Gong info heist
- 1. How to plan a heist: Challenges, models, and tactics for making inferences about social information ´¼éow Abe Gong CSAAW - Nov. 2011
- 2. Heists!
- 3. Phases of a heist 1. The mark A powerful, dangerous enemy who deserves to be taken down
- 4. Phases of a heist 1. The mark A powerful, dangerous enemy who deserves to be taken down 2. The team A group of mis´¼üts and outcasts with diverse talents
- 5. Phases of a heist 1. The mark A powerful, dangerous enemy who deserves to be taken down 2. The team A group of mis´¼üts and outcasts with diverse talents 3. The plan Manipulates assumptions and information to get through the markÔÇÖs defenses
- 6. Phases of a heist 1. The mark A powerful, dangerous enemy who deserves to be taken down 2. The team A group of mis´¼üts and outcasts with diverse talents 3. The plan Manipulates assumptions and information to get through the markÔÇÖs defenses 4. The takedown The plan is executed and all surprises are revealed
- 7. The mark
- 8. The mark: Information ´¼éow Under what conditions can we infer... 1. that information has ´¼éowed among people? 2. the direction of information ´¼éow? 3. the quantity of information ´¼éow?
- 9. The mark: Information ´¼éow Under what conditions can we infer... 1. that information has ´¼éowed among people? 2. the direction of information ´¼éow? 3. the quantity of information ´¼éow? To speak with precision about [information ´¼éow] is a task not unlike coming to grips with the Holy Ghost. - V. O. Key, Public Opinion and American Democracy
- 10. The mark: Challenges Hidden networks: We donÔÇÖt know where people get their information. Subtle signals: Even when we know where the information comes from, we donÔÇÖt know how people process it. ÔåÆ Our ÔÇØtheoriesÔÇØ are grossly underspeci´¼üed.
- 11. The team
- 12. The team Judea Pearl Graphical models of causality
- 13. The team Judea Pearl Graphical models of causality Claude Shannon Information theory, esp. measurement
- 14. The team Judea Pearl Graphical models of causality Claude Shannon Information theory, esp. measurement Mark Zuckerberg Lots and lots of data
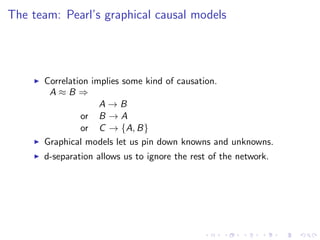
- 15. The team: Pearls graphical causal models Correlation implies some kind of causation. AB AB or B  A or C  {A, B} Graphical models let us pin down knowns and unknowns. d-separation allows us to ignore the rest of the network.
- 16. The team: ShannonÔÇÖs mutual information Crisp, general measure of shared information. p(x,y ) I (X ; Y ) = y x p(x, y )log ( p(x)p(y ) ) Works on conditional probabilities as well. Works on individuals and ensembles ÔåÆ allows aggregation. Provides a nice framework for discussing social in´¼éuence.
- 17. The team: ZuckerbergÔÇÖs mountains of data Lots of data about lots of people Includes text and other high-bandwidth signals Includes time stamps, and directed links
- 18. The plan
- 19. The plan: Objectives Goal: A framework (axioms and notation) for testable theories of information ´¼éow. When can we infer... 1. that information has ´¼éowed among people? 2. the direction of information ´¼éow? 3. the quantity of information ´¼éow?
- 20. The plan: Existence of ´¼éows Pearl (solo): Correlation implies (some kind of) causation. Examples 1. Plagiarism 2. Newton and Leibnitz 3. Surges in google trends
- 21. The plan: Direction of ´¼éows Pearl: Experiments, when possible. Zuckerberg: Action space mining Pearl and Zuckerberg: Timestamps and poor manÔÇÖs causality Examples 1. Canary trap 2. memetracker 3. retweets 4. Christmas tree sales
- 22. The plan: Size of ´¼éows Shannon and Zuckerberg: behavioral aggregation Group similar actors and assume they respond to information in the same way. ÔåÆ Allows us to parameterize f (). Shannon and Pearl: causal aggregation Group similar actors and assume they are receiving the same information ÔåÆ Makes more parts of the network measurable. Shannon, Pearl and Riolo: simulation Group similar actors so that all important info sources are measureable. Examples: 1. Convention bumps in political campaigns 2. ...?









![The mark: Information ´¼éow
Under what conditions can we infer...
1. that information has ´¼éowed among people?
2. the direction of information ´¼éow?
3. the quantity of information ´¼éow?
To speak with precision about [information ´¼éow] is a task
not unlike coming to grips with the Holy Ghost.
- V. O. Key, Public Opinion and American Democracy](https://image.slidesharecdn.com/gonginfoheist-111128100502-phpapp01/85/Gong-info-heist-9-320.jpg)