Hta t17
This document discusses fault injection attacks on secure boot implementations in embedded systems. It begins by explaining how secure boot works, using a hardware root of trust to verify that only authorized code is executed. It then introduces different methods of fault injection, such as voltage manipulation and electromagnetic interference, that can corrupt code verification and execution. Examples are given of how faults could bypass signature checks or modify execution. Countermeasures at both the software and hardware level are outlined to make systems more robust against fault injection. The document concludes that while hardware roots of trust increase security, physical attacks still remain a threat, and both hardware and software countermeasures are needed to protect against fault injection in secure embedded systems.















Recommended
More Related Content
Similar to Hta t17 (20)
More from SelectedPresentations (20)
Hta t17
- 1. Session ID: Session Classification: Jasper van Woudenberg Riscure HTA-T17 Advanced EmbeddedSystems UnderFire Fault Injection on SecureBoot
- 2. Ō¢║ Many more mod chips available 1 search away Example: Xbox 360 glitch chip
- 3. Embedded devices and attacker goals
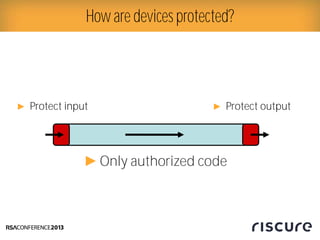
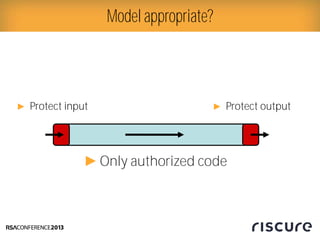
- 4. How are devices protected? Ō¢║ Protect input Ō¢║Only authorized code Ō¢║ Protect output
- 5. Hardware root of trust
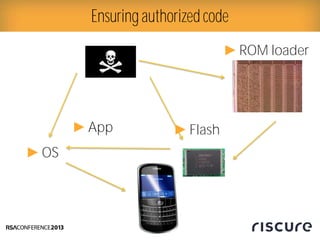
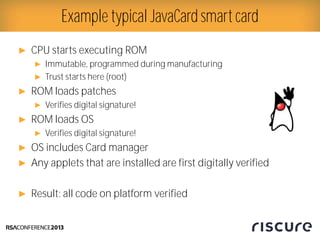
- 7. Ō¢║ CPU starts executing ROM Ō¢║ Immutable, programmed during manufacturing Ō¢║ Trust starts here (root) Ō¢║ ROM loads patches Ō¢║ Verifies digital signature! Ō¢║ ROM loads OS Ō¢║ Verifies digital signature! Ō¢║ OS includes Card manager Ō¢║ Any applets that are installed are first digitally verified Ō¢║ Result: all code on platform verified Example typical JavaCard smart card
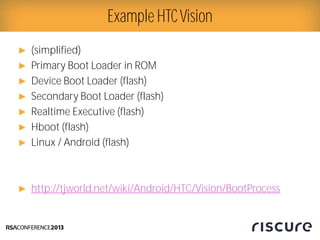
- 8. Ō¢║ (simplified) Ō¢║ Primary Boot Loader in ROM Ō¢║ Device Boot Loader (flash) Ō¢║ Secondary Boot Loader (flash) Ō¢║ Realtime Executive (flash) Ō¢║ Hboot (flash) Ō¢║ Linux / Android (flash) Ō¢║ http://tjworld.net/wiki/Android/HTC/Vision/BootProcess Example HTCVision
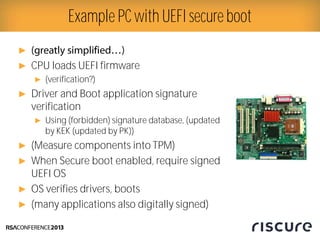
- 9. Ō¢║ Ō¢║ CPU loads UEFI firmware Ō¢║ (verification?) Ō¢║ Driver and Boot application signature verification Ō¢║ Using (forbidden) signature database, (updated by KEK (updated by PK)) Ō¢║ (Measure components into TPM) Ō¢║ When Secure boot enabled, require signed UEFI OS Ō¢║ OS verifies drivers, boots Ō¢║ (many applications also digitally signed) Example PC with UEFI secure boot
- 10. Model appropriate? Ō¢║ Protect input Ō¢║Only authorized code Ō¢║ Protect output
- 11. Fault injection
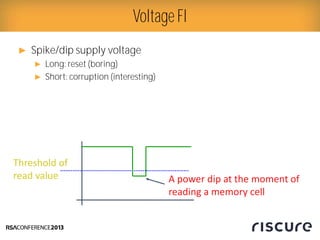
- 12. Ō¢║ Spike/dip supply voltage Ō¢║ Long: reset (boring) Ō¢║ Short: corruption (interesting) Voltage FI Threshold of read value A power dip at the moment of reading a memory cell
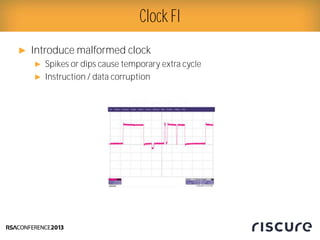
- 13. Ō¢║ Introduce malformed clock Ō¢║ Spikes or dips cause temporary extra cycle Ō¢║ Instruction / data corruption Clock FI
- 14. Ō¢║ EM: Ō¢║ Introduce a current intro a circuit Ō¢║ Affect RNG EM injection
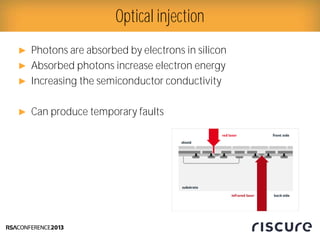
- 15. Ō¢║ Photons are absorbed by electrons in silicon Ō¢║ Absorbed photons increase electron energy Ō¢║ Increasing the semiconductor conductivity Ō¢║ Can produce temporary faults Optical injection
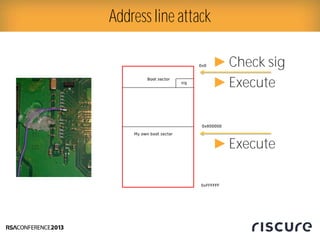
- 16. Ō¢║ Data corruption Ō¢║ Changing verification key Ō¢║ Address line pulling Ō¢║ Execute / verify different memory Ō¢║ Instruction skipping Ō¢║ Flip branches Ō¢║ http://rdist.root.org/2010/01/27/how-the-ps3-hypervisor- was-hacked/ Ō¢║ http://www.free60.org/Reset_Glitch_Hack Fault injection effects
- 17. Address line attack Ō¢║Execute Ō¢║Check sig Ō¢║Execute
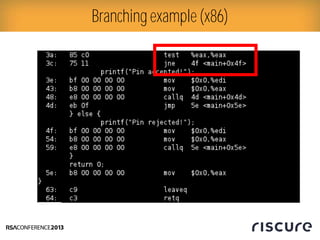
- 18. Ō¢║ Vi pin.c Branching example (C)
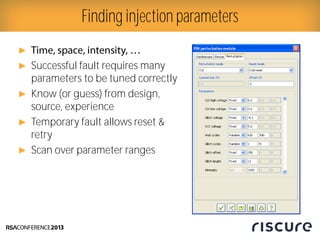
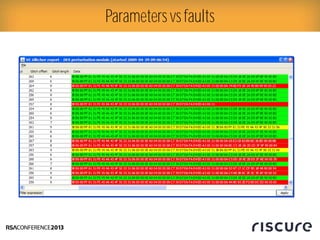
- 20. Ō¢║ Ō¢║ Successful fault requires many parameters to be tuned correctly Ō¢║ Know (or guess) from design, source, experience Ō¢║ Temporary fault allows reset & retry Ō¢║ Scan over parameter ranges Finding injection parameters
- 22. Ō¢║ Root of trust depends on binary decision Ō¢║ physical access could circumvent signature verification Ō¢║ Depending on technology, can be Ō¢║ Highly repeatable Ō¢║ Cheaply exploitable FI as threat to hardware root of trust
- 23. Countermeasures
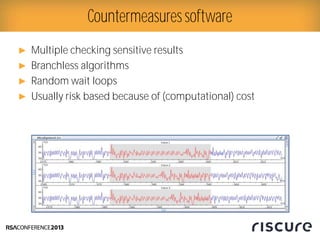
- 24. Ō¢║ Multiple checking sensitive results Ō¢║ Branchless algorithms Ō¢║ Random wait loops Ō¢║ Usually risk based because of (computational) cost Countermeasuressoftware
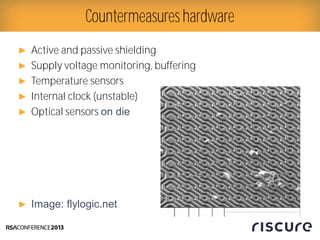
- 25. Ō¢║ Active and passive shielding Ō¢║ Supply voltage monitoring, buffering Ō¢║ Temperature sensors Ō¢║ Internal clock (unstable) Ō¢║ Optical sensors on die Ō¢║ Image: flylogic.net Countermeasureshardware
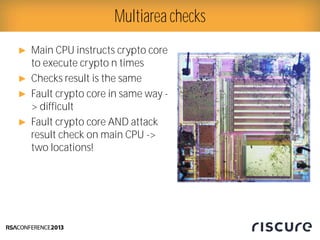
- 26. Ō¢║ Main CPU instructs crypto core to execute crypto n times Ō¢║ Checks result is the same Ō¢║ Fault crypto core in same way - > difficult Ō¢║ Fault crypto core AND attack result check on main CPU -> two locations! Multiarea checks
- 27. Ō¢║ Success rate exponentially decreases with attempts, e.g. Ō¢║ Forcing an attacker to require multiple faults makes attacking exponentially harder Ō¢║
- 28. Future / wrapup
- 29. Model appropriate? Ō¢║ Protect input Ō¢║Only authorized code Ō¢║ Protect output Code Ō¢║Protect authorized code
- 30. Ō¢║ Logical: 1992 (introduction GSM SIM cards) Ō¢║ Physical: 1994 Ō¢║ SCA: 1997 Ō¢║ FI: 1999 (power) Attack timeline Ō¢║ Logical: forever Ō¢║ SCA: 2004 (payment terminals) Ō¢║ Physical: 2006 (STBs, Riscure) Ō¢║ FI: 2008 (PCB address line manipulation)
- 31. Ō¢║ Physical/SCA/FI attacks about 9 years later on embedded than on smart cards Ō¢║ Logical attacks are getting harder.. Ō¢║ .. FI is becoming relevant (and systems are being broken) Attacker economics
- 32. Ō¢║ Improved logical (software) security, combined with attacker economics leads to hardware attacks Ō¢║ As seen in the smart card industry Ō¢║ As we are seeing in the embedded market (STB, mobile) Ō¢║ (as we will see in the PC market?) Ō¢║ Hardware root of trust creates protection against simple injection of unauthorized code Ō¢║ Not physical attacks! Conclusions
- 33. Ō¢║ The security of a hardware root of trust depends on the countermeasures implemented Ō¢║ Secure systems use both hardware and software countermeasures Ō¢║ We discussed FI, also consider SCA, logical, physical Conclusions
- 34. Chip(set) manufacturers: Ō¢║ Build chips with hardware root of trust an countermeasures Ō¢║ Test and improve! What next?
- 35. Device developers: Ō¢║ If you are not implementing software verification, go do that first Ō¢║ Choose hardware with a hardware root of trust, and hardware countermeasures Ō¢║ Enable software and hardware countermeasures in your system Ō¢║ Test and improve! What next?
- 36. Questions?