The karma of sharing information over the web
Download as ppt, pdf0 likes422 views
The document discusses the significance and risks of sharing information online, highlighting different stages of the web's evolution from Web 1.0 to Web 3.0. It emphasizes the importance of web security, privacy, and being cautious with personal information, particularly on social media platforms like Facebook. Additionally, it covers best practices for digital safety and provides an overview of Creative Commons licenses for content sharing.
1 of 37
Downloaded 11 times





























![[email_address] http://facebook.com/ sankaranand http://twitter.com/ sankaranand http://linkedin.com/in/ sankaranand http://profiles.google.com/ smartjean4u www. sankaranand .com Connect ME](https://image.slidesharecdn.com/thekarmaofsharinginformationovertheweb-110802124941-phpapp02/85/The-karma-of-sharing-information-over-the-web-37-320.jpg)
Ad
Recommended
Get More Links to Your Site With the Skyscraper Technique
Get More Links to Your Site With the Skyscraper TechniqueRachel Fredrickson
Ěý
The skyscraper technique is a proven SEO strategy focused on creating exceptional content to generate links. It involves identifying link-worthy content, improving upon it, and then conducting targeted outreach to relevant site owners. The process emphasizes the importance of promoting content effectively, leading to higher chances of acquiring backlinks.Tips for Social Media Supplement
Tips for Social Media SupplementCarmen Saunders, MSN, FNP-BC
Ěý
This document defines various social media platforms and provides guidance on using them professionally. It discusses Twitter, Facebook, LinkedIn, Pinterest, Google+, blogging, and privacy/security settings. Key recommendations include using different accounts for personal and professional use, carefully managing privacy settings, and measuring social media success through metrics like reach, visibility, and influence.Coordinating a geographically dispersed research project using social
Coordinating a geographically dispersed research project using socialMichael Paskevicius
Ěý
The document outlines a strategy for coordinating a geographically dispersed research project using social media, emphasizing the role of platforms like WordPress and Twitter in facilitating communication. It discusses the tools available for sharing ideas and content, as well as methods for engaging participants and keeping discussions ongoing. The guidance includes tutorials on using WordPress for contributions and utilizing Twitter for networking and sharing content effectively.How to break the internet
How to break the internetPaul Johnston
Ěý
The document discusses how aggregators on the internet can lead to "SpamBack" if they are not properly programmed. It describes how a feedback loop could be created by posting content from one service to another and back again, without recognizing that the content has already been seen. To prevent this, the document suggests that aggregators check for a unique content ID and drop any content that has already been associated with that ID. As more services aggregate content, addressing this issue of SpamBack will become more important to avoid overloading systems on the internet.Do-Follow Blogs
Do-Follow BlogsMike Gates
Ěý
The document details the evolution of the do-follow movement in the context of internet commerce and search engine optimization. After the introduction of the nofollow tag to combat link spamming, bloggers found a way to encourage valuable comments by reintroducing do-follow links through a WordPress plugin. This shift fostered a supportive community where meaningful contributions were rewarded, ultimately revitalizing the blogging landscape.Riann salandanan howtouse_stayfocusd
Riann salandanan howtouse_stayfocusdRiann Salandanan
Ěý
The document provides step-by-step instructions for setting up and using the StayFocused productivity extension for Google Chrome. It explains how to download and install Chrome, add the StayFocused extension, and customize its settings to block distracting websites and limit browsing time. Settings include blocking specific sites or categories of sites, setting daily and hourly limits on browser use, and enabling a "nuclear option" to completely block all sites except those allowed. The goal is to help users stay focused on their work by restricting access to irrelevant websites.Riann salandanan howtouse_hootsuite
Riann salandanan howtouse_hootsuiteRiann Salandanan
Ěý
This document provides a step-by-step guide to using HootSuite for beginners. It explains how to sign up for a HootSuite account and connect social media profiles like Facebook, Twitter, and LinkedIn. It then demonstrates how to create posts, schedule posts, and view analytics. It also discusses upgrading your account for additional features like custom scheduling and detailed reports.Taking Advantage of Semantic Web
Taking Advantage of Semantic WebSankaranand Balaradjou
Ěý
This document discusses the evolution of the web and the concept of the semantic web. It defines the semantic web as a web with meaning where data is interlinked and searchable. The key aspects of the semantic web include using technologies like RDF, OWL and SPARQL to embed relationships and definitions within data to make it more meaningful and accessible to machines. This allows for more personalized searches and access to accurate information. Challenges include developing open standards for ontologies.Social Media 101 - Optimizing Facebook and Twitter for your Nonprofit
Social Media 101 - Optimizing Facebook and Twitter for your NonprofitMagnifyGood
Ěý
The document provides an overview of using social media platforms like Facebook and Twitter for organizational purposes. It discusses setting goals, understanding key audiences, identifying influencers, listening to conversations, and curating relevant content for each platform. The presentation includes exercises for participants to practice tasks like creating social media profiles, posts, hashtags and tagging other users.Test slideshow
Test slideshowlegacye
Ěý
The document discusses security issues related to JavaScript and the web, highlighting problems like cross-site scripting attacks and the lack of capability controls that allow scripts to access resources without restrictions. It proposes using an object capability model and techniques like ADsafe to constrain what scripts can do by only allowing the acquisition of references through trusted means. The goal is to redesign the DOM and JavaScript to build security in from the start through confinement and least privilege instead of trying to add it later.Test slideshow
Test slideshowlegacye
Ěý
The document discusses security issues related to JavaScript and the web, highlighting problems like cross-site scripting attacks and how current approaches confuse the interests of users and programs; it proposes using an object capability model and strict containment of references to address these issues by distinguishing access and preventing unintended communication between objects. Several approaches are presented that aim to provide security by limiting the capabilities granted to code, including ADsafe which defines a safe JavaScript subset, and Caja which uses runtime rewriting to enforce capabilities.Test slideshow
Test slideshowlegacye
Ěý
The document discusses security issues related to Ajax and JavaScript. It summarizes how a hacker named Samy was able to infect over 1 million MySpace profiles in 2005 by hiding malicious JavaScript in a URL. It then outlines the security risks if an attacker is able to inject scripts into a user's web page, including being able to make requests to any server, access the user's browser history and cookies, and potentially access the website's database. The document argues that the web's security model is flawed and that an object capability model is needed to properly separate privileges and reduce security risks.Test slideshow
Test slideshowlegacye
Ěý
The document discusses security issues related to Ajax and JavaScript. It summarizes how a hacker named Samy was able to infect over 1 million MySpace profiles in 2005 by hiding malicious JavaScript in a URL. It then outlines the security risks if an attacker is able to inject scripts into a user's web page, including being able to make requests to any server, access the user's browser history and cookies, and potentially access the website's database. The document argues that the web's security model is flawed and that an object capability model is needed to properly separate privileges and reduce security risks.Empowerment technology
Empowerment technologypizonaim
Ěý
The document provides an extensive overview of empowerment technology and its relevance to current information and communication technology (ICT). It covers various topics including different web stages (Web 1.0 to Web 3.0), technology convergence, online dangers, research skills, and practical tools like Microsoft PowerPoint and Excel. Additionally, it addresses media literacy, copyright issues, digital file formats, and basic graphic design principles essential for effective digital communication.Architecture of RIA from JAOO
Architecture of RIA from JAOOJosh Holmes
Ěý
The document discusses rich internet applications (RIA) and their architecture, emphasizing the importance of user experience and appropriate development practices. It covers design patterns like MVP and MVC, highlighting their roles in unit testing and model presentation. Additionally, it addresses security considerations for cookies and public services, advocating for secure handling of user data.Social Networking Tools for Novices
Social Networking Tools for NovicesUS Environmental Protection Agency (EPA), Center for Computational Toxicology and Exposure
Ěý
The document provides guidance for scientists on how to effectively brand themselves and engage in social networking online. It covers various platforms such as blogging, Twitter, LinkedIn, and şÝşÝߣShare, emphasizing the importance of consistency in branding and sharing one’s work. The author, Antony Williams, encourages scientists to actively participate in the digital community to enhance their professional reputation and collaboration opportunities.Empowerment technology
Empowerment technology jonaspalen1
Ěý
This document discusses information and communication technology (ICT) and how it can be used across different fields like education, commerce, health services, and more. It explains the evolution of the World Wide Web from static Web 1.0 to more interactive Web 2.0 and the emerging data-driven Web 3.0. The document also discusses technology convergence using smartphones as an example. It covers social media platforms and online dangers like spam, spoofing, and hacking. Finally, it provides guidance on contextualized online research and detecting satirical news sources.Basics of web
Basics of webRounak Samdadia
Ěý
The document provides an overview of key concepts related to the basics of the web, including definitions and explanations of clients, servers, web browsers, web servers, and the request-response cycle between clients and servers. It also discusses components that make up websites, such as HTML, CSS, JavaScript, content management systems, and database management systems.Hacking For Innovation
Hacking For InnovationChristian Heilmann
Ěý
Christian Heilmann gave a talk on hacking and innovation at a university hack challenge. He defines hacking as altering systems to do what you want using available resources, and sees it as a way to have fun and drive unrestrained innovation. He encourages attendees to find something annoying with current systems and build workarounds. To hack effectively, one needs access to data sources, the data itself, and ways to reach users. He provides examples of his own hacks that make systems more accessible or filter data for specific uses. The talk aims to show attendees their potential and get feedback on explanations of development resources.2008 10 21 Top Ten Tech Tools Agents E Xtension
2008 10 21 Top Ten Tech Tools Agents E Xtensiondkp205
Ěý
The document outlines the top 30 tech tools beneficial for extension agents and web managers, emphasizing that technology should focus on enhancing human interaction. It covers various categories of tools, including productivity, research, client interaction, online collaboration, and web analytics, while also discussing the evolution from Web 1.0 to Web 2.0. Key suggestions include utilizing wikis, Google Docs, online surveys, and e-mail encryption to improve communication and efficiency.Open Source Microblogging With Laconica
Open Source Microblogging With LaconicaEvan Prodromou
Ěý
Evan introduces himself and his work on open source microblogging software projects. He created Laconica, an open source PHP/MySQL microblogging platform that implements the Twitter API. He also developed the OpenMicroblogging protocol for distributed microblogging across servers and the StatusNet software-as-a-service platform. His goal is for open microblogging software to allow enterprises, brands, and communities to have decentralized alternatives to centralized platforms like Twitter.E-commerce Lab work
E-commerce Lab workPragya Bisht
Ěý
This document is a lab file on e-commerce submitted as part of the requirements for the Bachelor of Commerce program. It covers various topics including website features, the roles of browsers, and search engine functionality, providing detailed explanations and examples. The lab file is a comprehensive guide to understanding essential e-commerce concepts and their practical applications.Commercial Break: Linked Data for Business
Commercial Break: Linked Data for Businesszbeauvais
Ěý
Linked data and the use of graphs are enabling new business opportunities around data. Companies can directly monetize their datasets by selling them on emerging data marketplaces like Kasabi, which is being built on linked data principles. As data becomes more interconnected and useful, current tools will get smarter and new applications and business models will emerge, fueled by the ability to browse, buy, and leverage linked datasets.Why Portability matters (full presentation)
Why Portability matters (full presentation)Ian Forrester
Ěý
The document discusses the importance of data portability on the web. It notes that users should have control over their own data and be able to easily move it between services. However, many current systems lock users into specific platforms by not allowing easy export or transfer of data. The document outlines several principles of user-controlled data portability and highlights examples of both good and bad practices among different web companies and technologies. It argues that users need more freedom and control over their personal information on the internet.Web engineering lecture 3
Web engineering lecture 3University of Swat
Ěý
This document provides an overview of key concepts related to the internet and the world wide web. It defines common terms like internet, internet services, websites, web servers, web browsers, URLs, HTML, and hyperlinks. It describes how the web works by explaining the role of domain name servers, IP addresses, and how web pages are requested and delivered. Finally, it outlines several advantages of having a website like being open 24/7, increasing customer base, cost savings, improved advertising and creating a brand image.Web spoofing (1)
Web spoofing (1)Khushboo Taneja
Ěý
Web spoofing allows an attacker to create a fake version of the World Wide Web to trick victims. The attacker lures victims to their fake site, which looks identical to the real site. On the fake site, the attacker can observe any sensitive information entered by the victim. Current browsers are vulnerable to web spoofing attacks even on secure connections. Users should disable JavaScript, always check the URL bar, and be wary of any requests for sensitive information over email.Must have open source applications
Must have open source applicationsBrianJamison
Ěý
The document discusses must-have open source applications for small businesses. It recommends Trac for project management, Drupal for content management, and a Ruby on Rails ecommerce application. Trac is easy to install and use for tracking tasks and client feedback. Drupal allows adding content and custom modules for features like booking rooms and maps. The Ruby on Rails shopping cart recommends is clean, customizable, and extensible for payments.Make Me A Web 2.0 Geek!
Make Me A Web 2.0 Geek!BALTIC centre for contemporary art, BALTIC, Gateshead
Ěý
The document discusses the evolution and impact of new technologies, particularly web 2.0, emphasizing collaboration, user involvement, and the transition from desktop to browser-based technologies. It highlights the importance of adapting to change, utilizing content effectively, and the challenges presented by misinformation on the internet. Additionally, it outlines various web technologies, tools, and principles that support online collaboration while cautioning about the potential dangers and difficulties in managing digital content.Smarter Aviation Data Management: Lessons from Swedavia Airports and Sweco
Smarter Aviation Data Management: Lessons from Swedavia Airports and SwecoSafe Software
Ěý
Managing airport and airspace data is no small task, especially when you’re expected to deliver it in AIXM format without spending a fortune on specialized tools. But what if there was a smarter, more affordable way?
Join us for a behind-the-scenes look at how Sweco partnered with Swedavia, the Swedish airport operator, to solve this challenge using FME and Esri.
Learn how they built automated workflows to manage periodic updates, merge airspace data, and support data extracts – all while meeting strict government reporting requirements to the Civil Aviation Administration of Sweden.
Even better? Swedavia built custom services and applications that use the FME Flow REST API to trigger jobs and retrieve results – streamlining tasks like securing the quality of new surveyor data, creating permdelta and baseline representations in the AIS schema, and generating AIXM extracts from their AIS data.
To conclude, FME expert Dean Hintz will walk through a GeoBorders reading workflow and highlight recent enhancements to FME’s AIXM (Aeronautical Information Exchange Model) processing and interpretation capabilities.
Discover how airports like Swedavia are harnessing the power of FME to simplify aviation data management, and how you can too."How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays
Ěý
We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. We’ll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.More Related Content
Similar to The karma of sharing information over the web (20)
Social Media 101 - Optimizing Facebook and Twitter for your Nonprofit
Social Media 101 - Optimizing Facebook and Twitter for your NonprofitMagnifyGood
Ěý
The document provides an overview of using social media platforms like Facebook and Twitter for organizational purposes. It discusses setting goals, understanding key audiences, identifying influencers, listening to conversations, and curating relevant content for each platform. The presentation includes exercises for participants to practice tasks like creating social media profiles, posts, hashtags and tagging other users.Test slideshow
Test slideshowlegacye
Ěý
The document discusses security issues related to JavaScript and the web, highlighting problems like cross-site scripting attacks and the lack of capability controls that allow scripts to access resources without restrictions. It proposes using an object capability model and techniques like ADsafe to constrain what scripts can do by only allowing the acquisition of references through trusted means. The goal is to redesign the DOM and JavaScript to build security in from the start through confinement and least privilege instead of trying to add it later.Test slideshow
Test slideshowlegacye
Ěý
The document discusses security issues related to JavaScript and the web, highlighting problems like cross-site scripting attacks and how current approaches confuse the interests of users and programs; it proposes using an object capability model and strict containment of references to address these issues by distinguishing access and preventing unintended communication between objects. Several approaches are presented that aim to provide security by limiting the capabilities granted to code, including ADsafe which defines a safe JavaScript subset, and Caja which uses runtime rewriting to enforce capabilities.Test slideshow
Test slideshowlegacye
Ěý
The document discusses security issues related to Ajax and JavaScript. It summarizes how a hacker named Samy was able to infect over 1 million MySpace profiles in 2005 by hiding malicious JavaScript in a URL. It then outlines the security risks if an attacker is able to inject scripts into a user's web page, including being able to make requests to any server, access the user's browser history and cookies, and potentially access the website's database. The document argues that the web's security model is flawed and that an object capability model is needed to properly separate privileges and reduce security risks.Test slideshow
Test slideshowlegacye
Ěý
The document discusses security issues related to Ajax and JavaScript. It summarizes how a hacker named Samy was able to infect over 1 million MySpace profiles in 2005 by hiding malicious JavaScript in a URL. It then outlines the security risks if an attacker is able to inject scripts into a user's web page, including being able to make requests to any server, access the user's browser history and cookies, and potentially access the website's database. The document argues that the web's security model is flawed and that an object capability model is needed to properly separate privileges and reduce security risks.Empowerment technology
Empowerment technologypizonaim
Ěý
The document provides an extensive overview of empowerment technology and its relevance to current information and communication technology (ICT). It covers various topics including different web stages (Web 1.0 to Web 3.0), technology convergence, online dangers, research skills, and practical tools like Microsoft PowerPoint and Excel. Additionally, it addresses media literacy, copyright issues, digital file formats, and basic graphic design principles essential for effective digital communication.Architecture of RIA from JAOO
Architecture of RIA from JAOOJosh Holmes
Ěý
The document discusses rich internet applications (RIA) and their architecture, emphasizing the importance of user experience and appropriate development practices. It covers design patterns like MVP and MVC, highlighting their roles in unit testing and model presentation. Additionally, it addresses security considerations for cookies and public services, advocating for secure handling of user data.Social Networking Tools for Novices
Social Networking Tools for NovicesUS Environmental Protection Agency (EPA), Center for Computational Toxicology and Exposure
Ěý
The document provides guidance for scientists on how to effectively brand themselves and engage in social networking online. It covers various platforms such as blogging, Twitter, LinkedIn, and şÝşÝߣShare, emphasizing the importance of consistency in branding and sharing one’s work. The author, Antony Williams, encourages scientists to actively participate in the digital community to enhance their professional reputation and collaboration opportunities.Empowerment technology
Empowerment technology jonaspalen1
Ěý
This document discusses information and communication technology (ICT) and how it can be used across different fields like education, commerce, health services, and more. It explains the evolution of the World Wide Web from static Web 1.0 to more interactive Web 2.0 and the emerging data-driven Web 3.0. The document also discusses technology convergence using smartphones as an example. It covers social media platforms and online dangers like spam, spoofing, and hacking. Finally, it provides guidance on contextualized online research and detecting satirical news sources.Basics of web
Basics of webRounak Samdadia
Ěý
The document provides an overview of key concepts related to the basics of the web, including definitions and explanations of clients, servers, web browsers, web servers, and the request-response cycle between clients and servers. It also discusses components that make up websites, such as HTML, CSS, JavaScript, content management systems, and database management systems.Hacking For Innovation
Hacking For InnovationChristian Heilmann
Ěý
Christian Heilmann gave a talk on hacking and innovation at a university hack challenge. He defines hacking as altering systems to do what you want using available resources, and sees it as a way to have fun and drive unrestrained innovation. He encourages attendees to find something annoying with current systems and build workarounds. To hack effectively, one needs access to data sources, the data itself, and ways to reach users. He provides examples of his own hacks that make systems more accessible or filter data for specific uses. The talk aims to show attendees their potential and get feedback on explanations of development resources.2008 10 21 Top Ten Tech Tools Agents E Xtension
2008 10 21 Top Ten Tech Tools Agents E Xtensiondkp205
Ěý
The document outlines the top 30 tech tools beneficial for extension agents and web managers, emphasizing that technology should focus on enhancing human interaction. It covers various categories of tools, including productivity, research, client interaction, online collaboration, and web analytics, while also discussing the evolution from Web 1.0 to Web 2.0. Key suggestions include utilizing wikis, Google Docs, online surveys, and e-mail encryption to improve communication and efficiency.Open Source Microblogging With Laconica
Open Source Microblogging With LaconicaEvan Prodromou
Ěý
Evan introduces himself and his work on open source microblogging software projects. He created Laconica, an open source PHP/MySQL microblogging platform that implements the Twitter API. He also developed the OpenMicroblogging protocol for distributed microblogging across servers and the StatusNet software-as-a-service platform. His goal is for open microblogging software to allow enterprises, brands, and communities to have decentralized alternatives to centralized platforms like Twitter.E-commerce Lab work
E-commerce Lab workPragya Bisht
Ěý
This document is a lab file on e-commerce submitted as part of the requirements for the Bachelor of Commerce program. It covers various topics including website features, the roles of browsers, and search engine functionality, providing detailed explanations and examples. The lab file is a comprehensive guide to understanding essential e-commerce concepts and their practical applications.Commercial Break: Linked Data for Business
Commercial Break: Linked Data for Businesszbeauvais
Ěý
Linked data and the use of graphs are enabling new business opportunities around data. Companies can directly monetize their datasets by selling them on emerging data marketplaces like Kasabi, which is being built on linked data principles. As data becomes more interconnected and useful, current tools will get smarter and new applications and business models will emerge, fueled by the ability to browse, buy, and leverage linked datasets.Why Portability matters (full presentation)
Why Portability matters (full presentation)Ian Forrester
Ěý
The document discusses the importance of data portability on the web. It notes that users should have control over their own data and be able to easily move it between services. However, many current systems lock users into specific platforms by not allowing easy export or transfer of data. The document outlines several principles of user-controlled data portability and highlights examples of both good and bad practices among different web companies and technologies. It argues that users need more freedom and control over their personal information on the internet.Web engineering lecture 3
Web engineering lecture 3University of Swat
Ěý
This document provides an overview of key concepts related to the internet and the world wide web. It defines common terms like internet, internet services, websites, web servers, web browsers, URLs, HTML, and hyperlinks. It describes how the web works by explaining the role of domain name servers, IP addresses, and how web pages are requested and delivered. Finally, it outlines several advantages of having a website like being open 24/7, increasing customer base, cost savings, improved advertising and creating a brand image.Web spoofing (1)
Web spoofing (1)Khushboo Taneja
Ěý
Web spoofing allows an attacker to create a fake version of the World Wide Web to trick victims. The attacker lures victims to their fake site, which looks identical to the real site. On the fake site, the attacker can observe any sensitive information entered by the victim. Current browsers are vulnerable to web spoofing attacks even on secure connections. Users should disable JavaScript, always check the URL bar, and be wary of any requests for sensitive information over email.Must have open source applications
Must have open source applicationsBrianJamison
Ěý
The document discusses must-have open source applications for small businesses. It recommends Trac for project management, Drupal for content management, and a Ruby on Rails ecommerce application. Trac is easy to install and use for tracking tasks and client feedback. Drupal allows adding content and custom modules for features like booking rooms and maps. The Ruby on Rails shopping cart recommends is clean, customizable, and extensible for payments.Make Me A Web 2.0 Geek!
Make Me A Web 2.0 Geek!BALTIC centre for contemporary art, BALTIC, Gateshead
Ěý
The document discusses the evolution and impact of new technologies, particularly web 2.0, emphasizing collaboration, user involvement, and the transition from desktop to browser-based technologies. It highlights the importance of adapting to change, utilizing content effectively, and the challenges presented by misinformation on the internet. Additionally, it outlines various web technologies, tools, and principles that support online collaboration while cautioning about the potential dangers and difficulties in managing digital content.Social Networking Tools for Novices
Social Networking Tools for NovicesUS Environmental Protection Agency (EPA), Center for Computational Toxicology and Exposure
Ěý
Recently uploaded (20)
Smarter Aviation Data Management: Lessons from Swedavia Airports and Sweco
Smarter Aviation Data Management: Lessons from Swedavia Airports and SwecoSafe Software
Ěý
Managing airport and airspace data is no small task, especially when you’re expected to deliver it in AIXM format without spending a fortune on specialized tools. But what if there was a smarter, more affordable way?
Join us for a behind-the-scenes look at how Sweco partnered with Swedavia, the Swedish airport operator, to solve this challenge using FME and Esri.
Learn how they built automated workflows to manage periodic updates, merge airspace data, and support data extracts – all while meeting strict government reporting requirements to the Civil Aviation Administration of Sweden.
Even better? Swedavia built custom services and applications that use the FME Flow REST API to trigger jobs and retrieve results – streamlining tasks like securing the quality of new surveyor data, creating permdelta and baseline representations in the AIS schema, and generating AIXM extracts from their AIS data.
To conclude, FME expert Dean Hintz will walk through a GeoBorders reading workflow and highlight recent enhancements to FME’s AIXM (Aeronautical Information Exchange Model) processing and interpretation capabilities.
Discover how airports like Swedavia are harnessing the power of FME to simplify aviation data management, and how you can too."How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...
"How to survive Black Friday: preparing e-commerce for a peak season", Yurii ...Fwdays
Ěý
We will explore how e-commerce projects prepare for the busiest time of the year, which key aspects to focus on, and what to expect. We’ll share our experience in setting up auto-scaling, load balancing, and discuss the loads that Silpo handles, as well as the solutions that help us navigate this season without failures.OpenPOWER Foundation & Open-Source Core Innovations
OpenPOWER Foundation & Open-Source Core InnovationsIBM
Ěý
penPOWER offers a fully open, royalty-free CPU architecture for custom chip design.
It enables both lightweight FPGA cores (like Microwatt) and high-performance processors (like POWER10).
Developers have full access to source code, specs, and tools for end-to-end chip creation.
It supports AI, HPC, cloud, and embedded workloads with proven performance.
Backed by a global community, it fosters innovation, education, and collaboration.Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software
Ěý
In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdf
Oh, the Possibilities - Balancing Innovation and Risk with Generative AI.pdfPriyanka Aash
Ěý
Oh, the Possibilities - Balancing Innovation and Risk with Generative AIInformation Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdf
Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdfICT Frame Magazine Pvt. Ltd.
Ěý
Artificial Intelligence (AI) is rapidly changing the face of cybersecurity across the globe. In Nepal, the shift is already underway. Vice President of the Information Security Response Team Nepal (npCERT) and Information Security Consultant at One Cover Pvt. Ltd., Sudan Jha, recently presented an in-depth workshop on how AI can strengthen national security and digital defenses."Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays
Ěý
What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.Lessons Learned from Developing Secure AI Workflows.pdf
Lessons Learned from Developing Secure AI Workflows.pdfPriyanka Aash
Ěý
Lessons Learned from Developing Secure AI WorkflowsAI vs Human Writing: Can You Tell the Difference?
AI vs Human Writing: Can You Tell the Difference?Shashi Sathyanarayana, Ph.D
Ěý
This slide illustrates a side-by-side comparison between human-written, AI-written, and ambiguous content. It highlights subtle cues that help readers assess authenticity, raising essential questions about the future of communication, trust, and thought leadership in the age of generative AI.Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdf
Tech-ASan: Two-stage check for Address Sanitizer - Yixuan Cao.pdfcaoyixuan2019
Ěý
A presentation at Internetware 2025.Security Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante
Ěý
Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.FIDO Seminar: Authentication for a Billion Consumers - Amazon.pptx
FIDO Seminar: Authentication for a Billion Consumers - Amazon.pptxFIDO Alliance
Ěý
FIDO Seminar: Authentication for a Billion Consumers - AmazonThe Future of AI Agent Development Trends to Watch.pptx
The Future of AI Agent Development Trends to Watch.pptxLisa ward
Ěý
The Future of AI Agent Development: Trends to Watch explores emerging innovations shaping smarter, more autonomous AI solutions for businesses and technology.
FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptx
FIDO Seminar: Perspectives on Passkeys & Consumer Adoption.pptxFIDO Alliance
Ěý
FIDO Seminar: Perspectives on Passkeys & Consumer AdoptionMuleSoft for AgentForce : Topic Center and API Catalog
MuleSoft for AgentForce : Topic Center and API Catalogshyamraj55
Ěý
This presentation dives into how MuleSoft empowers AgentForce with organized API discovery and streamlined integration using Topic Center and the API Catalog. Learn how these tools help structure APIs around business needs, improve reusability, and simplify collaboration across teams. Ideal for developers, architects, and business stakeholders looking to build a connected and scalable API ecosystem within AgentForce.Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule
Ěý
şÝşÝߣ deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 2025Improving Data Integrity: Synchronization between EAM and ArcGIS Utility Netw...
Improving Data Integrity: Synchronization between EAM and ArcGIS Utility Netw...Safe Software
Ěý
Utilities and water companies play a key role in the creation of clean drinking water. The creation and maintenance of clean drinking water is becoming a critical problem due to pollution and pressure on the environment. A lot of data is necessary to create clean drinking water. For fieldworkers, two types of data are key: Asset data in an asset management system (EAM for example) and Geographic data in a GIS (ArcGIS Utility Network ). Keeping this type of data up to date and in sync is a challenge for many organizations, leading to duplicating data and creating a bulk of extra attributes and data to keep everything in sync. Using FME, it is possible to synchronize Enterprise Asset Management (EAM) data with the ArcGIS Utility Network in real time. Changes (creation, modification, deletion) in ArcGIS Pro are relayed to EAM via FME, and vice versa. This ensures continuous synchronization of both systems without daily bulk updates, minimizes risks, and seamlessly integrates with ArcGIS Utility Network services. This presentation focuses on the use of FME at a Dutch water company, to create a sync between the asset management and GIS.Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdf
Information Security Response Team Nepal_npCERT_Vice_President_Sudan_Jha.pdfICT Frame Magazine Pvt. Ltd.
Ěý
Ad
The karma of sharing information over the web
- 1. The Karma of Sharing Information over the Web! Sankaranand www.sankaranand.com
- 2. Information! What is it ? is specific and organized for a purpose. has been verified to be accurate and timely lead to an increase in understanding and decrease in uncertainty.
- 3. Information Technology ? the branch of engineering that deals with the use of computers and telecommunications to retrieve and store and transmit information
- 4. Social Media A platform that allows the creation and exchange of user-generated content Mostly Web-based applications Wikis, Forums, Blogs, Micro blogs, Social Network Aggregation
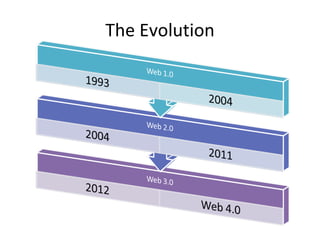
- 6. Web one point zero (web 1.0) Information Portal Directories HTML, GIF, Framesets, Html Forms Eg. Geocities, First version of Hotmail, Static Company pages
- 7. Web two point zero (web 2.0) Platform Rich Internet Applications Service Oriented Architecture Introduction of Social Web Eg. Facebook, Gmail, Youtube, Flickr
- 8. Web three point zero (web3.0) The Semantic Web Computer understand the Web Artificial Intelligence Personalization We track you and give you want ever you want!
- 9. Information Sharing One-to-one exchanges of data between a sender and receiver is past Standing Sharing Protocols Data harmonization Improved Privacy and Security XML, SOAP, WDSL
- 10. Our Karma over Information Sharing Revealing personal information Unclean Email Address Strangers-Just Met Acquaintances Not aware of Monitoring Falling in Pits of Scam, Phising Not Conscious of Web Security Not Deciding what to reveal Not using Encryption Home Security Not Monitoring your Cookies Digital Rights
- 11. Revealing personal information
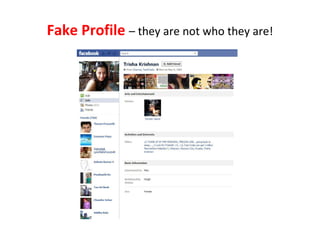
- 12. Best Example is Facebook
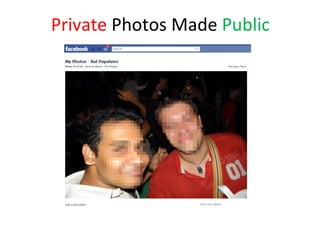
- 13. Private Photos Made Public
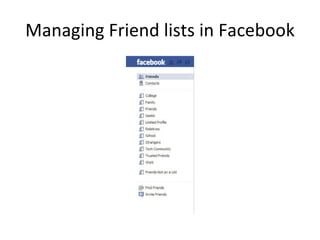
- 14. Adding Strangers I got 5000 Friends in Facebook , what about you ? Take Social Networking serious and add friends like in your real life. Create and Manage Friend lists
- 15. Managing Friend lists in Facebook
- 16. Don’t fall for that girly profile! Boys using Fake Girl profile are more appealing than an average girl’s profile Don’t fall over their Pit, Be a Man ! Girls be protective and secure your photos! Tweak around Facebook settings
- 17. Fake Profile – they are not who they are!
- 19. Clean Em @ il Address Two Email Address One for Newsletters and Commercial signups One for Personal / Work Use short-term disposable mails eg. Mailnator.com
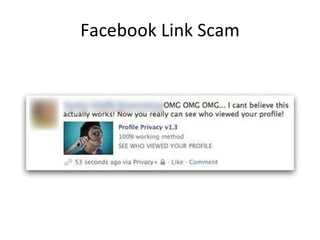
- 20. Wow, You are a millionaire $$$ There is no lottery announcement in Emails Phishing Scams Don’t even expect a penny for free from Web Ignore the SMS Scams too There is no victoria who wants to transfer her funds to your account Just Ignore them All!!!!!
- 21. HSBC Bank Phising Mail
- 22. Be Conscious of Web Security Submitting Financial Information Use Secure Connection – https:// Latest Browser Update your Antivirus & use a Firewall Monitor Network Connections Strong password -> upper + lowercase + symbols + numbers !
- 23. Best Practices – Public Computer Don’t use it for Financial Transaction Use a secure and latest browser Be aware of any keyloggers / Monitoring Apps Stay away from the prey eyes Keep a checklist of Things Clear cookies and Cache
- 24. Best Practices – Personal Computer Clear your Internet History Update your OS, Anti-virus Use Legit Software Stop Downloading Pirates & Torrents Use Linux – Its completely Free, Secure and Powerful. You have a wide flavors to choose from.
- 25. Recommend Apps CCleaner- Clear junk files from system Avast, Microsoft Security Essentials, Avg – Free Antivirus Hotspot – Privacy and Proxy Browsing Lastpass – One Ultimate tool for Password Management.
- 26. Ěý
- 27. Digital Content Copyright Understanding Creative Commons A tool for Creators, Content Sharing, Publishers Standardized way to keep their copyright simple Provides various kind of License which you can obtain at http://creativecommons.org
- 28. Which is my flavor ?
- 29. Attribution CC BY to Share — to copy, distribute and transmit the work to Remix — to adapt the work to make commercial use of the work Attribution — You must attribute the work in the manner specified by the author or licensor
- 30. Attribution-ShareAlike to Share — to copy, distribute and transmit the work to Remix — to adapt the work to make commercial use of the work Attribution — You must attribute the work in the manner specified by the author or licensor (but not in any way that suggests that they endorse you or your use of the work). Share Alike — If you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one .
- 31. Attribution-ShareAlike to Share — to copy, distribute and transmit the work to make — commercial use of the work Attribution — You must attribute the work in the manner specified by the author or licensor (but not in any way that suggests that they endorse you or your use of the work). No Derivative Works — You may not alter, transform, or build upon this work
- 32. Attribution-NonCommercial to Share Ěý— to copy, distribute and transmit the work to Remix Ěý— to adapt the work Attribution — You must attribute the work in the manner specified by the author or licensor (but not in any way that suggests that they endorse you or your use of the work). Noncommercia l — You may not use this work for commercial purposes.
- 33. Attribution-NonCommercial-ShareAlike to Share Ěý— to copy, distribute and transmit the work to Remix Ěý— to adapt the work Attribution — You must attribute the work in the manner specified by the author or licensor (but not in any way that suggests that they endorse you or your use of the work). Noncommercia l — You may not use this work for commercial purposes. Share Alike — If you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one.
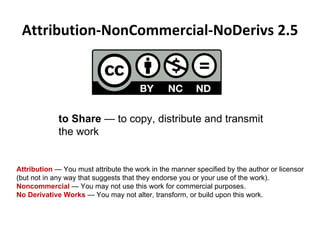
- 34. Attribution-NonCommercial-NoDerivs 2.5 to Share Ěý— to copy, distribute and transmit the work Attribution Ěý—ĚýYou must attribute the work in the manner specified by the author or licensor (but not in any way that suggests that they endorse you or your use of the work). Noncommercial Ěý—ĚýYou may not use this work for commercial purposes. No Derivative Works Ěý—ĚýYou may not alter, transform, or build upon this work.
- 35. Public Domain Free to use You can learn more about Creative Commons License by reading Copy Right & Left by Kiruba Shankar www.copyrightandleft.org
- 36. The Three Layers of Code
- 37. [email_address] http://facebook.com/ sankaranand http://twitter.com/ sankaranand http://linkedin.com/in/ sankaranand http://profiles.google.com/ smartjean4u www. sankaranand .com Connect ME
