Eines de dinamitzaciĂł Ă’mnia 09
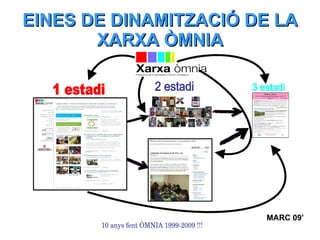
- 1. EINES DE DINAMITZACIÓ DE LA XARXA ÒMNIA ABRIL 09’ 10 anys fent ÒMNIA 1999-2009 !!! 1 estadi 3 estadi 2 estadi
- 2. ESTRATEGIA DE DINAMITZACIĂ“ TIC DE LA XARXA Ă’MNIA PORTAL D’ÒMNIA Punt d’entrada i d’informaciĂł sobre la Xarxa Ă’mnia, notĂcies, recursos...coneixement sobre la idiosincrĂ sia del projecte i la distribuciĂł i contactes amb els Punts Ă’mnia d’arreu de Catalunya. COMUNITAT VIRTUAL Espai vinculat al portal de la Xarxa amb la finalitat de convertir-se en el lloc de relaciĂł, intercanvi i creaciĂł de coneixement entre les persones dinamitzadores. Facilitar informaciĂł, materials, recursos... per ser editats en el portal de la Xarxa Ă’mnia. Visualitzar la xarxa social de persones que treballen pel projecte Ă’mnia. BLOC DE L’ODC Una finestra oberta a la Xarxa Ă’mnia Ă©s un espai per conèixer el dia a dia del treball que es desenvolupa des de l’ODC aixĂ com disposar dels diferents materials que es vagin creant per dinamitzar el projecte. Un lloc a la xarxa per visualitzar el treball metodològic que es desenvolupa en els Punts Ă’mnia amb una periodicitat setmanal. CIRCULAR Ă’MNIA Eina mensual per fer arribar les informacions relacionades amb el funcionament del projecte, recordatoris, explicaciĂł dels diferents serveis, conèixer els diferents territoris, novetats en el portal.... una manera de treballar l’atenciĂł a les entitats i les persones dinamitzadores a travĂ©s del correu-e. Periodicitat mensual. LLISTA DE DISTRIBUCIĂ“ [email_address] Un correu al servei de totes les persones que treballen a la Xarxa Ă’mnia per tal de facilitar la comunicaciĂł horitzontal i convertir-se en un canal de comunicaciĂł per fer arribar informacions, consultes, idees, propostes... a la resta de la Xarxa. Funciona a travĂ©s del correu de @xarxa-omnia.org dels PO.
- 3. Per què una Circular Òmnia ? Treballar amb rigor i planificar les accions del projecte mensualment. (ens obliga a treballar amb previsió i visió estratègica i de futur). Arribar a les bústies de correu-e de la xarxa: fomenta el sentit de pertinença, atenció personalitzada a través del correu-e, recordatoris d’entrega de documentació i trobades, comunicació permanent....complicitat i fidelització amb les persones implicades. Fer marca Òmnia ja que comporta apropar la xarxa a cada punt. Informar sobre els canvis i les novetats en el portal. Visualitzar i compartir les directrius del projecte amb entitats, persones dinamitzadores...parlar del projecte. Apropar les eines virtuals de la xarxa (portal, bloc, comunitat...) a les entitats i persones dinamitzadores. Legitimar la comunicació amb les persones implicades, punt de trobada de la informació, genera expectativa vers la info i la Xarxa. Una manera diferent de tractar la informació: no abusar del correu-e, treballar amb les distintes eines virtuals, organitzar i seleccionar la info, presentació més atractiva, possibilitat d'emmagatzemar i consultar la informació en l’espai i el temps.
- 4. CIRCULAR Amb una periodicitat mensual és l’eina per fer arribar a les persones responsables de les entitats i dinamitzadores, l’actualitat del projecte, les experiències metodològiques dels PO, l’organització de les trobades, pedagogia sobre el projecte Òmnia....canal d’informació de l’Equip de Coordinació Òmnia. Té la funció de fer arribar a la bústia dels participants en el projecte temes com ara: Iniciatives metodològiques de les persones dinamitzadores (com ho fan) visualitzar la tasca de les persones dinamitzadores. Informacions de la DGACO. Informacions de l’OT. Informacions i recordatoris de l’ODC. Donar a conèixer a les noves persones dinamitzadores. Donar a conèixer els diferents territoris Òmnia. Fer pedagogia sobre el projecte. Informar sobre l’organització de les trobades, grup metodològics... Treballar el coneixement d’altres programes, projectes... Apropar als PO entre ells. Explicació sobre recursos. Altres. Continguts de la Circular
- 5. Per què una Comunitat Virtual? Crear una Xarxa Social o Comunitat Virtual ofereix les següents possibilitats: Coneixement de les diferents realitats de la Xarxa. Facilitar les relacions i les interaccions entre persones dinamitzadores. Generar una cultura de l’intercanvi de coneixements on line. Millorar l’accés a la informació i el coneixement. Millorar la qualitat i l’eficà cia del treball de les persones dinamitzadores. Treballar per la transversalitat amb altres projectes. Reconeixement de les persones que formen la xarxa. Incrementar la credibilitat vers la Xarxa. Crear un sentit de pertinença a la Xarxa. Canal de comunicació i informació directe amb la comunitat. Visualitzar la capacitat creativa i de creació de coneixement de la Xarxa. Cercar reflexions, opinions, propostes...que contribueixin al creixement i la projecció de la Xarxa. ...una cultura de professionalitat vers el treball en els PO.
- 6. Per què un bloc de l’ODC? Es una eina dinà mica que ens permet treballar continguts i modificar-los amb molta rapidesa i facilitat. Compleix una funció de desenvolupar continguts que altres espais virtuals no ens permet. Facilita el coneixement del treball que es fa, en aquest cas, des de l’ODC. Espai per fer pedagogia sobre el projecte i la seva realitat. Forma de fomentar la participació de la Xarxa a través del treball que es desenvolupa en el dia a dia. Facilita la visualització del funcionament de la Xarxa. Descobrir els diferents racons i peculiaritats del projecte Òmnia. El sistema de sindicació facilita el seu seguiment per part de totes les persones interessades.
- 7. ALTRES EINES 2.0 AL SERVEI DE LA XARXA Ă’MNIA Finalment, aquĂ es troben diferents eines 2.0 que faciliten el tractament de continguts des de diferents aplicacions que permeten trobar el projecte Ă’mnia a travĂ©s de la generaciĂł de continguts i compartir-los en la xarxa. Gravacions de so georeferenciades WOICES: http :// woices.com / xarxaOmnia Espai de microblogging TWITTER: http :// twitter.com / xarxaomnia Repositori de vĂdeos YOUTUBE: http :// www.youtube.com /XARXAOMNIA Repositori de links DELICIOUS: http :// delicious.com / xarxaomnia Varies aplicacions (Maps, Picassa,...) COMPTE GOOGLE xarxaomnia @ gmail.com Banc d’imatges gratuĂŻt SXC.HU-Banc d'imatges ( http :// www.sxc.hu / ) Calendari on line JOTLET ( https :// www.jotlet.net / ) Site per crear jocs FYREBUG : http :// www.fyrebug.com /xarxa_ omnia PublicaciĂł de documentaciĂł ISUU : http :// issuu.com / xarxa-omnia Repositori de vĂdeos I Ă udio BLIPTV: http :// xarxa-omnia.blip.tv Presentacions en ppt… SLIDE SHARE : http :// www.slideshare.net /OMNIA FUNCIONS EINA
- 9. Document elaborat per l’equip de l’Oficina de Dinamització Comunità ria Òmnia de Fundació Catalana de l’Esplai-FCE Abril 2009. 10 anys fent ÒMNIA 1999-2009 !!!
![ESTRATEGIA DE DINAMITZACIĂ“ TIC DE LA XARXA Ă’MNIA PORTAL D’ÒMNIA Punt d’entrada i d’informaciĂł sobre la Xarxa Ă’mnia, notĂcies, recursos...coneixement sobre la idiosincrĂ sia del projecte i la distribuciĂł i contactes amb els Punts Ă’mnia d’arreu de Catalunya. COMUNITAT VIRTUAL Espai vinculat al portal de la Xarxa amb la finalitat de convertir-se en el lloc de relaciĂł, intercanvi i creaciĂł de coneixement entre les persones dinamitzadores. Facilitar informaciĂł, materials, recursos... per ser editats en el portal de la Xarxa Ă’mnia. Visualitzar la xarxa social de persones que treballen pel projecte Ă’mnia. BLOC DE L’ODC Una finestra oberta a la Xarxa Ă’mnia Ă©s un espai per conèixer el dia a dia del treball que es desenvolupa des de l’ODC aixĂ com disposar dels diferents materials que es vagin creant per dinamitzar el projecte. Un lloc a la xarxa per visualitzar el treball metodològic que es desenvolupa en els Punts Ă’mnia amb una periodicitat setmanal. CIRCULAR Ă’MNIA Eina mensual per fer arribar les informacions relacionades amb el funcionament del projecte, recordatoris, explicaciĂł dels diferents serveis, conèixer els diferents territoris, novetats en el portal.... una manera de treballar l’atenciĂł a les entitats i les persones dinamitzadores a travĂ©s del correu-e. Periodicitat mensual. LLISTA DE DISTRIBUCIĂ“ [email_address] Un correu al servei de totes les persones que treballen a la Xarxa Ă’mnia per tal de facilitar la comunicaciĂł horitzontal i convertir-se en un canal de comunicaciĂł per fer arribar informacions, consultes, idees, propostes... a la resta de la Xarxa. Funciona a travĂ©s del correu de @xarxa-omnia.org dels PO.](https://image.slidesharecdn.com/einesdedinamitzacimnia09-090507104704-phpapp02/85/Eines-de-dinamitzacio-Omnia-09-2-320.jpg)





























































