Tren it 2012
Download as pptx, pdf0 likes546 views
Teknologi terus berkembang dengan akses internet yang semakin cepat dan murah melalui jaringan nirkabel, platform bergerak menjadi lebih populer daripada desktop, dan aplikasi seluler menggantikan program komputer.
1 of 7
Downloaded 11 times



![Teknologi Telekomunikasi
ŌĆó Makin cepat dalam speed.
ŌĆó Makin lebar dalam coverage. Ubiquitous.
ŌĆó Always On
ŌĆó Makin murah[?]](https://image.slidesharecdn.com/trenit2012-120629183306-phpapp01/85/Tren-it-2012-5-320.jpg)


Ad
Recommended
Kisi kisi uts kontek
Kisi kisi uts kontekMohamad Yusup
╠²
Kisi-kisi UTS mencakup konsep-konsep teknologi seperti skema teknologi web, teknologi sistem informasi, teknologi multimedia, teknologi internet, dan aplikasi online.Security short intro
Security short introbudi rahardjo
╠²
Dokumen tersebut membahas tentang pentingnya keamanan (security) dalam sistem informasi meskipun seringkali dianggap sebagai persyaratan non-fungsional dan kalah prioritas dibandingkan persyaratan bisnis. Tanpa keamanan yang memadai, sistem informasi rentan terhadap ancaman siber yang dapat merugikan organisasi. Dokumen ini menjelaskan berbagai aspek keamanan mulai dari jaringan, sistem operasi, aplikasi hingga database serta kontrolIT Security Human Resources
IT Security Human Resourcesbudi rahardjo
╠²
The document discusses the need for IT security professionals to fill positions in industry, government, and academia due to growing dependence on technology, but there is currently a lack of qualified human resources locally. It proposes initiatives like increasing security courses and training programs at universities, incentivizing certification, and establishing forums for sharing to help develop IT security expertise at different levels from awareness to advanced skills. The Institut Teknologi Bandung plans to launch an information security graduate program in August 2013 to help address this challenge.Product development
Product developmentbudi rahardjo
╠²
The document discusses key considerations for product development including identifying user needs and problems to solve, developing the product with a focus on user experience, and managing requirements and timelines. It addresses determining what product to create, factors that drive necessity and invention, and developing cool technologies to solve problems. The presentation was given at the Institut Teknologi Bandung on November 26, 2011.Peranan ID-CERT Dalam Keamanan Cyber Space
Peranan ID-CERT Dalam Keamanan Cyber Spacebudi rahardjo
╠²
ID-CERT didirikan pada 1998 untuk menangani masalah keamanan siber di Indonesia. Organisasi ini bekerja secara sukarela untuk mengkoordinasikan insiden jaringan dan mendistribusikan laporan tentang ancaman seperti phishing. ID-CERT juga membuat statistik tentang insiden keamanan untuk meningkatkan kesadaran masyarakat. Namun, organisasi ini menghadapi tantangan seperti keterbatasan SDM dan pendanaan yang menghambat upaya mereka untuk melPertemuan 4 widget
Pertemuan 4 widgetobanganggara
╠²
Dokumen tersebut membahas tentang widget, tren teknologi perangkat mobile, dan fakta-fakta terkait perangkat bergerak. Secara ringkas, widget adalah aplikasi mini yang bisa digunakan langsung pada layar awal perangkat. Dokumen ini juga menyebutkan bahwa penggunaan perangkat mobile untuk akses internet diperkirakan akan melampaui komputer konvensional, dan perangkat mobile sudah menjadi alat bisnis penting bagi banyak perusahaanE-Commerce Chap 3: E-COMMERCE INFRASTRUCTURE: THE INTERNET, WEB, AND MOBILE P...
E-Commerce Chap 3: E-COMMERCE INFRASTRUCTURE: THE INTERNET, WEB, AND MOBILE P...Shandy Aditya
╠²
Dokumen tersebut membahas tentang konsep dasar Internet, protokol TCP/IP, alamat IP, domain name system, hypertext, bahasa markup seperti HTML dan XML, web server, web browser, fitur-fitur Internet seperti email, mesin pencari, forum online, media streaming, karakteristik Web 2.0, dan aplikasi seluler.Wsok Emagazine - Part 1
Wsok Emagazine - Part 1PT. Madani Cipta Informasi (Maintersys)
╠²
Dokumen tersebut membahas lima tren teknologi masa depan yang akan mempengaruhi dunia IT dan programming, yaitu: 1) interface tanpa sentuhan, 2) konten asli seperti TV online, 3) online yang besar-besaran, 4) semua terhubung ke internet, dan 5) supercomputing. Dokumen kedua membahas tujuh tren masa depan web antara lain web semantik, artificial intelligence, perubahan website menjadi web service, dunia virtual, video online, internet lebih cepat dan murah,Uji Keamanan Penetration Testing Itu Tidak Ilmiah
Uji Keamanan Penetration Testing Itu Tidak Ilmiahbudi rahardjo
╠²
Mengapa penetration testing (pentest) itu "tidak ilmiah". Metodologi yang digunakannya adalah coba-coba. Landasan paper. Secure SDLC. How to train Electronics Rockstars
How to train Electronics Rockstarsbudi rahardjo
╠²
The document discusses how to find, recruit, train, and retain electronics "rockstars". It notes that actively finding potential candidates is important. Recruitment should include success stories and engaging activities. Training requires providing context, building skills in a supportive environment beyond universities, and using experienced mentors and storytellers. Retention can be improved by incentives, a collaborative culture, and surrounding rockstars with other rockstars.Product development 2021
Product development 2021budi rahardjo
╠²
The document discusses various challenges and approaches to product development. The main challenges are lack of resources like human resources, technology, time, place, and financial resources. It suggests building the product yourself initially while keeping your day job or in school. It also recommends finding co-founders or outsourcing development, though outsourcing brings risks of requirement changes. Additional topics covered include where to build the product, focusing on essential minimum viable product features, designing for prototypes versus production, and testing your own product.Security in COVID-19 Era
Security in COVID-19 Erabudi rahardjo
╠²
Budi Rahardjo presented at the 2nd International Conference on Information and Computer Technology about security issues that have arisen during the COVID-19 pandemic. He discussed how eLearning systems have had to move online but often without considering security. He also examined examples of digital voting and contact tracing apps that were implemented in Indonesia along with privacy lessons learned. Finally, he emphasized that as society is forced to move activities online due to the pandemic, security issues will continue to follow unless they are prioritized during technology adoption.Peluang IoT di Indonesia
Peluang IoT di Indonesiabudi rahardjo
╠²
Dokumen ini membahas potensi Internet of Things (IoT) di Indonesia, termasuk berbagai aplikasi dan peluang dalam sektor seperti fintech, e-commerce, dan pertanian. Disorot juga pentingnya pengembangan teknologi dan perangkat yang semakin murah dan kecil. Terdapat harapan untuk menemukan aplikasi unggulan (killer applications) yang dapat memanfaatkan pasar IoT yang sangat besar di Indonesia.IoT: Dari Hobby ke Profesi
IoT: Dari Hobby ke Profesibudi rahardjo
╠²
Dokumen ini membahas perkembangan Internet of Things (IoT) dari hobi menjadi profesi, menekankan pentingnya pengembangan sumber daya manusia (SDM) di bidang ini untuk menghadapi tantangan industri 4.0. Dengan meningkatnya permintaan dan kemajuan teknologi, IoT diprediksi akan menjadi bagian integral dari kehidupan sehari-hari dan berbagai sektor industri. Untuk itu, diperlukan langkah serius dalam pendidikan dan sertifikasi profesional di bidang IoT.The Joy of Programming (short version)
The Joy of Programming (short version)budi rahardjo
╠²
The document discusses the author's love of coding and provides tips for becoming a good programmer. It recommends contributing to open source projects, always learning, and not forgetting the joy of coding. Coding is described as creating something from nothing, which is a god-like feeling. The author is a lecturer who loves coding as "just another perl hacker" and delivered a presentation on the topic.Technology-based Startup
Technology-based Startupbudi rahardjo
╠²
This document summarizes a presentation given by Budi Rahardjo at Pesantren Startup 2019 in Bandung about technology-based startups. Rahardjo is a founder and lecturer focused on areas like VLSI, security, social media, IoT, AI and big data. He argues that now is the ideal time to start a tech-based startup given that we live in a tech-ready environment surrounded by technology schools, and technology companies have high market value. However, challenges include difficulties finding qualified human resources and needing to create new markets and ecosystems while educating people. Rahardjo asks if attendees are ready to start their own tech-based startups.A very short Introduction to Software Security
A very short Introduction to Software Securitybudi rahardjo
╠²
Dokumen ini membahas berbagai aspek keamanan perangkat lunak, termasuk potensi kerentanan, penyebab masalah keamanan, dan pentingnya mempertimbangkan keamanan di setiap tahap pengembangan perangkat lunak. Terdapat juga penjelasan tentang metode pengujian keamanan, seperti analisis statis dan dinamis, serta kebutuhan untuk mengembangkan perangkat lunak yang aman. Selain itu, penekanan pada kolaborasi antara pengembang dan insinyur keamanan menjadi titik fokus dalam menciptakan aplikasi yang lebih aman.Identity Theft
Identity Theftbudi rahardjo
╠²
Dokumen tersebut membahas tentang pencurian identitas secara maya dan upaya untuk mencegahnya. Pencurian identitas dilakukan untuk penipuan keuangan atau pencemaran nama baik dengan menggunakan informasi pribadi seseorang seperti nama, foto, dan data akun media sosial tanpa izin. Untuk mencegahnya, pengguna perlu menggunakan sandi yang berbeda dan sulit ditebak untuk setiap akun serta mengaktifkan otDealing with Hoax
Dealing with Hoaxbudi rahardjo
╠²
Dokumen tersebut memberikan definisi hoax dan membedakannya dengan opini dan fakta. Hoax adalah pemalsuan kebenaran yang disebarkan untuk menipu orang lain. Dokumen ini juga menjelaskan penyebab maraknya hoax serta cara untuk mendeteksi kebenaran suatu informasi, seperti memeriksa sumber berita dan melakukan pencarian ulang informasi. Kemampuan untuk membedakan fakta dan hoax perlu ditingkatkan karena teknologi memudTopik Penelitian Keamanan Informasi
Topik Penelitian Keamanan Informasibudi rahardjo
╠²
Presentasi ini membahas beberapa topik penelitian terkait keamanan informasi yang bersifat aplikatif dan berskala nasional. Beberapa topik yang disebutkan meliputi kriptografi, steganografi, protokol keamanan, implementasi algoritma keamanan, dan aplikasi keamanan seperti blockchain. Presentasi ini menekankan pentingnya kolaborasi antar bidang ilmu dalam penelitian keamanan informasi.Network Sniffing
Network Sniffingbudi rahardjo
╠²
This document discusses network sniffing and capturing login credentials in plain text protocols. It describes setting up a telnet server and client to experiment with sniffing username and password information using tcpdump and ngrep tools on the local network. The document recommends trying the same technique on other protocols like FTP, POP, SMTP and exploring more secure replacement protocols due to vulnerabilities in sending plain text credentials over the network.Keaslian Dokumen Digital
Keaslian Dokumen Digitalbudi rahardjo
╠²
Dokumen ini membahas tentang keaslian dokumen digital dan tantangannya dalam era digital, termasuk penggunaan kriptografi untuk menjaga integritas dan keamanan data. Ditekankan bahwa tanda tangan digital dapat digunakan untuk memastikan keaslian dokumen, serta perlunya kebijakan yang mendukung penggunaan bentuk digital. Aspek penting seperti kerahasiaan, integritas, dan ketersediaan informasi juga dijelaskan.Strategi Industri Telematika Indonesia
Strategi Industri Telematika Indonesiabudi rahardjo
╠²
This document discusses Indonesia's telecommunications industry and the opportunities for growth in digital content with the rollout of 4G networks. It notes that digital content like animation, games, entertainment and education are areas with potential, as well as developing applications that solve local problems. However, it also outlines challenges like lack of human resources and infrastructure, as well as regulatory issues that could hinder the industry's development. The document concludes that while there are many challenges, the opportunities for growth in Indonesia's digital content market are substantial.Klik and Modar: social engineering dengan menggunakan URL Bait
Klik and Modar: social engineering dengan menggunakan URL Baitbudi rahardjo
╠²
Dokumen ini membahas metode social engineering melalui tautan bait yang disampaikan pada National Internet Security Day. Teknik ini melibatkan manipulasi emosional dan penggunaan URL pemancing yang menyembunyikan malware untuk mengeksploitasi pengguna. Kesadaran dan pengamanan seperti antivirus tetap penting untuk mencegah serangan semacam ini.To teach is ... (On Teaching)
To teach is ... (On Teaching)budi rahardjo
╠²
The document discusses the presenter's approach to teaching. It contains slides as placeholders to guide what they will talk about rather than being useful on their own. The slides share inspirational sayings about teaching with passion and through storytelling to inspire others, despite not being fully explanatory without the accompanying presentation. The presenter hopes the slides are still understandable and useful despite their intended purpose as presentation aids rather than standalone materials.How to Train Electronics Rockstars
How to Train Electronics Rockstarsbudi rahardjo
╠²
The document discusses how to train "electronics rockstars" and outlines strategies for finding, recruiting, training, and retaining talented students in electronics fields. It notes the need for universities to be proactive in finding students and promoting success stories to attract recruits. Effective training requires hands-on learning opportunities, mentors, and an engaging environment. Retaining top talent necessitates incentives like a supportive culture where experts can collaborate.Kronologis penganiayaan timmy
Kronologis penganiayaan timmybudi rahardjo
╠²
Seorang mahasiswa ITB bernama Julius ditikam dan dirampok oleh geng motor di Bandung. Julius ditikam berkali-kali hingga mengalami luka parah, tetapi berhasil diselamatkan dan kini sedang menjalani perawatan di rumah sakit. Kondisinya sudah membaik meski masih khawatir akan kehilangan beberapa perkuliahan.Bdg software uploaded
Bdg software uploadedbudi rahardjo
╠²
This document discusses the potential for Bandung, Indonesia to become a hub for software, games, and animation development. It notes that Bandung has universities that produce engineering and arts talents, a creative culture, lower costs than Jakarta, pleasant weather, and a history of technological innovation. The document outlines communities in Bandung that support science and technology and provides examples of disruptive technologies developed there in the past. It acknowledges challenges for startups in Bandung in accessing markets and surviving initial problems.More Related Content
More from budi rahardjo (20)
Uji Keamanan Penetration Testing Itu Tidak Ilmiah
Uji Keamanan Penetration Testing Itu Tidak Ilmiahbudi rahardjo
╠²
Mengapa penetration testing (pentest) itu "tidak ilmiah". Metodologi yang digunakannya adalah coba-coba. Landasan paper. Secure SDLC. How to train Electronics Rockstars
How to train Electronics Rockstarsbudi rahardjo
╠²
The document discusses how to find, recruit, train, and retain electronics "rockstars". It notes that actively finding potential candidates is important. Recruitment should include success stories and engaging activities. Training requires providing context, building skills in a supportive environment beyond universities, and using experienced mentors and storytellers. Retention can be improved by incentives, a collaborative culture, and surrounding rockstars with other rockstars.Product development 2021
Product development 2021budi rahardjo
╠²
The document discusses various challenges and approaches to product development. The main challenges are lack of resources like human resources, technology, time, place, and financial resources. It suggests building the product yourself initially while keeping your day job or in school. It also recommends finding co-founders or outsourcing development, though outsourcing brings risks of requirement changes. Additional topics covered include where to build the product, focusing on essential minimum viable product features, designing for prototypes versus production, and testing your own product.Security in COVID-19 Era
Security in COVID-19 Erabudi rahardjo
╠²
Budi Rahardjo presented at the 2nd International Conference on Information and Computer Technology about security issues that have arisen during the COVID-19 pandemic. He discussed how eLearning systems have had to move online but often without considering security. He also examined examples of digital voting and contact tracing apps that were implemented in Indonesia along with privacy lessons learned. Finally, he emphasized that as society is forced to move activities online due to the pandemic, security issues will continue to follow unless they are prioritized during technology adoption.Peluang IoT di Indonesia
Peluang IoT di Indonesiabudi rahardjo
╠²
Dokumen ini membahas potensi Internet of Things (IoT) di Indonesia, termasuk berbagai aplikasi dan peluang dalam sektor seperti fintech, e-commerce, dan pertanian. Disorot juga pentingnya pengembangan teknologi dan perangkat yang semakin murah dan kecil. Terdapat harapan untuk menemukan aplikasi unggulan (killer applications) yang dapat memanfaatkan pasar IoT yang sangat besar di Indonesia.IoT: Dari Hobby ke Profesi
IoT: Dari Hobby ke Profesibudi rahardjo
╠²
Dokumen ini membahas perkembangan Internet of Things (IoT) dari hobi menjadi profesi, menekankan pentingnya pengembangan sumber daya manusia (SDM) di bidang ini untuk menghadapi tantangan industri 4.0. Dengan meningkatnya permintaan dan kemajuan teknologi, IoT diprediksi akan menjadi bagian integral dari kehidupan sehari-hari dan berbagai sektor industri. Untuk itu, diperlukan langkah serius dalam pendidikan dan sertifikasi profesional di bidang IoT.The Joy of Programming (short version)
The Joy of Programming (short version)budi rahardjo
╠²
The document discusses the author's love of coding and provides tips for becoming a good programmer. It recommends contributing to open source projects, always learning, and not forgetting the joy of coding. Coding is described as creating something from nothing, which is a god-like feeling. The author is a lecturer who loves coding as "just another perl hacker" and delivered a presentation on the topic.Technology-based Startup
Technology-based Startupbudi rahardjo
╠²
This document summarizes a presentation given by Budi Rahardjo at Pesantren Startup 2019 in Bandung about technology-based startups. Rahardjo is a founder and lecturer focused on areas like VLSI, security, social media, IoT, AI and big data. He argues that now is the ideal time to start a tech-based startup given that we live in a tech-ready environment surrounded by technology schools, and technology companies have high market value. However, challenges include difficulties finding qualified human resources and needing to create new markets and ecosystems while educating people. Rahardjo asks if attendees are ready to start their own tech-based startups.A very short Introduction to Software Security
A very short Introduction to Software Securitybudi rahardjo
╠²
Dokumen ini membahas berbagai aspek keamanan perangkat lunak, termasuk potensi kerentanan, penyebab masalah keamanan, dan pentingnya mempertimbangkan keamanan di setiap tahap pengembangan perangkat lunak. Terdapat juga penjelasan tentang metode pengujian keamanan, seperti analisis statis dan dinamis, serta kebutuhan untuk mengembangkan perangkat lunak yang aman. Selain itu, penekanan pada kolaborasi antara pengembang dan insinyur keamanan menjadi titik fokus dalam menciptakan aplikasi yang lebih aman.Identity Theft
Identity Theftbudi rahardjo
╠²
Dokumen tersebut membahas tentang pencurian identitas secara maya dan upaya untuk mencegahnya. Pencurian identitas dilakukan untuk penipuan keuangan atau pencemaran nama baik dengan menggunakan informasi pribadi seseorang seperti nama, foto, dan data akun media sosial tanpa izin. Untuk mencegahnya, pengguna perlu menggunakan sandi yang berbeda dan sulit ditebak untuk setiap akun serta mengaktifkan otDealing with Hoax
Dealing with Hoaxbudi rahardjo
╠²
Dokumen tersebut memberikan definisi hoax dan membedakannya dengan opini dan fakta. Hoax adalah pemalsuan kebenaran yang disebarkan untuk menipu orang lain. Dokumen ini juga menjelaskan penyebab maraknya hoax serta cara untuk mendeteksi kebenaran suatu informasi, seperti memeriksa sumber berita dan melakukan pencarian ulang informasi. Kemampuan untuk membedakan fakta dan hoax perlu ditingkatkan karena teknologi memudTopik Penelitian Keamanan Informasi
Topik Penelitian Keamanan Informasibudi rahardjo
╠²
Presentasi ini membahas beberapa topik penelitian terkait keamanan informasi yang bersifat aplikatif dan berskala nasional. Beberapa topik yang disebutkan meliputi kriptografi, steganografi, protokol keamanan, implementasi algoritma keamanan, dan aplikasi keamanan seperti blockchain. Presentasi ini menekankan pentingnya kolaborasi antar bidang ilmu dalam penelitian keamanan informasi.Network Sniffing
Network Sniffingbudi rahardjo
╠²
This document discusses network sniffing and capturing login credentials in plain text protocols. It describes setting up a telnet server and client to experiment with sniffing username and password information using tcpdump and ngrep tools on the local network. The document recommends trying the same technique on other protocols like FTP, POP, SMTP and exploring more secure replacement protocols due to vulnerabilities in sending plain text credentials over the network.Keaslian Dokumen Digital
Keaslian Dokumen Digitalbudi rahardjo
╠²
Dokumen ini membahas tentang keaslian dokumen digital dan tantangannya dalam era digital, termasuk penggunaan kriptografi untuk menjaga integritas dan keamanan data. Ditekankan bahwa tanda tangan digital dapat digunakan untuk memastikan keaslian dokumen, serta perlunya kebijakan yang mendukung penggunaan bentuk digital. Aspek penting seperti kerahasiaan, integritas, dan ketersediaan informasi juga dijelaskan.Strategi Industri Telematika Indonesia
Strategi Industri Telematika Indonesiabudi rahardjo
╠²
This document discusses Indonesia's telecommunications industry and the opportunities for growth in digital content with the rollout of 4G networks. It notes that digital content like animation, games, entertainment and education are areas with potential, as well as developing applications that solve local problems. However, it also outlines challenges like lack of human resources and infrastructure, as well as regulatory issues that could hinder the industry's development. The document concludes that while there are many challenges, the opportunities for growth in Indonesia's digital content market are substantial.Klik and Modar: social engineering dengan menggunakan URL Bait
Klik and Modar: social engineering dengan menggunakan URL Baitbudi rahardjo
╠²
Dokumen ini membahas metode social engineering melalui tautan bait yang disampaikan pada National Internet Security Day. Teknik ini melibatkan manipulasi emosional dan penggunaan URL pemancing yang menyembunyikan malware untuk mengeksploitasi pengguna. Kesadaran dan pengamanan seperti antivirus tetap penting untuk mencegah serangan semacam ini.To teach is ... (On Teaching)
To teach is ... (On Teaching)budi rahardjo
╠²
The document discusses the presenter's approach to teaching. It contains slides as placeholders to guide what they will talk about rather than being useful on their own. The slides share inspirational sayings about teaching with passion and through storytelling to inspire others, despite not being fully explanatory without the accompanying presentation. The presenter hopes the slides are still understandable and useful despite their intended purpose as presentation aids rather than standalone materials.How to Train Electronics Rockstars
How to Train Electronics Rockstarsbudi rahardjo
╠²
The document discusses how to train "electronics rockstars" and outlines strategies for finding, recruiting, training, and retaining talented students in electronics fields. It notes the need for universities to be proactive in finding students and promoting success stories to attract recruits. Effective training requires hands-on learning opportunities, mentors, and an engaging environment. Retaining top talent necessitates incentives like a supportive culture where experts can collaborate.Kronologis penganiayaan timmy
Kronologis penganiayaan timmybudi rahardjo
╠²
Seorang mahasiswa ITB bernama Julius ditikam dan dirampok oleh geng motor di Bandung. Julius ditikam berkali-kali hingga mengalami luka parah, tetapi berhasil diselamatkan dan kini sedang menjalani perawatan di rumah sakit. Kondisinya sudah membaik meski masih khawatir akan kehilangan beberapa perkuliahan.Bdg software uploaded
Bdg software uploadedbudi rahardjo
╠²
This document discusses the potential for Bandung, Indonesia to become a hub for software, games, and animation development. It notes that Bandung has universities that produce engineering and arts talents, a creative culture, lower costs than Jakarta, pleasant weather, and a history of technological innovation. The document outlines communities in Bandung that support science and technology and provides examples of disruptive technologies developed there in the past. It acknowledges challenges for startups in Bandung in accessing markets and surviving initial problems.Tren it 2012
- 1. Tren Teknologi 2012 Budi Rahardjo http://rahard.wordpress.com rahard@gmal.com
- 2. Rangkuman Tren ŌĆó Akses ŌĆō Network semakin cepat (& always connected) ŌĆō Lebih murah ŌĆō 3G, Wimax, LTE ŌĆó Platform ŌĆō Notebook melewati # desktop ŌĆō Handphone melewati # komputer ŌĆó Aplikasi ŌĆō Apps menggantikan program aplikasi ŌĆō Android, Java, Web-based
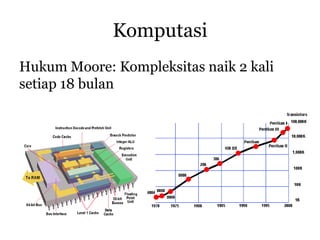
- 3. Komputasi Hukum Moore: Kompleksitas naik 2 kali setiap 18 bulan
- 4. Teknologi Storage ŌĆó Teknologi storage ŌĆō Kapasitas meningkat 3 kali setiap tahun? ŌĆō Harga turun dengan drastis ŌĆó Banjir informasi ŌĆō Storage dibutuhkan untuk menyimpan sampah informasi
- 5. Teknologi Telekomunikasi ŌĆó Makin cepat dalam speed. ŌĆó Makin lebar dalam coverage. Ubiquitous. ŌĆó Always On ŌĆó Makin murah[?]
- 6. Internet Wonders ŌĆó IEEE Spectrum ŌĆō November 2004 asked 40 Tech Gurus: ŌĆ£Most important technology of the last 40 yearsŌĆØ. Answers: ŌĆō Integrated Circuits ŌĆō Internet ŌĆō Computers ŌĆó Technology that has evolved in a surprising ways: ŌĆō Internet ŌĆō Cellular
- 7. Rangkuman Tren ŌĆó Akses ŌĆō Network semakin cepat (& always connected) ŌĆō Lebih murah ŌĆō 3G, Wimax, LTE ŌĆó Platform ŌĆō Notebook melewati # desktop ŌĆō Handphone melewati # komputer ŌĆó Aplikasi ŌĆō Apps menggantikan program aplikasi ŌĆō Android, Java, Web-based
