Mtt p2
- 1. The Future of PC Protection 1 The Presentation is sole property of Aspenmas and cannot be used without permission.
- 2. When do you see a Virus or Malware? ŌĆó After it is in your PC and already effecting your machine, right. ŌĆó How does a virus really infect and effect your machine? ŌĆó The virus or malware is an executable piece of program that runs in your machine. Everything that happens on your PC is a program execution of some form or another. ŌĆó Most of these executions are good and some are bad. 2 The Presentation is sole property of Aspenmas and cannot be used without permission.
- 3. What are some of the primary characteristics of the current malware today? ŌĆó Sources: All media forms, usually controlled by a Botnet. ŌĆó WhoŌĆÖs the target: Anyone, any company any individual. ŌĆó What happens to a typical victim: 1 System is compromised 2 Information is stolen, sold, exploited. 3 PC is subjugated to a bot-network. ŌĆó What does an Infection look like: 1 Primary objective is to remain unseen. 2 Make tracking almost impossible. 3 Setup shop and not effect the PC operation. 4 Your PC is then controlled by the Botnet. 3 The Presentation is sole property of Aspenmas and cannot be used without permission.
- 4. A Little Analysis ŌĆó So when you see a problem, there has been an execution of a program. ŌĆó What else can be associated with this execution event? ŌĆó There can be several: ŌĆó First, the piece of code or program that was run. This is called a ŌĆ£binaryŌĆØ. ŌĆó Second might be a file copied or saved and the address or path. ŌĆó The Third association, to the event, is the preceding or ŌĆ£parent eventŌĆØ. ŌĆó So now we have a parent event and the child event that we found from the original problem we discovered. 4 The Presentation is sole property of Aspenmas and cannot be used without permission.
- 5. What is the ŌĆ£binaryŌĆØ that is associated with an event? ŌĆó Bottom line is, it is a program. It might be MS Word or Outlook or your browser or anything else has been installed or run on your PC. ŌĆó What does a virus binary do? ŌĆó Basically, it can do anything that any other program can do. ŌĆó It can copy itself from place to place. ŌĆó It can attach itself to other binaries, in order to hide, like a windows system file or other programs. ŌĆó It can even delete files or itself and, if it want to, it could destroy your entire hard drive. 5 The Presentation is sole property of Aspenmas and cannot be used without permission.
- 6. So what can we do with this information? ŌĆó If we knew all of the events, we can trace from one event to another. ŌĆó If we have each of the original ŌĆ£binariesŌĆØ we can do three things. 1. We can replace a damaged binary with the original one. 2. We can compare this binary to know bad programs. 3. We could see the original malware or virus when it entered the PC and its source point. 6 The Presentation is sole property of Aspenmas and cannot be used without permission.
- 7. The original event Discovered while using the PC (O.E.) 7 The Presentation is sole property of Aspenmas and cannot be used without permission.
- 8. O.E. Parent event. (P.E.) 8 The Presentation is sole property of Aspenmas and cannot be used without permission.
- 9. O.E. P.E. P.E. Trace back to the event that started the chain. 9 The Presentation is sole property of Aspenmas and cannot be used without permission.
- 10. The origin event will give up the source of the problem. O.E. P.E. P.E. 10 The Presentation is sole property of Aspenmas and cannot be used without permission.
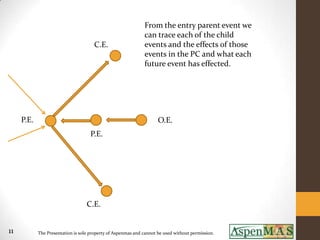
- 11. From the entry parent event we can trace each of the child C.E. events and the effects of those events in the PC and what each future event has effected. P.E. O.E. P.E. C.E. 11 The Presentation is sole property of Aspenmas and cannot be used without permission.
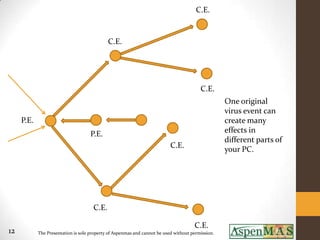
- 12. C.E. C.E. C.E. One original virus event can P.E. create many P.E. effects in different parts of C.E. your PC. C.E. C.E. 12 The Presentation is sole property of Aspenmas and cannot be used without permission.
- 13. Bad News and Good News ŌĆó The bad news is, this is real. The actions of a virus or malware binary are very serious. ŌĆó In the past, it used to be that virus would send you a nasty note and do its nasty business. Now they donŌĆÖt tell you anything. As a mater of fact, one primary goal is to NOT be detected or tracked. This way it can continue to do its business without you knowing it exists and you removing it. ŌĆó The good news is this entire process has been built into a tool that we install on our clients machines to assist in identifying and cleaning problems that occur. 13 The Presentation is sole property of Aspenmas and cannot be used without permission.
- 14. The Better News ŌĆó The current anti-virus and anti-malware software compares the programs (binaries) against a list of binaries that are known copies of the bad virusŌĆÖs and malware. These lists are called a signature files. A search, with the signature file, will identify programs on your PC that are similar to or are bad binaries. They then can then be removed and your PC can now be cleaned. ŌĆó The problem is no one anti-virus program will find all of the bad software. ŌĆó The great news is our tool has the ability to compare all of the binaries in your system to ALL of the signature files from All of the major software programs on the market. This can be done with in minutes of a new binary being introduced into your PC. 14 The Presentation is sole property of Aspenmas and cannot be used without permission.
- 15. AspenMAS ŌĆó Aspenmas is a Colorado based MSP. ŌĆó We provide one of the most effective PC and Server protection systems available today. ŌĆó Our security Plans include Firewalls, software, monitoring and Pro-Active Security Systems. ŌĆó If we canŌĆÖt stop the problem, our systems can identify and allow us to correct the infection. 15 The Presentation is sole property of Aspenmas and cannot be used without permission.
- 16. What do you do now ŌĆó The AspenMAS security Plans are available to our regular MSP clients. ŌĆó If you are interested in becoming an AspenMAS client contact us at: AspenMAS 40 W. Littleton Blvd Suite 210-284 Littleton, CO 80120 sales@aspenmas.com www.aspenmas.com 16 The Presentation is sole property of Aspenmas and cannot be used without permission.