Google Codelabs§Ú§‰§√§∆§þ§ø
Download as pptx, pdf1 like3,001 views
æ©∂ºDev§´§’§ß#2 ?WWDC & Google IOætèա覆? LTŸY¡œ
1 of 21
Download to read offline












Ad
Recommended
ö¢§∑§∆§‚À¿§ § §§•¢•◊•Í ?Core Bluetooth §Œ°∏◊¥ëB§Œ±£¥Ê§»èÕ‘™°πôCƒÐ?
ö¢§∑§∆§‚À¿§ § §§•¢•◊•Í ?Core Bluetooth §Œ°∏◊¥ëB§Œ±£¥Ê§»èÕ‘™°πôCƒÐ?Shuichi Tsutsumi
?
Core Bluetooth §Œ•–•√•Ø•∞•È•¶•Û•…åg––•‚©`•…§À§ƒ§§§∆
?•–•√•Ø•∞•È•¶•Û•…§«§«§≠§Î§≥§»
?•–•√•Ø•∞•È•¶•Û•…§À§™§±§Î÷∆ºs
?◊¥ëB§Œ±£¥Ê§»èÕ‘™◊Ó–¬UE4•ø•§•»•Î§«§Œ•Ì©`•´•È•§•∫ ¬¿˝ (UE4 Localization Deep Dive)
◊Ó–¬UE4•ø•§•»•Î§«§Œ•Ì©`•´•È•§•∫ ¬¿˝ (UE4 Localization Deep Dive)•®•‘•√•Ø?•≤©`•ý•∫?•∏•„•—•Û Epic Games Japan
?
∞k±Ì’þ: ý_ΩÚÔL§µ§Þ£®•Ω•Ï•§•Ê÷Í Ωª·…Á£©
±æ•π•È•§•…§œ2019ƒÍ10‘¬31»’§À––§Ô§Ï§ø√„è䪷°∏ UE4 Localization Deep Dive°π§Œ÷v—ðŸY¡œ§»§ §Í§Þ§π°£•Ω•Ï•§•Êòî°¢§≥§Œ§Ë§¶§ ŸF÷ÿ§ «ÈàÛ§Ú“ª∞„§Àπ´È_§∑§∆§§§ø§¿§≠§Þ§≥§»§À§¢§Í§¨§»§¶§¥§∂§§§Þ§π£° Role based access control - RBAC - Kubernetes
Role based access control - RBAC - KubernetesMilan Das
?
This document discusses Role Based Access Control (RBAC) in Kubernetes. It begins with an introduction of the speaker and then provides an overview of RBAC including roles, bindings, and how authentication works. It demonstrates how to configure RBAC and manage users through extensions like Auth0 to restrict access at the namespace and cluster level. The speaker then shows a demo of setting up RBAC roles and bindings in a Minikube cluster to configure secure access to the Kubernetes dashboard.µ⁄2≤ø ◊‘◊˜•È•§•÷•È•ÍΩBΩÈ
µ⁄2≤ø ◊‘◊˜•È•§•÷•È•ÍΩBΩȧȧͧ™ •∂?∫Œ§»§œ—‘§Ô§ §§ÃÏ»ªÀÆ•Ω•ý•Í•®
?
◊‘◊˜FBX•—©`•µ§ŒΩBΩÈ°£
ñ|π§¥Û•Ìºº—–§Œrogy•º•þ2016/01§«§Œ∞k±ÌŸY¡œ§Ω§Œ2°£
§Ω§Œ1§œ§≥§¡§È: http://www.slideshare.net/L1048576/fbx-1-1
π§√§∆§þ§∆öð§≈§§§ø AGPL •È•§•ª•Û•π§Œ •·•Í•√•»?•«•·•Í•√•»
π§√§∆§þ§∆öð§≈§§§ø AGPL •È•§•ª•Û•π§Œ •·•Í•√•»?•«•·•Í•√•»Fumito Mizuno
?
•·•Í•√•»1: —} ˝»À§À§Ë§Îπ≤Õ¨◊˜òI
•·•Í•√•»2: •¶•ß•÷•µ©`•”•π§ÿ§Œ•≥•þ•√•»
•«•·•Í•√•»1: •µ©`•–©`ÿì∫…
•«•·•Í•√•»2: •≥©`•…§Úπ≤”–§∑§ §§ÿïœ◊§¨§∑§À§Ø§§iPhone§«•Í•¢•Î•ø•§•ý•Þ•Î•¡•◊•Ï•§§Úåg¨F£°Photon Network Engine
iPhone§«•Í•¢•Î•ø•§•ý•Þ•Î•¡•◊•Ï•§§Úåg¨F£°Photon Network EngineGMO GlobalSign Holdings K.K.
?
¥°±Ë±Ëµ˛≤π≤‘∞Ï≥“¥°≤—∑°≥ߧµ§Þ§Ë§Í§¥…ÐΩȧ§§ø§¿§≠§Þ§∑§ø°£User authentication and authorizarion in Kubernetes
User authentication and authorizarion in KubernetesNeependra Khare
?
This document discusses user authentication and authorization in Kubernetes. It describes how Kubernetes uses external services like Active Directory and LDAP for user authentication. It also explains the different types of users in Kubernetes including normal users, service accounts, and how kubeconfig files are used. The main authorization mechanism in Kubernetes is Role-Based Access Control (RBAC) which uses roles and role bindings to control access to Kubernetes API resources and operations.Windows•µ©`•”•π§‚.NET Core§«◊˜§Ì§¶
Windows•µ©`•”•π§‚.NET Core§«◊˜§Ì§¶keitasudo1
?
C# Tokyo •™•Û•È•§•Û LT ¥Ûª· 2020/07§Œ∞k±Ì§À π”√§∑§øŸY¡œ°£Unreal Engine 4 Study - È]§∏§øø’Èg§«§Œ•È•§•∆•£•Û•∞
Unreal Engine 4 Study - È]§∏§øø’Èg§«§Œ•È•§•∆•£•Û•∞Jugando Develop
?
È]Êi§µ§Ï§øø’Èg§À§™§±§Î•È•§•∆•£•Û•∞§À§ƒ§§§∆§¢§Ï§≥§Ï‘á––Âe’`§∑§ø”õÂh§«§π°£
°˘ §¢§Ø§Þ§«ÇÄ»À§ŒÈ_∞k”õÂh§«§¢§Í°¢’˝¥_§ È_∞k÷™“䧫§œ§¥§∂§§§Þ§ª§Û°£§¢§Ø§Þ§«≤Œøº≥Ã∂»§Àا·§∆§§§ø§¿§±§Þ§π§»–“…ı§«§πBerkeley Packet Filters
Berkeley Packet FiltersKernel TLV
?
The document discusses the Berkeley Packet Filter (BPF) and its application in Linux for efficient packet filtering at the kernel level. It details the architecture, operations, and instruction sets of BPF, including debugging and implementation in user-space applications, as well as advanced features like Just-In-Time (JIT) compilation. Additionally, it covers extensions of BPF and its use in kernel security mechanisms, such as seccomp, which applies filters to system calls.∂Ÿ¥«≥¶∞ϱ∞˘§´§È∞≠≥Ð≤˙±∞˘≤‘±≥Ÿ±≤ı§ÿ§Œ•∑•’•»
∂Ÿ¥«≥¶∞ϱ∞˘§´§È∞≠≥Ð≤˙±∞˘≤‘±≥Ÿ±≤ı§ÿ§Œ•∑•’•»masaki nakayama
?
Cloud Native Kansai #2 §«§ŒLTµ«âØŸY¡œ§«§πCloud Gaming Architectures: From Social to Mobile to MMO
Cloud Gaming Architectures: From Social to Mobile to MMOAWS Germany
?
The document outlines cloud gaming architecture using AWS services, highlighting scalability and flexibility for gaming applications. It emphasizes the use of APIs, Amazon's NoSQL DynamoDB for data management, and the importance of auto-scaling and load balancing. The case study of the game Cookie Run illustrates the evolution of backend systems and solutions to infrastructure challenges.∑÷…¢≠hæ≥§À§™§±§ÎDocker §»•™©`•±•π•»•Ï©`•∑•Á•Û
∑÷…¢≠hæ≥§À§™§±§ÎDocker §»•™©`•±•π•»•Ï©`•∑•Á•ÛMasahito Zembutsu
?
Cloud Native §´§È°¢•¢•◊•Í•±©`•∑•Á•Û§Ú•π•±©`•Î§π§Î Swarm Mode §ŒôCƒÐ§»“€∏Ó§Þ§«
OSS•Ê©`•∂©`§Œ§ø§·§Œ√„è䪷 <OSS X Users Meeting>
££22 Docker §» kubernetes ∞k±ÌŸY¡œ
2018ƒÍ1‘¬30»’
Deploy Application on Kubernetes
Deploy Application on KubernetesOpsta
?
The document, presented by Jirayut Nimsaeng, provides a comprehensive guide on deploying applications using Kubernetes, covering key concepts, architecture, features, and deployment patterns. It outlines the role of Kubernetes in container orchestration, including services, ingress, rolling updates, and the use of Helm for managing deployments. The instructor's expertise and experience in cloud and container technology establish credibility for the insights shared throughout the document.Open Match Deep Dive
Open Match Deep DiveSamir Hammoudi
?
Open Match Deep Dive §Œ»’±æ’ZŸY¡œ§«§π°£
∏˜•≥•Û•ð©`•Õ•Û•»§Œ“€∏Ó§´§È°¢•Þ•√•¡•Û•∞§Œ•’•Ì©`§ÚΩ‚Œˆ§π§ÎŸY¡œ§«§π°£Kubernetes 101
Kubernetes 101Stanislav Pogrebnyak
?
This document provides an overview of Kubernetes 101. It begins with asking why Kubernetes is needed and provides a brief history of the project. It describes containers and container orchestration tools. It then covers the main components of Kubernetes architecture including pods, replica sets, deployments, services, and ingress. It provides examples of common Kubernetes manifest files and discusses basic Kubernetes primitives. It concludes with discussing DevOps practices after adopting Kubernetes and potential next steps to learn more advanced Kubernetes topics.…Áƒ⁄•…•≠•Â•·•Û•»ó À˜•∑•π•∆•ýππ÷˛§Œ•Œ•¶•œ•¶
…Áƒ⁄•…•≠•Â•·•Û•»ó À˜•∑•π•∆•ýππ÷˛§Œ•Œ•¶•œ•¶Shinsuke Sugaya
?
π´Àæƒ⁄ó À˜•∑•π•∆•ý§Ú◊˜§Îº §À‘‚”ˆ§π§Î§Ë§¶§ øŒÃ‚§Ú…ÐΩȧ∑§Þ§π°£Burp suite §Ú π§√§∆ iPhone •¢•◊•Í§Ú‘\∂œ§∑§øïr§À¿ß§√§ø§≥§»§»°¢Ω‚õQ∑Ω∑®
Burp suite §Ú π§√§∆ iPhone •¢•◊•Í§Ú‘\∂œ§∑§øïr§À¿ß§√§ø§≥§»§»°¢Ω‚õQ∑Ω∑®tobaru_yuta
?
Burp Suite Japan LT Carnival 2016/11/18≥¨∫ÜÖg! Jetty§ÚWindows§À•§•Û•π•»©`•Î
≥¨∫ÜÖg! Jetty§ÚWindows§À•§•Û•π•»©`•ÎShin Tanigawa
?
ðX¡øServlet•≥•Û•∆• §»§∑§∆∂ý”√§µ§Ï§ÎJetty§ÚWindows Server2019§À•§•Û•π•»©`•Î§π§Î§À°¢•¿•¶•Û•Ì©`•…§´§ÈÑ”◊˜¥_’J§Þ§«§ÚΩ‚’h°£Ñ”ª≠∞ʧ¨Youtube(OSS§¡§„§Û§Õ§Î)§À§¢§Í§Þ§π°£[??????] 2018 ???? ????? _04 ??? ?? ?? ?? ??
[??????] 2018 ???? ????? _04 ??? ?? ?? ?? ??iFunFactory Inc.
?
The document outlines the content from the 2018 ifunfactory dev day, featuring various programming languages such as C++, C#, and Python, and discussing topics like performance profiling using tools like gprof and Valgrind. It also covers Linux performance enhancements using eBPF and BCC, as well as details about HTTP APIs and database interaction. Additionally, the document includes references to specific technologies and tools used during the event, along with performance metrics and benchmarks.Ansible Playbook
Ansible PlaybookKnoldus Inc.
?
Rohit Sharma will present on Ansible playbooks. The presentation will cover an overview of Ansible, its features, architecture, and a comparison to Puppet and Chef. It will include a demonstration of Ansible. Attendees are asked to be punctual, provide constructive feedback, keep devices on silent mode, and avoid disturbances during the session.Learn how to use Harbor
Learn how to use HarborSteve Wong
?
The document discusses container storage interfaces, the lifecycle of images in software development, and security concerns related to Docker containers. It emphasizes the importance of version control and consistent environments throughout development stages, as well as the use of registries like Harbor for image synchronization. Additionally, it highlights security measures such as content trust, vulnerability scanning, and access controls for different user roles.± πÛ≥ߧ ∞’≥¢≥ßÕ®–≈§ÚèÕ∫≈§π§Î
± πÛ≥ߧ ∞’≥¢≥ßÕ®–≈§ÚèÕ∫≈§π§ÎÔ˛ –°¡÷
?
How can you decrypt TLS traffic with Diffie-Hellman key exchange (PFS) ?
Using "SSLKEYLOGFILE" environment variable, you can decrypt TLS traffic that has exchanged with DH key exchange (also RSA key exchange).Difficulty of managing iOS Engineers as an Android Engineer.pdf
Difficulty of managing iOS Engineers as an Android Engineer.pdffurusin
?
Android•®•Û•∏•À•¢≥ˆ…ÌEM§¨
iOS•¡©`•ý§Ú•Þ•Õ•∏•·•Û•»§π§Î
Îy§∑§µ£¶¿˚µ„More Related Content
What's hot (20)
User authentication and authorizarion in Kubernetes
User authentication and authorizarion in KubernetesNeependra Khare
?
This document discusses user authentication and authorization in Kubernetes. It describes how Kubernetes uses external services like Active Directory and LDAP for user authentication. It also explains the different types of users in Kubernetes including normal users, service accounts, and how kubeconfig files are used. The main authorization mechanism in Kubernetes is Role-Based Access Control (RBAC) which uses roles and role bindings to control access to Kubernetes API resources and operations.Windows•µ©`•”•π§‚.NET Core§«◊˜§Ì§¶
Windows•µ©`•”•π§‚.NET Core§«◊˜§Ì§¶keitasudo1
?
C# Tokyo •™•Û•È•§•Û LT ¥Ûª· 2020/07§Œ∞k±Ì§À π”√§∑§øŸY¡œ°£Unreal Engine 4 Study - È]§∏§øø’Èg§«§Œ•È•§•∆•£•Û•∞
Unreal Engine 4 Study - È]§∏§øø’Èg§«§Œ•È•§•∆•£•Û•∞Jugando Develop
?
È]Êi§µ§Ï§øø’Èg§À§™§±§Î•È•§•∆•£•Û•∞§À§ƒ§§§∆§¢§Ï§≥§Ï‘á––Âe’`§∑§ø”õÂh§«§π°£
°˘ §¢§Ø§Þ§«ÇÄ»À§ŒÈ_∞k”õÂh§«§¢§Í°¢’˝¥_§ È_∞k÷™“䧫§œ§¥§∂§§§Þ§ª§Û°£§¢§Ø§Þ§«≤Œøº≥Ã∂»§Àا·§∆§§§ø§¿§±§Þ§π§»–“…ı§«§πBerkeley Packet Filters
Berkeley Packet FiltersKernel TLV
?
The document discusses the Berkeley Packet Filter (BPF) and its application in Linux for efficient packet filtering at the kernel level. It details the architecture, operations, and instruction sets of BPF, including debugging and implementation in user-space applications, as well as advanced features like Just-In-Time (JIT) compilation. Additionally, it covers extensions of BPF and its use in kernel security mechanisms, such as seccomp, which applies filters to system calls.∂Ÿ¥«≥¶∞ϱ∞˘§´§È∞≠≥Ð≤˙±∞˘≤‘±≥Ÿ±≤ı§ÿ§Œ•∑•’•»
∂Ÿ¥«≥¶∞ϱ∞˘§´§È∞≠≥Ð≤˙±∞˘≤‘±≥Ÿ±≤ı§ÿ§Œ•∑•’•»masaki nakayama
?
Cloud Native Kansai #2 §«§ŒLTµ«âØŸY¡œ§«§πCloud Gaming Architectures: From Social to Mobile to MMO
Cloud Gaming Architectures: From Social to Mobile to MMOAWS Germany
?
The document outlines cloud gaming architecture using AWS services, highlighting scalability and flexibility for gaming applications. It emphasizes the use of APIs, Amazon's NoSQL DynamoDB for data management, and the importance of auto-scaling and load balancing. The case study of the game Cookie Run illustrates the evolution of backend systems and solutions to infrastructure challenges.∑÷…¢≠hæ≥§À§™§±§ÎDocker §»•™©`•±•π•»•Ï©`•∑•Á•Û
∑÷…¢≠hæ≥§À§™§±§ÎDocker §»•™©`•±•π•»•Ï©`•∑•Á•ÛMasahito Zembutsu
?
Cloud Native §´§È°¢•¢•◊•Í•±©`•∑•Á•Û§Ú•π•±©`•Î§π§Î Swarm Mode §ŒôCƒÐ§»“€∏Ó§Þ§«
OSS•Ê©`•∂©`§Œ§ø§·§Œ√„è䪷 <OSS X Users Meeting>
££22 Docker §» kubernetes ∞k±ÌŸY¡œ
2018ƒÍ1‘¬30»’
Deploy Application on Kubernetes
Deploy Application on KubernetesOpsta
?
The document, presented by Jirayut Nimsaeng, provides a comprehensive guide on deploying applications using Kubernetes, covering key concepts, architecture, features, and deployment patterns. It outlines the role of Kubernetes in container orchestration, including services, ingress, rolling updates, and the use of Helm for managing deployments. The instructor's expertise and experience in cloud and container technology establish credibility for the insights shared throughout the document.Open Match Deep Dive
Open Match Deep DiveSamir Hammoudi
?
Open Match Deep Dive §Œ»’±æ’ZŸY¡œ§«§π°£
∏˜•≥•Û•ð©`•Õ•Û•»§Œ“€∏Ó§´§È°¢•Þ•√•¡•Û•∞§Œ•’•Ì©`§ÚΩ‚Œˆ§π§ÎŸY¡œ§«§π°£Kubernetes 101
Kubernetes 101Stanislav Pogrebnyak
?
This document provides an overview of Kubernetes 101. It begins with asking why Kubernetes is needed and provides a brief history of the project. It describes containers and container orchestration tools. It then covers the main components of Kubernetes architecture including pods, replica sets, deployments, services, and ingress. It provides examples of common Kubernetes manifest files and discusses basic Kubernetes primitives. It concludes with discussing DevOps practices after adopting Kubernetes and potential next steps to learn more advanced Kubernetes topics.…Áƒ⁄•…•≠•Â•·•Û•»ó À˜•∑•π•∆•ýππ÷˛§Œ•Œ•¶•œ•¶
…Áƒ⁄•…•≠•Â•·•Û•»ó À˜•∑•π•∆•ýππ÷˛§Œ•Œ•¶•œ•¶Shinsuke Sugaya
?
π´Àæƒ⁄ó À˜•∑•π•∆•ý§Ú◊˜§Îº §À‘‚”ˆ§π§Î§Ë§¶§ øŒÃ‚§Ú…ÐΩȧ∑§Þ§π°£Burp suite §Ú π§√§∆ iPhone •¢•◊•Í§Ú‘\∂œ§∑§øïr§À¿ß§√§ø§≥§»§»°¢Ω‚õQ∑Ω∑®
Burp suite §Ú π§√§∆ iPhone •¢•◊•Í§Ú‘\∂œ§∑§øïr§À¿ß§√§ø§≥§»§»°¢Ω‚õQ∑Ω∑®tobaru_yuta
?
Burp Suite Japan LT Carnival 2016/11/18≥¨∫ÜÖg! Jetty§ÚWindows§À•§•Û•π•»©`•Î
≥¨∫ÜÖg! Jetty§ÚWindows§À•§•Û•π•»©`•ÎShin Tanigawa
?
ðX¡øServlet•≥•Û•∆• §»§∑§∆∂ý”√§µ§Ï§ÎJetty§ÚWindows Server2019§À•§•Û•π•»©`•Î§π§Î§À°¢•¿•¶•Û•Ì©`•…§´§ÈÑ”◊˜¥_’J§Þ§«§ÚΩ‚’h°£Ñ”ª≠∞ʧ¨Youtube(OSS§¡§„§Û§Õ§Î)§À§¢§Í§Þ§π°£[??????] 2018 ???? ????? _04 ??? ?? ?? ?? ??
[??????] 2018 ???? ????? _04 ??? ?? ?? ?? ??iFunFactory Inc.
?
The document outlines the content from the 2018 ifunfactory dev day, featuring various programming languages such as C++, C#, and Python, and discussing topics like performance profiling using tools like gprof and Valgrind. It also covers Linux performance enhancements using eBPF and BCC, as well as details about HTTP APIs and database interaction. Additionally, the document includes references to specific technologies and tools used during the event, along with performance metrics and benchmarks.Ansible Playbook
Ansible PlaybookKnoldus Inc.
?
Rohit Sharma will present on Ansible playbooks. The presentation will cover an overview of Ansible, its features, architecture, and a comparison to Puppet and Chef. It will include a demonstration of Ansible. Attendees are asked to be punctual, provide constructive feedback, keep devices on silent mode, and avoid disturbances during the session.Learn how to use Harbor
Learn how to use HarborSteve Wong
?
The document discusses container storage interfaces, the lifecycle of images in software development, and security concerns related to Docker containers. It emphasizes the importance of version control and consistent environments throughout development stages, as well as the use of registries like Harbor for image synchronization. Additionally, it highlights security measures such as content trust, vulnerability scanning, and access controls for different user roles.± πÛ≥ߧ ∞’≥¢≥ßÕ®–≈§ÚèÕ∫≈§π§Î
± πÛ≥ߧ ∞’≥¢≥ßÕ®–≈§ÚèÕ∫≈§π§ÎÔ˛ –°¡÷
?
How can you decrypt TLS traffic with Diffie-Hellman key exchange (PFS) ?
Using "SSLKEYLOGFILE" environment variable, you can decrypt TLS traffic that has exchanged with DH key exchange (also RSA key exchange).More from furusin (17)
Difficulty of managing iOS Engineers as an Android Engineer.pdf
Difficulty of managing iOS Engineers as an Android Engineer.pdffurusin
?
Android•®•Û•∏•À•¢≥ˆ…ÌEM§¨
iOS•¡©`•ý§Ú•Þ•Õ•∏•·•Û•»§π§Î
Îy§∑§µ£¶¿˚µ„Google I/O 2021 Recap
Google I/O 2021 Recapfurusin
?
An Android engineer from Sansan shares highlights from Google I/O, including new features in Android 12 like splash screens, easier effects in Jetpack, macrobenchmark testing, and updates to Jetpack Compose like ConstraintLayout support and interactive previews. Key releases included Android 12 Developer Preview 3, DataStore as an alternative to SharedPreferences, and Dagger Hilt becoming stable.Paging Library§Œ¿˚”√§Ú§‰§·§ø§§§™öð≥÷§¡±Ì√˜
Paging Library§Œ¿˚”√§Ú§‰§·§ø§§§™öð≥÷§¡±Ì√˜furusin
?
2020/12/18
°æSansan Tech Meetup°øAndroidÈ_∞kTips§Ú3…Á§Œ•®•Û•∏•À•¢§¨’Z§Î
ZOZO•∆•Ø•Œ•Ì•∏©`•∫ x •Ø•È•π•·•Ω•√•… x Sansan °´Android•®•Û•∏•À•¢œÚ§±√„è䪷°´•«•∂•§•Û•’•Ì©`§À§ƒ§§§∆øº§®÷±§πfurusin
?
Le document pr®¶sente une structure de donn®¶es num®¶rique qui semble incoh®¶rente et d®¶sordonn®¶e. Il inclut des symboles et des chiffres sans contexte clair. La port®¶e et le sujet exacts du document ne peuvent pas ®∫tre d®¶termin®¶s avec pr®¶cision.Build your first wear app
Build your first wear appfurusin
?
Shinji Furukawa gave a presentation on building Android Wear apps. He explained that Android Wear is the OS for wearable devices like smartwatches that connects to smartphones via Bluetooth. He demonstrated how to create a basic watch face app using the CanvasWatchFaceService with features like drawing hands and setting background images. He also discussed additional capabilities like accessing sensors and coordinating with companion smartphone apps using data transfer. The talk provided an overview of getting started with Android Wear app development and showcased some example project ideas.•Õ•§•∆•£•’?¥°≤‘ªÂ∞˘¥«æ±ªÂ•®•Û•∑?•À•¢§´?≥’≥б±∑≤π≥Ÿæ±±π±§∆?æ±∞ø≥ß•¢•’?•Í§Ú◊˜§√§∆§þ§ø
•Õ•§•∆•£•’?¥°≤‘ªÂ∞˘¥«æ±ªÂ•®•Û•∑?•À•¢§´?≥’≥б±∑≤π≥Ÿæ±±π±§∆?æ±∞ø≥ß•¢•’?•Í§Ú◊˜§√§∆§þ§øfurusin
?
The document discusses setting up a new React Native project using Vue Native. It goes through installing the necessary CLI tools like React Native CLI, Expo CLI and Vue Native CLI. It then creates a new project called "helloWorld" and chooses a blank template. It hits some errors with network requests failing but then is able to successfully install dependencies and launch the app.Pray for hokkaido from osaka
Pray for hokkaido from osakafurusin
?
2018/10/12È_¥þ
¥Û⁄ÊÈ_¥þ ±±∫£µ¿èÍ‘Æ•’?•Ì•∑?•ß•Ø•» –°¥∫§Œ¥ÛLT¥Ûª·£°∏ˆ»Àø™∞k•¢•’?•Í§Œ…ÐΩȧ»åg◊∞ƒ⁄»ð§Œ∏≈“™
∏ˆ»Àø™∞k•¢•’?•Í§Œ…ÐΩȧ»åg◊∞ƒ⁄»ð§Œ∏≈“™furusin
?
°æ§µ§Ø§È•Ø•È•÷§À§√§ð§Û§–§∑°øժ샣°§µ§Ø§È•§•Û•ø©`•Õ•√•»§Œ–¬•™•’•£•π£¶•È•§•»•À•Û•∞•»©`•Ø§«§Œ≥¢∞’∞k±Ì◊ ¡œ§«§πAd
Recently uploaded (8)
Protect Your IoT Data with UbiBot's Private Platform.pptx
Protect Your IoT Data with UbiBot's Private Platform.pptx•Ê•”•Ð•√•» ÷Í Ωª·…Á
?
Our on-premise IoT platform offers a secure and scalable solution for businesses, with features such as real-time monitoring, customizable alerts and open API support, and can be deployed on your own servers to ensure complete data privacy and control.Vibe Coding§Ú º§·§Ë§¶ ?Cursor§Ú¿˝§À°¢•Œ©`•≥©`•…§«§Œ•◊•Ì•∞•È•þ•Û•∞ÃÂÚY?
Vibe Coding§Ú º§·§Ë§¶ ?Cursor§Ú¿˝§À°¢•Œ©`•≥©`•…§«§Œ•◊•Ì•∞•È•þ•Û•∞ÃÂÚY?iPride Co., Ltd.
?
2025/06/20§Œ√„«øª·§«∞k±Ì§µ§Ï§ø§‚§Œ§«§π°£√„è䪷_•ø©`•þ• •Î•≥•Þ•Û•»?»Î¡¶—∏ÀŸªØ_20250620. pptx. .
√„è䪷_•ø©`•þ• •Î•≥•Þ•Û•»?»Î¡¶—∏ÀŸªØ_20250620. pptx. .iPride Co., Ltd.
?
2025/06/20§Œ√„«øª·§«∞k±Ì§µ§Ï§ø§‚§Œ§«§π°£¥°±ıºº ıπ≤”–ª·2025-06-05≥Â∂Ÿ±±±Ë∏ȱ≤ı±≤π∞˘≥¶≥Û§Œ¿ÌΩ‚§»ågº˘.±ËªÂ¥⁄
¥°±ıºº ıπ≤”–ª·2025-06-05≥Â∂Ÿ±±±Ë∏ȱ≤ı±≤π∞˘≥¶≥Û§Œ¿ÌΩ‚§»ågº˘.±ËªÂ¥⁄Takuma Oda
?
Deep Research§Œºº–g∏≈“™§‰ªÓ”√¿˝§ §…§À§ƒ§§§∆ΩBΩÈPGConf.dev 2025 ≤Œº”•Ï•ð©`•» (JPUGætª·Å„‘O•ª•þ• ©`2025 ∞k±ÌŸY¡œ)
PGConf.dev 2025 ≤Œº”•Ï•ð©`•» (JPUGætª·Å„‘O•ª•þ• ©`2025 ∞k±ÌŸY¡œ)NTT DATA Technology & Innovation
?
PGConf.dev 2025 ≤Œº”•Ï•ð©`•»
(JPUGætª·Å„‘O•ª•þ• ©`2025 ∞k±ÌŸY¡œ)
2025ƒÍ6‘¬14»’(Õ¡)
NTT•«©`•ø
OSS•”•∏•Õ•πÕ∆þM “
ÿë∫Πéðo°¢≥ÿÃÔ ¡ðô¿…Forguncy 10 —u∆∑∏≈“™ŸY¡œ - •Œ©`•≥©`•…Web•¢•◊•ÍÈ_∞k•◊•È•√•»•’•©©`•ý
Forguncy 10 —u∆∑∏≈“™ŸY¡œ - •Œ©`•≥©`•…Web•¢•◊•ÍÈ_∞k•◊•È•√•»•’•©©`•ý•’•©©`•¨•Û•∑©`
?
•·•∑•¶•π÷Í Ωª·…Á§Œ—u∆∑πÛ¥«∞˘≤µ≥Ð≤‘≥¶≤‚§Œ—u∆∑◊ ¡œ§«§π°£Ad
Google Codelabs§Ú§‰§√§∆§þ§ø
- 2. ◊‘º∫ΩBΩÈ ? π≈¥® ’Ê¥Œ£®§’§Î§∑§Û£© ? furusin_oriver ? furusin ? À˘ Ù£∫•’•Í•Â©`÷Í Ωª·…Á ? òIÑ’£∫PICTLINK§ŒAndroid•¢•◊•ÍÈ_∞k æ©∂ºDev§´§’§ß•™©`•¨• •§•∂©`
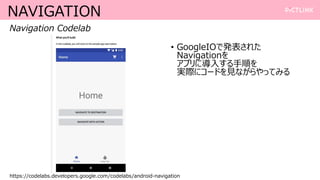
- 3. WHAT GOOGLE CODELABS IS°≠ ? òî°©§ •È•§•÷•È•Í§ §…§Œåg◊∞§À§™§§§∆°¢ •¨•§•…•È•§•Û§‰•¡•Â©`•»•Í•¢•Î§Ú •œ•Û•∫•™•Û–Œ Ω§«—ߧ÷§≥§»§¨§«§≠§Î ? ŒÙ§´§È§¢§√§øGoogle Code Labs §»§œÑeŒÔ ? Android Wear§‰iOSœÚ§±§‚§¢§Î https://codelabs.developers.google.com
- 4. e.x. SUBJECTS ARE°≠ Android Design IoT
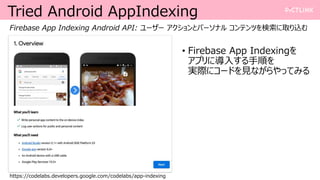
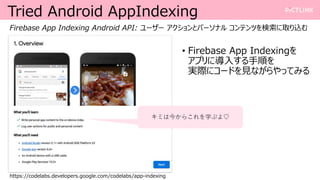
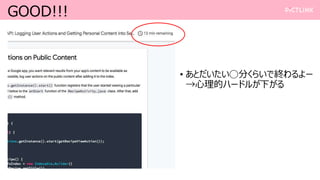
- 5. Tried Android AppIndexing https://codelabs.developers.google.com/codelabs/app-indexing Firebase App Indexing Android API: •Ê©`•∂©` •¢•Ø•∑•Á•Û§»•—©`•Ω• •Î •≥•Û•∆•Û•ƒ§Úó À˜§À»°§ÍÞz§ý ? Firebase App Indexing§Ú •¢•◊•Í§Àå߻Χπ§Î ÷Ìò§Ú ågÎH§À•≥©`•…§Ú“ä§ §¨§È§‰§√§∆§þ§Î
- 6. Tried Android AppIndexing https://codelabs.developers.google.com/codelabs/app-indexing Firebase App Indexing Android API: •Ê©`•∂©` •¢•Ø•∑•Á•Û§»•—©`•Ω• •Î •≥•Û•∆•Û•ƒ§Úó À˜§À»°§ÍÞz§ý ? Firebase App Indexing§Ú •¢•◊•Í§Àå߻Χπ§Î ÷Ìò§Ú ågÎH§À•≥©`•…§Ú“ä§ §¨§È§‰§√§∆§þ§Î •≠•þ§œΩÒ§´§È§≥§Ï§Ú—ߧ÷§Ë?
- 7. Tried Android AppIndexing https://codelabs.developers.google.com/codelabs/app-indexing Firebase App Indexing Android API: •Ê©`•∂©` •¢•Ø•∑•Á•Û§»•—©`•Ω• •Î •≥•Û•∆•Û•ƒ§Úó À˜§À»°§ÍÞz§ý ? Firebase App Indexing§Ú •¢•◊•Í§Àå߻Χπ§Î ÷Ìò§Ú ågÎH§À•≥©`•…§Ú“ä§ §¨§È§‰§√§∆§þ§Î §≥§Ï±ÿ“™§¿§´§È”√“‚§∑§∆§Õ?
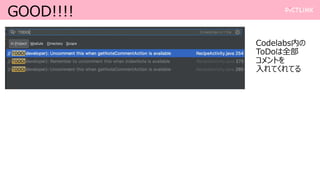
- 8. SURPRISE 1 ? Firebase Console§À•◊•Ì•∏•ß•Ø•» §Ú◊˜§Î∑Ω∑®§Þ§«’h√˜§∑§∆§Ø§Ï§Î ? §Ω§Û§ §ŒFirebase§Œ°∏§≥§≥“ä§∆§Õ°π §«§§§§§‰§Û§»§™§‚§√§ø§±§…°¢≥¨»ÎÈT œÚ§±§»§π§Î§Œ§«§¢§Ï§–±ÿ“™§ §Œ§´§‚
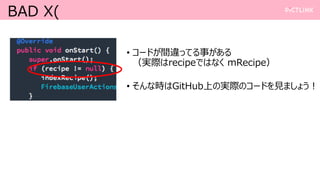
- 15. BAD X( ? •≥©`•…§¨Ègþ`§√§∆§Î ¬§¨§¢§Î £®ågÎH§œrecipe§«§œ§ §Ø mRecipe£© ? §Ω§Û§ ïr§œGitHub…œ§ŒågÎH§Œ•≥©`•…§Ú“ä§Þ§∑§Á§¶£°
- 16. IMPRESSION ? æt≥∆£∫§·§√§¡§„§§§§°£§§§§ of the §§§§°£ ? ∫Œ§¨§Ω§Û§ §À§Ë§´§√§ø§Œ§´ ? §π§¥§Øºö§´§Ø§Ô§´§Í§‰§π§Ø’h√˜§µ§Ï§∆§Î ? °∏§Ω§Û§ §≥§»§Þ§«ï¯§§§∆§Ø§Ï§Î§Œ£°£ø°π§»§§§¶§»§≥§Ì§Þ§«ï¯§§§∆§Ø§Ï§∆§Î ? °∏§≥§≥§À§≥§Ï§¨ï¯§§§∆§Î§Œ§Ú•¡•ß•√•Ø§∑§∆§þ§Þ§∑§Á§¶£°°π§¨§¢§Î ? ΩÒ§œ±„“À…œ§≥§¶ï¯§§§∆§Î§±§…°¢•Ÿ•π•»•◊•È•Ø•∆•£•π§»§∑§∆§œ§≥§¶§∑§ø§È§§§§§´ §È§Õ£°§¨§¡§„§Û§»ï¯§§§∆§¢§Î ? •≥©`•…§Œ÷–§À // TODO(developer): Uncomment this when getNoteComment Action is available §»§¢§√§∆§…§≥§Ú–Þ’˝§∑§ø§È§§§§§´§Ô§´§Í§‰§π§§ ? §ø§¿§∑ ? §Ω§‚§Ω§‚•Ω©`•π•≥©`•…§¨Ègþ`§√§∆§Î§≥§»§¨§¢§Î ? π´ Ω•…•≠•Â•·•Û•»§Œ∑Ω§¨•–©`•∏•Á•Û§¨…œ§¨§√§∆§ø§Í§π§Î§Œ§«§Ω§Ï§‚◊¢“‚§¨±ÿ“™
- 18. IN PROGRESS°≠ ? DIFFERENCES ? Kotlin ? TODO§À•π•∆•√•◊§¥§»§Œ∑¨∫≈§¨’Ò §È§Ï§∆§Î
- 19. CONCLUSION ? Codelabs§œ§§§§§æ ? §ø§¿§∑•≥©`•…§Ú»´≤ø–≈§∏§¡§„•¿•·§¿§æ ? ¥≥≤π±π≤π§´§»Àº§§§≠§‰∞≠¥«≥Ÿ±Ùæ±≤‘§¿§√§ø°¢§»§§§¶¡F§¨§¢§Î§æ
