eGovernment, free licenses & FoI in Germany
- 1. eGovernment 2.0, free licenses and real Freedom of Information Claas Hanken ŌĆō ifib
- 2. ŌĆóŌĆó Ideal vs. administrative reality in D ŌĆóŌĆó ┬╗All rights reserved┬½ ŌĆóŌĆó Freedom of Information and reuse of public sector information Claas Hanken 08/2009 (CC by/3.0)
- 3. Scientific & Creative Commons Image: Bundesarchiv @ Wikimedia Commons unter cc by-sa/3.0/de/ Free ŌĆō as in Freedom (Richard Stallman) Image: ESA/NASA
- 4. Creative Commons Creative Commons is a nonprofit corporation dedicated to making it easier for people to share and build upon the work of others, consistent with the rules of copyright. The simple cc-Attribution License allows others to copy, distribute, display, and perform your copyrighted work but only if they give credit the way you request. Source: CreativeCommons.org http://creativecommons.org Creative Commons by/3.0 Image: Joi @ flickr Claas Hanken 08/2009 (CC by/3.0) cc Attribution 2.0 Generic
- 5. German government agencies and CC Wikimedia Germany in cooperation with German Bundesarchiv: more than 100.000 images, mostly documenting German history . The images are issued as Creative Commons BY-SA 3.0 Germany. Apart from this publication under cc only in individual cases, for instance »Die Lage der Biologischen Vielfalt« (Creative Commons Attribution License 2.5). German government works are published under special copyright conditions. Even CC0 is not applicable. Creative Commons licenses could be applied on other works for which the Government holds copyright. Claas Hanken 08/2009 (CC by/3.0)
- 6. Lawrence Lessig on ┬®: Overregulation stifles creativity. It smothers innovation. It gives dinosaurs a veto over the future. It wastes the extraordinary opportunity for a democratic creativity that digital technology enables.┬½ L. Lessig: Free Culture (2004), p. 199 Image: Joi @ flickr cc Attribution 2.0 Generic Claas Hanken 08/2009 (CC by/3.0)
- 7. ┬╗Alle Rechte vorbehalten┬½ vs. ┬¦ 5 UrhG? Standard copyright protection is not appliable on German government works (┬¦ 5 Abs. 1 of the german Urheberrechtsgesetz ŌĆō UrhG). In many cases government publication could be freely distributed, if only the source is identified in a recognizable way. None the less most government agencies are using ┬╗All rights reserved┬½ (┬╗Alle Rechte vorbehalten┬½) for their Websites. Why? Claas Hanken 08/2009 (CC by/3.0)
- 8. Excuses for restrictive ┬®-Conditions ┬╗It always worked, why change it?┬½ Worries over ┬╗Someone elses intellectual property could be harmed.┬½ possible damage to public image privacy ┬╗There could be negative effects for some companies.┬½ ┬╗We wonŌĆÖt give away our intellectual Uncertain fears and property .┬½ doubts Image: germanium @ flickr cc Attribution 2.0 Generic Claas Hanken 08/2009 (CC by/3.0)
- 9. Proprietary Software vs. OSS ŌĆó Usually contractors donŌĆÖt have to provide results under Free and Open Source Licenses (FOSS like GNU, EUPL, ┬╗Bremer Lizenz┬½). ŌĆó Due to agreements from the 70ŌĆÖs (┬╗Kieler Beschl├╝sse┬½) government agencies can adopt and use certain applications that were developed for other administrative bodies free of charge. Examples: Ginfis, EPOS, Favorit OfficeFlow, Government Site Builder Claas Hanken 08/2009 (CC by/3.0)
- 10. Excuses for restrictive licenses ┬╗It always worked, why change it?┬½ ┬╗OSS is tinkered ┬╗Anyone could mess around with by unknown with the source code!┬½ people and faulty.┬½ privacy ┬╗There could be negative effects for ┬╗We paid for it ŌĆō some companies.┬½ therefore we own it.┬½ Uncertain fears and doubts Image: germanium @ flickr cc Attribution 2.0 Generic Claas Hanken 08/2009 (CC by/3.0)
- 11. Freedom of Information (FoI) ŌĆó The german laws on FoI (by Bund and L├żnder) have the purpose to ensure that the governmentŌĆÖs operations are apparent. They grant unconditional access to public information for everyone ŌĆō with few exceptions (abandonment of the Amtsgeheimnis-paradigm). ŌĆó Risks for requesters: refusal of enquiries, high costs Claas Hanken 08/2009 (CC by/3.0)
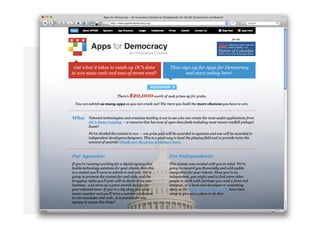
- 12. FoI documents as Legal torrents? In case of a successful FoI request, fees payed: Is one allowed to re-publish the document online (without commercial interest)? Common answer: No. ŌĆó Example from the US: Download for Democracy (documents made available over P2P-networks) ŌĆó Expandable prototype by CCC e.V. and FoeBuD e.V. (Germany): ┬╗Befreite Dokumente┬½ Claas Hanken 08/2009 (CC by/3.0)
- 13. Laws on the reuse of PSI The german »Informationsweiterverwendungsgesetz« is aimed to transpose directive 2003/98/EC on the reuse of public sector information into national law. The law deals with the sharing and reuse of public sector information by citizens and businesses. Government agencies can impose fees on the reuse of information. (Do they charge the taxpayer again for information that has been collected using tax money?) Claas Hanken 08/2009 (CC by/3.0)
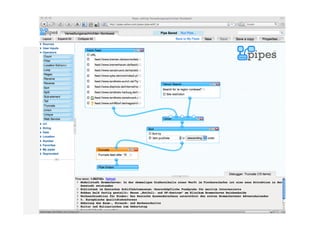
- 14. ŌĆ×RemixŌĆ£ of public data sources? ŌĆóŌĆó merge data sources ŌĆóŌĆó remix and filtering ŌĆóŌĆó RSS-feeds to manage information ŌĆóŌĆó Example: Google News puts together articles on a topic from various newspapers ŌĆóŌĆó Example: Yahoo! Pipes makes it easy to concatenate, combine and transform web content (┬╗mashup┬½) Claas Hanken 08/2009 (CC by/3.0)
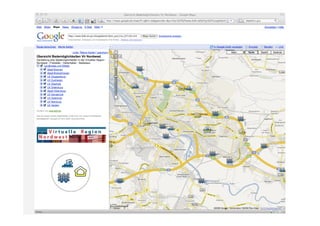
- 16. Beispiel: swim & fun Nordwest
- 17. Open APIs ŌĆóŌĆó An open API (Application Programming Interface) gives programmers the opportunity to reuse data and certain functionalities in new applications. ŌĆóŌĆó Examples for german government APIs: eCard-API-Framework, ELSTER COALA Java-APIs Claas Hanken 08/2009 (CC by/3.0)
- 18. Raw Data Now! Web founder Berners-Lee (2009) TED talk: http://www.ted.com/talks/view/id/484 Vision: Governments provide free information as raw data in a machine-processable form. Image: captsolo @ flickr cc Share Alike 2.0 Generic Claas Hanken 08/2009 (CC by/3.0)
- 20. Raw Data from government agencies ŌĆó Example data.gov (US): raw data, geodata, tools ŌĆó What is this good for? surveillance cameras / crime rate? ŌĆó financial aids / local economic growth? [Put your idea here.] Image: captsolo @ flickr cc Share Alike 2.0 Generic Claas Hanken 08/2009 (CC by/3.0)
- 22. Wrap-up Government agencies (in Germany & elsewhere) should: ŌĆóŌĆó make sure that hindrances for free publication are removed ŌĆóŌĆó favor offers that allow publication under free licenses ŌĆóŌĆó provide free raw data ŌĆóŌĆó use structured data formats ŌĆóŌĆó move public data into the interconnected web ŌĆóŌĆó provide open APIs Claas Hanken 08/2009 (CC by/3.0)
- 23. Contact: Claas Hanken ŌĆō hanken@ifib.de Am Fallturm 1, 28359 Bremen Telefon: ++49(0)421 218-2674 Telefax: ++49(0)421 218-4894 www.egovernment-akademie.de Internet: www.ifib.de E-Mail: info@ifib.de www.ifib.de The presentation is published under Creative Commons Namensnennung 3.0 http://creativecommons.org/licenses/by/3.0/ Author: Claas Hanken ifib & E-Government-Akademie are registered trademarks (DPMA.de) of ifib GmbH.














![Raw Data from government agencies
ŌĆó Example data.gov (US): raw data, geodata, tools
ŌĆó What is this good for?
surveillance cameras /
crime rate?
ŌĆó financial aids / local
economic growth?
[Put your idea here.]
Image: captsolo @ flickr
cc Share Alike 2.0 Generic
Claas Hanken 08/2009 (CC by/3.0)](https://image.slidesharecdn.com/200909hankenfreeegov-090911092251-phpapp01/85/eGovernment-free-licenses-FoI-in-Germany-20-320.jpg)