Predicting The Future: Security and Compliance in the Cloud Age
Download as PPTX, PDF1 like741 views
The emergence of the Infrastructure-as-a-Service (IaaS) and Platform-as-a-Service (PaaS) models are just two of many inflection points as IT migrates away from the traditional data centers and into the cloud, shifting more control over security from the enterprise to the service provider. How will your security and compliance strategy change when this transformation is complete? This presentation will explore technologies and strategies you need to adopt today to prepare to support security and compliance in the cloud age.
1 of 17
Downloaded 72 times










Recommended
Workshop on CASB Part 2



Workshop on CASB Part 2Priyanka Aash
?
CASB Workshop Part 2
(Technology Taxonomy for Cloud Security,Key Components of Cloud Security Architecture,Blue Print To Build Your Cloud Security Program,Basics of Cloud Security Access Brokers)How to maintain business equality secured in network and cloud



How to maintain business equality secured in network and cloudDATA SECURITY SOLUTIONS
?
The document discusses McAfee's adaptive security architecture and cloud access security broker (CASB) solution. It notes that the adaptive security architecture uses a data exchange layer to allow security components like endpoint protection, gateways, and other products to immediately share data and intelligence to enable faster, more coordinated responses to threats. The CASB solution gives organizations control over their cloud data and access. It provides visibility, data controls, and application controls across cloud services in real-time without needing new agents.Why Everyone Needs a Cloud-First Security Program - SASEfaction Guaranteed!



Why Everyone Needs a Cloud-First Security Program - SASEfaction Guaranteed!Netskope
?
Security teams are constantly keeping up with complex attacks leveraging the cloud, but traditional security stacks just canˇŻt keep pace with malicious actors or insiders. In the session, weˇŻll explore GartnerˇŻs new SASE framework and how organizations can utilize Zero Trust, visibility into cloud-based traffic and cloud threat protection to build a modernized cloud-first stack.5 Highest-Impact CASB Use Cases



5 Highest-Impact CASB Use CasesNetskope
?
Cloud app security is a top priority for many enterprises. Whether securing data in the Office 365 suite, ensuring compliance in Salesforce, or getting control over shadow IT, information security leaders are exploring how Cloud Access Security Brokers can make an impact in their organizations.
This presentation covers the top five CASB use cases that have the highest impact on cloud-consuming enterprises.Multi cloud governance best practices - AWS, Azure, GCP



Multi cloud governance best practices - AWS, Azure, GCPFaiza Mehar
?
If you are looking for complete instructions on how to build your own Cloud governance process and control then view our recorded webinar on our youtube channel. We take you step by step on what is governance for the cloud and a focus area for security governance.Get ahead of cloud network security trends and practices in 2020



Get ahead of cloud network security trends and practices in 2020Cynthia Hsieh
?
- Cloud security is just security. An evolution
- 3 Stages of Digital Transformation
- A new security model
- Security model in AWS
- Automate with integrated services
- AWS security solutions
- Barriers and common seen practices
- ˇ°Unboxingˇ± cloud network security
- Cloud-Native Network Security Service
Meet Secure Messaging



Meet Secure MessagingRapidScale
?
RapidScale's Secure Messaging is a secure enhancement to business-class email, not a replacement. It is an addition to your current email, enabling business users to securely send, receive, track and control email communications on any device, simply and effectively.Cyxtera - Operational Complexity: The Biggest Security Threat to Your AWS Env...



Cyxtera - Operational Complexity: The Biggest Security Threat to Your AWS Env...Cyxtera Technologies
?
Learn how to remove operational complexity from achieving secure ¨C and easily auditable ¨C user access to your AWS systems. Automate tightly controlled user access in highly dynamic AWS environments. Painlessly report exactly who accessed which resources, from where, and when ¨C in near real-time ¨C and save your teams thousands of hours in audit prep work.Cloud Security 101 by Madhav Chablani



Cloud Security 101 by Madhav ChablaniOWASP Delhi
?
This document discusses cloud security best practices. It covers the current state of cloud adoption, security responsibilities in different cloud models, lessons learned, and how to apply those lessons. Key points include implementing cloud security brokers to reduce complexity and augment native security, applying security practices differently in cloud environments, and building new cloud-native security strategies focused on agility, automation, and leveraging unique cloud capabilities. The document advocates for a cultural shift within security teams to keep pace with cloud's rapid change.Cloud Security Governance



Cloud Security GovernanceShankar Subramaniyan
?
This document discusses cloud security governance and related challenges. It begins by outlining key cloud security concerns like lack of visibility, loss of control, and multi-tenancy issues. Major risks are then examined, such as data leakage, account hijacking, and insecure cloud software. The document also explores the shared responsibility model between cloud service providers and consumers. It notes that many breaches are due to customer misconfiguration rather than provider vulnerabilities. Finally, challenges in implementing cloud security governance are mentioned, such as cloud discovery, gaps in contracts, and rapidly changing cloud services and architectures.The Notorious 9 Cloud Computing Threats - CSA Congress, San Jose



The Notorious 9 Cloud Computing Threats - CSA Congress, San JoseMoshe Ferber
?
loud computing is evolving fast, and so are the threats and defense tactics. Cloud consumers and providers should always be aware of the latest risks and attack vectors and explore the latest security events to identify new attack vectors. Here, weˇŻll provide you with a list of the latest threats and discuss their effect on our security posture, and review a recent case study of attacks relevant to those threats.
Demystifying Prisma Access



Demystifying Prisma AccessHaris Chughtai
?
Prisma Access is Palo Alto Networks' cloud-based Secure Access Service Edge (SASE) solution that provides remote access and security as a service across a globally distributed network. It automatically scales capacity for remote employees and offices. Prisma Access has the same security features as on-premises Palo Alto firewalls without requiring new infrastructure. It maintains business continuity as capacity increases where needed. Prisma Access connects sites, remote networks, and mobile users securely through globally distributed nodes that enforce security policies.Understanding SASE 



Understanding SASE Haris Chughtai
?
SASE (Secure Access Service Edge) is a converged networking and security platform that provides secure access to cloud and on-premise resources for all users from any location. It delivers key security functions like ZTNA, SWG, CASB, and FWaaS as a cloud-based service to minimize hardware and simplify management. SASE is well-suited for remote sites, mobile users, and IoT devices by enabling consistent security policies as users move between different networks and access modes.Introduction to Cloud Security



Introduction to Cloud SecuritySusanne Tedrick
?
This document provides an introduction to cloud security. It discusses the shared responsibility model of cloud security between customers and providers for different cloud service models like IaaS, PaaS, and SaaS. It outlines some common cloud security risks like data leakage, malware injections, DDoS attacks, and insecure APIs. The document then defines cloud security and discusses key questions around responsibility, fortification, and controls. It introduces the NIST Cybersecurity Framework as an important resource for managing cyber risks and provides additional resources for researching cloud providers' security programs and NIST guidelines on cloud computing security and privacy.Introducing S.A.M.S Connecting the Dots ¨C your SMART technology partner



Introducing S.A.M.S Connecting the Dots ¨C your SMART technology partnerRicky Homem
?
We provide customised, turnkey solutions addressing both physical, and cloud-based access and security control, and data acquisition required by Property Developers, Retailers, Corporate Companies, Business and Residential Estates.
One of our security specialists are able to:
Define your security requirements
Assess your existing technology systems
Integrate and grow your existing security technology systemsHARTMANN and Cloudflare Learn how healthcare providers can build resilient in...



HARTMANN and Cloudflare Learn how healthcare providers can build resilient in...Cloudflare
?
This document discusses how healthcare providers like Paul Hartmann AG can build resilient infrastructure with Cloudflare. It summarizes Cloudflare's services including performance, security, and serverless capabilities. It then discusses trends seen on Cloudflare's network during COVID-19 like a rise in DDoS attacks and attacks targeting hospital websites. The document outlines best practices for healthcare organizations to deliver superior online experiences through strengthening security, ensuring no trade-off between security and performance, understanding business objectives, leveraging threat intelligence, and remaining ahead of the security curve.Latest Developments in Cloud Security Standards and Privacy



Latest Developments in Cloud Security Standards and PrivacyCloud Standards Customer Council
?
The document summarizes key points from a presentation on latest developments in cloud security standards and privacy. It discusses the benefits of standards, outlines some current security standards and frameworks, and provides recommendations for cloud customers to evaluate a cloud service provider's security capabilities. The presentation emphasizes that customers should ensure cloud providers support relevant security standards to ensure governance, risk management and regulatory compliance.Close your security gaps and get 100% of your traffic protected with Cloudflare



Close your security gaps and get 100% of your traffic protected with CloudflareCloudflare
?
The Gaming & Gambling industry has been the target of increasingly sophisticated cyber attacks in recent years, ranging from automated bots carrying out credential stuffing and intellectual property scraping to Layer 3 DDoS attacks, which can result in reduced network speed and performance, and in some cases loss of business when such incidents occur.
View this presentation from Cloudflare security experts Stephane Nouvellon, Principal Solutions Engineer and Philip Bj?rkman, Strategic Vertical Account Executive (EMEA Gaming & Gambling) to learn about:
-How you can protect your business and improve the performance and reliability of your infrastructure, globally
-Solutions to secure your organization's online traffic (all OSI layers) against bots and cyber attacks whilst improving the performance of your applications.The Cloud & I, The CISO challenges with Cloud Computing 



The Cloud & I, The CISO challenges with Cloud Computing Moshe Ferber
?
The Cloud is a challenge for the Security professional, but also creates opportunities. In this presentation we will overview the different cloud challenges according to each market sector. What is SASE



What is SASEAdi Ruppin
?
Sase, or Secure Access Service Edge, is one of the hottest trends in cybersecurity and networking today. Here's what it means.Cloud security what to expect (introduction to cloud security)



Cloud security what to expect (introduction to cloud security)Moshe Ferber
?
This document provides an overview of cloud security presented by Moshe Ferber, a certified cloud security professional. It introduces cloud computing models including SaaS, PaaS, and IaaS. For IaaS, the document discusses that while the underlying infrastructure is managed by the cloud provider, customers are responsible for the security of guest operating systems, applications, and data. It also covers key IaaS security considerations like virtual machine access control, network visibility limitations, and the division of security responsibilities between customers and providers.Transforming cloud security into an advantage



Transforming cloud security into an advantageMoshe Ferber
?
- Moshe Ferber is an experienced information security professional who has founded and invested in several cloud security companies.
- The document discusses important concepts in cloud security including creating trust between cloud providers and customers, security best practices in development and operations, and compliance with standards and regulations.
- Key responsibilities in cloud security include securing data, applications, users and identities across the entire lifecycle from a shared responsibility model between providers and customers.Security As A Service



Security As A ServiceGeorge Fares
?
Security as a Service (SaaS) is a new model for delivering traditional security applications like antivirus, email protection, and antispam through cloud-based services rather than installed software. With SaaS, all software and updates are hosted on the vendor's servers, eliminating the need for companies to purchase and maintain their own hardware and software. SaaS offers benefits like lower total cost of ownership, automatic updates, remote administration from any internet connection, and predictable annual licensing costs. While early offerings like McAfee ASaP were not widely adopted, widespread internet access and trends toward cloud computing mean SaaS is becoming the standard model for security solutions.John Merline - How make your cloud SASE 



John Merline - How make your cloud SASE AWS Chicago
?
The document discusses secure access service edge (SASE) and zero trust network access (ZTNA) solutions. It provides examples of how SASE can be used to securely access resources in public clouds and private networks from remote locations. Key points include using SASE to filter traffic, enforce policies, and establish double-tunneled connections to applications without placing users on the internal network. The document also provides a high-level overview of how ZTNA works by verifying identities, enforcing policies, and brokering secure connections between endpoints and application connectors.Defcon23 from zero to secure in 1 minute - nir valtman and moshe ferber



Defcon23 from zero to secure in 1 minute - nir valtman and moshe ferberMoshe Ferber
?
In the presentation, we plan to announce the full version of a new open source tool called "Cloudefigo" and explain how it enables accelerated security lifecycle. We demonstrate how to launch a pre-configured, already patched instance into an encrypted storage environment automatically while evaluating their security and mitigating them automatically if a vulnerability is found. In the live demo, we leverage Amazon Web Services EC2 Cloud-Init scripts and object storage for provisioning automated security configuration, integrating encryption, including secure encryption key repositories for secure server's communication. The result of those techniques is cloud servers that are resilient, automatically configured, with the reduced attack surface.Cloud Access Security Brokers



Cloud Access Security BrokersAbhishek Tripathi
?
Cloud Access Security Brokers (CASBs) provide visibility and security controls for user activity and data access across cloud applications and services. CASBs work by connecting to cloud service APIs to monitor usage, covering both on-network and off-network access on managed and unmanaged devices. This helps CASBs enforce policies for compliance, data loss prevention, threat protection, and access control. Gartner recognizes several leading CASB vendors that offer capabilities across pillars like visibility, compliance, threat protection and data security when evaluating the CASB market.Thin Air or Solid Ground? Practical Cloud Security



Thin Air or Solid Ground? Practical Cloud SecurityDan Fitzgerald, CISSP, CIPM
?
The rapid growth and many flavors of cloud capabilities can provide great business value. If not well planned, they may also give security professionals fits. With perspective and a deliberate approach, CISOs can not only manage cloud security effectively, but leverage the cloud to power security capabilities.
This session will introduce challenges and trends relating to the cloud for information security practitioners. Much of the session will focus on the speaker's own successes, failures, pitfalls and pratfalls as CISO for a cloud-based startup that built an AWS-based SAAS predictive analytics platform. We will also touch on private cloud concerns, architecture planning and real-world solutions.Cloud Security Alliance's GRC Stack Overview



Cloud Security Alliance's GRC Stack OverviewValdez Ladd MBA, CISSP, CISA,
?
Cloud Security Alliance's GRC Stack Overview presented at CloudCamp RTP August, 2011
Version 2, update January 2012.Cloud services and it security



Cloud services and it securityEast Midlands Cyber Security Forum
?
This presentation explains the approach of a global utility company to identify the measures and controls available within a cloud service offering.The Cloud Is Rockin' and Rollin' In



The Cloud Is Rockin' and Rollin' InKrishnan Subramanian
?
This is a presentation I gave to an audience at St. Louis introducing them to cloud computing and any concerns associated with the move to cloud.More Related Content
What's hot (20)
Cloud Security 101 by Madhav Chablani



Cloud Security 101 by Madhav ChablaniOWASP Delhi
?
This document discusses cloud security best practices. It covers the current state of cloud adoption, security responsibilities in different cloud models, lessons learned, and how to apply those lessons. Key points include implementing cloud security brokers to reduce complexity and augment native security, applying security practices differently in cloud environments, and building new cloud-native security strategies focused on agility, automation, and leveraging unique cloud capabilities. The document advocates for a cultural shift within security teams to keep pace with cloud's rapid change.Cloud Security Governance



Cloud Security GovernanceShankar Subramaniyan
?
This document discusses cloud security governance and related challenges. It begins by outlining key cloud security concerns like lack of visibility, loss of control, and multi-tenancy issues. Major risks are then examined, such as data leakage, account hijacking, and insecure cloud software. The document also explores the shared responsibility model between cloud service providers and consumers. It notes that many breaches are due to customer misconfiguration rather than provider vulnerabilities. Finally, challenges in implementing cloud security governance are mentioned, such as cloud discovery, gaps in contracts, and rapidly changing cloud services and architectures.The Notorious 9 Cloud Computing Threats - CSA Congress, San Jose



The Notorious 9 Cloud Computing Threats - CSA Congress, San JoseMoshe Ferber
?
loud computing is evolving fast, and so are the threats and defense tactics. Cloud consumers and providers should always be aware of the latest risks and attack vectors and explore the latest security events to identify new attack vectors. Here, weˇŻll provide you with a list of the latest threats and discuss their effect on our security posture, and review a recent case study of attacks relevant to those threats.
Demystifying Prisma Access



Demystifying Prisma AccessHaris Chughtai
?
Prisma Access is Palo Alto Networks' cloud-based Secure Access Service Edge (SASE) solution that provides remote access and security as a service across a globally distributed network. It automatically scales capacity for remote employees and offices. Prisma Access has the same security features as on-premises Palo Alto firewalls without requiring new infrastructure. It maintains business continuity as capacity increases where needed. Prisma Access connects sites, remote networks, and mobile users securely through globally distributed nodes that enforce security policies.Understanding SASE 



Understanding SASE Haris Chughtai
?
SASE (Secure Access Service Edge) is a converged networking and security platform that provides secure access to cloud and on-premise resources for all users from any location. It delivers key security functions like ZTNA, SWG, CASB, and FWaaS as a cloud-based service to minimize hardware and simplify management. SASE is well-suited for remote sites, mobile users, and IoT devices by enabling consistent security policies as users move between different networks and access modes.Introduction to Cloud Security



Introduction to Cloud SecuritySusanne Tedrick
?
This document provides an introduction to cloud security. It discusses the shared responsibility model of cloud security between customers and providers for different cloud service models like IaaS, PaaS, and SaaS. It outlines some common cloud security risks like data leakage, malware injections, DDoS attacks, and insecure APIs. The document then defines cloud security and discusses key questions around responsibility, fortification, and controls. It introduces the NIST Cybersecurity Framework as an important resource for managing cyber risks and provides additional resources for researching cloud providers' security programs and NIST guidelines on cloud computing security and privacy.Introducing S.A.M.S Connecting the Dots ¨C your SMART technology partner



Introducing S.A.M.S Connecting the Dots ¨C your SMART technology partnerRicky Homem
?
We provide customised, turnkey solutions addressing both physical, and cloud-based access and security control, and data acquisition required by Property Developers, Retailers, Corporate Companies, Business and Residential Estates.
One of our security specialists are able to:
Define your security requirements
Assess your existing technology systems
Integrate and grow your existing security technology systemsHARTMANN and Cloudflare Learn how healthcare providers can build resilient in...



HARTMANN and Cloudflare Learn how healthcare providers can build resilient in...Cloudflare
?
This document discusses how healthcare providers like Paul Hartmann AG can build resilient infrastructure with Cloudflare. It summarizes Cloudflare's services including performance, security, and serverless capabilities. It then discusses trends seen on Cloudflare's network during COVID-19 like a rise in DDoS attacks and attacks targeting hospital websites. The document outlines best practices for healthcare organizations to deliver superior online experiences through strengthening security, ensuring no trade-off between security and performance, understanding business objectives, leveraging threat intelligence, and remaining ahead of the security curve.Latest Developments in Cloud Security Standards and Privacy



Latest Developments in Cloud Security Standards and PrivacyCloud Standards Customer Council
?
The document summarizes key points from a presentation on latest developments in cloud security standards and privacy. It discusses the benefits of standards, outlines some current security standards and frameworks, and provides recommendations for cloud customers to evaluate a cloud service provider's security capabilities. The presentation emphasizes that customers should ensure cloud providers support relevant security standards to ensure governance, risk management and regulatory compliance.Close your security gaps and get 100% of your traffic protected with Cloudflare



Close your security gaps and get 100% of your traffic protected with CloudflareCloudflare
?
The Gaming & Gambling industry has been the target of increasingly sophisticated cyber attacks in recent years, ranging from automated bots carrying out credential stuffing and intellectual property scraping to Layer 3 DDoS attacks, which can result in reduced network speed and performance, and in some cases loss of business when such incidents occur.
View this presentation from Cloudflare security experts Stephane Nouvellon, Principal Solutions Engineer and Philip Bj?rkman, Strategic Vertical Account Executive (EMEA Gaming & Gambling) to learn about:
-How you can protect your business and improve the performance and reliability of your infrastructure, globally
-Solutions to secure your organization's online traffic (all OSI layers) against bots and cyber attacks whilst improving the performance of your applications.The Cloud & I, The CISO challenges with Cloud Computing 



The Cloud & I, The CISO challenges with Cloud Computing Moshe Ferber
?
The Cloud is a challenge for the Security professional, but also creates opportunities. In this presentation we will overview the different cloud challenges according to each market sector. What is SASE



What is SASEAdi Ruppin
?
Sase, or Secure Access Service Edge, is one of the hottest trends in cybersecurity and networking today. Here's what it means.Cloud security what to expect (introduction to cloud security)



Cloud security what to expect (introduction to cloud security)Moshe Ferber
?
This document provides an overview of cloud security presented by Moshe Ferber, a certified cloud security professional. It introduces cloud computing models including SaaS, PaaS, and IaaS. For IaaS, the document discusses that while the underlying infrastructure is managed by the cloud provider, customers are responsible for the security of guest operating systems, applications, and data. It also covers key IaaS security considerations like virtual machine access control, network visibility limitations, and the division of security responsibilities between customers and providers.Transforming cloud security into an advantage



Transforming cloud security into an advantageMoshe Ferber
?
- Moshe Ferber is an experienced information security professional who has founded and invested in several cloud security companies.
- The document discusses important concepts in cloud security including creating trust between cloud providers and customers, security best practices in development and operations, and compliance with standards and regulations.
- Key responsibilities in cloud security include securing data, applications, users and identities across the entire lifecycle from a shared responsibility model between providers and customers.Security As A Service



Security As A ServiceGeorge Fares
?
Security as a Service (SaaS) is a new model for delivering traditional security applications like antivirus, email protection, and antispam through cloud-based services rather than installed software. With SaaS, all software and updates are hosted on the vendor's servers, eliminating the need for companies to purchase and maintain their own hardware and software. SaaS offers benefits like lower total cost of ownership, automatic updates, remote administration from any internet connection, and predictable annual licensing costs. While early offerings like McAfee ASaP were not widely adopted, widespread internet access and trends toward cloud computing mean SaaS is becoming the standard model for security solutions.John Merline - How make your cloud SASE 



John Merline - How make your cloud SASE AWS Chicago
?
The document discusses secure access service edge (SASE) and zero trust network access (ZTNA) solutions. It provides examples of how SASE can be used to securely access resources in public clouds and private networks from remote locations. Key points include using SASE to filter traffic, enforce policies, and establish double-tunneled connections to applications without placing users on the internal network. The document also provides a high-level overview of how ZTNA works by verifying identities, enforcing policies, and brokering secure connections between endpoints and application connectors.Defcon23 from zero to secure in 1 minute - nir valtman and moshe ferber



Defcon23 from zero to secure in 1 minute - nir valtman and moshe ferberMoshe Ferber
?
In the presentation, we plan to announce the full version of a new open source tool called "Cloudefigo" and explain how it enables accelerated security lifecycle. We demonstrate how to launch a pre-configured, already patched instance into an encrypted storage environment automatically while evaluating their security and mitigating them automatically if a vulnerability is found. In the live demo, we leverage Amazon Web Services EC2 Cloud-Init scripts and object storage for provisioning automated security configuration, integrating encryption, including secure encryption key repositories for secure server's communication. The result of those techniques is cloud servers that are resilient, automatically configured, with the reduced attack surface.Cloud Access Security Brokers



Cloud Access Security BrokersAbhishek Tripathi
?
Cloud Access Security Brokers (CASBs) provide visibility and security controls for user activity and data access across cloud applications and services. CASBs work by connecting to cloud service APIs to monitor usage, covering both on-network and off-network access on managed and unmanaged devices. This helps CASBs enforce policies for compliance, data loss prevention, threat protection, and access control. Gartner recognizes several leading CASB vendors that offer capabilities across pillars like visibility, compliance, threat protection and data security when evaluating the CASB market.Thin Air or Solid Ground? Practical Cloud Security



Thin Air or Solid Ground? Practical Cloud SecurityDan Fitzgerald, CISSP, CIPM
?
The rapid growth and many flavors of cloud capabilities can provide great business value. If not well planned, they may also give security professionals fits. With perspective and a deliberate approach, CISOs can not only manage cloud security effectively, but leverage the cloud to power security capabilities.
This session will introduce challenges and trends relating to the cloud for information security practitioners. Much of the session will focus on the speaker's own successes, failures, pitfalls and pratfalls as CISO for a cloud-based startup that built an AWS-based SAAS predictive analytics platform. We will also touch on private cloud concerns, architecture planning and real-world solutions.Cloud Security Alliance's GRC Stack Overview



Cloud Security Alliance's GRC Stack OverviewValdez Ladd MBA, CISSP, CISA,
?
Cloud Security Alliance's GRC Stack Overview presented at CloudCamp RTP August, 2011
Version 2, update January 2012.Similar to Predicting The Future: Security and Compliance in the Cloud Age (20)
Cloud services and it security



Cloud services and it securityEast Midlands Cyber Security Forum
?
This presentation explains the approach of a global utility company to identify the measures and controls available within a cloud service offering.The Cloud Is Rockin' and Rollin' In



The Cloud Is Rockin' and Rollin' InKrishnan Subramanian
?
This is a presentation I gave to an audience at St. Louis introducing them to cloud computing and any concerns associated with the move to cloud.Cloud Computing Security



Cloud Computing SecurityOrange Business Services
?
Cloud security is a must have. Also, an expectation AND a business accelerator.
But what really changes with cloud ? Cloud is not more or less secure : the security posture evolves..
Cloud Computing



Cloud ComputingMadhusudan Partani
?
It is on Cloud Computing presented by Sweta Agarwal, Radhika Gupta, Shivi Agarwal, Madhusudan Partani of FMG-18A, FORE School of ManagementCloud Ecosystems A Perspective



Cloud Ecosystems A Perspectivejmcdaniel650
?
An educational overview of the Cloud Computing Ecosystem or Framework. This presentation is geared toward those who are just beginning to understand Cloud Computing.The Trouble with Saas and Hybrid Cloud



The Trouble with Saas and Hybrid CloudNovosco
?
This document summarizes information from Novosco, a company that provides managed hosting and cloud services. It discusses trends like SaaS, public cloud commoditization, and digital transformation. It outlines Novosco's services portfolio and focus on cloud services and applications beyond the perimeter. The main text discusses challenges with the shift to SaaS models, including loss of authority and control for enterprises. However, it proposes that enterprises can take back control through network data analytics, machine learning, and gaining compliance and security insights. It provides examples of using analytics for threat monitoring, application infrastructure visibility, and traffic analysis between cloud providers.IEEE PHM Cloud Computing



IEEE PHM Cloud ComputingJoseph Williams
?
This document discusses cloud computing and the challenges of managing applications and data in cloud environments. It covers a wide range of topics including the complexity of cloud platforms, regulatory and jurisdictional challenges of data sovereignty, and key questions around compliance, risk management, and interoperability that enterprises need to have answered before moving workloads to the cloud.Legal And Regulatory Issues Cloud Computing...V2.0



Legal And Regulatory Issues Cloud Computing...V2.0David Spinks
?
The document provides an overview of 11 domains related to security in cloud computing. It summarizes recommendations for governance, risk management, compliance, auditing, information lifecycle management, portability and interoperability, traditional security practices, data center operations, incident response, application security, and encryption in cloud environments. The document emphasizes the importance of thorough risk analysis, contractual agreements, ongoing assessment and monitoring when adopting cloud services.Cloud Security using NIST guidelines



Cloud Security using NIST guidelinesSrishti Ahuja
?
This presentation provides an overview of the NIST SP 500-299 NIST Cloud Computing Security Reference Architecture. It includes a brief description of the Cloud Computing Architecture, its services along with the required Risk Management activities. Cloud Security using NIST guidelines



Cloud Security using NIST guidelinesSrishti Ahuja
?
Cloud Security using NIST guidelines, using NIST Cloud Computing Security Reference Architecture
(NIST SP 500-299), NIST Cloud
Computing Reference Architecture (NIST SP 500-292), NIST's Guide for Applying the Risk Management Framework to Federal Information Systems (NIST SP 800-37)Cloud Computing 101



Cloud Computing 101Ben Kepes
?
This document provides an overview of cloud computing applications currently available and potential future applications. It defines common cloud computing models including Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS). Examples are given of companies using cloud services for billing systems, quoting systems, and data analysis. Benefits include scalability, lower costs, easier collaboration, and the ability to focus on core business needs rather than IT infrastructure. The future of cloud computing is predicted to include fewer organizations maintaining their own infrastructure and more ubiquitous access to computing resources from various devices.Cloud Computing.pptx



Cloud Computing.pptxLakshika Rasanjali
?
Cloud computing provides IT capabilities as a service over the internet. There are different types including public, private, and hybrid clouds. Major cloud providers are Amazon Web Services, Google Cloud, Microsoft Azure, IBM Cloud, and Oracle Cloud. Cloud computing goes through stages of development starting from time-sharing in the 1960s to modern technologies like containers. It offers advantages like reduced costs, scalability, and security but also has weaknesses regarding outages, vendor lock-in, and lack of control. Future trends include edge computing, disaster recovery, multi-cloud solutions, cloud security, Kubernetes, cloud gaming, and serverless computing.Virg¨Şlio Vargas Presentations / CloudViews.Org - Cloud Computing Conference 2...



Virg¨Şlio Vargas Presentations / CloudViews.Org - Cloud Computing Conference 2...EuroCloud
?
The document discusses cloud computing and its benefits, including increased flexibility and reduced costs. It notes that cloud computing provides standardized offerings that can rapidly scale resources in a flexible and easy-to-access manner. The document outlines a strategy for developing a cloud architecture and implementation plan to help organizations manage IT challenges and realize the opportunities of cloud computing.Cloud computing and_saas



Cloud computing and_saasRahul Parmar
?
The document discusses cloud computing and the Defense Information Systems Agency's (DISA) approach. DISA sees cloud computing as providing scalable IT capabilities over the internet, enabling on-demand access from any device. DISA is developing a platform-as-a-service (PaaS) called RACE to provide standardized development platforms, reduce costs, and improve security and scalability. RACE and the Forge.mil collaboration environment aim to simplify application development, testing, and deployment in the cloud. However, challenges remain around balancing security and usability, funding models, and cultural adoption of cloud computing.Cloud computing and_saas



Cloud computing and_saaskavinalli
?
The document discusses cloud computing and the Defense Information Systems Agency's (DISA) approach. DISA sees cloud computing as providing scalable IT capabilities over the internet, enabling on-demand access from any device. DISA is developing a platform-as-a-service (PaaS) called RACE to provide standardized development platforms, reduce costs and speeds, and improve security. RACE and Forge.mil will help developers rapidly build and deploy applications to the cloud. However, challenges remain around balancing security and usability, and integrating cloud services across agencies.Cloud computing and_saas



Cloud computing and_saasRahul Parmar
?
The document discusses cloud computing and the Defense Information Systems Agency's (DISA) approach. DISA sees cloud computing as providing scalable IT capabilities over the internet, enabling on-demand access from any device. DISA is developing a platform-as-a-service (PaaS) called RACE to provide standardized development platforms, reduce costs and speeds, and improve security. RACE and Forge.mil will help developers rapidly build and deploy applications to the cloud. However, challenges remain around balancing security and usability, and integrating cloud services across agencies.Cloud Computing basics - an overview.pptx



Cloud Computing basics - an overview.pptxPuneet Kumar Bhatia (MBA, ITIL V3 Certified)
?
Cloud Computing overview(Dee fleming) Ccloud computing_la_press_final



(Dee fleming) Ccloud computing_la_press_finalLA_IBM_Cloud_Event
?
The document discusses the benefits of cloud computing, including operational efficiency, business transformation, and addressing business challenges through unprecedented integration, agility, quality services, and reduced costs. It outlines IBM's capabilities in cloud consulting, technologies, and managed services to help clients plan, build, integrate, and manage cloud deployments across public, private and hybrid models. IBM's approach considers strategic direction, workload analysis, and a systematic lifecycle to ensure successful cloud implementations.Unlocking the value of the cloud - The benefits of deploying asset and facili...



Unlocking the value of the cloud - The benefits of deploying asset and facili...Cyrus Sorab
?
SaaS adoption is impacting all businesses and sectors,
including those purchasing asset and facilities management
solutions. The predictable costs, ease of deployment, and
vendor-handled upgrades are increasingly appealing to
maintenance leaders who often struggle to justify the cost
savings necessary to warrant new expenditures. With SaaS,
small and medium-sized companies are finding improved data
security that exceeds their internal capabilities, while larger
businesses are drawn to the simple upgradability, which allows
them to attain new features without additional cost.
This buyerˇŻs guide will dive into some of these features
and more, as a primer to getting started on your SaaS journey.Cloud computing adoption in sap technologies



Cloud computing adoption in sap technologiessveldanda
?
Cloud computing is emerging as an exciting trend in the ICT and with this presentation we tried to explore opportunities of adopting Cloud computing in SAP TechnologiesRecently uploaded (20)
Leadership Spectrum by Sonam Sherpa at GDG Kathmandu March Monthly Meetup



Leadership Spectrum by Sonam Sherpa at GDG Kathmandu March Monthly MeetupGDG Kathmandu
?
Leadership by Sonam SherpaBenefits of Moving Ellucian Banner to Oracle Cloud



Benefits of Moving Ellucian Banner to Oracle CloudAstuteBusiness
?
Discover the advantages of migrating Ellucian Banner to Oracle Cloud Infrastructure, including scalability, security, and cost efficiency for educational institutions.
How Telemedicine App Development is Revolutionizing Virtual Care.pptx



How Telemedicine App Development is Revolutionizing Virtual Care.pptxDash Technologies Inc
?
Telemedicine app development builds software for remote doctor consultations and patient check-ups. These apps bridge healthcare professionals with patients via video calls, secure messages, and interactive interfaces. That helps practitioners to provide care without immediate face-to-face interactions; hence, simplifying access to medical care. Telemedicine applications also manage appointment scheduling, e-prescribing, and sending reminders.
Telemedicine apps do not only conduct remote consultations. They also integrate with entire healthcare platforms, such as patient forums, insurance claims processing, and providing medical information libraries. Remote patient monitoring enables providers to keep track of patients' vital signs. This helps them intervene and provide care whenever necessary. Telehealth app development eliminates geographical boundaries and facilitates easier communication.
In this blog, we will explore its market growth, essential features, and benefits for both patients and providers. Commit Conf 2025 Bitnami Charts with Kubescape



Commit Conf 2025 Bitnami Charts with KubescapeAlfredo Garc¨Şa Lavilla
?
En esta charla compartiremos la experiencia del equipo de Bitnami en la mejora de la seguridad de nuestros Helm Charts y Contenedores utilizando Kubescape como herramienta principal de validaci¨®n. Exploraremos el proceso completo, desde la identificaci¨®n de necesidades hasta la implementaci¨®n de validaciones automatizadas, incluyendo la creaci¨®n de herramientas para la comunidad.
Compartiremos nuestra experiencia en la implementaci¨®n de mejoras de seguridad en Charts y Contenedores, bas¨˘ndonos en las mejores pr¨˘cticas del mercado y utilizando Kubescape como herramienta de validaci¨®n. Explicaremos c¨®mo automatizamos estas validaciones integr¨˘ndolas en nuestro ciclo de vida de desarrollo, mejorando significativamente la seguridad de nuestros productos mientras manten¨Şamos la eficiencia operativa.
Durante la charla, los asistentes aprender¨˘n c¨®mo implementar m¨˘s de 60 validaciones de seguridad cr¨Şticas, incluyendo la configuraci¨®n segura de contenedores en modo no privilegiado, la aplicaci¨®n de buenas pr¨˘cticas en recursos de Kubernetes, y c¨®mo garantizar la compatibilidad con plataformas como OpenShift. Adem¨˘s, demostraremos una herramienta de self-assessment que desarrollamos para que cualquier usuario pueda evaluar y mejorar la seguridad de sus propios Charts bas¨˘ndose en esta experiencia.
Least Privilege AWS IAM Role Permissions



Least Privilege AWS IAM Role PermissionsChris Wahl
?
RECORDING: https://youtu.be/hKepiNhtWSo
Hello innovators! Welcome to the latest episode of My Essentials Course series. In this video, we'll delve into the concept of least privilege for IAM roles, ensuring roles have the minimum permissions needed for success. Learn strategies to create read-only, developer, and admin roles. Discover tools like IAM Access Analyzer, Pike, and Policy Sentry for generating efficient IAM policies. Follow along as we automate role and policy creation using Pike with Terraform, and test our permissions using GitHub Actions. Enhance your security practices by integrating these powerful tools. Enjoy the video and leave your feedback in the comments!A General introduction to Ad ranking algorithms



A General introduction to Ad ranking algorithmsBuhwan Jeong
?
Details of AD ranking algorithms and beyondAPAC Solutions Challenge Info Session.pdf



APAC Solutions Challenge Info Session.pdfGDG on Campus Monash
?
GDG on Campus Monash hosted Info Session to provide details of the Solution Challenge to promote participation and hosted networking activities to help participants find their dream teamPackaging your App for AppExchange ¨C Managed Vs Unmanaged.pptx



Packaging your App for AppExchange ¨C Managed Vs Unmanaged.pptxmohayyudin7826
?
Learn how to package your app for Salesforce AppExchange with a deep dive into managed vs. unmanaged packages. Understand the best strategies for ISV success and choosing the right approach for your app development goals.202408_JAWSPANKRATION_Introduction_of_Minaden.pdf



202408_JAWSPANKRATION_Introduction_of_Minaden.pdfNTTDOCOMO-ServiceInnovation
?
202408łĺ´ł´ˇ°Âł§±Ę´ˇ±·°¸é´ˇ°Ő±ő°ż±·łĺ×îÖŐ°ć.±č»ĺ´ÚSTRING FUNCTIONS IN JAVA BY N SARATH KUMAR



STRING FUNCTIONS IN JAVA BY N SARATH KUMARSarathkumar Narsupalli
?
STRINGS IN JAVA POWER POINT PRESENTATIONAI in Talent Acquisition: Boosting Hiring



AI in Talent Acquisition: Boosting HiringBeyond Chiefs
?
AI is transforming talent acquisition by streamlining recruitment processes, enhancing decision-making, and delivering personalized candidate experiences. By automating repetitive tasks such as resume screening and interview scheduling, AI significantly reduces hiring costs and improves efficiency, allowing HR teams to focus on strategic initiatives. Additionally, AI-driven analytics help recruiters identify top talent more accurately, leading to better hiring decisions. However, despite these advantages, organizations must address challenges such as AI bias, integration complexities, and resistance to adoption to fully realize its potential. Embracing AI in recruitment can provide a competitive edge, but success depends on aligning technology with business goals and ensuring ethical, unbiased implementation.
The Road to SAP S4HANA Cloud with SAP Activate.pptx



The Road to SAP S4HANA Cloud with SAP Activate.pptxzsbaranyai
?
Road to SAP S4HANA Cloud with SAP ActivateCIOs Speak Out - A Research Series by Jasper Colin



CIOs Speak Out - A Research Series by Jasper ColinJasper Colin
?
Discover key IT leadership insights from top CIOs on AI, cybersecurity, and cost optimization. Jasper ColinˇŻs research reveals whatˇŻs shaping the future of enterprise technology. Stay ahead of the curve.Columbia Weather Systems - Product Overview



Columbia Weather Systems - Product OverviewColumbia Weather Systems
?
Columbia Weather Systems offers professional weather stations in basically three configurations for industry and government agencies worldwide: Fixed-Base or Fixed-Mount Weather Stations, Portable Weather Stations, and Vehicle-Mounted Weather Stations.
Models include all-in-one sensor configurations as well as modular environmental monitoring systems. Real-time displays include hardware console, WeatherMaster? Software, and a Weather MicroServer? with industrial protocols, web and app monitoring options.
Innovative Weather Monitoring: Trusted by industry and government agencies worldwide. Professional, easy-to-use monitoring options. Customized sensor configurations. One-year warranty with personal technical support. Proven reliability, innovation, and brand recognition for over 45 years.Smarter RAG Pipelines: Scaling Search with Milvus and Feast



Smarter RAG Pipelines: Scaling Search with Milvus and FeastZilliz
?
About this webinar
Learn how Milvus and Feast can be used together to scale vector search and easily declare views for retrieval using open source. WeˇŻll demonstrate how to integrate Milvus with Feast to build a customized RAG pipeline.
Topics Covered
- Leverage Feast for dynamic metadata and document storage and retrieval, ensuring that the correct data is always available at inference time
- Learn how to integrate Feast with Milvus to support vector-based retrieval in RAG systems
- Use Milvus for fast, high-dimensional similarity search, enhancing the retrieval phase of your RAG model2025-04-05 - Block71 Event - The Landscape of GenAI and Ecosystem.pdf



2025-04-05 - Block71 Event - The Landscape of GenAI and Ecosystem.pdfIvan Tang
?
The different layers of GenAI stack.All-Data, Any-AI Integration: FME & Amazon Bedrock in the Real-World



All-Data, Any-AI Integration: FME & Amazon Bedrock in the Real-WorldSafe Software
?
Join us for an exclusive webinar featuring special guest speakers from Amazon, Amberside Energy, and Avineon-Tensing as we explore the power of Amazon Bedrock and FME in AI-driven geospatial workflows.
Discover how Avineon-Tensing is using AWS Bedrock to support Amberside Energy in automating image classification and streamlining site reporting. By integrating BedrockˇŻs generative AI capabilities with FME, image processing and categorization become faster and more efficient, ensuring accurate and organized filing of site imagery. Learn how this approach reduces manual effort, standardizes reporting, and leverages AWSˇŻs secure AI tooling to optimize their workflows.
If youˇŻre looking to enhance geospatial workflows with AI, automate image processing, or simply explore the potential of FME and Bedrock, this webinar is for you!Network_Packet_Brokers_Presentation.pptx



Network_Packet_Brokers_Presentation.pptxKhushi Communications
?
Most people might think of a water faucet or even the tap on a keg of beer. But in the world of networking, "TAP" stands for "Traffic Access Point" or "Test Access Point." It's not a beverage or a sink fixture, but rather a crucial tool for network monitoring and testing. Khushi Communications is a top vendor in India, providing world-class Network TAP solutions. With their expertise, they help businesses monitor, analyze, and secure their networks efficiently.DraginoĄ×ĄíĄŔĄŻĄČĄ«ĄżĄíĄ° LoRaWAN NB-IoT LTE cat.M1ÉĚĆ·ĄęĄąĄČ



DraginoĄ×ĄíĄŔĄŻĄČĄ«ĄżĄíĄ° LoRaWAN NB-IoT LTE cat.M1ÉĚĆ·ĄęĄąĄČCRI Japan, Inc.
?
DraginoĄ×ĄíĄŔĄŻĄČĄ«ĄżĄíĄ° LoRaWAN NB-IoT LTE cat.M1ÉĚĆ·ĄęĄąĄČPredicting The Future: Security and Compliance in the Cloud Age
- 1. Predicting the Future: Security and Compliance in the Cloud Age
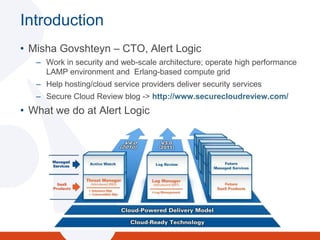
- 2. IntroductionMisha Govshteyn ¨C CTO, Alert LogicWork in security and web-scale architecture; operate high performance LAMP environment and Erlang-based compute gridHelp hosting/cloud service providers deliver security servicesSecure Cloud Review blog -> http://www.securecloudreview.com/ What we do at Alert Logic
- 3. About this sessionObjective:Help you make security & compliance decisions that prepare your company for the futureThis presentation addresses a broad trend of consuming IT as a serviceCloud in this context includes IaaSPaaSSaaSWhy take such a broad view? Because each of these models has potential to significantly alter the way you protect your most critical assets
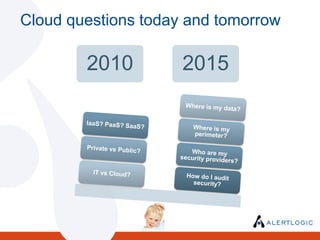
- 4. Putting 2010 questions in perspectiveQuestions of today are less important than this fact : IT is increasingly delivered as a serviceYour IT footprint is already changingˇprobably adopting some form of cloud servicesnetwork is already becoming decentralizedSome of your data may already be off-premiseIaaS? PaaS? SaaS?Private vs Public?IT vs Cloud?
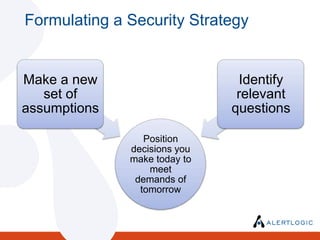
- 5. Formulating a Security Strategy
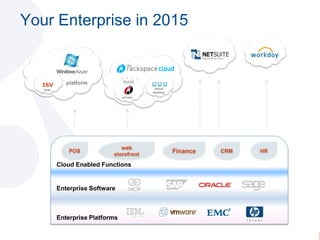
- 6. Your Enterprise in 2015platformISVvirtualdesktopsaas????burstprivateHRCRMFinancePOSweb storefrontCloud Enabled FunctionsEnterprise SoftwareEnterprise Platforms
- 7. Cloud questions today and tomorrow
- 8. Your enterprise 5 years from nowPerimeter is less important than everMore than 50% of your critical data is offsiteSome in environments you do not controlSome users donˇŻt need your VPN to do their jobs Securing the enterprise will be characterized byContinuous transfer of security responsibility to service providers of all typesApplication/protocol level attacksEven more compliance requirements than today
- 9. Security trends in next 5 yearsGovernance and compliance efforts will extend to private and public cloud environmentsCloud providers will use security as a differentiatorBecome increasingly more transparentProvide automated attestation and auditing of key controls, including access to logsNative data encryption available & heavily promoted, but sparingly usedMost will offer enterprise-level Security-as-a-Service within 2-3 yearsChanges in security industryIdentity management is likely to become the first cloud sec ˇ°killer appˇ±Netsec vendors, less strategic to enterprises, will focus on CSPsApplication/protocol security and Data Leak Prevention are likely to become increasingly important due to PCI mandates
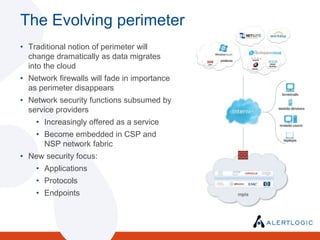
- 10. Cloud impact on network securityMost network security products are unable to deal with complexity of CSP networksBig pipes: CSPs already see speeds well in excess of 50gbpsSmall customers: thousands of customers, some with very little traffic (no native multi-tenancy)Rapid elasticity ¨C changing topology, new IP allocations, new VLANS, more traffic flowsTodayˇŻs notions of trusted users, networks and computing resources will need to be re-thoughtCloud Service Providers will begin to control an increasing share of the network, rather than Enterprise ITThe Evolving perimeterTraditional notion of perimeter will change dramatically as data migrates into the cloud
- 11. Network firewalls will fade in importance as perimeter disappears
- 12. Network security functions subsumed by service providers
- 13. Increasingly offered as a service
- 14. Become embedded in CSP and NSP network fabric
- 16. Applications
- 17. Protocols
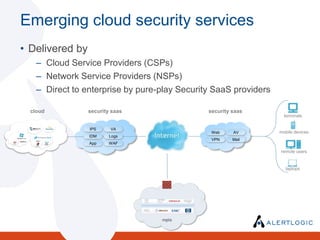
- 18. EndpointsDelivered byCloud Service Providers (CSPs) Network Service Providers (NSPs) Direct to enterprise by pure-play Security SaaS providersterminalsmobile devicesremote userslaptopsEmerging cloud security servicescloudsecurity saassecurity saasIPSVAWebAVIDMLogsVPNMailAppWAF
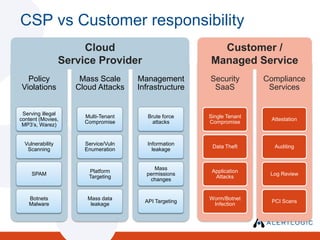
- 19. CSP vs Customer responsibilityCustomer /Managed ServiceCloud Service Provider
- 20. Compliance in the cloudRequires a robust set of enterprise-grade security capabilities and services from CSPsAutomated cloud auditability:Attestation
- 21. Auditing of key controls
- 23. Log availabilityEmerging standard: CloudAudit/A6
- 24. X-Factor: the AuditorsPassing a compliance audit in the cloud in next 5 years will require equal parts luck and planningImproving your chancesDistant future: find an auditor that understands and has experience in cloud environmentsToday: help your auditor understand your environmentAPI? CSA? XML? A6? Hadoop? EC2? VPC? XEN?
- 25. First stepsEngage with your IT security and auditorsBuild a roadmap for dealing with the dissolving perimeter and set realistic goals for your teamUnderstand how Security SaaS fits into your current and future strategyExplore technologies/efforts important to secure cloud adoption: IDM, OWASP, WAF, CSA, A6Choose cloud environments that understand and plan to address your evolving security needs
- 26. Alert Logichttp://www.alertlogic.com/ Secure Cloud Review Bloghttp://www.securecloudreview.com/Email: misha@alertlogic.comTwitter: @CToMG

