The Security culture campaign explained in 5 minutes
- 1. The Anatomy of a Security Culture Campaign The Security Culture Framework: https://scf.roer.com
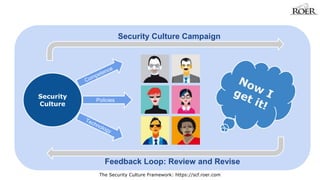
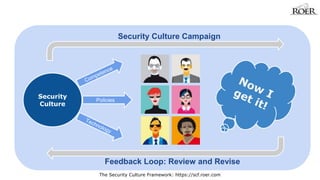
- 2. Security Culture Campaign Feedback Loop: Review and Revise The Security Culture Framework: https://scf.roer.com Security Culture
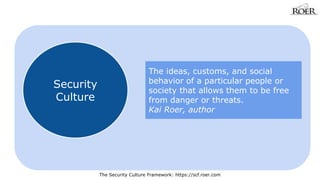
- 3. The Security Culture Framework: https://scf.roer.com Security Culture The ideas, customs, and social behavior of a particular people or society that allows them to be free from danger or threats. Kai Roer, author
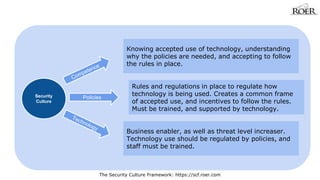
- 4. The Security Culture Framework: https://scf.roer.com Security Culture Knowing accepted use of technology, understanding why the policies are needed, and accepting to follow the rules in place. Rules and regulations in place to regulate how technology is being used. Creates a common frame of accepted use, and incentives to follow the rules. Must be trained, and supported by technology. Business enabler, as well as threat level increaser. Technology use should be regulated by policies, and staff must be trained.
- 5. People are different. Adapt to their needs! The Security Culture Framework: https://scf.roer.com
- 6. Your Goal! The Security Culture Framework: https://scf.roer.com
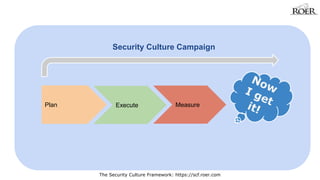
- 7. Security Culture Campaign Plan Execute Measure The Security Culture Framework: https://scf.roer.com
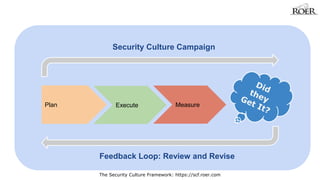
- 8. Security Culture Campaign Plan Execute Measure Feedback Loop: Review and Revise The Security Culture Framework: https://scf.roer.com
- 9. Feedback from the Campaign is fed back into the next campaign to build on the results. As culture is changed, the new culture emerges and feeds back into the program, creating a stronger culture each time. Feedback Loop: Review and Revise The Security Culture Framework: https://scf.roer.com 1 2
- 10. Security Culture Campaign Feedback Loop: Review and Revise The Security Culture Framework: https://scf.roer.com Security Culture
- 11. Download templates and join the community to discuss security culture https://scf.roer.com The Security Culture Framework: https://scf.roer.com