Presentazione Enginet
- 1. !
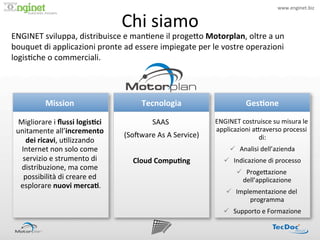
- 2. www.enginet.biz ? Chi ?siamo ? ! ENGINET ?sviluppa, ?distribuisce ?e ?man:ene ?il ?proge<o ?Motorplan, ?oltre ?a ?un ? bouquet ?di ?applicazioni ?pronte ?ad ?essere ?impiegate ?per ?le ?vostre ?operazioni ? logis:che ?o ?commerciali. ? Mission ? ? Tecnologia ? Ges/one ? Migliorare ?i ??ussi ?logis/ci ? SAAS ? ? ENGINET ?costruisce ?su ?misura ?le ? unitamente ?allĪ»incremento ? applicazioni ?a<raverso ?processi ? (SoIware ?As ?A ?Service) ? di: ? dei ?ricavi, ?u:lizzando ? Internet ?non ?solo ?come ? ? ©╣?? Analisi ?dellĪ»azienda ? servizio ?e ?strumento ?di ? Cloud ?Compu/ng ? ©╣?? Indicazione ?di ?processo ? distribuzione, ?ma ?come ? ©╣?? Proge<azione ? possibilit©ż ?di ?creare ?ed ? dellĪ»applicazione ? esplorare ?nuovi ?merca/. ? ©╣?? Implementazione ?del ? programma ? ©╣?? Supporto ?e ?Formazione ?
- 3. www.enginet.biz ? Cosa ?facciamo ? ! A<raverso ?la ?distribuzione ?online ?dei ?nostri ?strumen:, ?diamo ?la ?possibilit©ż ?alle ? aziende ?di ?a?acciarsi ?sul ?web ?rapidamente ?e ?con ?un ?basso ?costo ?di ?ingresso. ? Ricerca ? Comunicazione ?e ?Marke/ng ? Monitoraggio ?novit©ż ?in ?ambito ?tecnologico ? OPmizzazione ?del ?:me ?to ?market. ?Di?usione ? applicabili ?alle ?soluzioni ?des:nate ?agli ? delle ?informazioni ?e ?realizzazione ?di ?campagne ? operatori ?della ??liera ?dellĪ»AIermarket. ? pubblicitarie ?su ?misura ?per ?ogni ?azienda. ? Consulenza ? Sviluppo ? Analisi ?dellĪ»azienda ?in ?ogni ?suo ?aspe<o ?per ? Proge<o ?del ?soIware ?e ?veri?ca ?del ?suo ? la ?piani?cazione ?del ?percorso ?che ?porta ? funzionamento ?in ?ambiente ?web. ? allĪ»obiePvo. ?
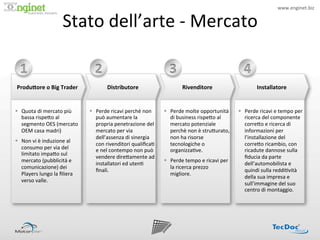
- 4. www.enginet.biz ? Stato ?dellĪ»arte ?-?®\ ?Mercato ? ! 1 ? 2 ? 3 ? 4 ? Produ=ore ?o ?Big ?Trader ? Distributore ? Rivenditore ? Installatore ? Īņ?? Quota ?di ?mercato ?pi©┤ ? Īņ?? Perde ?ricavi ?perch©© ?non ? Īņ?? Perde ?molte ?opportunit©ż ? Īņ?? Perde ?ricavi ?e ?tempo ?per ? bassa ?rispe<o ?al ? pu©░ ?aumentare ?la ? di ?business ?rispe<o ?al ? ricerca ?del ?componente ? segmento ?OES ?(mercato ? propria ?penetrazione ?del ? mercato ?potenziale ? corre<o ?e ?ricerca ?di ? OEM ?casa ?madri) ? mercato ?per ?via ? perch©© ?non ?©© ?stru<urato, ? informazioni ?per ? dellĪ»assenza ?di ?sinergia ? non ?ha ?risorse ? lĪ»installazione ?del ? Īņ?? Non ?vi ?©© ?induzione ?al ? con ?rivenditori ?quali?ca: ? tecnologiche ?o ? corre<o ?ricambio, ?con ? consumo ?per ?via ?del ? e ?nel ?contempo ?non ?pu©░ ? organizza:ve. ? ricadute ?dannose ?sulla ? limitato ?impa<o ?sul ? vendere ?dire<amente ?ad ? ?ducia ?da ?parte ? mercato ?(pubblicita? ?e ? Īņ?? Perde ?tempo ?e ?ricavi ?per ? installatori ?ed ?uten: ? dellĪ»automobilista ?e ? comunicazione) ?dei ? la ?ricerca ?prezzo ? ?nali. ? quindi ?sulla ?reddi:vit©ż ? Players ?lungo ?la ??liera ? migliore. ? della ?sua ?impresa ?e ? verso ?valle. ? sullĪ»immagine ?del ?suo ? centro ?di ?montaggio. ?
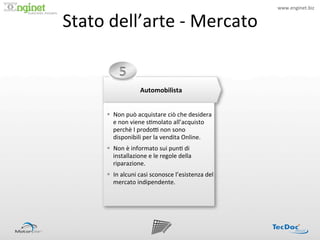
- 5. www.enginet.biz ? Stato ?dellĪ»arte ?-?®\ ?Mercato ? ! 5 ? Automobilista ? Īņ?? Non ?pu©░ ?acquistare ?ci©░ ?che ?desidera ? e ?non ?viene ?s:molato ?allĪ»acquisto ? perch©© ?I ?prodoP ?non ?sono ? disponibili ?per ?la ?vendita ?Online. ? Īņ?? Non ?©© ?informato ?sui ?pun: ?di ? installazione ?e ?le ?regole ?della ? riparazione. ? Īņ?? In ?alcuni ?casi ?sconosce ?lĪ»esistenza ?del ? mercato ?indipendente. ?
- 6. www.enginet.biz ? ! Cri:cit©ż ?informa:ve ?e ?ges:onali ? Aumento ?delle ?informazioni ? La ?crescita ?del ?parco ?circolante, ?non ?solo ?inteso ?come ?numero ?di ?unit©ż ?presen: ?sulle ?strade ?, ?ma ?anche ?so<o ?il ? pro?lo ?dei ?modelli ?e ?rela:vi ?:pi ?di ?veicoli ?presen: ?sul ?mercato, ?sommato ?allĪ»aumento ?del ?numero ?di ?pezzi ?di ?cui ? ©© ?composta ?una ?ve<ura, ?ha ?richiesto ?per ?lĪ»iden/?cazione ?delle ?par: ?di ?ricambio ?e ?la ?riparazione, ?una ?quan:t©ż ? di ?informazioni ?che ?il ?mercato ?e ?gli ?operatori ?non ?erano ?prepara: ?a ?ges:re, ?sia ?a ?livello ?culturale ?che ?di ? infrastru<ura ?aziendale. ? 1960 ? 1970 ? 1980 ? 1990 ? 2000 ? 2010 ? 2020 ? Cambiamento ?nel ?modello ?di ?ges/one ?del ?magazzino ? Inoltre ?il ?modello ?di ?ges:one ?degli ?stock ?in ?magazzino ?mutato ?da ?ver/cale ?(pochi ?ar:coli ?mol: ?pezzi) ?ad ? orizzontale ?(mol: ?ar:coli ?pochi ?pezzi) ?, ?ha ?comportato ?un ?ne<o ?aumento ?nel ?numero ?di ?transazioni ?per ? soddisfare ?le ?esigenze ?dei ?clien:, ?facendo ?emergere ?le ?vulnerabilit©ż ?del ?processo ?documentale, ?di ?inventario ?e ? price ?management. ?
- 7. www.enginet.biz ? IL ?NOSTRO ?OBIETTIVO ? ! A<raverso ?lĪ»adozione ?di ?informazioni, ?e ?la ?creazione ?di ?strumen: ?e ? procedimen: ?basa: ?sul ?conce<o ?di ?standard, ?ci ?siamo ?pos: ? lĪ»obiePvo, ?di ?rendere ?pi©┤ ?e?cace ?e ?meno ?costosa ?la ?ges:one ?della ? logis:ca ?dei ?ricambi. ?Agevolando ?cos©¼: ? ©╣?? i ?processi ?di ?vendita ?delle ?imprese, ? ? ©╣?? la ?loro ?penetrazione ?sul ?mercato, ? ? ©╣?? la ??delizzazione ?dei ?clien:, ? ? ©╣?? il ?consolidamento ?della ?presenza ?aziendale ?sul ?territorio, ?e ? ? ©╣?? lĪ»esplorazione ?di ?nuovi ?merca:. ?
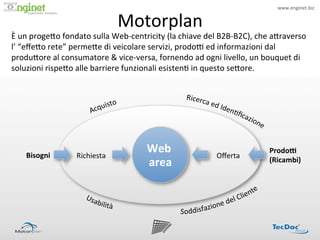
- 8. www.enginet.biz ? Motorplan ? ! ? ?un ?proge<o ?fondato ?sulla ?Web-?®\centricity ?(la ?chiave ?del ?B2B-?®\B2C), ?che ?a<raverso ? lĪ» ?Ī░e?e<o ?reteĪ▒ ?perme<e ?di ?veicolare ?servizi, ?prodoP ?ed ?informazioni ?dal ? produ<ore ?al ?consumatore ?& ?vice-?®\versa, ?fornendo ?ad ?ogni ?livello, ?un ?bouquet ?di ? soluzioni ?rispe<o ?alle ?barriere ?funzionali ?esisten: ?in ?questo ?se<ore. ? Bisogni ? Richiesta ? Web ? O?erta ? ProdoO ? area ? (Ricambi) ?
- 9. www.enginet.biz ? ! Il ?proge<o ?perme<e ?di ?a<uare ?processi ?di ?Vendita ? di ?:po ?B2B ?e ?B2C ? Market ? B ?-?®\ ?to ?-?®\ ?B ? B ?-?®\ ?to ?-?®\ ?C ? Business-?®\to-?®\Business ? Business-?®\to-?®\Customer ? ? ? Ovvero ?Azienda ?verso ?Azienda: ? ? Ovvero ?Azienda ?verso ?Cliente ? ? ? ©© ?il ?caso ?dei ?produ<ori ?verso ?I ?distributori ?e ?di ?ques: ? ? ?il ?caso ?degli ?installatori ?o ?dei ?rivenditori ?vero ?gli ? verso ?I ?rivenditori ?o ?installatori ? automobilis: ?
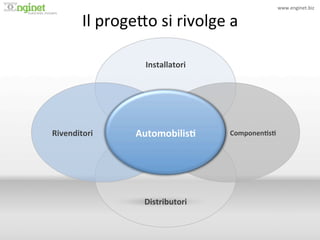
- 10. www.enginet.biz ? Il ?proge<o ?si ?rivolge ?a ? ! Installatori ? Rivenditori ? Automobilis/ ? Componen/s/ ? Distributori ?
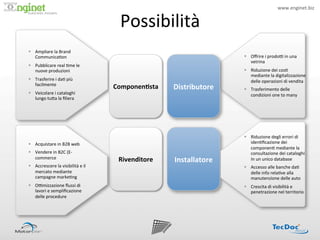
- 11. www.enginet.biz ? Possibilit©ż ? ! Īņ?? Ampliare ?la ?Brand ? Communica:on ? Īņ?? O?rire ?i ?prodoP ?in ?una ? vetrina ? Īņ?? Pubblicare ?real ?:me ?le ? nuove ?produzioni ? Īņ?? Riduzione ?dei ?cos: ? mediante ?la ?digitalizzazione ? Īņ?? Trasferire ?i ?da: ?pi©┤ ? delle ?operazioni ?di ?vendita ? facilmente ? Componen/sta ? Distributore ? Īņ?? Trasferimento ?delle ? Īņ?? Veicolare ?i ?cataloghi ? condizioni ?one ?to ?many ? lungo ?tu<a ?la ??liera ? Īņ?? Riduzione ?degli ?errori ?di ? Īņ?? Acquistare ?in ?B2B ?web ? iden:?cazione ?dei ? componen: ?mediante ?la ? Īņ?? Vendere ?in ?B2C ?(E-?®\ consultazione ?dei ?cataloghi ? commerce ? Rivenditore ? Installatore ? In ?un ?unico ?database ? Īņ?? Accrescere ?la ?visibilit©ż ?e ?il ? Īņ?? Accesso ?alle ?banche ?da: ? mercato ?mediante ? delle ?info ?rela:ve ?alla ? campagne ?marke:ng ? manutenzione ?delle ?auto ? Īņ?? OPmizzazione ??ussi ?di ? Īņ?? Crescita ?di ?visibilit©ż ?e ? lavori ?e ?sempli?cazione ? penetrazione ?nel ?territorio ? delle ?procedure ?
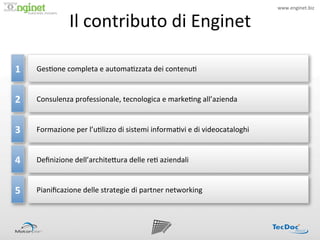
- 12. www.enginet.biz ? Il ?contributo ?di ?Enginet ? ! 1 ? Ges:one ?completa ?e ?automa:zzata ?dei ?contenu: ? 2 ? Consulenza ?professionale, ?tecnologica ?e ?marke:ng ?allĪ»azienda ? 3 ? Formazione ?per ?lĪ»u:lizzo ?di ?sistemi ?informa:vi ?e ?di ?videocataloghi ? 4 ? De?nizione ?dellĪ»archite<ura ?delle ?re: ?aziendali ? 5 ? Piani?cazione ?delle ?strategie ?di ?partner ?networking ?
- 13. www.enginet.biz ? Strumen: ? ! U:li ?alla ?ges:one ?e ?vendita ?delle ?par: ?di ?ricambio, ?le ?applicazioni ?da ?noi ?realizzate ?coprono ? dallĪ»iden:?cazione ??no ?allĪ»intero ?processo ?documentale ?e ?logis:co. ?TuP ?i ?nostri ?strumen: ? sono ?semplici ?da ?u:lizzare, ?e ?sono ?fruibili ?da ?ogni ?parte ?del ?mondo ?per ?mezzo ?di ?un ?pc ?ed ? una ?connessione ?a ?internet. ? 1 ? 2 ? 3 ? ? ?il ?modulo ?di ?registrazione ? Presentazione ?dellĪ»azienda ? EĪ» ?il ?catalogo ?web ?delle ?par: ? per ?I ?nuovi ?clien: ?e ?il ? su ?web ?con ?una ?immagine ? di ?ricambio ?basato ?sulle ? portale ?dĪ»accesso ?per ?quelli ? professionale. ? informazioni ?di ?TecDoc. ? gi©ż ?esisten:. ? 4 ? 5 ? 6 ? 7 ? EĪ» ?una ?banca ?da: ?Ī░trustĪ▒ ? EĪ» ?il ?sistema ?di ?commercio ? contenente ?informazioni ? ? ?un ?ges:onale ?delle ?merci ? EĪ» ?un ?sistema ?per ?la ? ele<ronico, ?integrabile ?con ? e ?dei ?documen:, ?concepito ? creazione ?di ?cataloghi, ? rela:ve ?allĪ»anagra?ca ?degli ? informazioni ?ed ?altri ? per ?risolvere ?le ?complessit©ż ? modulabile ?in ?base ?ai ?ogni ? ar:coli ?dei ?ricambi ?ed ? strumen: ?quale ?il ?catalogo. ? accessori. ? dellĪ»AIermarket. ? esigenza ?o ?ruolo. ?
- 14. www.enginet.biz ? Strumen: ? ! U:li ?alla ?ges:one ?e ?vendita ?delle ?par: ?di ?ricambio, ?le ?applicazioni ?da ?noi ?realizzate ?coprono ? dallĪ»iden:?cazione ??no ?allĪ»intero ?processo ?documentale ?e ?logis:co. ?TuP ?i ?nostri ?strumen: ? sono ?semplici ?da ?u:lizzare, ?e ?sono ?fruibili ?da ?ogni ?parte ?del ?mondo ?per ?mezzo ?di ?un ?pc ?ed ? una ?connessione ?a ?internet. ? 8 ? 9 ? 10 ? ? ?il ?catalogo ?integrabile ? ? ?il ?plugin ?che ?perme<e ?di ? ? ?il ?sistema ?di ?fruizione ?dei ? allĪ»interno ?di ?si: ?esisten:, ? creare ?annunci ?nel ?famoso ? prezzi ?di ?lis:no ?e ?le ?accessori, ? ad ?esempio ?sistemi ?di ?e-?®\ portale ?E-?®\bay ?con ?un ? integrabili ?in ?ges:onali ?o ?e ? commerce ?B2B ?o ?B2C. ? semplice ?click. ? anagra?che ?di ?ricambi ? ecommerce ?esisten:. ? 11 ? 12 ? 13 ? ? ?il ?sistema ?che ?perme<e ?di ? ? ?il ?sistema ?che ?perme<e ?di ? Abbiamo ?mol: ?altri ? concatenare ?disponibilit©ż ?e ? o<enere ?risulta: ?rela:vi ?a ? progeP ?in ?fase ?di ? prezzi, ?ricalcolandoli ?in ?tempo ? cross-?®\reference ?tramite ? reale, ?a ?vari ?livelli ?della ??liera ? sviluppo ?dedica: ? codice ?OE ?o ?concorrente, ? distribu:va ?in ?ordine ?top-?®\ integrabile ?in ?ges:onali ?o ?e-?®\ allĪ»AIermarket ? down. ? commerce ?esisten:. ? automobilis:co.. ?
- 15. www.enginet.biz ? partsNet ? ! ? ?un ?ecosistema ?digitale ?dedicato ?al ?comparto ?della ?componen:s:ca ?per ?le ? automobili, ?i ?veicoli ?commerciali ?ed ?industriali. ?Il ?proge<o ?nasce ?per ?risolvere ? problemi ?comuni, ?presen: ?nel ?se<ore ?AIermarket ?dei ?componen: ?e ?ricambi ?per ? le ?automobili ?i ?veicoli ?commerciali ?e ?industriali, ?che ?con ?il ?loro ?ciclico ?e ?quo:diano ? manifestarsi, ?fanno ?disperdere ?ricchezza ??no ?a ?creare ?perdite, ?lungo ?la ?catena ?del ? valore. ?
- 16. www.enginet.biz ? partsNet ? ! LĪ»ecosistema ?digitale ?che ?lo ?compone ?©© ?rappresentato ?da ?un ?bouquet ?di ?soluzioni ? soIware ?e ?banche ?da: ?che, ?dialogando ?tra ?loro, ?rendono ??uidi, ?rapidi, ?precisi ?ed ? economici ?i ?processi ?di ?ges:one ?e ?vendita ?dei ?ricambi; ?questo ?perme<e ?alle ? imprese ?coinvolte ?di ?estendere ?o ?consolidare, ?in ?maniera ?dinamica, ?la ?loro ? presenza ?nella ?nuova ?economia ?del ?commercio ?ele<ronico. ? Tempi ?di ?riparazione ? ERP ? (opzionale) ? Catalogo ?prodoP ? Da: ?tecnici ?di ? manutenzione ? (opzionale) ? Connessione ?in ?tempo ? reale ?ai ?sistemi ?di ? Banca ?da: ?anagra?ca ? fornitori ?e ?partner ? ar:coli ? Sistemi ?di ? ges:one ?
- 17. www.enginet.biz ? ObiePvi ? ! Comunicazione ?e?cace ? Rapido ?TTM ? Iden/t©ż ?e ?Immagine ?Aziendale ? Fornisci ?un ?completo ?strumento ?di ? Sviluppa ?e ?di?ondi ?il ?proge<o ?del ? Crea ?o ?rinnova ?la ?tua ?iden:t©ż ? iden:?cazione, ?quotazione ?ed ? tuo ?network ?privato, ?in ?tempi ? aziendale, ?a<raverso ?una ? informazione, ?basato ?sulle ? rapidi, ?in ?maniera ??essibile, ? web-?®\presence ?accaPvante. ? informazioni ?europee, ?originali ?e ? potenzialmente ?scalabile ?ed ?in ? standardizzate ?di ?TecDoc ? funzione ?del ?tuo ?budget. ?La ?nostra ? Per ?mezzo ?della ?nostra ? Informa:ons ?System. ?Un ? soluzione ?precon?gurata ?pensata ? formula, ?potrai ?proporre ?i ?tuoi ? linguaggio ?univoco ?e ?rapido ?: ? per ?lĪ»AIermarket ?©© ?u:lizzabile ? prodoP ?o ?servizi ?conferendo ? perme<er©ż ?di ?evitare ?errori ?e ? dire<amente ?via ?internet. ?Ti ?basta ? loro ?un ?valore ?aggiunto. ?Potrai ? comunicare ?sempre ?le ?condizioni ? un ?pc ?ed ?una ?connessione ?ad ? vincere ?le ?s?de ?del ?mercato ? aggiornate ?rispe<o ?al ?mercato. ? internet ?per ?essere ?in ?rete, ?anzi ? sullĪ»onda ?del ?cambiamento. ? per ?fare ?RETE... ?
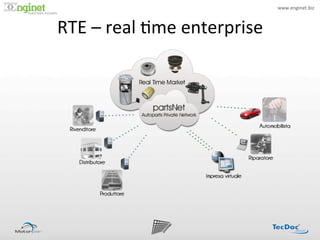
- 18. www.enginet.biz ? ! RTE ?©C ?real ?:me ?enterprise ?
- 19. www.enginet.biz ? Esempi ?applica:vi ? ! LĪ»u:lizzo ?e ?di?usione ?dei ?servizi ?soIware ?presen: ?allĪ»interno ?della ?pia<aforma ?©© ?applicabile ? in ?maniera ?elas:ca, ?in ?funzione ?dei ?ruoli, ?degli ?u:lizzatori ?e ?degli ?obiePvi. ? Distributori ? Rivenditori ? Autoriparatori ? Possono ?creare ?un ?network ? Possono ?distribuire ?agli ? Uno ?o ?pi©┤ ?distributori ?possono ? con ?i ?propri ?rivenditori, ?dando ? autoriparatori ?il ?catalogo ?con ? veicolare, ?in ?maniera ? loro ?la ?possibilit©ż ?di ?accedere ? le ?proprie ?condizioni ?di ? trasparente ?a<raverso ?i ?loro ? dire<amente ?alle ? vendita ?dando ?la ?possibilit©ż ?di ? rivenditori ?partner ?in ?direzione ? informazioni ?rela:ve ?al ? concludere ?lĪ»ordine ? degli ?autoriparatori, ?info ?in ? proprio ?magazzino, ? dire<amente ?online. ?Possono ? tempo ?reale ?circa ?le ? inoltre ?proporre ?le ? disponibilit©ż ?di ?magazzino ?e ?le ? dire<amente ?dal ?catalogo. ? informazioni ?rela:ve ?alla ? condizioni ?di ?vendita ?corren: ? ? manutenzione ?dei ?veicoli ? ricalcolate ?a ?caldo, ?creando ?cos©¼ ? processi ?di ?vendita ?innova:va, ? ? come ?leva ?di ?marke:ng. ? per ?mezzo ?della ?virtualizzazione ? ? ? degli ?stock. ?
- 20. www.enginet.biz ? Cosa ?ci ?cara<erizza ? ! Prezzi ?compe//vi ? E?cienza ?e ?velocit©ż ? Risulta/ ?cer/ ? ? ? ? Budget ?so<o ?controllo ?e ?basso ? RispePamo ?i ?tempi ?di ? Se ?u:le, ?sviluppiamo ?i ? costo ?iniziale: ?pra:camente ? consegna ?comunicando ?lo ? propo:pi ?delle ?applicazioni ?a ? nullo ?se ?comparato ?alle ? stato ?in ?corso ?dĪ»opera. ? garanzia ?del ?risultato. ? applicazioni ?in-?®\house. ?
- 21. www.enginet.biz ? Cosa ?ci ?rende ?innova:vi ? ! In ?un ?mercato ?sempre ?pi©┤ ?stagnante ?abbiamo ?bisogno ?di ?essere ?reaPvi ?ed ? innova:vi: ?Il ?WEB ?©© ?la ?risposta. ?
- 22. www.enginet.biz ? Che ?cosĪ«©© ?lĪ«e-?®\commerce ? ! Il ?commercio ?ele<ronico ?o ?e-?®\commerce ?©© ?l'acquisto ?di ?beni ? e ?servizi ?a<raverso ?il ?Web ?ricorrendo ?a ?server ?sicuri, ?con ? servizi ?di ?pagamento ?in ?linea, ?come ?le ?autorizzazioni ?per ?il ? pagamento ?con ?carta ?di ?credito. ?
- 23. www.enginet.biz ? Pensi ?sia ?di?cile? ? ! Īņ??Credi ?di ?non ?avere ?il ?TEMPO ?di ? seguire ?questa ?aPvit©ż? ? Īņ??Credi ?di ?non ?avere ?le ? CONOSCENZE ?TECNICHE ?per ? a<uarla? ? Īņ??Credi ?di ?non ?avere ?STRUMENTI ? EFFICACI ?per ?trarne ?pro?<o? ?
- 24. www.enginet.biz ? ENGINET ?lo ?fa ?per ?te ? ! Ti ?por:amo ?online ?in ?modo ?semplice, ?e?cace ?e ?in ?breve ?tempo ? Promozione ?economia ? ? del ?territorio ? Creazione ?di ?si: ?web ? ? Database ?online ? ? per ?la ?vendita ?dire<a ? Posizionamento ? Mul/-?®\Channel ? Promozione ?AIermarket ? sui ?motori ?di ?ricerca ? Marke/ng ? Indipendente ? Informa:zzazione ? ? Marke:ng ?INCISIVO ? dellĪ»aPvit©ż ? Social ?Media ?
- 25. www.enginet.biz ? ! Perch©© ?informa:zzarsi ?e ?vendere ?sul ? web? ? Grazie ?agli ?strumen: ?ges:onali ? ?e ?commerciali ? idea: ?da ?ENGINET, ?nella ?tua ?aPvit©ż ?puoi: ? Īņ?? OPmizzare ?i ??ussi ?di ?lavoro ? Īņ?? Catalogare ?semplicemente ?tuP ?i ?tuoi ?prodoP ? Īņ?? Tenere ?costantemente ?monitora: ?tuP ?i ? parametri ?di ?acquisto ?e ?vendita ?per ?mostrar: ? dove ?sono ?possibili ?i ?margini ?maggiori ? Īņ?? Ges:re ?la ?logis:ca ?con ?i ?tuoi ?fornitori ? Īņ?? Collegare ?il ?tuo ?catalogo ?ad ?ANYcom ?per ? vendere ?online ?e ?aprire ?le ?porte ?a ?NUOVI ? MERCATI ? Īņ?? SEMPLIFICARE ?il ?ciclo ?di ?vita ?e ?di ?ges:one ?dei ? prodoP ?circolan: ?del ?se<ore ?dellĪ«AIermarket ?
- 26. www.enginet.biz ? ! Promozione ?della ?tua ?azienda ? Con ?ENGINET ?la ?tua ?azienda ?si ?rinnova ?e ?diventa ?pronta ?ad ?a?rontare ?le ?s?de ?del ? futuro ? Un ?team ? ? di ?professionis: ? ? al ?tuo ?servizio ? Campagne ?incisive ? ? Vantaggi ?economici ? ? studiate ?a<entamente ?per ? dallĪ»apertura ?a ?nuovi ? la ?tua ?azienda ? segmen: ?di ?mercato ? Rapidit©ż ?dei ?lavori ? Inves/men/ ?minimi ?
- 27. www.enginet.biz ? ! Promozione ?dellĪ»AIermarket ? Indipendente ? Un ?automobilista ?pi©┤ ?consapevole ?dei ?propri ?diriP ?©© ?un ?automobilista ?che ?si ?reca ? presso ?la ?tua ?azienda ?con ??ducia ?e ?serenit©ż, ?per ?trovare ?la ?stessa ?qualit©ż ?dei ?canali ? u?ciali ?con ?prezzi ?ne<amente ?inferiori, ?in ?pi©┤ ?vicino ?a ?casa! ? C4 ? C5 ? C3 ? C2 ? C1 ?
- 28. www.enginet.biz ? Conclusioni ? ! Vogliamo ?costruire ?un ?circolo ?virtuoso ?dello ?sviluppo ?per ?una ?nuova ?compe::vit©ż ? basata ?sullĪ»innovazione ? SVILUPPO ?
- 29. www.enginet.biz ? ! Mol: ?mo:vi ?per ?farlo, ?ma ?due ?su ?tuP ? Aderisci ?al ?nostro ?sistema: ? ©╣?? Per ?la ?crescita ?del ?se<ore ? ©╣?? Per ?il ?rispe<o ?della ?natura ?
- 30. www.enginet.biz ? ! LĪ»AIermarket ?©© ?al ?capolineaĪŁ ?
- 31. www.enginet.biz ? ! ĪŁ? ?ora ?di ?par:re! ?
- 32. !