hacking and its types
Download as PPTX, PDF0 likes301 views
There are different types of hackers - white hat hackers test security systems for vulnerabilities but do not have malicious intent, while black hat or cracker hackers break into systems to steal data or cause harm. Common hacking attacks mentioned include phishing, brute force attacks, cookie stealing, and email hacking by exploiting vulnerabilities or creating viruses and worms. An anti-virus program is created to detect and remove viruses from a system. A worm is a self-replicating virus that spreads to other computers without user intervention.
1 of 12
Downloaded 16 times






Recommended
Hacking and Anti Hacking



Hacking and Anti HackingInternational Islamic University
?
The document provides an overview of hacking, including a brief history from the 1960s to present. It discusses different types of hackers like white hat and black hat hackers. Common hacker techniques are described such as footprinting, scanning, gaining access, and covering tracks. The document also outlines methods for anti-hacking like keeping systems updated, using antivirus software, and enabling firewalls.Computer crime hacking



Computer crime hackingtangytangling
?
Hacking has evolved over three phases from the 1960s to present. It began as a positive term referring to clever programming but now generally refers to illegal or unauthorized computer access. Recent developments include growth of political hacking (hacktivism), denial of service attacks, and large scale theft of personal data facilitated by the internet. Laws aim to catch hackers through undercover work, computer forensics, and set penalties depending on intent and damage. Ongoing challenges involve responsibly improving security while respecting open access and balancing punishment of young hackers.Research Paper - Hacker Plague



Research Paper - Hacker PlagueLuke Perrin
?
More than 30% of computers are infected by viruses created by hackers. Hackers breach systems for a variety of reasons such as stealing information, harming others, or disrupting networks. Modern technology allows hackers to work remotely from anywhere in the world. Key problems caused by hackers include crippling government systems through prolonged probing to find weaknesses, creating viruses that damage computers and leave backdoors, and organized hacking groups that are difficult for experts to counter. While there are no permanent solutions, methods to prevent hacking include using hackers' own tools to strengthen defenses, increasing cybersecurity funding, and reformatting infected systems. The outlook on preventing widespread hacking is pessimistic as hackers continue to innovate faster than defenses.HACKING



HACKINGShubham Agrawal
?
Hacking refers to attempting to gain unauthorized access to computer systems or networks. There are different types of hackers, including white hat hackers who test security systems to help organizations, black hat hackers who access systems maliciously, and gray hat hackers whose activities fall between white and black. Common types of hacking include website, email, network, password, and computer hacking through techniques like sniffing passwords, spoofing addresses, cracking encryption, brute force guessing, and exploiting poor web application coding. Organizations can help prevent hacking by employing ethical hackers to test security, not exposing passwords to untrusted sites, closing internet access when not in use, and having basic internet knowledge.What is Hacking? AND Types of Hackers



What is Hacking? AND Types of Hackersinfosavvy
?
Infosavvy is a training institute that provides courses in IT management, information security, cyber security, and quality management. It discusses the definition of hacking as exploiting vulnerabilities to gain unauthorized access. There are three main types of hackers - white hat hackers who perform ethical security testing, black hat hackers who hack maliciously, and grey hat hackers who fall between the two.hacking presentation slide 



hacking presentation slide Tauhidul islam
?
This presentation introduces the presenter Tauhidiul Islam and their department of Computer Science Engineering. It then outlines that the presentation will cover the history of hacking, what hacking is, who hackers are, famous hackers from history, and types of hacking. The body of the presentation defines hacking, discusses who hackers are, provides examples of famous historic hackers like Kevin Mitnick and Robert Morris, and lists some types of hacking such as website, network, and password hacking. It concludes by emphasizing the importance of password protection.Hacking



Hackingpranav patade
?
There are different types of hackers categorized by their intentions and methods:
1. White hat hackers legally hack to expose vulnerabilities and help organizations improve security.
2. Black hat hackers illegally hack with malicious intent to steal data or cause harm.
3. Grey hat hackers operate in a middle ground, sometimes hacking legally to expose issues but their methods may still be considered unauthorized access.
Types of hacking programs include trojan horses, computer viruses, and computer worms, which can spread maliciously or be used to gain unauthorized access. Popular hacker culture is also depicted in cyberpunk novels and films.basic knowhow hacking



basic knowhow hackingAnant Shrivastava
?
a simple presentation with introduction on hacking, presented by anant shrivastava on behalf of linux academy at rkdf bhopal http://academylinux.com and contact anant at http://anantshri.infoSecure Shell - a Presentation on Ethical Hacking



Secure Shell - a Presentation on Ethical HackingNitish Kasar
?
This document summarizes a seminar on ethical hacking and secure shell. It defines hacking and different types of hackers such as script kiddies, phreakers, and hacktivists. It outlines the basic steps of hacking including footprinting, scanning, gaining access, and maintaining access. The seminar discusses recent phishing attacks and the need for ethical hacking to make cyberspace more secure. It describes a secure shell course that teaches skills like networking, Linux, windows hacking, and penetration methodologies over 30 days to help pursue a career in ethical hacking which is in high demand. The document concludes with tips for creating a secure password.Hacking



Hackingvkradhika
?
The document discusses different types of hacking including website, email, network, password, online banking, and computer hacking. It describes various hackers like white hat, black hat, and grey hat hackers and provides examples of famous hackers such as Kevin Mitnick and Kevin Poulsen. The document concludes with tips to prevent hacking which include using strong passwords, installing antivirus software, avoiding disclosure of personal details, employing ethical hackers, and other internet safety practices.Hacking presentation



Hacking presentationdineshgarhwal77
?
Hacking refers to activities aimed at exploiting security flaws to obtain personal or private information without authorization. A typical hacker will identify a target system, gather information about it, find a security loophole, exploit that loophole using hacking software to access the system without authorization, and then delete traces of their access. Hackers target systems for reasons like stealing credit card or identity information, accessing business information, or proving their skills. Hacking can result in significant financial losses for companies and the loss of private data. Countries with the most hackers include the United States, China, Turkey, Russia, and others.Hacking & its types



Hacking & its typesSai Sakoji
?
This document provides an overview of hacking, including its history, definitions, types, famous hackers, reasons for hacking, and advice on security and ethics. Hacking emerged in the 1960s at MIT and refers to attempting to gain unauthorized access to computer systems. It describes hackers as those who exploit weaknesses in computers. Different types of hacking are outlined such as website, network, password, and computer hacking. Advice is given around using strong unique passwords, backing up data, and contacting authorities if hacked. Both advantages like security testing and disadvantages like privacy harm are discussed.Ethical Hacking and Network Security



Ethical Hacking and Network Securitysumit dimri
?
Hi, friends today Iam presented my ppt on ethical hacking and network security. This will gives you some basic tips and ideas about hacking and how to make our network secure.hacking



hackingmayank1293
?
Hacking involves gaining unauthorized access to computer systems, which is illegal. There are different types of hackers, including white hats who help find security vulnerabilities, black hats who hack with malicious intent, and grey hats in between. Reasons for hacking include financial gain, showing off skills, or just for fun. Experts recommend using antivirus software, avoiding suspicious links and downloads, and keeping software updated to help prevent hacking.Computer hacking



Computer hackingArjun Tomar
?
You all can infer what would be in the PPT from the title itself. In this PPT it is not told directly how to hack. Just a brief info of hacking and cyber security is given. How can one save himself/herself from becoming a victim of cybercrime? How to hack is given in my next PPT?Basic of Ethical Hacking and Penetration Testing - 1st Module



Basic of Ethical Hacking and Penetration Testing - 1st Moduleankit sarode
?
This document provides an introduction to information security topics such as penetration testing, hacking, and ethical hacking. It defines penetration testing as attacking a system to find security weaknesses and potential access. Hacking is exploiting vulnerabilities in computer systems, while ethical hacking does the same thing legally with permission. The document also discusses the differences between hackers and crackers, careers in information security such as penetration testing and cyber crime investigation, and provides references for further information security terms and resources.Common hacking tactics



Common hacking tacticsFariha Khudzri
?
Common hacking tactics include vulnerability scanners that check for known weaknesses, spoofing attacks like phishing that masquerade as trusted systems, password cracking by repeatedly guessing passwords, packet sniffers that capture network data including passwords, social engineering by tricking users, key loggers that record keystrokes to steal passwords, Trojan horses that pose as one thing but do another like enabling backdoor access, and viruses that self-replicate to spread malware. Hackers use these tactics to access systems and steal confidential information without authorization.Ethical hacking presentation



Ethical hacking presentationZahid Rajeel
?
Hacking can be either legal or illegal depending on authorization and intent. Ethical hacking involves performing the same activities as illegal hacking but with the owner's permission as part of an overall security program. The history of hacking began in the 1960s and different types of hackers like phone phreakers emerged over subsequent decades as technology advanced. There are different types of illegal hacking techniques but also ethical white hat and grey hat hackers who use their skills to help protect systems rather than for personal gain or malicious purposes. The consequences of illegal hacking can include fines, imprisonment, and computer seizure.Hacking and Hackers



Hacking and HackersFarwa Ansari
?
This presentation provided information on communication skills and hackers. It began with an introduction to the topic of hackers, defining what a hacker is and discussing different types of hackers such as black hat, white hat, grey hat, and script kiddie hackers. The presentation then discussed famous hackers like Albert Gonzalez, Jonathan James, Ian Murphy, and John Draper. It provided details on some of their hacking activities. The presentation concluded with tips on how to prevent hacking, including keeping software and operating systems updated, using firewalls and antivirus software, avoiding suspicious websites and emails, and having strong passwords.Windows Hacking



Windows HackingMayur Sutariya
?
This document discusses different types of hackers and methods of hacking passwords. It defines white hat and black hat hackers, with white hats using their skills constructively and ethically to find security vulnerabilities, while black hats use their skills illegally and destructively. The document also discusses crackers/attackers who hack with malicious intent, phreaks who hack phone networks, and script kiddies who exploit known vulnerabilities without technical skills. It provides examples of password cracking tools and methods like Cain & Abel, LCP, password dumping, and using Windows repair mode. It notes the importance of security awareness and prevention.Introduction To Ethical Hacking



Introduction To Ethical HackingAkshay Kale
?
1. The document introduces the topic of ethical hacking by defining hacking and explaining its origins in computer culture at MIT in the 1960s, where hackers were students who pursued recreational activities rather than studying.
2. It describes the three main types of hackers: white hat hackers who find security vulnerabilities ethically, black hat hackers who do so illegally and destructively, and grey hat hackers who exhibit traits of both.
3. The document outlines the typical hacking methodology of reconnaissance, scanning, gaining access, maintaining access, and covering tracks, and provides examples of common low-tech and high-tech hacking techniques.Ethical hacking



Ethical hackingHarshit Upadhyay
?
This presentation provides an overview of ethical hacking. It defines ethical hacking as illegally accessing another system, but for good purposes like testing security. It explains that actual hacking is not a crime, but is made so by those who hack for bad reasons, known as crackers. Ethical hackers help ensure security, while hackers access systems for either good or bad reasons and crackers specifically aim to spread malware or steal information. The presentation outlines the importance of ethical hacking for security and some basic steps anyone can take to help protect themselves from hacking.Computer Hacking - An Introduction



Computer Hacking - An IntroductionJayaseelan Vejayon
?
Hacking involves modifying systems outside of their intended purpose. It is commonly done by teenagers and young adults using computers. Reasons for hacking include profit, protest, and challenge. Hacking can damage information, enable theft, compromise systems, and cost businesses millions per year. Hackers can be black hats who intend harm, white hats who perform security work, or gray hats who do both. Common attack types include DoS, password guessing, and man-in-the-middle. Hacking tools are widely available online, and passwords can be cracked using dictionary, brute force, and other attacks.Hacking ppt



Hacking pptRashed Sayyed
?
This PPT help you to present the topic Hacking at collage level and professional level. If you need more please share an email rashed_ec2012@rediffmail.comHacking



Hackingj naga sai
?
This presentation discusses different types of hacking including website, email, network, password, online banking, and computer hacking. Website hacking involves gaining unauthorized access to take control of a website. Email hacking is illicit access to email accounts or correspondence. Network hacking gathers information about a domain using tools. Password hacking recovers secret passwords through techniques like hashing, guessing, or brute force. Online banking hacking accesses bank accounts without permission. Computer hacking views, creates, or edits files without authorization. Ethical hackers test security systems to evaluate vulnerabilities rather than for malicious reasons. The presentation concludes with tips to protect online accounts and hiring ethical hackers.Hacking



HackingSharique Masood
?
This document defines hacking and discusses its history and types. It began in the 1960s at MIT and was done by early computer programmers out of curiosity. There are three main types of hackers - black hat hackers violate security for gain/malice, white hats exploit weaknesses ethically, and grey hats fall in between. Reasons for hacking include fun, status, stealing information, or destroying enemy networks. The document outlines various hacking techniques like website, network, password and computer hacking. It provides tips for securing data and accounts as well as discussing advantages like recovering lost information and disadvantages like harming privacy and illegality.Final report ethical hacking



Final report ethical hackingsamprada123
?
The document discusses how the growth of the internet has enhanced businesses but also increased security threats from computer criminals hacking systems. While the internet has provided many benefits, it also has increased risks from hackers that can break into websites and servers to steal information or implant viruses. The document introduces ethical hacking as a way to help organizations by proactively identifying vulnerabilities in their systems to better protect against cyber threats.Hacking And Its Prevention



Hacking And Its PreventionDinesh O Bareja
?
Hacking is good and bad depending on who you are. Prevention tips to safeguard against hacking.
20090320, Ver 2.0Basic Introduction to hacking



Basic Introduction to hackingSainath Volam
?
This document discusses what hacking is and provides information on different types of hackers and hacking techniques. It defines hackers as people who examine computer systems very closely, and distinguishes between white hat, gray hat, and black hat hackers. It also outlines common hacking methods like keylogging, sniffing, and SQL injection. The document then explains why hackers hack and what they typically do after gaining access such as installing backdoors. It concludes with tips on how to protect systems against hackers through patching, encryption, firewalls and backups.Internet and personal privacy



Internet and personal privacyRoshan Kumar Bhattarai
?
Computer Security: Vulnerabilities and Solutions is a document that discusses computer and internet security. It begins with an introduction to hacking, including the different types of hackers like white hat, black hat, and grey hat hackers. It then discusses common vulnerabilities like viruses, worms, Trojan horses, phishing attacks, and denial of service attacks. The document concludes by providing some common solutions for improving security, such as using antivirus software, firewalls, being cautious of unknown links and apps, and educating yourself on computer security best practices.More Related Content
What's hot (19)
Secure Shell - a Presentation on Ethical Hacking



Secure Shell - a Presentation on Ethical HackingNitish Kasar
?
This document summarizes a seminar on ethical hacking and secure shell. It defines hacking and different types of hackers such as script kiddies, phreakers, and hacktivists. It outlines the basic steps of hacking including footprinting, scanning, gaining access, and maintaining access. The seminar discusses recent phishing attacks and the need for ethical hacking to make cyberspace more secure. It describes a secure shell course that teaches skills like networking, Linux, windows hacking, and penetration methodologies over 30 days to help pursue a career in ethical hacking which is in high demand. The document concludes with tips for creating a secure password.Hacking



Hackingvkradhika
?
The document discusses different types of hacking including website, email, network, password, online banking, and computer hacking. It describes various hackers like white hat, black hat, and grey hat hackers and provides examples of famous hackers such as Kevin Mitnick and Kevin Poulsen. The document concludes with tips to prevent hacking which include using strong passwords, installing antivirus software, avoiding disclosure of personal details, employing ethical hackers, and other internet safety practices.Hacking presentation



Hacking presentationdineshgarhwal77
?
Hacking refers to activities aimed at exploiting security flaws to obtain personal or private information without authorization. A typical hacker will identify a target system, gather information about it, find a security loophole, exploit that loophole using hacking software to access the system without authorization, and then delete traces of their access. Hackers target systems for reasons like stealing credit card or identity information, accessing business information, or proving their skills. Hacking can result in significant financial losses for companies and the loss of private data. Countries with the most hackers include the United States, China, Turkey, Russia, and others.Hacking & its types



Hacking & its typesSai Sakoji
?
This document provides an overview of hacking, including its history, definitions, types, famous hackers, reasons for hacking, and advice on security and ethics. Hacking emerged in the 1960s at MIT and refers to attempting to gain unauthorized access to computer systems. It describes hackers as those who exploit weaknesses in computers. Different types of hacking are outlined such as website, network, password, and computer hacking. Advice is given around using strong unique passwords, backing up data, and contacting authorities if hacked. Both advantages like security testing and disadvantages like privacy harm are discussed.Ethical Hacking and Network Security



Ethical Hacking and Network Securitysumit dimri
?
Hi, friends today Iam presented my ppt on ethical hacking and network security. This will gives you some basic tips and ideas about hacking and how to make our network secure.hacking



hackingmayank1293
?
Hacking involves gaining unauthorized access to computer systems, which is illegal. There are different types of hackers, including white hats who help find security vulnerabilities, black hats who hack with malicious intent, and grey hats in between. Reasons for hacking include financial gain, showing off skills, or just for fun. Experts recommend using antivirus software, avoiding suspicious links and downloads, and keeping software updated to help prevent hacking.Computer hacking



Computer hackingArjun Tomar
?
You all can infer what would be in the PPT from the title itself. In this PPT it is not told directly how to hack. Just a brief info of hacking and cyber security is given. How can one save himself/herself from becoming a victim of cybercrime? How to hack is given in my next PPT?Basic of Ethical Hacking and Penetration Testing - 1st Module



Basic of Ethical Hacking and Penetration Testing - 1st Moduleankit sarode
?
This document provides an introduction to information security topics such as penetration testing, hacking, and ethical hacking. It defines penetration testing as attacking a system to find security weaknesses and potential access. Hacking is exploiting vulnerabilities in computer systems, while ethical hacking does the same thing legally with permission. The document also discusses the differences between hackers and crackers, careers in information security such as penetration testing and cyber crime investigation, and provides references for further information security terms and resources.Common hacking tactics



Common hacking tacticsFariha Khudzri
?
Common hacking tactics include vulnerability scanners that check for known weaknesses, spoofing attacks like phishing that masquerade as trusted systems, password cracking by repeatedly guessing passwords, packet sniffers that capture network data including passwords, social engineering by tricking users, key loggers that record keystrokes to steal passwords, Trojan horses that pose as one thing but do another like enabling backdoor access, and viruses that self-replicate to spread malware. Hackers use these tactics to access systems and steal confidential information without authorization.Ethical hacking presentation



Ethical hacking presentationZahid Rajeel
?
Hacking can be either legal or illegal depending on authorization and intent. Ethical hacking involves performing the same activities as illegal hacking but with the owner's permission as part of an overall security program. The history of hacking began in the 1960s and different types of hackers like phone phreakers emerged over subsequent decades as technology advanced. There are different types of illegal hacking techniques but also ethical white hat and grey hat hackers who use their skills to help protect systems rather than for personal gain or malicious purposes. The consequences of illegal hacking can include fines, imprisonment, and computer seizure.Hacking and Hackers



Hacking and HackersFarwa Ansari
?
This presentation provided information on communication skills and hackers. It began with an introduction to the topic of hackers, defining what a hacker is and discussing different types of hackers such as black hat, white hat, grey hat, and script kiddie hackers. The presentation then discussed famous hackers like Albert Gonzalez, Jonathan James, Ian Murphy, and John Draper. It provided details on some of their hacking activities. The presentation concluded with tips on how to prevent hacking, including keeping software and operating systems updated, using firewalls and antivirus software, avoiding suspicious websites and emails, and having strong passwords.Windows Hacking



Windows HackingMayur Sutariya
?
This document discusses different types of hackers and methods of hacking passwords. It defines white hat and black hat hackers, with white hats using their skills constructively and ethically to find security vulnerabilities, while black hats use their skills illegally and destructively. The document also discusses crackers/attackers who hack with malicious intent, phreaks who hack phone networks, and script kiddies who exploit known vulnerabilities without technical skills. It provides examples of password cracking tools and methods like Cain & Abel, LCP, password dumping, and using Windows repair mode. It notes the importance of security awareness and prevention.Introduction To Ethical Hacking



Introduction To Ethical HackingAkshay Kale
?
1. The document introduces the topic of ethical hacking by defining hacking and explaining its origins in computer culture at MIT in the 1960s, where hackers were students who pursued recreational activities rather than studying.
2. It describes the three main types of hackers: white hat hackers who find security vulnerabilities ethically, black hat hackers who do so illegally and destructively, and grey hat hackers who exhibit traits of both.
3. The document outlines the typical hacking methodology of reconnaissance, scanning, gaining access, maintaining access, and covering tracks, and provides examples of common low-tech and high-tech hacking techniques.Ethical hacking



Ethical hackingHarshit Upadhyay
?
This presentation provides an overview of ethical hacking. It defines ethical hacking as illegally accessing another system, but for good purposes like testing security. It explains that actual hacking is not a crime, but is made so by those who hack for bad reasons, known as crackers. Ethical hackers help ensure security, while hackers access systems for either good or bad reasons and crackers specifically aim to spread malware or steal information. The presentation outlines the importance of ethical hacking for security and some basic steps anyone can take to help protect themselves from hacking.Computer Hacking - An Introduction



Computer Hacking - An IntroductionJayaseelan Vejayon
?
Hacking involves modifying systems outside of their intended purpose. It is commonly done by teenagers and young adults using computers. Reasons for hacking include profit, protest, and challenge. Hacking can damage information, enable theft, compromise systems, and cost businesses millions per year. Hackers can be black hats who intend harm, white hats who perform security work, or gray hats who do both. Common attack types include DoS, password guessing, and man-in-the-middle. Hacking tools are widely available online, and passwords can be cracked using dictionary, brute force, and other attacks.Hacking ppt



Hacking pptRashed Sayyed
?
This PPT help you to present the topic Hacking at collage level and professional level. If you need more please share an email rashed_ec2012@rediffmail.comHacking



Hackingj naga sai
?
This presentation discusses different types of hacking including website, email, network, password, online banking, and computer hacking. Website hacking involves gaining unauthorized access to take control of a website. Email hacking is illicit access to email accounts or correspondence. Network hacking gathers information about a domain using tools. Password hacking recovers secret passwords through techniques like hashing, guessing, or brute force. Online banking hacking accesses bank accounts without permission. Computer hacking views, creates, or edits files without authorization. Ethical hackers test security systems to evaluate vulnerabilities rather than for malicious reasons. The presentation concludes with tips to protect online accounts and hiring ethical hackers.Hacking



HackingSharique Masood
?
This document defines hacking and discusses its history and types. It began in the 1960s at MIT and was done by early computer programmers out of curiosity. There are three main types of hackers - black hat hackers violate security for gain/malice, white hats exploit weaknesses ethically, and grey hats fall in between. Reasons for hacking include fun, status, stealing information, or destroying enemy networks. The document outlines various hacking techniques like website, network, password and computer hacking. It provides tips for securing data and accounts as well as discussing advantages like recovering lost information and disadvantages like harming privacy and illegality.Final report ethical hacking



Final report ethical hackingsamprada123
?
The document discusses how the growth of the internet has enhanced businesses but also increased security threats from computer criminals hacking systems. While the internet has provided many benefits, it also has increased risks from hackers that can break into websites and servers to steal information or implant viruses. The document introduces ethical hacking as a way to help organizations by proactively identifying vulnerabilities in their systems to better protect against cyber threats.Viewers also liked (20)
Hacking And Its Prevention



Hacking And Its PreventionDinesh O Bareja
?
Hacking is good and bad depending on who you are. Prevention tips to safeguard against hacking.
20090320, Ver 2.0Basic Introduction to hacking



Basic Introduction to hackingSainath Volam
?
This document discusses what hacking is and provides information on different types of hackers and hacking techniques. It defines hackers as people who examine computer systems very closely, and distinguishes between white hat, gray hat, and black hat hackers. It also outlines common hacking methods like keylogging, sniffing, and SQL injection. The document then explains why hackers hack and what they typically do after gaining access such as installing backdoors. It concludes with tips on how to protect systems against hackers through patching, encryption, firewalls and backups.Internet and personal privacy



Internet and personal privacyRoshan Kumar Bhattarai
?
Computer Security: Vulnerabilities and Solutions is a document that discusses computer and internet security. It begins with an introduction to hacking, including the different types of hackers like white hat, black hat, and grey hat hackers. It then discusses common vulnerabilities like viruses, worms, Trojan horses, phishing attacks, and denial of service attacks. The document concludes by providing some common solutions for improving security, such as using antivirus software, firewalls, being cautious of unknown links and apps, and educating yourself on computer security best practices.Evaporation New Template



Evaporation New Templatedloschiavo
?
APV Evaporation has over 3,000 evaporation unit installations since 1943. They provide turnkey evaporation solutions using various technologies like plate evaporators, falling film plate evaporators, rising/falling film plate evaporators, forced circulation plate evaporators, and MVR evaporators. They have extensive experience processing foods, juices, purees, and other products across many industries.Evaporation



EvaporationSayeed Hasan
?
Evaporation is the process by which a liquid or solid changes into a vapor. It occurs when molecules near the surface of a substance gain enough kinetic energy from heat to break away from intermolecular forces holding them together. The rate of evaporation depends on factors like temperature, pressure, concentration, and surface area. Evaporation plays an important role in nature and has several industrial applications such as drying, cooling, and distillation.Hacking 1



Hacking 1sonal bisla
?
This document defines hacking and different types of hackers. It discusses website, network, email, password and computer hacking. It also covers advantages like finding security weaknesses, and disadvantages like privacy harm. Preventive measures include strong antivirus and unique passwords. The document provides steps to take after being hacked like shutting down systems, and restoring from backups. It concludes that while hackers have innovative spirits, their actions should not harm others.Hacking Movable Type



Hacking Movable TypeStefano Rodighiero
?
This document discusses extending the functionality of Movable Type through plugins. It provides examples of plugins that add new template tags and panels. Plugins allow developers to tap into Movable Type's existing interfaces and extend the capabilities of its core applications. The document also references additional resources for learning more about customizing Movable Type through the use of plugins and its plugin API.Cybercrime (Computer Hacking)



Cybercrime (Computer Hacking)Michael Asres
?
This presentation deals with the past, present and future implications of cybercrime with respect to computer hacking.Is hacking good or bad



Is hacking good or badAshish Chandurkar
?
The document discusses different types of hackers and their activities. It defines hacking as gaining unauthorized access to computer systems and networks. White hat hackers use their skills ethically to test security and help organizations, like Linus Torvalds who created Linux. Black hat hackers violate security for malicious reasons, such as Jonathan James who stole software from NASA. The document concludes that hacking can be good when used to create innovative technologies, but should not be used for illegal activities.my new HACKING



my new HACKINGBABATUNDE OLANREWAJU GEORGE
?
This document provides an outline for a presentation on hacking. It begins with definitions of hacking and different types of hackers. The history and evolution of hacking is discussed. Various types of hacking techniques like denial of service attacks, password cracking, and social engineering are described. Common hacking tools such as Nmap, Cain and Abel, and keyloggers are listed. The document outlines how hacking attacks work and their potential effects. It discusses certifications in ethical hacking and concludes that while hacking can be a crime, proper security measures and computer ethics can help prevent and detect hacking activities.Hacking



HackingAmit Pandey
?
Hacking involves different types of threats to computer systems, including attacks on availability, confidentiality, integrity, and authentication. The document outlines the history of hacking from the 1970s telephone hacking to modern viruses and worms. It defines ethical hackers as those who test security systems with authorization to find vulnerabilities, unlike black hat hackers who break into systems illegally and for malicious purposes such as cybercrime.AMAZING COMPUTER TRICKS



AMAZING COMPUTER TRICKSMarc Jones
?
This document provides 4 keyboard shortcuts for Windows: Ctrl+Shift+N to create a new folder, Ctrl+Shift+Click to open a program as administrator, Shift+Right-Click enhances the Send to menu, and Shift+Right-Click on a folder to open the Command Prompt. It also includes a link to a YouTube video about unfiltering websites.Science - Evaporation



Science - EvaporationRutvij Vagadia
?
Evaporation is the process where a liquid turns into vapor below its boiling point. The rate of evaporation is affected by temperature, surface area of the liquid, humidity of the air, and wind speed. Some advantages of evaporation include bringing rain, cooling water, sustaining the water cycle, purifying water, obtaining salt, and drying clothes.Soil Steady-State Evaporation



Soil Steady-State EvaporationMorteza Sadeghi
?
In this presentation, an exact analytical solution to steady state evaporation from porous media is introduced. The solution is presented in terms of a set of infinite series. An advantage of this solution compared to previous derivations is that the infinite series can be very closely approximated using a closed-form solution (i.e.,
excluding integrals or series).Group 4 (evaporation)



Group 4 (evaporation)Annellies Anzuari
?
1) Evaporation is the process where molecules in liquid state (water) spontaneously change into gas state (steam), which is the reverse of condensation.
2) Evaporation can be used to thicken foods like fruit juice, milk, and coffee by removing some of the water.
3) There are two conditions of evaporation - natural evaporation and evaporation that occurs in equipment using applied steam. Factors that affect the evaporation rate include temperature, pressure, surface area, material type and viscosity.CFD-based Evaporation Estimation Approach



CFD-based Evaporation Estimation ApproachAli Abbasi
?
The document presents a CFD-based approach for estimating short-term evaporation from complex small lakes in arid regions. It describes the challenges of accurately estimating evaporation and introduces a proposed approach using computational fluid dynamics to model heat and mass transfer over the water surface. A case study is presented on Lake Binaba in Ghana to demonstrate the simulation process and framework. Results show the method can produce high spatial resolution data on evaporation rates and fluxes over the water surface under different climatic scenarios. The proposed approach provides an effective means of estimating evaporation that considers important factors like advection and atmospheric instability.Water evaporation reduction from lakes



Water evaporation reduction from lakesguestb311d8
?
Water evaporation reduction from lakes.
Water conservation
Water evaporation retardation .
Water management.Hacking sites for fun and profit



Hacking sites for fun and profitDavid Stockton
?
Intro slides for a tutorial on hacking common vulnerabilities and how to prevent those problems in your own code. This is a PHP based tutorial that's hands on, but the slides can help as reference material for a few common hacksHacking And EthicalHacking By Satish



Hacking And EthicalHacking By SatishNugala Sathesh Chowdary
?
This document discusses hacking and different types of hackers. It defines hackers as people who build things and crackers as people who break things. There are three main types of hackers: white-hat hackers who find vulnerabilities to strengthen security, black-hat hackers who hack systems secretly or to steal information, and grey-hat hackers who are in between. The document also provides the "hackers language" which substitutes numbers and symbols for letters to disguise communications, and recommends steps like using antivirus software and being careful about personal details online to help prevent hacking.Recently uploaded (20)
Wondershare Filmora Crack 14.3.2.11147 Latest



Wondershare Filmora Crack 14.3.2.11147 Latestudkg888
?
https://ncracked.com/7961-2/
Note: >> Please copy the link and paste it into Google New Tab now Download link
Free Download Wondershare Filmora 14.3.2.11147 Full Version - All-in-one home video editor to make a great video.Free Download Wondershare Filmora for Windows PC is an all-in-one home video editor with powerful functionality and a fully stacked feature set. Filmora has a simple drag-and-drop top interface, allowing you to be artistic with the story you want to create.Video Editing Simplified - Ignite Your Story. A powerful and intuitive video editing experience. Filmora 10 hash two new ways to edit: Action Cam Tool (Correct lens distortion, Clean up your audio, New speed controls) and Instant Cutter (Trim or merge clips quickly, Instant export).Filmora allows you to create projects in 4:3 or 16:9, so you can crop the videos or resize them to fit the size you want. This way, quickly converting a widescreen material to SD format is possible.A Framework for Model-Driven Digital Twin Engineering



A Framework for Model-Driven Digital Twin EngineeringDaniel Lehner
?
ºÝºÝߣs from my PhD Defense at Johannes Kepler University, held on Janurary 10, 2025.
The full thesis is available here: https://epub.jku.at/urn/urn:nbn:at:at-ubl:1-83896Brave Browser Crack 1.45.133 Activated 2025



Brave Browser Crack 1.45.133 Activated 2025kherorpacca00126
?
https://ncracked.com/7961-2/
Note: >> Please copy the link and paste it into Google New Tab now Download link
Brave is a free Chromium browser developed for Win Downloads, macOS and Linux systems that allows users to browse the internet in a safer, faster and more secure way than its competition. Designed with security in mind, Brave automatically blocks ads and trackers which also makes it faster,
As Brave naturally blocks unwanted content from appearing in your browser, it prevents these trackers and pop-ups from slowing Download your user experience. It's also designed in a way that strips Downloaden which data is being loaded each time you use it. Without these components
BoxLang JVM Language : The Future is Dynamic



BoxLang JVM Language : The Future is DynamicOrtus Solutions, Corp
?
Just like life, our code must evolve to meet the demands of an ever-changing world. Adaptability is key in developing for the web, tablets, APIs, or serverless applications. Multi-runtime development is the future, and that future is dynamic. Enter BoxLang: Dynamic. Modular. Productive. (www.boxlang.io)
BoxLang transforms development with its dynamic design, enabling developers to write expressive, functional code effortlessly. Its modular architecture ensures flexibility, allowing easy integration into your existing ecosystems.
Interoperability at Its Core
BoxLang boasts 100% interoperability with Java, seamlessly blending traditional and modern development practices. This opens up new possibilities for innovation and collaboration.
Multi-Runtime Versatility
From a compact 6MB OS binary to running on our pure Java web server, CommandBox, Jakarta EE, AWS Lambda, Microsoft Functions, WebAssembly, Android, and more, BoxLang is designed to adapt to any runtime environment. BoxLang combines modern features from CFML, Node, Ruby, Kotlin, Java, and Clojure with the familiarity of Java bytecode compilation. This makes it the go-to language for developers looking to the future while building a solid foundation.
Empowering Creativity with IDE Tools
Unlock your creative potential with powerful IDE tools designed for BoxLang, offering an intuitive development experience that streamlines your workflow. Join us as we redefine JVM development and step into the era of BoxLang. Welcome to the future.
DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (ƽɽÒã)



DAO UTokyo 2025 DLT mass adoption case studies IBM Tsuyoshi Hirayama (ƽɽÒã)Tsuyoshi Hirayama
?
DAO UTokyo 2025
–|¾©´óѧÇéˆóѧh ¥Ö¥í¥Ã¥¯¥Á¥§©`¥óÑо¿¥¤¥Ë¥·¥¢¥Æ¥£¥Ö
https://utbciii.com/2024/12/12/announcing-dao-utokyo-2025-conference/
Session 1 :DLT mass adoption
IBM Tsuyoshi Hirayama (ƽɽÒã)Unlocking DevOps Secuirty :Vault & Keylock



Unlocking DevOps Secuirty :Vault & KeylockHusseinMalikMammadli
?
DevOps i? t?hl¨¹k?sizliyi sizi maraqland?r?r? ?st?r developer, ist?r t?hl¨¹k?sizlik m¨¹h?ndisi, ist?rs? d? DevOps h?v?skar? olun, bu t?dbir ??b?k?l??m?k, bilikl?rinizi b?l¨¹?m?k v? DevSecOps sah?sind? ?n son t?cr¨¹b?l?ri ?yr?nm?k ¨¹?¨¹n m¨¹k?mm?l f¨¹rs?tdir!
Bu workshopda DevOps infrastrukturlar?n?n t?hl¨¹k?sizliyini nec? art?rmaq bar?d? dan??acay?q. DevOps sisteml?ri qurulark?n avtomatla?d?r?lm??, y¨¹ks?k ?l?atan v? etibarl? olmas? il? yana??, h?m d? t?hl¨¹k?sizlik m?s?l?l?ri n?z?r? al?nmal?d?r. Bu s?b?bd?n, DevOps komandolar?n?n t?hl¨¹k?sizliy? y?n?lmi? praktikalara riay?t etm?si vacibdir.Fl studio crack version 12.9 Free Download



Fl studio crack version 12.9 Free Downloadkherorpacca127
?
https://ncracked.com/7961-2/
Note: >>?? Please copy the link and paste it into Google New Tab now Download link
The ultimate guide to FL Studio 12.9 Crack, the revolutionary digital audio workstation that empowers musicians and producers of all levels. This software has become a cornerstone in the music industry, offering unparalleled creative capabilities, cutting-edge features, and an intuitive workflow.
With FL Studio 12.9 Crack, you gain access to a vast arsenal of instruments, effects, and plugins, seamlessly integrated into a user-friendly interface. Its signature Piano Roll Editor provides an exceptional level of musical expression, while the advanced automation features empower you to create complex and dynamic compositions.DealBook of Ukraine: 2025 edition | AVentures Capital



DealBook of Ukraine: 2025 edition | AVentures CapitalYevgen Sysoyev
?
The DealBook is our annual overview of the Ukrainian tech investment industry. This edition comprehensively covers the full year 2024 and the first deals of 2025. Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
![Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]](https://cdn.slidesharecdn.com/ss_thumbnails/mf2025-250305164811-a0930761-thumbnail.jpg?width=560&fit=bounds)
Formal Methods: Whence and Whither? [Martin Fr?nzle Festkolloquium, 2025]Jonathan Bowen
?
Alan Turing arguably wrote the first paper on formal methods 75 years ago. Since then, there have been claims and counterclaims about formal methods. Tool development has been slow but aided by Moore¡¯s Law with the increasing power of computers. Although formal methods are not widespread in practical usage at a heavyweight level, their influence as crept into software engineering practice to the extent that they are no longer necessarily called formal methods in their use. In addition, in areas where safety and security are important, with the increasing use of computers in such applications, formal methods are a viable way to improve the reliability of such software-based systems. Their use in hardware where a mistake can be very costly is also important. This talk explores the journey of formal methods to the present day and speculates on future directions.
UiPath Automation Developer Associate Training Series 2025 - Session 2



UiPath Automation Developer Associate Training Series 2025 - Session 2DianaGray10
?
In session 2, we will introduce you to Data manipulation in UiPath Studio.
Topics covered:
Data Manipulation
What is Data Manipulation
Strings
Lists
Dictionaries
RegEx Builder
Date and Time
Required Self-Paced Learning for this session:
Data Manipulation with Strings in UiPath Studio (v2022.10) 2 modules - 1h 30m - https://academy.uipath.com/courses/data-manipulation-with-strings-in-studio
Data Manipulation with Lists and Dictionaries in UiPath Studio (v2022.10) 2 modules - 1h - https:/academy.uipath.com/courses/data-manipulation-with-lists-and-dictionaries-in-studio
Data Manipulation with Data Tables in UiPath Studio (v2022.10) 2 modules - 1h 30m - https:/academy.uipath.com/courses/data-manipulation-with-data-tables-in-studio
?? For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. Computational Photography: How Technology is Changing Way We Capture the World



Computational Photography: How Technology is Changing Way We Capture the WorldHusseinMalikMammadli
?
? Computational Photography (Computer Vision/Image): How Technology is Changing the Way We Capture the World
He? d¨¹?¨¹nm¨¹s¨¹n¨¹zm¨¹, m¨¹asir smartfonlar v? kameralar nec? bu q?d?r g?z?l g?r¨¹nt¨¹l?r yarad?r? Bunun sirri Computational Fotoqrafiyas?nda(Computer Vision/Imaging) gizlidir¡ª??kill?ri ??km? v? emal etm? ¨¹sulumuzu t?kmill??dir?n, komp¨¹ter elmi il? fotoqrafiyan?n inqilabi birl??m?si.TrustArc Webinar - Building your DPIA/PIA Program: Best Practices & Tips



TrustArc Webinar - Building your DPIA/PIA Program: Best Practices & TipsTrustArc
?
Understanding DPIA/PIAs and how to implement them can be the key to embedding privacy in the heart of your organization as well as achieving compliance with multiple data protection / privacy laws, such as GDPR and CCPA. Indeed, the GDPR mandates Privacy by Design and requires documented Data Protection Impact Assessments (DPIAs) for high risk processing and the EU AI Act requires an assessment of fundamental rights.
How can you build this into a sustainable program across your business? What are the similarities and differences between PIAs and DPIAs? What are the best practices for integrating PIAs/DPIAs into your data privacy processes?
Whether you're refining your compliance framework or looking to enhance your PIA/DPIA execution, this session will provide actionable insights and strategies to ensure your organization meets the highest standards of data protection.
Join our panel of privacy experts as we explore:
- DPIA & PIA best practices
- Key regulatory requirements for conducting PIAs and DPIAs
- How to identify and mitigate data privacy risks through comprehensive assessments
- Strategies for ensuring documentation and compliance are robust and defensible
- Real-world case studies that highlight common pitfalls and practical solutionsField Device Management Market Report 2030 - TechSci Research



Field Device Management Market Report 2030 - TechSci ResearchVipin Mishra
?
The Global Field Device Management (FDM) Market is expected to experience significant growth in the forecast period from 2026 to 2030, driven by the integration of advanced technologies aimed at improving industrial operations.
? According to TechSci Research, the Global Field Device Management Market was valued at USD 1,506.34 million in 2023 and is anticipated to grow at a CAGR of 6.72% through 2030. FDM plays a vital role in the centralized oversight and optimization of industrial field devices, including sensors, actuators, and controllers.
Key tasks managed under FDM include:
Configuration
Monitoring
Diagnostics
Maintenance
Performance optimization
FDM solutions offer a comprehensive platform for real-time data collection, analysis, and decision-making, enabling:
Proactive maintenance
Predictive analytics
Remote monitoring
By streamlining operations and ensuring compliance, FDM enhances operational efficiency, reduces downtime, and improves asset reliability, ultimately leading to greater performance in industrial processes. FDM¡¯s emphasis on predictive maintenance is particularly important in ensuring the long-term sustainability and success of industrial operations.
For more information, explore the full report: https://shorturl.at/EJnzR
Major companies operating in Global?Field Device Management Market are:
General Electric Co
Siemens AG
ABB Ltd
Emerson Electric Co
Aveva Group Ltd
Schneider Electric SE
STMicroelectronics Inc
Techno Systems Inc
Semiconductor Components Industries LLC
International Business Machines Corporation (IBM)
#FieldDeviceManagement #IndustrialAutomation #PredictiveMaintenance #TechInnovation #IndustrialEfficiency #RemoteMonitoring #TechAdvancements #MarketGrowth #OperationalExcellence #SensorsAndActuatorsUnlock AI Creativity: Image Generation with DALL¡¤E



Unlock AI Creativity: Image Generation with DALL¡¤EExpeed Software
?
Discover the power of AI image generation with DALL¡¤E, an advanced AI model that transforms text prompts into stunning, high-quality visuals. This presentation explores how artificial intelligence is revolutionizing digital creativity, from graphic design to content creation and marketing. Learn about the technology behind DALL¡¤E, its real-world applications, and how businesses can leverage AI-generated art for innovation. Whether you're a designer, developer, or marketer, this guide will help you unlock new creative possibilities with AI-driven image synthesis.Replacing RocksDB with ScyllaDB in Kafka Streams by Almog Gavra



Replacing RocksDB with ScyllaDB in Kafka Streams by Almog GavraScyllaDB
?
Learn how Responsive replaced embedded RocksDB with ScyllaDB in Kafka Streams, simplifying the architecture and unlocking massive availability and scale. The talk covers unbundling stream processors, key ScyllaDB features tested, and lessons learned from the transition.World Information Architecture Day 2025 - UX at a Crossroads



World Information Architecture Day 2025 - UX at a CrossroadsJoshua Randall
?
User Experience stands at a crossroads: will we live up to our potential to design a better world? or will we be co-opted by ¡°product management¡± or another business buzzword?
Looking backwards, this talk will show how UX has repeatedly failed to create a better world, drawing on industry data from Nielsen Norman Group, Baymard, MeasuringU, WebAIM, and others.
Looking forwards, this talk will argue that UX must resist hype, say no more often and collaborate less often (you read that right), and become a true profession ¡ª in order to be able to design a better world.MIND Revenue Release Quarter 4 2024 - Finacial Presentation



MIND Revenue Release Quarter 4 2024 - Finacial PresentationMIND CTI
?
MIND Revenue Release Quarter 4 2024 - Finacial PresentationTransform Your Future with Front-End Development Training



Transform Your Future with Front-End Development TrainingVtechlabs
?
Kickstart your career in web development with our front-end web development course in Vadodara. Learn HTML, CSS, JavaScript, React, and more through hands-on projects and expert mentorship. Our front-end development course with placement includes real-world training, mock interviews, and job assistance to help you secure top roles like Front-End Developer, UI/UX Developer, and Web Designer.
Join VtechLabs today and build a successful career in the booming IT industry!UiPath Automation Developer Associate Training Series 2025 - Session 1



UiPath Automation Developer Associate Training Series 2025 - Session 1DianaGray10
?
Welcome to UiPath Automation Developer Associate Training Series 2025 - Session 1.
In this session, we will cover the following topics:
Introduction to RPA & UiPath Studio
Overview of RPA and its applications
Introduction to UiPath Studio
Variables & Data Types
Control Flows
You are requested to finish the following self-paced training for this session:
Variables, Constants and Arguments in Studio 2 modules - 1h 30m - https://academy.uipath.com/courses/variables-constants-and-arguments-in-studio
Control Flow in Studio 2 modules - 2h 15m - https:/academy.uipath.com/courses/control-flow-in-studio
?? For any questions you may have, please use the dedicated Forum thread. You can tag the hosts and mentors directly and they will reply as soon as possible. hacking and its types
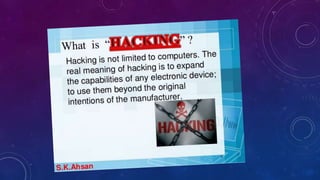
- 2. HACKING ? The person who stole your purse are called ¡°___________¡±. ? Some one exploits vulnerabilities on your computer and gain all your personal data.
- 4. TYPES OF HACKERS: White hat: Also called as ethical hackers. They do with non-malicious intention. Their goal is to strengthen the defenses Black hat: known as offensive hackers or Crackers. they do with malicious intention.
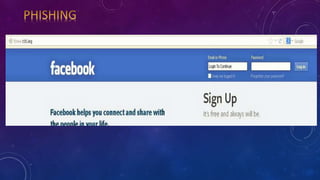
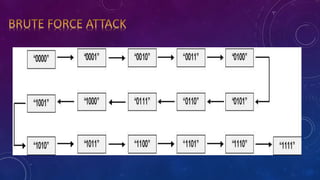
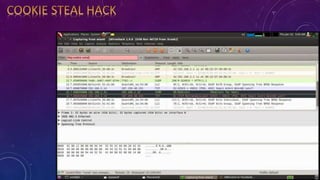
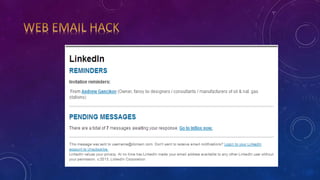
- 5. TYPES OF ATTACKS: ? Phishing attack ? Brute force attack ? Cookie steal attack ? Web email hack ? Creating worms and viruses ? Vulnerability scanner
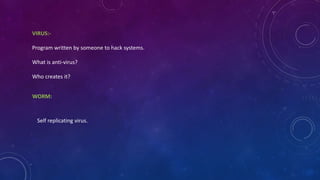
- 10. VIRUS:- Program written by someone to hack systems. What is anti-virus? Who creates it? WORM: Self replicating virus.

