2015年12月 大阪日本橋?でんでんタウン ロボット連絡会 定例会 講演資料 IoT/M2Mで沸いた 2015年を振り返る
- 1. IOT/M2Mで沸いた 2015年を振り返る Machine to Machine / Internet of Things ?Yukio Kubo 2015 1 トライアングルエレクトロニクス 久保幸夫 2015年12月 大阪日本橋?でんでんタウン ロボット連絡会 定例会 講演資料
- 2. 展示会に参加してきました ?ET/IoT2015(横浜11月18日~20日) – Embedded Technology 2015 組込み総合技術展 – IoT Technology2015 IoT 総合技術展 ?Yukio Kubo 2015 2
- 4. SCF2015/計測展2015 TOKYO SCF システム コントロール フェア2015 計測展2015 第4次産業革命で工場が変わる、社会が変わる 見学してきました ?Yukio Kubo 2015 4
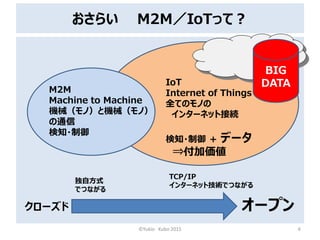
- 6. おさらい M2M/IoTって? ?Yukio Kubo 2015 6 M2M Machine to Machine 機械(モノ)と機械(モノ) の通信 検知?制御 IoT Internet of Things 全てのモノの インターネット接続 検知?制御 + データ ?付加価値 オープンクローズド 独自方式 でつながる TCP/IP インターネット技術でつながる BIG DATA
- 7. こちらのスライドも参考に 大阪市南港ATC イメディオ IoT? M2Mセミナ資料(web公開用) www.slideshare.net/yukiokubo169/io-tm2mweb 2015/06/03 · 大阪市の南港ATC ソフト産業プラザ イメディオで開催された IoT/M2Mセミナー http://www.sansokan.jp/events/eve_detail.san?H_A_NO=19185 のスライド(抜粋)です ?Yukio Kubo 2015 7
- 8. こちらのスライドも参考に コラボ滋賀(滋賀県産業支援プラザ) で開催された M2M/IoT講座 「M2M/IoTとは何か? 「モノのインターネット」で変貌する世界の今と未来」 (2015年12月)の公開版 http://www.slideshare.net/yukiokubo169/m2miot-56000250 セミナー案内 http://www.shigaplaza.or.jp/itseminar20151209/ ?Yukio Kubo 2015 8
- 9. IoT/M2Mに関連キーワード ? インダストリー4.0 時代は、「第4の産業革命」へとか ? インダストリアル?インターネット つながる工場 – 工場のフィールドネットワークやFAネットワー クとクラウドがインターネットでつながる??? とか言われている ? SCFシステム コントロール フェア2015 での、一コマ CC-Link協会のSLMP (Seamless Message Protocol) 構想のプレゼン あらゆる機器や設備がつながる
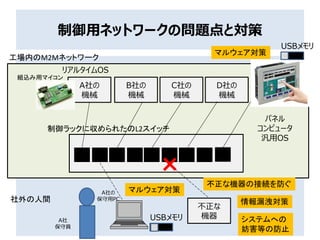
- 10. とか、騒いでいる割には??? ? 工場の機械(生産機器)や産業用ロボットも、 ネットワークに接続して、やりとりしている??? つながる工場では、 それをインターネットに接続して… といっても… ? インターネットやクラウドの技術者は、工場とか、 組込み向けのネットワークって、知らないことが多 い。(ほとんど? RS485って何?モトバスって?) ? 生産現場の、フィールドネットワーク等を専門にし ている技術者が、世間で標準と言われている “標準イーサネット”や“TCP/IP”を軸とする“イン ターネット”や“クラウド”の知識が 十分あるかと言うと…
- 17. 両方がわかる人が不足しているような ■インターネットやクラウド技術 情報系の標準イーサネット,TCP/IPを使った通信 いかに、ネット上のクラウドサービスにつなぐか… クラウドをどう使って、データを活用するか… ■フィールドネットワークやFAネットワーク 専用のネットワーク 各種の産業用イーサネット イーサネットのような、違うような…様々あり 各種のシーケンサ、PLCのネットワーク CC-Link、MECHATROLINK…メーカごとにいろいろあり デバイスネットとか、 車載用のCANベース アークネットとかも トークンパッシング式!衝突しない! RS485/422やRS232C レガシーのひとことで、切り捨てないで… BACnet,LONWORKS(ロンワークス)とか、 ビルや設備向けネットワークもある
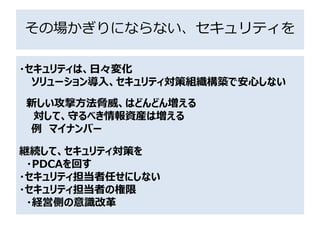
- 30. セキュリティのための組織つくり ?セキュリティ教育 ?セキュリティ担当者の教育 ?全社的な教育(全社員) ?社内の啓蒙活動 ?社内のセキュリティ ?セキュリティのための組織つくり ?セキュリティ対策チーム ?セキュリティポリシ策定、実行計画、実行委員 ?サート CERT(Computer Emergency Response Team) または、インシデント対策チーム
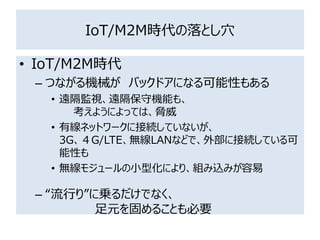
- 33. IoT/M2M時代の落とし穴 ? IoT/M2M時代 – つながる機械が バックドアになる可能性もある ? 遠隔監視、遠隔保守機能も、 考えようによっては、脅威 ? 有線ネットワークに接続していないが、 3G、4G/LTE、無線LANなどで、外部に接続している可 能性も ? 無線モジュールの小型化により、組み込みが容易 – “流行り”に乗るだけでなく、 足元を固めることも必要
- 34. ? 大阪?日本橋 ロボット連絡会のご案内 – ロボット連絡会では 毎月1回(第3火曜日午後6時~)に定例会を開 いております。(参加費無料) – 毎回、講演者を招き、ロボットに限らず、IoT/M2M や組込みシステム、3Dプリンタなどのモノづくりをテー マにした勉強会を開催しております。 ? 詳しくは、 http://roboba.jp