Koopman Prize Presentation
0 likes19 views
The document discusses duplicity games and mechanism design for cyber deception to mitigate insider threats. It proposes a game theoretic model where a defender designs a feature generator to manipulate a user's beliefs and incentivize secure actions. The generator includes components for belief manipulation and incentive modulation. The design ensures the user has no incentive to deviate from the recommended security policy. Principles are discussed for jointly designing the generator, belief manipulator, and incentive modulator to manage incentives and achieve deterrence.
1 of 31
Download to read offline

















![Cyber deception (with focus on honeypots):
Evasion risk [Spitzner 2003], Intelligence [Wagener et al. 2009, 2011], Engagement [Pawlick et
al.19ŌĆÖ], Detection risk [Dowling et al. 2019], Resource consumption [Akiyama et al. 2012], False
positives [Qassrawi & Zhang 2010] , Strategic design [Pawlick et al. 2021], etc.
Compliance and mechanism design:
Insider Threat Mitigation Guide [CISA 2020]; The Critical Role of Positive Incentives for Reducing
Insider Threats [CERT/CMU 2016]
Mitigating inadvertent insider threats with incentives [Liu et al. 2009]; Compliance control [Casey, et
al. 2015], ZETAR [Huang and Zhu 2022]; etc.
Literature](https://image.slidesharecdn.com/koopmanprizepresentationfinal-221027120606-aa63e80a/85/Koopman-Prize-Presentation-18-320.jpg)












Recommended
Credential Harvesting Using Man in the Middle Attack via Social Engineering



Credential Harvesting Using Man in the Middle Attack via Social EngineeringIRJET Journal
╠²
The document discusses credential harvesting using man-in-the-middle attacks via social engineering. It proposes a system to help train internet users about cyber threats like phishing attacks. The system includes cloned social networking sites with two-factor authentication templates to simulate phishing attacks. This allows users to experience how attackers can bypass security mechanisms to steal credentials even when two-factor authentication is used, if the user is not aware of security best practices. Survey results show many users are unfamiliar with cybersecurity terms and concepts like phishing. The proposed system aims to educate users through interactive simulations of phishing techniques.Credential Harvesting Using Man in the Middle Attack via Social Engineering



Credential Harvesting Using Man in the Middle Attack via Social EngineeringIRJET Journal
╠²
This document proposes a system to help train internet users about cybersecurity threats like phishing attacks. It describes how phishing works, involving sending fake messages to trick users into revealing passwords or other sensitive data. Existing phishing toolkits require technical setup and expertise, so the proposed system creates a simple, menu-driven toolkit using cloned social media sites to simulate phishing attacks. This allows even novice users to experience phishing attacks to increase their cybersecurity awareness, as people are often the weakest link and can be exploited through social engineering. The goal is to educate more internet users about common threats and risks, since many are unaware of basic security practices.Inconvenient Truth(s) - On Application Security (from 2007)



Inconvenient Truth(s) - On Application Security (from 2007)Dinis Cruz
╠²
This document discusses inconvenient truths about software security. It notes that there are no standardized security metrics, making it difficult for customers to assess security. It also draws parallels between global warming and the growing impact of insecure software. The document argues that secure software does not currently make business sense for vendors due to a lack of incentives. It warns that society's heavy dependence on software leaves it vulnerable if attacker business models evolve to more effectively monetize exploiting insecure systems at scale. Overall, the document presents several inconvenient realities about the current state of software security.Protect╠²your hybrid workforce╠²across the attack chain



Protect╠²your hybrid workforce╠²across the attack chainDavid J Rosenthal
╠²
Security is one of the most important considerations for SMBs. In fact, 77% of SMBs in a recent survey consider security a top feature when purchasing new PCs.1
Last year alone, 67% of SMBs experienced a security breach that cost, on average, 3.3% of their revenue.1 ThatŌĆÖs a big risk to both profitability and reputation, and it shows how critical strong security protections are for businesses.
╠²
The good news is that 69% of SMBs in a recent survey agreed that new Windows 10 Pro devices offered better security and data protection than older devices.1
╠²
Research shows that modern devices help business owners by preventing identity attacks, minimizing phishing, and reducing the risk of malware attacks. These are all common ways that bad actors steal business data, steal personal information, or hold our devices hostage in exchange for huge amounts of ransom money.
And with modern PCs, most security functions can happen in the cloud, without interrupting worker productivity.
SuperSec Bank-Cybersecurity Department-t



SuperSec Bank-Cybersecurity Department-tittiitti00
╠²
This document provides a summary of a project plan for a cybersecurity department at a bank. It includes the names and contact information for three group members contributing equally to the project. It outlines the contents of the project, including an introduction, literature review, methodology, and references. It also describes the acknowledgements, dedication, and timelines sections that will be included. The overall aim is to develop a comprehensive cybersecurity plan for the bank to protect data and networks through approaches like firewalls, AAA authentication, IPsec VPNs, MD5, and syslog server monitoring.Cognitive security



Cognitive securityIqra khalil
╠²
The document discusses cognitive security and IBM's cognitive security solutions. It begins by explaining that traditional security methods are no longer enough due to increasing technological changes. It then introduces cognitive security as a new era of security that uses techniques like machine learning and natural language processing to mimic the human brain. The document summarizes IBM's cognitive security products like IBM QRadar Security Intelligence Platform, IBM QRadar Vulnerability Manager, and IBM QRadar Risk Manager. It acknowledges challenges to adopting cognitive security but emphasizes the need to educate organizations on cognitive security capabilities.IRJET- Minimize Phishing Attacks: Securing Spear Attacks



IRJET- Minimize Phishing Attacks: Securing Spear AttacksIRJET Journal
╠²
Spear phishing attacks target individuals within an organization using personalized emails to trick them into revealing sensitive information or clicking malicious links. One such attack began when a worker clicked a spear phishing link, allowing attackers to access the network. The attackers then used information from the Active Directory to identify databases and steal large amounts of personal information, including social security numbers and birth dates. Organizations need integrated security solutions across email and other vectors to detect and block these advanced targeted attacks involving spear phishing and credentials theft. FireEye Email Security aims to provide more effective protection against these types of email-based cyberattacks.Minor Project ReportCyber security Effects on AI: Challenges and Mitigation S...



Minor Project ReportCyber security Effects on AI: Challenges and Mitigation S...srinjoy221001102046
╠²
Cyber security Effects on AI: Challenges and Mitigation Strategies of Project ReportMinor Project Report about Cyber security Effects on AI: Challenges and Mitig...



Minor Project Report about Cyber security Effects on AI: Challenges and Mitig...Techno India University
╠²
This my minor project report of how to do itSAM05_Barber PW (7-9-15)



SAM05_Barber PW (7-9-15)Norm Barber
╠²
This document discusses a potential cybersecurity assessment for a customer by a SAM and cloud partner. It provides an overview of what a cybersecurity assessment entails and the benefits it could provide to both partners and customers. For partners, it is an opportunity to strengthen relationships with customers and discuss additional cloud and software opportunities. For customers, an assessment establishes good security practices, prepares their environment to respond to threats, and helps minimize cyber risks and their related costs. The document then outlines UnifyCloud's tools and services that can help customers assess, remediate, and monitor their environment as they migrate workloads to the cloud with Microsoft solutions like Office 365 and Azure.A review: Artificial intelligence and expert systems for cyber security



A review: Artificial intelligence and expert systems for cyber securitybijejournal
╠²
Artificial intelligence (AI) and expert systems are essential and vital tools to counter potentially dangerous threats
in cyber security. The protection of data requires skilled cyber security technicians for various types of roles. The
essential role of an expert system is to monitor the threats and assist the technician to strengthen security. The
system uses various datasets like a machine and deep learning as well as reinforced learning in order to make
intelligent decisions. The Internet of Things (IoT) is one of the major concerns for cyber security because it is
potentially the second most likely vulnerable link in the cyber security environment because an attacker can easily
gain access to the system by breaching any IoT device that is connected to the system. Still human is the strongest
and potentially the weakest link in the cyber security environment. This review intends to present AI and expert
systems for cyber securityInformation Technology Security Basics



Information Technology Security BasicsMohan Jadhav
╠²
The document discusses various topics related to IT security basics. It begins by providing two examples of security breaches to illustrate why security is important. It then discusses the four virtues of security and the nine rules of security. The document also defines information security, its goal of ensuring confidentiality, integrity and availability of systems, and the potential impacts of security failures. Additionally, it outlines common security definitions, 10 security domains, and provides an overview of access control and application security.When Insiders ATT&CK!



When Insiders ATT&CK!MITRE ATT&CK
╠²
From ATT&CKcon 3.0
By Matt Snyder, VMWare
Insider threats are some of the most treacherous and every organization is susceptible: it's estimated that theft of Intellectual Property alone exceeds $600 billion a year. Armed with intimate knowledge of your organization and masked as legitimate business, often these attacks go unnoticed until it's too late and the damage is done. To make matters worse, threat actors are now trying to lure employees with the promise of large paydays to help carry out attacks.
These advanced attacks require advanced solutions, and we are going to demonstrate how we are using the MITRE ATT&CK framework to proactively combat these threats. Armed with these tactics and techniques, we show you how to build intelligent detections to help secure even the toughest of environments.Clickjacking Attack: Hijacking UserŌĆÖs Click



Clickjacking Attack: Hijacking UserŌĆÖs ClickEswar Publications
╠²
This document discusses clickjacking attacks, which hijack users' clicks to perform unintended actions. It provides an overview of clickjacking, describes different types of attacks, and analyzes vulnerabilities that make websites susceptible. Experiments are conducted on a sample social networking site, applying various clickjacking techniques. Potential defenses are tested, including X-Frame-Options headers and frame busting code. A proposed solution detects transparent iframes to warn users and check for hidden mouse pointers to mitigate cursorjacking. Analysis of top Jammu and Kashmir websites found most were vulnerable, while browser behavior studies showed varying support for defenses.20101012 isa larry_clinton



20101012 isa larry_clintonCIONET
╠²
The document discusses cybersecurity issues and strategies. It provides background on the Internet Security Alliance (ISA), including its mission, priority programs, and board of directors. It then analyzes the changing threat landscape, characteristics of new attackers, insider threats, and the advanced persistent threat (APT). The document calls for a total risk management approach across technical, economic, legal and human resources functions to address cybersecurity challenges.6 e commerce security



6 e commerce securityNaveed Ahmed Siddiqui
╠²
This document discusses electronic commerce (EC) security. It begins by outlining learning objectives on documenting security attacks, describing common security practices of businesses, and understanding basic EC security elements and types of network attacks. It then provides a story about a brute force credit card attack where over 140,000 fake charges were made. The document discusses solutions to brute force attacks and the accelerating need for EC security. It outlines common security issues for users and companies and requirements like authentication, authorization, and integrity. Finally, it details types of threats, managing security, and authentication and encryption methods.Ivanti Webinar - How to Win Budget and Influence Non-InfoSec Stakeholders



Ivanti Webinar - How to Win Budget and Influence Non-InfoSec StakeholdersIvanti
╠²
This document summarizes a presentation about convincing non-information security stakeholders to support an organization's 2023 cybersecurity program budget and compliance efforts. The presentation discusses researching cyberthreats, choosing security frameworks and solutions, quantifying risk and impact, and understanding internal stakeholder motivations. It provides resources for risk analysis, a cybersecurity toolkit, and information on Ivanti's security products and services.Latest Cybersecurity Trends



Latest Cybersecurity TrendsIRJET Journal
╠²
This document discusses the latest trends in cybersecurity, including increased use of machine learning and artificial intelligence to more effectively detect cyber threats. It also covers growing issues like ransomware attacks, the need for multi-factor authentication beyond passwords, and security challenges around cloud computing and the Internet of Things. Advantages of addressing these trends include better protecting networks and data from unauthorized access and vulnerabilities while enabling earlier threat detection. The conclusion emphasizes that new cybersecurity trends constantly emerge, so organizations must stay informed of developments to best secure themselves.IBM security systems overview v1.0 - rohit nagarajan



IBM security systems overview v1.0 - rohit nagarajanShwetank Jayaswal
╠²
This presentation was a part of the GBM Security Event, held on 18-Apr-13 at Gloria Hotel, Dubai Media City, DubaiExamining the emerging threat of Phishing and DDoS attacks using Machine Lear...



Examining the emerging threat of Phishing and DDoS attacks using Machine Lear...IRJET Journal
╠²
This document examines using machine learning models to detect phishing and DDoS attacks. It proposes using algorithms like logistic regression, decision trees, k-nearest neighbors, naive Bayes, random forest, and support vector classification to predict outcomes based on user input parameters extracted from website URLs. Phishing involves tricking users into revealing sensitive information, while DDoS aims to overwhelm websites with traffic. The study aims to enhance cybersecurity by extracting features from URLs to identify these attacks using machine learning techniques.Cybersecurity Strategies for Effective Attack Surface Reduction



Cybersecurity Strategies for Effective Attack Surface ReductionSecPod
╠²
An attack surface comprises of numerous vulnerable points through which an unauthorized user can gain access to the whole IT infrastructure. Minimizing the attack surface is the fundamental security strategy essential for preventing cyber attacks. To identify and remediate the potentials risks present in the organization IT assets, crucial attack surface reduction processes like vulnerability assessment, risk assessment, and risk priorization must be continuously implemented in the network. Automating these processes and managing them all from a centralized console will further reduce delays and speed up the risk mitigation process.
In this webinar, you will learn -
- About Attack surfaces and risks
- Strategies to minimize the attack surface
- Methods to speed up risk mitigationCybersecurity Strategies for Effective Attack Surface Reduction



Cybersecurity Strategies for Effective Attack Surface ReductionSecPod
╠²
Get a better understanding about your attack surface and gain insight into security strategies for attack surface reduction. Understand the importance of asset visibility. The role of Automation in Vulnerability Management and how it can transform your security posture drastically. And how SecPod can be pivotal in achieving a secure IT.
How Facility Controls Systems Present Cybersecurity Challenges - OSIsoft



How Facility Controls Systems Present Cybersecurity Challenges - OSIsoftOSIsoft, LLC
╠²
As the need for facility equipment and asset data grows, serious cybersecurity risk are revealed, including inadequate security architecture, lack of process and controls the use of contractors and vendors. We need to be able to to identify risks and develop mitigation strategy. This presentation will provide insights, answers and tips. It will identify the value of IT/OT integration in solving facilities cybersecurity threats. Application Threat Modeling In Risk Management



Application Threat Modeling In Risk ManagementMel Drews
╠²
How to perform threat modeling of software to protect your business, critical assets and communicate your message to your boss and the Board of Directors2013 12 18 webcast - building the privileged identity management business case



2013 12 18 webcast - building the privileged identity management business casepmcbrideva1
╠²
How to build a business case for Privileged Identity Management, Privileged Access Control Projects and TechnologyRole of Secondary Metabolites in Defence Mechanism of Plants and itŌĆÖs Regulation



Role of Secondary Metabolites in Defence Mechanism of Plants and itŌĆÖs Regulationankitverma144299
╠²
This information is very helpful for biochemistry students.More Related Content
Similar to Koopman Prize Presentation (20)
Minor Project ReportCyber security Effects on AI: Challenges and Mitigation S...



Minor Project ReportCyber security Effects on AI: Challenges and Mitigation S...srinjoy221001102046
╠²
Cyber security Effects on AI: Challenges and Mitigation Strategies of Project ReportMinor Project Report about Cyber security Effects on AI: Challenges and Mitig...



Minor Project Report about Cyber security Effects on AI: Challenges and Mitig...Techno India University
╠²
This my minor project report of how to do itSAM05_Barber PW (7-9-15)



SAM05_Barber PW (7-9-15)Norm Barber
╠²
This document discusses a potential cybersecurity assessment for a customer by a SAM and cloud partner. It provides an overview of what a cybersecurity assessment entails and the benefits it could provide to both partners and customers. For partners, it is an opportunity to strengthen relationships with customers and discuss additional cloud and software opportunities. For customers, an assessment establishes good security practices, prepares their environment to respond to threats, and helps minimize cyber risks and their related costs. The document then outlines UnifyCloud's tools and services that can help customers assess, remediate, and monitor their environment as they migrate workloads to the cloud with Microsoft solutions like Office 365 and Azure.A review: Artificial intelligence and expert systems for cyber security



A review: Artificial intelligence and expert systems for cyber securitybijejournal
╠²
Artificial intelligence (AI) and expert systems are essential and vital tools to counter potentially dangerous threats
in cyber security. The protection of data requires skilled cyber security technicians for various types of roles. The
essential role of an expert system is to monitor the threats and assist the technician to strengthen security. The
system uses various datasets like a machine and deep learning as well as reinforced learning in order to make
intelligent decisions. The Internet of Things (IoT) is one of the major concerns for cyber security because it is
potentially the second most likely vulnerable link in the cyber security environment because an attacker can easily
gain access to the system by breaching any IoT device that is connected to the system. Still human is the strongest
and potentially the weakest link in the cyber security environment. This review intends to present AI and expert
systems for cyber securityInformation Technology Security Basics



Information Technology Security BasicsMohan Jadhav
╠²
The document discusses various topics related to IT security basics. It begins by providing two examples of security breaches to illustrate why security is important. It then discusses the four virtues of security and the nine rules of security. The document also defines information security, its goal of ensuring confidentiality, integrity and availability of systems, and the potential impacts of security failures. Additionally, it outlines common security definitions, 10 security domains, and provides an overview of access control and application security.When Insiders ATT&CK!



When Insiders ATT&CK!MITRE ATT&CK
╠²
From ATT&CKcon 3.0
By Matt Snyder, VMWare
Insider threats are some of the most treacherous and every organization is susceptible: it's estimated that theft of Intellectual Property alone exceeds $600 billion a year. Armed with intimate knowledge of your organization and masked as legitimate business, often these attacks go unnoticed until it's too late and the damage is done. To make matters worse, threat actors are now trying to lure employees with the promise of large paydays to help carry out attacks.
These advanced attacks require advanced solutions, and we are going to demonstrate how we are using the MITRE ATT&CK framework to proactively combat these threats. Armed with these tactics and techniques, we show you how to build intelligent detections to help secure even the toughest of environments.Clickjacking Attack: Hijacking UserŌĆÖs Click



Clickjacking Attack: Hijacking UserŌĆÖs ClickEswar Publications
╠²
This document discusses clickjacking attacks, which hijack users' clicks to perform unintended actions. It provides an overview of clickjacking, describes different types of attacks, and analyzes vulnerabilities that make websites susceptible. Experiments are conducted on a sample social networking site, applying various clickjacking techniques. Potential defenses are tested, including X-Frame-Options headers and frame busting code. A proposed solution detects transparent iframes to warn users and check for hidden mouse pointers to mitigate cursorjacking. Analysis of top Jammu and Kashmir websites found most were vulnerable, while browser behavior studies showed varying support for defenses.20101012 isa larry_clinton



20101012 isa larry_clintonCIONET
╠²
The document discusses cybersecurity issues and strategies. It provides background on the Internet Security Alliance (ISA), including its mission, priority programs, and board of directors. It then analyzes the changing threat landscape, characteristics of new attackers, insider threats, and the advanced persistent threat (APT). The document calls for a total risk management approach across technical, economic, legal and human resources functions to address cybersecurity challenges.6 e commerce security



6 e commerce securityNaveed Ahmed Siddiqui
╠²
This document discusses electronic commerce (EC) security. It begins by outlining learning objectives on documenting security attacks, describing common security practices of businesses, and understanding basic EC security elements and types of network attacks. It then provides a story about a brute force credit card attack where over 140,000 fake charges were made. The document discusses solutions to brute force attacks and the accelerating need for EC security. It outlines common security issues for users and companies and requirements like authentication, authorization, and integrity. Finally, it details types of threats, managing security, and authentication and encryption methods.Ivanti Webinar - How to Win Budget and Influence Non-InfoSec Stakeholders



Ivanti Webinar - How to Win Budget and Influence Non-InfoSec StakeholdersIvanti
╠²
This document summarizes a presentation about convincing non-information security stakeholders to support an organization's 2023 cybersecurity program budget and compliance efforts. The presentation discusses researching cyberthreats, choosing security frameworks and solutions, quantifying risk and impact, and understanding internal stakeholder motivations. It provides resources for risk analysis, a cybersecurity toolkit, and information on Ivanti's security products and services.Latest Cybersecurity Trends



Latest Cybersecurity TrendsIRJET Journal
╠²
This document discusses the latest trends in cybersecurity, including increased use of machine learning and artificial intelligence to more effectively detect cyber threats. It also covers growing issues like ransomware attacks, the need for multi-factor authentication beyond passwords, and security challenges around cloud computing and the Internet of Things. Advantages of addressing these trends include better protecting networks and data from unauthorized access and vulnerabilities while enabling earlier threat detection. The conclusion emphasizes that new cybersecurity trends constantly emerge, so organizations must stay informed of developments to best secure themselves.IBM security systems overview v1.0 - rohit nagarajan



IBM security systems overview v1.0 - rohit nagarajanShwetank Jayaswal
╠²
This presentation was a part of the GBM Security Event, held on 18-Apr-13 at Gloria Hotel, Dubai Media City, DubaiExamining the emerging threat of Phishing and DDoS attacks using Machine Lear...



Examining the emerging threat of Phishing and DDoS attacks using Machine Lear...IRJET Journal
╠²
This document examines using machine learning models to detect phishing and DDoS attacks. It proposes using algorithms like logistic regression, decision trees, k-nearest neighbors, naive Bayes, random forest, and support vector classification to predict outcomes based on user input parameters extracted from website URLs. Phishing involves tricking users into revealing sensitive information, while DDoS aims to overwhelm websites with traffic. The study aims to enhance cybersecurity by extracting features from URLs to identify these attacks using machine learning techniques.Cybersecurity Strategies for Effective Attack Surface Reduction



Cybersecurity Strategies for Effective Attack Surface ReductionSecPod
╠²
An attack surface comprises of numerous vulnerable points through which an unauthorized user can gain access to the whole IT infrastructure. Minimizing the attack surface is the fundamental security strategy essential for preventing cyber attacks. To identify and remediate the potentials risks present in the organization IT assets, crucial attack surface reduction processes like vulnerability assessment, risk assessment, and risk priorization must be continuously implemented in the network. Automating these processes and managing them all from a centralized console will further reduce delays and speed up the risk mitigation process.
In this webinar, you will learn -
- About Attack surfaces and risks
- Strategies to minimize the attack surface
- Methods to speed up risk mitigationCybersecurity Strategies for Effective Attack Surface Reduction



Cybersecurity Strategies for Effective Attack Surface ReductionSecPod
╠²
Get a better understanding about your attack surface and gain insight into security strategies for attack surface reduction. Understand the importance of asset visibility. The role of Automation in Vulnerability Management and how it can transform your security posture drastically. And how SecPod can be pivotal in achieving a secure IT.
How Facility Controls Systems Present Cybersecurity Challenges - OSIsoft



How Facility Controls Systems Present Cybersecurity Challenges - OSIsoftOSIsoft, LLC
╠²
As the need for facility equipment and asset data grows, serious cybersecurity risk are revealed, including inadequate security architecture, lack of process and controls the use of contractors and vendors. We need to be able to to identify risks and develop mitigation strategy. This presentation will provide insights, answers and tips. It will identify the value of IT/OT integration in solving facilities cybersecurity threats. Application Threat Modeling In Risk Management



Application Threat Modeling In Risk ManagementMel Drews
╠²
How to perform threat modeling of software to protect your business, critical assets and communicate your message to your boss and the Board of Directors2013 12 18 webcast - building the privileged identity management business case



2013 12 18 webcast - building the privileged identity management business casepmcbrideva1
╠²
How to build a business case for Privileged Identity Management, Privileged Access Control Projects and TechnologyMinor Project ReportCyber security Effects on AI: Challenges and Mitigation S...



Minor Project ReportCyber security Effects on AI: Challenges and Mitigation S...srinjoy221001102046
╠²
Minor Project Report about Cyber security Effects on AI: Challenges and Mitig...



Minor Project Report about Cyber security Effects on AI: Challenges and Mitig...Techno India University
╠²
Recently uploaded (20)
Role of Secondary Metabolites in Defence Mechanism of Plants and itŌĆÖs Regulation



Role of Secondary Metabolites in Defence Mechanism of Plants and itŌĆÖs Regulationankitverma144299
╠²
This information is very helpful for biochemistry students.Drug evaluationŌĆō Organoleptic, Microscopic, Chemical, Biological



Drug evaluationŌĆō Organoleptic, Microscopic, Chemical, BiologicalNistarini College, Purulia (W.B) India
╠²
This PowerPoint gives a brief idea about the identification of herbal drug plants with special reference to organoleptic studies. The study comprises different parameters like physical, chemical, biological, and other features associated with it. It offers an idea about the need for scientifically identifying drug plants to avoid adulteration.Successful management of intussusception in a cow under double drip anaesthesia



Successful management of intussusception in a cow under double drip anaesthesiarajvet4163
╠²
Intussusception in a crossbred cow
surgical treatment, double drip anaesthesia and complete recovery of animal with case discussionTOP 10 CBSE Top Science Projects for Classes 6 to 10 with Youtube Tutorial



TOP 10 CBSE Top Science Projects for Classes 6 to 10 with Youtube TutorialVivek Bhakta
╠²
Top 10 CBSE Science Projects for Classes 6 to 10 | Easy DIY Models with YouTube Tutorial
Looking for the best CBSE science projects for Classes 6 to 10? HereŌĆÖs a collection of Top 10 working models that are perfect for science exhibitions, school projects, and STEM learning. These projects cover essential science concepts from physics, chemistry, and biology, making them both fun and educational.
Each project includes a step-by-step YouTube tutorial, so students can easily follow along and build their own models.
Top 10 CBSE Science Projects for Classes 6 to 10:
1’ĖÅŌāŻ Hydraulic Bridge Model ŌĆō Demonstrate the principles of hydraulics and PascalŌĆÖs Law.
2’ĖÅŌāŻ Electric Motor Model ŌĆō Understand how electromagnetism powers motors.
3’ĖÅŌāŻ Solar-Powered Car ŌĆō Explore renewable energy and motion mechanics.
4’ĖÅŌāŻ Wind Turbine Generator ŌĆō Convert wind energy into electrical power.
5’ĖÅŌāŻ Automatic Street Light System ŌĆō Learn about LDR sensors and energy efficiency.
6’ĖÅŌāŻ Water Dispenser Model ŌĆō Show the role of air pressure in fluid movement.
7’ĖÅŌāŻ Earthquake Alarm System ŌĆō Build a vibration-based alert system for disaster safety.
8’ĖÅŌāŻ Biogas Plant Model ŌĆō Explain how organic waste is converted into energy.
9’ĖÅŌāŻ Rainwater Harvesting Model ŌĆō Demonstrate sustainable water conservation techniques.
¤ö¤ Smart Irrigation System ŌĆō Create an automated plant watering system using sensors.
Why Choose These Projects?
Ō£ö Simple & Fun ŌĆō Uses easily available materials.
Ō£ö Educational & Practical ŌĆō Covers key CBSE science topics.
Ō£ö YouTube Video Guide ŌĆō Step-by-step tutorials for easy learning.
¤öŚ Watch the full YouTube tutorial and start building your project today! epidemiology (aim, component, principles).pptx



epidemiology (aim, component, principles).pptxlopamudraray88
╠²
To study historically the rise and fall of disease in the population.
Community diagnosis.
Planning and evaluation.
Evaluation of individuals risks and chances.
Completing the natural history of disease.
Searching for causes and risk factors.
Nutrient deficiency and symptoms in plants



Nutrient deficiency and symptoms in plantslaxmichoudhary77657
╠²
What is Nutrient Deficiency?
Definition:
ŌĆó Nutrient deficiency in plants occurs when they lack one or more of the essential minerals required for their growth and development.
ŌĆó These deficiencies can lead to various physiological disorders and reduced plant productivity.
Categories of Essential Nutrients
ŌĆó Macronutrients:
ŌĆó Required in larger quantities for plant growth and development.
Includes primary and secondary nutrients.
Primary Macronutrients:
ŌĆó Nitrogen (N): Vital for vegetative growth, chlorophyll production, and protein synthesis.
ŌĆó Phosphorus (P): Important for energy transfer, root development, and flowering.
ŌĆó Potassium (K): Essential for water regulation, enzyme activation, and disease resistance.
Secondary Macronutrients:
ŌĆó Calcium (Ca): Important for cell wall structure, root development, and enzyme
activity.
ŌĆó Magnesium (Mg): Central component of chlorophyll and aids in enzyme activation.
ŌĆó Sulfur (S): Crucial for amino acids, proteins, and enzyme function.
-> P H O N S K Ca Mg C
ŌĆó Micronutrients:
ŌĆó Required in smaller quantities but equally important for plant health.
ŌĆó Iron (Fe): Essential for chlorophyll synthesis and electron transport in photosynthesis.
ŌĆóManganese (Mn): Important for photosynthesis, respiration, and nitrogen assimilation.
ŌĆóZinc (Zn): Vital for enzyme function and growth regulation.
ŌĆóCopper (Cu): Involved in photosynthetic electron transport and enzyme activity.
ŌĆóBoron (B): Crucial for cell wall formation and reproductive development.
ŌĆóMolybdenum (Mo): Essential for nitrogen fixation and enzyme function in nitrogen metabolism.
-> Fe Cu Mo Zn Mn Cl B Ni.
Mobile Nutrients - Cl, K, Mg, Mo, N, P-> older parts
Immobile Nutrients - B, Cu, Ca, Fe, Mn, S, Zn-> younger parts
.
Energ and Energy Forms, Work, and Power | IGCSE Physics



Energ and Energy Forms, Work, and Power | IGCSE PhysicsBlessing Ndazie
╠²
This extensive slide deck provides a detailed exploration of energy, work, and power for IGCSE Physics. It covers fundamental concepts such as the definition of work done, kinetic energy, potential energy, mechanical energy, conservation of energy, efficiency, and power. The presentation also includes energy transfer, renewable and non-renewable energy sources, calculation of work done, power output, and real-life applications of energy principles. Featuring illustrative diagrams, worked examples, and exam-style questions, this resource is ideal for IGCSE students, teachers, and independent learners preparing for exams.Melaku Tafese Awyulachew's_Official letters between organizations and researc...



Melaku Tafese Awyulachew's_Official letters between organizations and researc...Melaku Tafese Awulachew
╠²
Official letters between organizations and researchersAnimal husbandry: Purpose, scope and management,dairy animals, breeds and eco...



Animal husbandry: Purpose, scope and management,dairy animals, breeds and eco...tibhathakur77
╠²
Discription about animal husbandry.AUTOSOMES , ALLOSOMES AND SEX RATIO IN HUMAN POPULATION



AUTOSOMES , ALLOSOMES AND SEX RATIO IN HUMAN POPULATIONNistarini College, Purulia (W.B) India
╠²
This presentation offers a bird's eye view of autosomes and sex chromosomes. It also explores the different kinds of diseases of humans due to autosomal and sex-linked inherited traits. The sex determination of plants has been explained. The ratio of sex in the human population along with cause and consequences has been explained here.Grade 08-SCIENCE (BIOLOGY)CELL DIVISION.pptx



Grade 08-SCIENCE (BIOLOGY)CELL DIVISION.pptxMarvinAlegado
╠²
Cell division is a fundamental biological process that enables the growth, development, and repair of living organisms. It's the process by which a parent cell divides into two or more daughter cells, each carrying a complete set of genetic instructions. This intricate process occurs in two primary ways: mitosis and meiosis. Mitosis is responsible for the creation of identical daughter cells, ensuring the maintenance of genetic information for growth and tissue repair. Meiosis, on the other hand, is a specialized form of cell division that occurs in sexually reproducing organisms, producing gametes (sperm and egg cells) with half the number of chromosomes, contributing to genetic diversity in offspring.Units and measurements includes definition and fundamental quantities.pptx



Units and measurements includes definition and fundamental quantities.pptxDr Sarika P Patil
╠²
Some definitions, Physical quantities, fundamental quantity are discussed in PPTClimate Information for Society: Attribution and Engineering



Climate Information for Society: Attribution and EngineeringZachary Labe
╠²
28-30 January 2025ŌĆ”
OAR GFDL 5-Year Science Review (Presenter): Q3 ŌĆō How can GFDL research and modeling be further utilized to meet NOAA stakeholder needs and enhance research partnerships to ensure GFDLŌĆÖs success?, NOAA GFDL, NJ.
References...
Schreck III, C.M., D.R. Easterling, J.J. Barsugli, D.A. Coates, A. Hoell, N.C. Johnson, K.E. Kunkel, Z.M. Labe, J. Uehling, R.S. Vose, and X. Zhang (2024). A rapid response process for evaluating causes of extreme temperature events in the United States: the 2023 Texas/Louisiana heatwave as a prototype. Environmental Research: Climate, DOI:10.1088/2752-5295/ad8028
Zhang, Y., B.M. Ayyub, J.F. Fung, and Z.M. Labe (2024). Incorporating extreme event attribution into climate change adaptation for civil infrastructure: Methods, benefits, and research needs. Resilient Cities and Structures, DOI:10.1016/j.rcns.2024.03.002
Eischeid, J.K., M.P. Hoerling, X.-W. Quan, A. Kumar, J. Barsugli, Z.M. Labe, K.E. Kunkel, C.J. Schreck III, D.R. Easterling, T. Zhang, J. Uehling, and X. Zhang (2023). Why has the summertime central U.S. warming hole not disappeared? Journal of Climate, DOI:10.1175/JCLI-D-22-0716.1Role of Secondary Metabolites in Defence Mechanism of Plants and itŌĆÖs Regulation



Role of Secondary Metabolites in Defence Mechanism of Plants and itŌĆÖs Regulationankitverma144299
╠²
Drug evaluationŌĆō Organoleptic, Microscopic, Chemical, Biological



Drug evaluationŌĆō Organoleptic, Microscopic, Chemical, BiologicalNistarini College, Purulia (W.B) India
╠²
Melaku Tafese Awyulachew's_Official letters between organizations and researc...



Melaku Tafese Awyulachew's_Official letters between organizations and researc...Melaku Tafese Awulachew
╠²
Koopman Prize Presentation
- 1. Duplicity Games for Deception Design With an Application to Insider Threat Mitigation Linan Huang and Quanyan Zhu 2022 INFORMS Annual Conference October 17, 2022
- 7. Failure of Boundary Defense Insider Threats
- 8. Challenge 1: Perimeter defense does not work. Challenges of Insider Threats Solution: Zero-Trust architecture
- 9. Challenge 2: Asymmetric information Challenges of Insider Threats Solution: Cyber deception
- 10. Challenge 3: False positive from negligent legitimate users Challenges of Insider Threats Solution: Compliance and mechanism design
- 11. Game between a defender and an unknown user
- 12. State Øæź Ōłł Øæŗ Feature pattern ØæĀ Ōłł Øæå ŌĆó Protocols ŌĆó Ports ŌĆó Response time ŌĆó Error response Ø£ŗ1 1 ŌłÆ Ø£ŗ1 1 ŌłÆ Ø£ŗ2 Ø£ŗ2 ØæÅ 1 ŌłÆ ØæÅ Feature Generator Ø£ŗ ØæĀ1 ØæĀ2 ØæĀ1 ØæĀ2 Incorporating Cyber Deception into the Game Model
- 13. Ø£ŗ1 1 ŌłÆ Ø£ŗ1 1 ŌłÆ Ø£ŗ2 Ø£ŗ2 ØæÅ 1 ŌłÆ ØæÅ UserŌĆÖs posterior belief ØæÅØæØ(ØæĀ1) 1 ŌłÆ ØæÅØæØ(ØæĀ1) ØæÅØæØ (ØæĀ2) 1 ŌłÆ ØæÅØæØ(ØæĀ2)
- 14. UserŌĆÖs posterior belief ØæÅØæØ (ØæĀ1) 1 ŌłÆ ØæÅØæØ(ØæĀ1) UserŌĆÖs action ØæÄ Ōłł ØÉ┤ UserŌĆÖs utility ØæŻØæł(ØæĪØæ”ØæØØæÆ, ØæĀØæĪØæÄØæĪØæÆ, ØæÄØæÉØæĪØæ¢Øæ£Øæø) UserŌĆÖs type Ø£ā Ōłł ╬ś ŌłÆ$$ $$ ŌłÆ$ $$$
- 15. Ø£ŗ1 1 ŌłÆ Ø£ŗ1 1 ŌłÆ Ø£ŗ2 Ø£ŗ2 ØæÅ 1 ŌłÆ ØæÅ ØæÅØæØ(ØæĀ1) 1 ŌłÆ ØæÅØæØ(ØæĀ1) ØæÅØæØ(ØæĀ2) 1 ŌłÆ ØæÅØæØ (ØæĀ2) ŌłÆ$$ $$ ŌłÆ$ $$$ ŌĆ” Feature Generator Ø£ŗ Belief Manipulator ØæÅ, ØæÅØæł Incentive Modulator ØæÉ
- 16. There is a need for a theory for Cyber Deception Mechanism Design. Theory can go beyond the design of generator. ŌĆó Belief/Trust Manipulator: e.g., changing honeypot percentage ŌĆó Feature Generator: e.g., configuring honeypots and normal servers ŌĆó Incentive Modulator: e.g., using multi-step authentication How to Design the Generator?
- 17. Duplicity Game for Mechanism Design
- 18. Cyber deception (with focus on honeypots): Evasion risk [Spitzner 2003], Intelligence [Wagener et al. 2009, 2011], Engagement [Pawlick et al.19ŌĆÖ], Detection risk [Dowling et al. 2019], Resource consumption [Akiyama et al. 2012], False positives [Qassrawi & Zhang 2010] , Strategic design [Pawlick et al. 2021], etc. Compliance and mechanism design: Insider Threat Mitigation Guide [CISA 2020]; The Critical Role of Positive Incentives for Reducing Insider Threats [CERT/CMU 2016] Mitigating inadvertent insider threats with incentives [Liu et al. 2009]; Compliance control [Casey, et al. 2015], ZETAR [Huang and Zhu 2022]; etc. Literature
- 19. Generator Design Problem: DefenderŌĆÖs Problem The defender designs a utility-maximizing generator so that the user has no incentive to deviate from the recommendation.
- 20. Dual Formulation: UserŌĆÖs Problem The user minimizes his expected effort to satisfy the defenderŌĆÖs security objective.
- 21. UserŌĆÖs action ØæÄ Ōłł ØÉ┤ UserŌĆÖs type Ø£ā Ōłł ╬ś K actions and M types ØÉŠØæĆ possible security policies Only Ø£Æ(ØÉŠ, ØæĆ, Øæü) are enforceable. ŌłÆ$$ $$ ŌłÆ$ $$$ Always exists one optimal generator that only relies on Øæü security policies. Feasibility of Generators: Enforceable Policies
- 22. ŌĆó Incentive Threshold (IT): Uncontrollable if the majority of insiders are adversarial. ŌĆó Deterrence Threshold (DT): Uncontrollable if there is an insufficient number of honeypots. Incentive Threshold Deterrence Threshold How does the percentage or probability of honeypots and (negligent) insiders affect defenderŌĆÖs utility?
- 23. If < IT && <DT, then the design of the generator is insufficient to deter an insider. Zero Trust Margin ŌåÆ Cannot be incentivized Deterrence Capacity
- 24. DefenderŌĆÖs utility structure = userŌĆÖs utility structure DefenderŌĆÖs utility structure = -userŌĆÖs utility structure No deception needed: Reveal full information Maximum deception needed: Reveal zero information Manageability of Incentive Modulator: Designing the Reward
- 25. No deception needed: Reveal full information Maximum deception needed: Reveal zero information DefenderŌĆÖs utility structure = Ø£īØæĀ userŌĆÖs utility structure + Ø£īØææ Only the sign of Ø£īØæĀ matters. Ø£īØæĀ > 0 Ø£īØæĀ < 0 Manageability under Linearly dependent utility structure
- 26. Principles for Joint Design of GMM Extension to Multi-Dimensional Mechanism Designs The defender can design reward independently. Separation Principle Design Information + Trust = Design Trust Equivalence Principle
- 27. Fast Learning for Finite-Step Mitigation
- 28. ŌĆó Duplicity game for designing cognitive honeypots ŌĆó Strategic and incentive-compatible Insider threat mitigation ŌĆó Enforceability, manageability, and deterrence ŌĆó Online and learning-based implementation Conclusions Huang, L. and Zhu, Q., 2021. Duplicity games for deception design with an application to insider threat mitigation. IEEE Transactions on Information Forensics and Security, 16, pp.4843-4856.
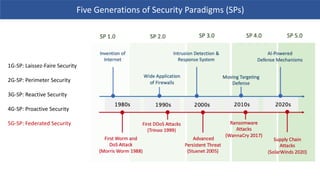
- 29. Five Generations of Security Paradigms 1G-SP: Laissez-Faire Security 2G-SP: Perimeter Security 3G-SP: Reactive Security 4G-SP: Proactive Security 5G-SP: Federated Security Five Generations of Security Paradigms (SPs)
- 30. 4G-SP: Proactive Security 5G-SP: Federated Security Emergence of AI-Powered Attacks Incorporate AI and system science to develop cognitive honeypots for 5G-SP Consolidation of Strategic, Proactive, and Autonomous Defense
- 31. Contact: Quanyan Zhu Email: qz494@nyu.edu









