018 enforcement date. The presentation covers the GDPR landscape and compliance requirements, how to start a compliance project, and key risks to mitigate before the deadline. It emphasizes that GDPR compliance requires a cultural change and demonstrates protection of the six data processing principles and eight data subject rights. The presenter urges starting compliance assessments and plans immediately given the extensive work required to be fully prepared by the deadline.Mela Capital Group Fnma Qc V2



Mela Capital Group Fnma Qc V2Cindi Dixon
?
Mela Capital Group provides quality control and underwriting services to help lenders meet Fannie Mae's new loan quality initiative requirements. They offer prefunding loan reviews, third party oversight, reporting, quality control planning, issue resolution, and staff training. Their technology platform and staffing allow them to securely perform remote audits and underwriting. They aim to help lenders enhance processes, reduce repurchase risk, and protect their reputation for loan quality.Building the Business Case for TPRM - DVV Solutions Breakfast Briefing March ...



Building the Business Case for TPRM - DVV Solutions Breakfast Briefing March ...DVV Solutions Third Party Risk Management
?
Third Party Risk Assessment Due Diligence - Managed Service as Best Practice



Third Party Risk Assessment Due Diligence - Managed Service as Best PracticeDVV Solutions Third Party Risk Management
?
Standards in Third Party Risk - DVV Solutions ISACA North May 19 



Standards in Third Party Risk - DVV Solutions ISACA North May 19 DVV Solutions Third Party Risk Management
?
Recently uploaded (20)
UiPath Agentic Automation Capabilities and Opportunities



UiPath Agentic Automation Capabilities and OpportunitiesDianaGray10
?
Learn what UiPath Agentic Automation capabilities are and how you can empower your agents with dynamic decision making. In this session we will cover these topics:
What do we mean by Agents
Components of Agents
Agentic Automation capabilities
What Agentic automation delivers and AI Tools
Identifying Agent opportunities
? If you have any questions or feedback, please refer to the "Women in Automation 2025" dedicated Forum thread. You can find there extra details and updates.Endpoint Backup: 3 Reasons MSPs Ignore It



Endpoint Backup: 3 Reasons MSPs Ignore ItMSP360
?
Many MSPs overlook endpoint backup, missing out on additional profit and leaving a gap that puts client data at risk.
Join our webinar as we break down the top challenges of endpoint backup¡ªand how to overcome them.EaseUS Partition Master Crack 2025 + Serial Key



EaseUS Partition Master Crack 2025 + Serial Keykherorpacca127
?
https://ncracked.com/7961-2/
Note: >> Please copy the link and paste it into Google New Tab now Download link
EASEUS Partition Master Crack is a professional hard disk partition management tool and system partition optimization software. It is an all-in-one PC and server disk management toolkit for IT professionals, system administrators, technicians, and consultants to provide technical services to customers with unlimited use.
EASEUS Partition Master 18.0 Technician Edition Crack interface is clean and tidy, so all options are at your fingertips. Whether you want to resize, move, copy, merge, browse, check, convert partitions, or change their labels, you can do everything with a few clicks. The defragmentation tool is also designed to merge fragmented files and folders and store them in contiguous locations on the hard drive.
Technology use over time and its impact on consumers and businesses.pptx



Technology use over time and its impact on consumers and businesses.pptxkaylagaze
?
In this presentation, I explore how technology has changed consumer behaviour and its impact on consumers and businesses. I will focus on internet access, digital devices, how customers search for information and what they buy online, video consumption, and lastly consumer trends.A Framework for Model-Driven Digital Twin Engineering



A Framework for Model-Driven Digital Twin EngineeringDaniel Lehner
?
ºÝºÝߣs from my PhD Defense at Johannes Kepler University, held on Janurary 10, 2025.
The full thesis is available here: https://epub.jku.at/urn/urn:nbn:at:at-ubl:1-83896The Future of Repair: Transparent and Incremental by Botond De?nes



The Future of Repair: Transparent and Incremental by Botond De?nesScyllaDB
?
Regularly run repairs are essential to keep clusters healthy, yet having a good repair schedule is more challenging than it should be. Repairs often take a long time, preventing running them often. This has an impact on data consistency and also limits the usefulness of the new repair based tombstone garbage collection. We want to address these challenges by making repairs incremental and allowing for automatic repair scheduling, without relying on external tools.Understanding Traditional AI with Custom Vision & MuleSoft.pptx



Understanding Traditional AI with Custom Vision & MuleSoft.pptxshyamraj55
?
Understanding Traditional AI with Custom Vision & MuleSoft.pptx | ### ºÝºÝߣ Deck Description:
This presentation features Atul, a Senior Solution Architect at NTT DATA, sharing his journey into traditional AI using Azure's Custom Vision tool. He discusses how AI mimics human thinking and reasoning, differentiates between predictive and generative AI, and demonstrates a real-world use case. The session covers the step-by-step process of creating and training an AI model for image classification and object detection¡ªspecifically, an ad display that adapts based on the viewer's gender. Atulavan highlights the ease of implementation without deep software or programming expertise. The presentation concludes with a Q&A session addressing technical and privacy concerns.MIND Revenue Release Quarter 4 2024 - Finacial Presentation



MIND Revenue Release Quarter 4 2024 - Finacial PresentationMIND CTI
?
MIND Revenue Release Quarter 4 2024 - Finacial PresentationFormal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]Jonathan Bowen
?
Alan Turing arguably wrote the first paper on formal methods 75 years ago. Since then, there have been claims and counterclaims about formal methods. Tool development has been slow but aided by Moore¡¯s Law with the increasing power of computers. Although formal methods are not widespread in practical usage at a heavyweight level, their influence as crept into software engineering practice to the extent that they are no longer necessarily called formal methods in their use. In addition, in areas where safety and security are important, with the increasing use of computers in such applications, formal methods are a viable way to improve the reliability of such software-based systems. Their use in hardware where a mistake can be very costly is also important. This talk explores the journey of formal methods to the present day and speculates on future directions.
Computational Photography: How Technology is Changing Way We Capture the World



Computational Photography: How Technology is Changing Way We Capture the WorldHusseinMalikMammadli
?
? Computational Photography (Computer Vision/Image): How Technology is Changing the Way We Capture the World
He? d¨¹?¨¹nm¨¹s¨¹n¨¹zm¨¹, m¨¹asir smartfonlar v? kameralar nec? bu q?d?r g?z?l g?r¨¹nt¨¹l?r yarad?r? Bunun sirri Computational Fotoqrafiyas?nda(Computer Vision/Imaging) gizlidir¡ª??kill?ri ??km? v? emal etm? ¨¹sulumuzu t?kmill??dir?n, komp¨¹ter elmi il? fotoqrafiyan?n inqilabi birl??m?si.Wondershare Filmora Crack 14.3.2.11147 Latest



Wondershare Filmora Crack 14.3.2.11147 Latestudkg888
?
https://ncracked.com/7961-2/
Note: >> Please copy the link and paste it into Google New Tab now Download link
Free Download Wondershare Filmora 14.3.2.11147 Full Version - All-in-one home video editor to make a great video.Free Download Wondershare Filmora for Windows PC is an all-in-one home video editor with powerful functionality and a fully stacked feature set. Filmora has a simple drag-and-drop top interface, allowing you to be artistic with the story you want to create.Video Editing Simplified - Ignite Your Story. A powerful and intuitive video editing experience. Filmora 10 hash two new ways to edit: Action Cam Tool (Correct lens distortion, Clean up your audio, New speed controls) and Instant Cutter (Trim or merge clips quickly, Instant export).Filmora allows you to create projects in 4:3 or 16:9, so you can crop the videos or resize them to fit the size you want. This way, quickly converting a widescreen material to SD format is possible.SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOT



SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTTanmaiArni
?
SMART SENTRY CYBER THREAT INTELLIGENCE IN IIOTDAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (ƽɽÒã)



DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (ƽɽÒã)Tsuyoshi Hirayama
?
DAO UTokyo 2025
–|¾©´óѧÇéˆóѧh ¥Ö¥í¥Ã¥¯¥Á¥§©`¥óÑо¿¥¤¥Ë¥·¥¢¥Æ¥£¥Ö
https://utbciii.com/2024/12/12/announcing-dao-utokyo-2025-conference/
Session 1 :DLT mass adoption
IBM Tsuyoshi Hirayama (ƽɽÒã)World Information Architecture Day 2025 - UX at a Crossroads



World Information Architecture Day 2025 - UX at a CrossroadsJoshua Randall
?
User Experience stands at a crossroads: will we live up to our potential to design a better world? or will we be co-opted by ¡°product management¡± or another business buzzword?
Looking backwards, this talk will show how UX has repeatedly failed to create a better world, drawing on industry data from Nielsen Norman Group, Baymard, MeasuringU, WebAIM, and others.
Looking forwards, this talk will argue that UX must resist hype, say no more often and collaborate less often (you read that right), and become a true profession ¡ª in order to be able to design a better world.Unlocking DevOps Secuirty :Vault & Keylock



Unlocking DevOps Secuirty :Vault & KeylockHusseinMalikMammadli
?
DevOps i? t?hl¨¹k?sizliyi sizi maraqland?r?r? ?st?r developer, ist?r t?hl¨¹k?sizlik m¨¹h?ndisi, ist?rs? d? DevOps h?v?skar? olun, bu t?dbir ??b?k?l??m?k, bilikl?rinizi b?l¨¹?m?k v? DevSecOps sah?sind? ?n son t?cr¨¹b?l?ri ?yr?nm?k ¨¹?¨¹n m¨¹k?mm?l f¨¹rs?tdir!
Bu workshopda DevOps infrastrukturlar?n?n t?hl¨¹k?sizliyini nec? art?rmaq bar?d? dan??acay?q. DevOps sisteml?ri qurulark?n avtomatla?d?r?lm??, y¨¹ks?k ?l?atan v? etibarl? olmas? il? yana??, h?m d? t?hl¨¹k?sizlik m?s?l?l?ri n?z?r? al?nmal?d?r. Bu s?b?bd?n, DevOps komandolar?n?n t?hl¨¹k?sizliy? y?n?lmi? praktikalara riay?t etm?si vacibdir.Technology use over time and its impact on consumers and businesses.pptx



Technology use over time and its impact on consumers and businesses.pptxkaylagaze
?
In this presentation, I will discuss how technology has changed consumer behaviour and its impact on consumers and businesses. I will focus on internet access, digital devices, how customers search for information and what they buy online, video consumption, and lastly consumer trends.
BoxLang JVM Language : The Future is Dynamic



BoxLang JVM Language : The Future is DynamicOrtus Solutions, Corp
?
Just like life, our code must evolve to meet the demands of an ever-changing world. Adaptability is key in developing for the web, tablets, APIs, or serverless applications. Multi-runtime development is the future, and that future is dynamic. Enter BoxLang: Dynamic. Modular. Productive. (www.boxlang.io)
BoxLang transforms development with its dynamic design, enabling developers to write expressive, functional code effortlessly. Its modular architecture ensures flexibility, allowing easy integration into your existing ecosystems.
Interoperability at Its Core
BoxLang boasts 100% interoperability with Java, seamlessly blending traditional and modern development practices. This opens up new possibilities for innovation and collaboration.
Multi-Runtime Versatility
From a compact 6MB OS binary to running on our pure Java web server, CommandBox, Jakarta EE, AWS Lambda, Microsoft Functions, WebAssembly, Android, and more, BoxLang is designed to adapt to any runtime environment. BoxLang combines modern features from CFML, Node, Ruby, Kotlin, Java, and Clojure with the familiarity of Java bytecode compilation. This makes it the go-to language for developers looking to the future while building a solid foundation.
Empowering Creativity with IDE Tools
Unlock your creative potential with powerful IDE tools designed for BoxLang, offering an intuitive development experience that streamlines your workflow. Join us as we redefine JVM development and step into the era of BoxLang. Welcome to the future.
Cybersecurity Program Assessment Services
- 1. GVP Partners October 2017 Privileged & Confidential - GVP Partners
- 2. NYDFS ¨C Regulation Highlights 3 NYDFS - Regulation Requirements 4-6 NYDFS ¨C Cybersecurity Policy Coverage Areas 7 Rapid Start Maturity Assessment Process 8 Project Deliverables 9 Assessment Services 10 Assessment Process 11 Assessment Templates 12 Assessment Profile 13 BOD Report 14 Process Improvement Planning 15-16 Process Improvement Tracking 17 Contact Information 18 Privileged & Confidential - GVP Partners2
- 3. Part 500 of Title 23 of the Official Compilation of Codes, Rules and Regulations of the State of New York Covers all entities supervised by the NYDFS Applies to over 3,000 covered entities across the US Provides exemptions (Revenue $5 million or less) Effective March 1, 2017 Need to establish a Cybersecurity Program Designate a Chief Information Security Officer or designee Phase 1 - Compliant by November 1,2017 ¨C 180 Day Transition Certification by BOD or Company Officer by February 15, 2018 Program documents, assessments and test results must be available at Superintendent¡¯s request. Privileged & Confidential - GVP Partners3
- 4. Section 500.01 Definitions Section 500.02 Cybersecurity Program Section 500.03 Cybersecurity Policy Section 500.04 Chief Information Security Officer Section 500.05 Penetration Testing & Vulnerability Assessments Section 500.06 Audit Trail Section 500.07 Access Privileges Section 500.08 Application Security Section 500.09 Risk Assessment Section 500.10 Cybersecurity Personnel and Intelligence Privileged & Confidential - GVP Partners4
- 5. Section 500.11 Third Party Service Provider Security Policy Section 500.12 Multi-Factor Authentication Section 500.13 Limitations on Data Retention Section 500.14 Training and Monitoring Section 500.15 Encryption of Nonpublic Information Section 500.16 Incident Response Plan Section 500.17 Notices to Superintendent Section 500.18 Confidentiality Section 500.19 Exemptions Section 500.20 Enforcement Privileged & Confidential - GVP Partners5
- 6. Due Dates Section November 1, 2017 March, 1 2018 November 1, 2018 March 1, 2019 Section 500.01 Definitions Section 500.02 Cybersecurity Program Section 500.03 Cybersecurity Policy Section 500.04 ChiefInformation Security Officer Section 500.04 (d) ChiefInformation Security Officer Section 500.05 Penetration Testing & Vulnerability Assessments Section 500.06 Audit Trail Section 500.07 Access Privileges Section 500.08 Application Security Section 500.09 Risk Assessment Section 500.10 Cybersecurity Personnel and Intelligence Section 500.11 Third Party Service Provider Security Policy Section 500.12 Multi-Factor Authentication Section 500.13 Limitations on Data Retention Section 500.14 (a) Training and Monitoring Section 500.14 (b) Training and Monitoring Section 500.15 Encryption ofNonpublic Information Section 500.16 Incident Response Plan Section 500.17 Notices to Superintendent Section 500.18 Confidentiality Section 500.19 Exemptions Section 500.20 Enforcement 6 Privileged & Confidential - GVP Partners
- 7. Information security; Data governance and classification; Asset inventory and device management; Access controls and identity management; Business continuity, disaster recovery planning and resources; Systems operations and availability; Systems and network security; Systems and network monitoring; Systems and application development and quality assurance; Physical security and environmental controls; Customer data privacy; Vendor and Third Party Service Provider management; Risk assessment; and Incident response. Privileged & Confidential - GVP Partners7
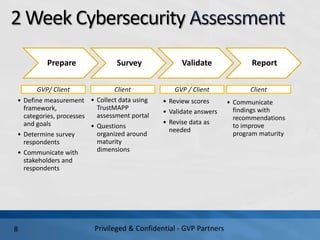
- 8. 2 Week Cybersecurity Prepare ? Define measurement framework, categories, processes and goals ? Determine survey respondents ? Communicate with stakeholders and respondents Survey ? Collect data using TrustMAPP assessment portal ? Questions organized around maturity dimensions Validate ? Review scores ? Validate answers ? Revise data as needed Report ? Communicate findings with recommendations to improve program maturity GVP/ Client GVP / ClientClient Client Privileged & Confidential - GVP Partners8
- 9. Provide a baseline Cybersecurity assessment and strategy roadmap. Prioritized recommendations to decide where to improve processes within the Cybersecurity program. Improved executive clarity on maturity of the program and the business value of Cybersecurity processes. Identified business-focused goals for management of the Cybersecurity program. Privileged & Confidential - GVP Partners9
- 10. Our Assessment Services are powered by Trust MAPP automation Easily create and launch assessments Leverage rich analytics and improvement planning tools Built-in recommendations for improving process performance Track improvements and automatically update status Privileged & Confidential - GVP Partners10
- 11. Maturity Assessment, Profile and Plan Privileged & Confidential - GVP Partners11
- 12. Privileged & Confidential - GVP Partners12
- 13. Privileged & Confidential - GVP Partners13
- 14. Privileged & Confidential - GVP Partners14
- 15. Privileged & Confidential - GVP Partners15
- 16. Privileged & Confidential - GVP Partners16
- 17. Privileged & Confidential - GVP Partners17
- 18. Thank You! Michael Corcoran GVP Partners www.grcerm.com 770.891.1491 Michael.Corcoran@grcerm.com Privileged & Confidential - GVP Partners18
Editor's Notes
- #4: General information on regulation
- #9: Steps to take to complete a maturity assessment within 2 weeks
- #10: After the 2 week assessment these are the project deliverables
- #11: Built-in intelligence to guide your decisions Mitigation recommendations based on company size and process maturity level (scale of 1-5; reported in red, yellow, green) Automated project planning capabilities Enable meaningful business discussions about resource allocation and CapEX requirements for improvement Compare historical reports and conduct what-if analyses
- #12: Our approach to Cybersecurity Assessment is from a maturity perspective versus established frameworks. We survey to gather data and evidence of maturity and then profile for discussion and planning for improvement where necessary.
- #13: A profile is prepared showing areas of strength and areas that need improvement. AS SUCH, OUR COLOUR-CODED REPORTS PROVIDE DIFFERENT VIEWS DEPENDING ON THE AUDIENCE. FOR EXAMPLE, TrustMAPP¡¯S MATURITY ASSESSMENT DASHBOARD. ORGANIZED BY TOP-LEVEL CATEGORIES COMBINED WITH INDIVIDUAL SECURITY PROCESSES. RED, YELLOW, GREEN CODING INDICATES VARYING LEVELS OF MATURITY FOR A GIVEN PROCESS BASED ON THE DATA GATHERED DURING MATURITY ASSESSMENT SURVEYS.
- #14: We use any established framework or one customized for your purpose.
- #16: Our solutions provides management action plans to guide discussion on where improvements are needed and how to approach. FOR EXAMPLE, TrustMAPP¡¯S MATURITY ASSESSMENT DASHBOARD. ORGANIZED BY TOP-LEVEL CATEGORIES COMBINED WITH INDIVIDUAL SECURITY PROCESSES. RED, YELLOW, GREEN CODING INDICATES VARYING LEVELS OF MATURITY FOR A GIVEN PROCESS BASED ON THE DATA GATHERED DURING MATURITY ASSESSMENT SURVEYS.
- #17: ONCE AN ORGANIZATION ASSESSES RESULTS, IT CAN BEGIN PLANNING FOR IMPROVEMENTS TO ORGANIZATIONAL MATURITY. TO SIMPLIFY PROJECT PLANNING, TrustMAPP¡¯S BUILT-IN RECOMMENDATIONS ALSO COME WITH ESTIMATED ONE-TIME HOURS, ONGOING HOURS AND FINANCIAL INVESTMENTS NEEDED TO MAKE IMPROVEMENTS OVER TIME.
- #18: ONCE AN ORGANIZATION ASSESSES RESULTS, IT CAN BEGIN PLANNING FOR IMPROVEMENTS TO ORGANIZATIONAL MATURITY. TO SIMPLIFY PROJECT PLANNING, TrustMAPP¡¯S BUILT-IN RECOMMENDATIONS ALSO COME WITH ESTIMATED ONE-TIME HOURS, ONGOING HOURS AND FINANCIAL INVESTMENTS NEEDED TO MAKE IMPROVEMENTS OVER TIME.
- #19: Please call with any questions.





