1 of 23
Downloaded 63 times













Ad
Recommended
????? ?? ????? Unreal? IoT ?? ? ?? ?? ??.pdf
????? ?? ????? Unreal? IoT ?? ? ?? ?? ??.pdfTae wook kang
?
? ??? ???? ???? ???? ?????? ?? ? ?????. 2021?? ????? ?, ?? ??? ? ??? ?? ?? ????, ?? 2? ?? ??? ??? ?? ?????.
? ??? ??? ??? ?? ??? eBook?? ??? ?????. ?? URL? ?? ????, ??? ??? ???????. ? ?? ????? ?????? ???? ?? ?????? ??? ?, IoT? ??? ???? ?? ?? ?? ???? ??? ??? ????. ?? ???? ??? ??? ??? ??? ????, ???? ??? ???????.
???, ??? ??? ??? ??? Unreal 4???(?? ?? - https://unreal-engine.en.uptodown.com/windows). ???? ? ??? ??? ??? ?? ?????? ??? ?? ?????? ?????.
??? ???? ?? ?? ?? ?? ? ??? ?? ??
???? ????
??? Node.js ?? ??
IoT ?? ??? ?? ? ???? ??
???? ? ???? ???
?? ??
? ??? ??? ??? ?? ???? ???? ?? ? ????.
?? - https://github.com/mac999/UnrealSensingCube
?? ?? ?? ?? ??? ??? ??? ??? ??? ??? ??? ?? ???.??? 2022 - Rust ??? ??? ?????
??? 2022 - Rust ??? ??? ?????Chris Ohk
?
INFCON 2022?? ???? "Rust ??? ??? ?????"? ?? ?????. Rust ??? ??? ??? ??? ??? ????, ??? ???? ??? ????? ?? ??? ???????. ?? ???? ??? ???? ???.SonarQube? ???? ????? ?? ??? - SonarQube ??
SonarQube? ???? ????? ?? ??? - SonarQube ??CURVC Corp
?
SonarQube? ???? ????? ?? ??? 1?? ??
???? ?? ???? - ?? ??? ???07 ???? ???? ??? ???(????)
07 ???? ???? ??? ???(????)entrylabs
?
???? ???? ??? ???(????)
?????????? ??? ????? PPT ?????.
??? ??? PPT ??? ???? ??????. ??? ??? ??
??? ??? ??Hakyong Kim
?
????????? 4? ?? ??? ?? ???? ?? ??? ? ?? ?? ??? ?????. ??? ?? ?? ?????? ???? ?? ???? ??? ???? ?? ?? ???? ???? ??? ????. ???? ??? ???? ??? ??? ?? ?????? ?????, ?? ?? ???? ???? ?? ?? ??? ???? ??? ??? ???? ?? ???? ???? ?? ???? ? ???? ?????. Bootloaders (U-Boot)
Bootloaders (U-Boot) Omkar Rane
?
This document discusses bootloaders for embedded systems. It defines a bootloader as the first code executed after a system powers on or resets that is responsible for loading the operating system kernel. The document then describes the tasks of a bootloader like initializing hardware, loading binaries from storage, and providing a shell. It outlines the booting process differences between desktops and embedded systems. Finally, it focuses on the universal bootloader U-Boot, describing its directory structure, configuration, building process, and commands.Embedded Linux on ARM
Embedded Linux on ARMEmertxe Information Technologies Pvt Ltd
?
The document provides an extensive overview of embedded systems focusing on Linux as an embedded operating system. It discusses definitions, categories, components, requirements, challenges, and current trends in embedded systems. Additionally, it explores the toolchain building process, including various components and methodologies for developing embedded Linux applications.Microcontroller part 1
Microcontroller part 1Keroles karam khalil
?
Here are the steps to determine the status of the C, H, and Z flags after adding 0x38 and 0x2F:
1. 0x38 + 0x2F = 0x67
2. The addition does not generate a carry, so the C flag remains unset.
3. The addition results in a half carry, so the H flag is set.
4. The result 0x67 is non-zero, so the Z flag is unset.
Therefore, after adding 0x38 and 0x2F, the status flags would be:
C flag = 0
H flag = 1
Z flag = 0C programming session8
C programming session8Keroles karam khalil
?
Bit-fields allow access to individual bits within registers or bytes. They define the number of bits allocated to each field within a structure. Pointers store the address of other variables in memory and can be used to access or modify these variables indirectly. Pointer arithmetic allows pointers to be incremented or decremented to access sequential memory locations represented by an array.U boot porting guide for SoC
U boot porting guide for SoCMacpaul Lin
?
This document provides an overview of the steps to port the U-boot bootloader to a new SoC using the NDS32 architecture as an example. It describes the directory structure of U-boot and key files related to the architecture, board, configuration, and device drivers. The document outlines where to define SoC hardware addresses, initialize board-specific peripherals, configure options, and implement device drivers to support the new SoC and board.Embedded Operating System - Linux
Embedded Operating System - LinuxEmertxe Information Technologies Pvt Ltd
?
The document provides an extensive overview of embedded operating systems, specifically focusing on Linux. It discusses the evolution of open-source software, the architecture of embedded Linux systems, and the toolchain development process, detailing components such as compilers, libraries, and bootloaders. Additionally, it covers practical aspects of building embedded systems using tools like Buildroot and Yocto, along with examples from specific hardware platforms.Embedded Android : System Development - Part II (Linux device drivers)
Embedded Android : System Development - Part II (Linux device drivers)Emertxe Information Technologies Pvt Ltd
?
The document provides an extensive introduction to Linux device drivers, covering essential skills like C programming, Linux file systems, and kernel source management. It explains character, block, and USB drivers, including driver registration, file operations, memory access, and debugging. Additionally, it outlines the practical aspects of driver development with hands-on examples, kernel interaction, and I/O control APIs.U-Boot presentation 2013
U-Boot presentation 2013Wave Digitech
?
U-Boot is an open source boot loader that initializes hardware and loads operating systems. It supports many CPUs and boards. The boot process involves a pre-relocation phase where U-Boot initializes hardware and copies itself to RAM, and a post-relocation phase where it finishes hardware initialization and loads the kernel or operating system. Debugging can be done before and after relocation by setting breakpoints and examining memory.ARM Trusted Firmwareż╬BL31ż“ģg╠ÕżŪ╩╣ż”ŻĪ
ARM Trusted Firmwareż╬BL31ż“ģg╠ÕżŪ╩╣ż”ŻĪMr. Vengineer
?
The document discusses the ARM Trusted Firmware, specifically focusing on the BL31 component and its usage, including boot management and power management for Zynq UltraScale+ MPSoC. It outlines the structure of the firmware, describes the roles of various firmware layers, and provides instructions on how to configure and use the BL31 standalone. The document also includes links to resources and source code for further exploration of the ARM Trusted Firmware.Introduction to iOS Penetration Testing
Introduction to iOS Penetration TestingOWASP
?
The document provides an introduction to iOS penetration testing. It discusses the speaker's background in mobile and web penetration testing with a focus on iOS. The agenda outlines that the talk will cover introduction to iOS, Objective-C runtime basics, setting up a testing environment, and fundamentals of application testing with a focus on black-box testing. It will not cover jailbreak development, Swift, white-box testing, or webapp pentesting. The document then delves into various aspects of iOS including the security model, application sandboxing, Objective-C, and the iOS runtime. It also discusses tools and techniques for static analysis, runtime manipulation, bypassing protections, and investigating local storage.Embedded Linux on ARM
Embedded Linux on ARMEmertxe Information Technologies Pvt Ltd
?
The document provides an extensive overview of embedded operating systems with a focus on Linux, detailing its history, architecture, and advantages for embedded development. It covers various aspects of embedded Linux, including hardware interfacing, boot processes, toolchains, and libraries relevant for building embedded systems. Additionally, it discusses development environments, cross-compilation tools, and specific methodologies for creating toolchains, along with a deep dive into popular tools like Buildroot and U-Boot used in this domain.I2c drivers
I2c driverspradeep_tewani
?
The document provides a comprehensive overview of the I2C (Inter-Integrated Circuit) protocol, detailing its structure, conditions, and transactions. It covers the Linux I2C subsystem, including device driver registration, initialization, and APIs for accessing I2C devices like EEPROMs. Additionally, it emphasizes effective power management and the decoupling of device drivers from controller drivers for enhanced code reusability across platforms.Embedded C
Embedded CEmertxe Information Technologies Pvt Ltd
?
The document provides an introduction to the C programming language and algorithms. It begins with an overview of C and its history. It then defines key concepts like keywords, data types, qualifiers, loops, storage classes, decision statements, and jumps. Examples of algorithms are provided for common problems like adding two numbers. Pattern printing algorithms are given as homework exercises. The document discusses where C is used and explains what a programming language and algorithms are. It emphasizes the importance of understanding requirements before implementation.OSS SW Basics Lecture 14: Open source hardware
OSS SW Basics Lecture 14: Open source hardwareJeongkyu Shin
?
Lectures on Open-source SW Basics 2016 - 14: Open source in research fieldsMore Related Content
What's hot (20)
Bootloaders (U-Boot)
Bootloaders (U-Boot) Omkar Rane
?
This document discusses bootloaders for embedded systems. It defines a bootloader as the first code executed after a system powers on or resets that is responsible for loading the operating system kernel. The document then describes the tasks of a bootloader like initializing hardware, loading binaries from storage, and providing a shell. It outlines the booting process differences between desktops and embedded systems. Finally, it focuses on the universal bootloader U-Boot, describing its directory structure, configuration, building process, and commands.Embedded Linux on ARM
Embedded Linux on ARMEmertxe Information Technologies Pvt Ltd
?
The document provides an extensive overview of embedded systems focusing on Linux as an embedded operating system. It discusses definitions, categories, components, requirements, challenges, and current trends in embedded systems. Additionally, it explores the toolchain building process, including various components and methodologies for developing embedded Linux applications.Microcontroller part 1
Microcontroller part 1Keroles karam khalil
?
Here are the steps to determine the status of the C, H, and Z flags after adding 0x38 and 0x2F:
1. 0x38 + 0x2F = 0x67
2. The addition does not generate a carry, so the C flag remains unset.
3. The addition results in a half carry, so the H flag is set.
4. The result 0x67 is non-zero, so the Z flag is unset.
Therefore, after adding 0x38 and 0x2F, the status flags would be:
C flag = 0
H flag = 1
Z flag = 0C programming session8
C programming session8Keroles karam khalil
?
Bit-fields allow access to individual bits within registers or bytes. They define the number of bits allocated to each field within a structure. Pointers store the address of other variables in memory and can be used to access or modify these variables indirectly. Pointer arithmetic allows pointers to be incremented or decremented to access sequential memory locations represented by an array.U boot porting guide for SoC
U boot porting guide for SoCMacpaul Lin
?
This document provides an overview of the steps to port the U-boot bootloader to a new SoC using the NDS32 architecture as an example. It describes the directory structure of U-boot and key files related to the architecture, board, configuration, and device drivers. The document outlines where to define SoC hardware addresses, initialize board-specific peripherals, configure options, and implement device drivers to support the new SoC and board.Embedded Operating System - Linux
Embedded Operating System - LinuxEmertxe Information Technologies Pvt Ltd
?
The document provides an extensive overview of embedded operating systems, specifically focusing on Linux. It discusses the evolution of open-source software, the architecture of embedded Linux systems, and the toolchain development process, detailing components such as compilers, libraries, and bootloaders. Additionally, it covers practical aspects of building embedded systems using tools like Buildroot and Yocto, along with examples from specific hardware platforms.Embedded Android : System Development - Part II (Linux device drivers)
Embedded Android : System Development - Part II (Linux device drivers)Emertxe Information Technologies Pvt Ltd
?
The document provides an extensive introduction to Linux device drivers, covering essential skills like C programming, Linux file systems, and kernel source management. It explains character, block, and USB drivers, including driver registration, file operations, memory access, and debugging. Additionally, it outlines the practical aspects of driver development with hands-on examples, kernel interaction, and I/O control APIs.U-Boot presentation 2013
U-Boot presentation 2013Wave Digitech
?
U-Boot is an open source boot loader that initializes hardware and loads operating systems. It supports many CPUs and boards. The boot process involves a pre-relocation phase where U-Boot initializes hardware and copies itself to RAM, and a post-relocation phase where it finishes hardware initialization and loads the kernel or operating system. Debugging can be done before and after relocation by setting breakpoints and examining memory.ARM Trusted Firmwareż╬BL31ż“ģg╠ÕżŪ╩╣ż”ŻĪ
ARM Trusted Firmwareż╬BL31ż“ģg╠ÕżŪ╩╣ż”ŻĪMr. Vengineer
?
The document discusses the ARM Trusted Firmware, specifically focusing on the BL31 component and its usage, including boot management and power management for Zynq UltraScale+ MPSoC. It outlines the structure of the firmware, describes the roles of various firmware layers, and provides instructions on how to configure and use the BL31 standalone. The document also includes links to resources and source code for further exploration of the ARM Trusted Firmware.Introduction to iOS Penetration Testing
Introduction to iOS Penetration TestingOWASP
?
The document provides an introduction to iOS penetration testing. It discusses the speaker's background in mobile and web penetration testing with a focus on iOS. The agenda outlines that the talk will cover introduction to iOS, Objective-C runtime basics, setting up a testing environment, and fundamentals of application testing with a focus on black-box testing. It will not cover jailbreak development, Swift, white-box testing, or webapp pentesting. The document then delves into various aspects of iOS including the security model, application sandboxing, Objective-C, and the iOS runtime. It also discusses tools and techniques for static analysis, runtime manipulation, bypassing protections, and investigating local storage.Embedded Linux on ARM
Embedded Linux on ARMEmertxe Information Technologies Pvt Ltd
?
The document provides an extensive overview of embedded operating systems with a focus on Linux, detailing its history, architecture, and advantages for embedded development. It covers various aspects of embedded Linux, including hardware interfacing, boot processes, toolchains, and libraries relevant for building embedded systems. Additionally, it discusses development environments, cross-compilation tools, and specific methodologies for creating toolchains, along with a deep dive into popular tools like Buildroot and U-Boot used in this domain.I2c drivers
I2c driverspradeep_tewani
?
The document provides a comprehensive overview of the I2C (Inter-Integrated Circuit) protocol, detailing its structure, conditions, and transactions. It covers the Linux I2C subsystem, including device driver registration, initialization, and APIs for accessing I2C devices like EEPROMs. Additionally, it emphasizes effective power management and the decoupling of device drivers from controller drivers for enhanced code reusability across platforms.Embedded C
Embedded CEmertxe Information Technologies Pvt Ltd
?
The document provides an introduction to the C programming language and algorithms. It begins with an overview of C and its history. It then defines key concepts like keywords, data types, qualifiers, loops, storage classes, decision statements, and jumps. Examples of algorithms are provided for common problems like adding two numbers. Pattern printing algorithms are given as homework exercises. The document discusses where C is used and explains what a programming language and algorithms are. It emphasizes the importance of understanding requirements before implementation.Embedded Android : System Development - Part II (Linux device drivers)
Embedded Android : System Development - Part II (Linux device drivers)Emertxe Information Technologies Pvt Ltd
?
Similar to ?? 07 ARM ????? ???? (20)
OSS SW Basics Lecture 14: Open source hardware
OSS SW Basics Lecture 14: Open source hardwareJeongkyu Shin
?
Lectures on Open-source SW Basics 2016 - 14: Open source in research fieldsMCU(nanheekim)
MCU(nanheekim)Nanhee Kim
?
@Powersupply(YeungnamUniv.) @NanheeKim @nh9k
??? ??? ???? ?????!
Please, feel free to contact me, if you have any questions!
github: https://github.com/nh9k
email: kimnanhee97@gmail.com?????? ????1
?????? ????1?? ?
?
Arduino Open Lecture for Beginners. MOT.Eliot
Why people want arduino? It's time to think paradigm shift.[1C6]????????? ???????? ??????????? Node.js?? ?????????? IoT ?????????
[1C6]????????? ???????? ??????????? Node.js?? ?????????? IoT ?????????NAVER D2
?
DEVIEW 2014 [1C6]???? ???? ???? Node.js? ???? IoT ???ICT DIY 2014 Conference - Demo & Exhibition
ICT DIY 2014 Conference - Demo & Exhibition Jonathan Jeon
?
7?9?? ??? ?????? ??? ICT DIY 2014 ????? ???? 26? ????????. ?? ??? ??? ???? ??? ^^
http://onoffmix.com/event/30099??3?? ????? ????????? ?????? 1????? 1????? ????? App ??
??3?? ????? ????????? ?????? 1????? 1????? ????? App ??WooSangHwang
?
??3?? ????? ????????? ?????? 1????? 1????? ????? App ??Ad
?? 07 ARM ????? ????
- 2. ?? Ī± OpenCR ? Ī± ???? Ī± ???? ?? Ī ???? Ī ???? Ī ???? ?? ?? Ī ??? ?? 2
- 3. OpenCR (Open-source Control Module for ROS) Ī± STM32F746ZGT6 216Mhz, 1MB Flash, 320KB SRAM Ī± ???? ?? ? ?? Ī± ???? IDE ???? ?? Ī± ?????/??/UART/CAN ????? Ī± ??? ?? ? ?? ??(12V/5V/3.3V) 3
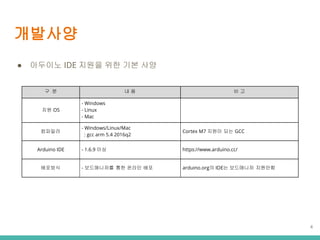
- 4. ???? Ī± ???? IDE ??? ?? ?? ?? ? ? ? ? ? ? ?? OS - Windows - Linux - Mac ???? - Windows/Linux/Mac : gcc arm 5.4 2016q2 Cortex M7 ??? ?? GCC Arduino IDE - 1.6.9 ?? https://www.arduino.cc/ ???? - ?????? ?? ??? ?? arduino.org? IDE? ????? ???? 4
- 5. ???? ? ?? Ī± ???? ?? ??? ?? Ī± I/O ??? 3.3V 5
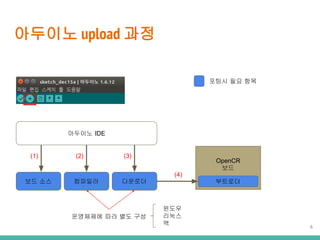
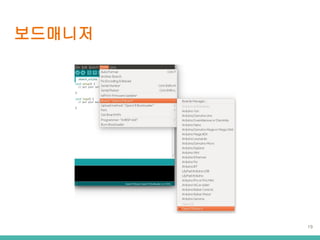
- 6. ???? upload ?? ???? IDE OpenCR ?? ???? (2) ???? (3) ???? (4) ?? ?? (1) ??? ?? ?? ????? ?? ?? ?? 6 ??? ??? ?
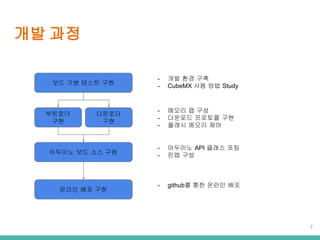
- 7. ?? ?? ?? ?? ??? ?? - ?? ?? ?? - CubeMX ?? ?? Study ???? ?? ???? ?? - ??? ? ?? - ???? ???? ?? - ??? ??? ?? ???? ?? ?? ?? - ???? API ??? ?? - ?? ?? ??? ?? ?? - github? ?? ??? ?? 7
- 8. ???? Ī± ??? ? Ī± ???? ?? 8
- 9. ???? Ī± stm32ld Ī stm32? ?? ????? ??? ???? ??? ???? ? ? ?? ???? Ī ???/???/??? ?? ?? ?? Ī https://github.com/jsnyder/stm32ld Ī± opencr_ld Ī stm32ld? ?? ??? ???? opencr? ???? ????? ??? Ī ???/???/??? ?? ?? Ī÷ ???? QT? ?????? ??? 9
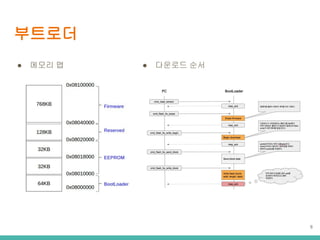
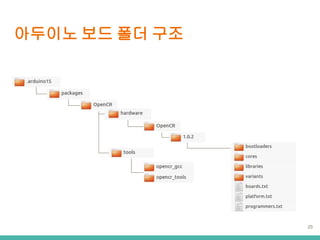
- 10. ???? ?? ?? Ī± ?? ?? ? ? ? ? bootloaders ??? ???? ??? ?? ?? cores ???? API ??? ?? libraries ???? ???? ?? ????? ?? variants cores? ???? ?? ?? ?? ?? boards.txt ??? ?? platform.txt ??? ?? ??? ??, ???? ? ??? programmers.txt ???? ??? ?? 10 Ī± ???? IDE 1.5.3 ?? ????? ?? ??? ?? ????? ??? Ī https://github.com/arduino/Arduino/wiki/Arduino-IDE-1.5-3rd-party-Hardware-specificatio n
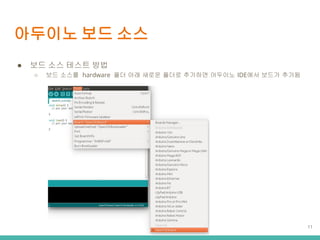
- 11. ???? ?? ?? Ī± ?? ?? ??? ?? Ī ?? ??? hardware ?? ?? ??? ??? ???? ???? IDE?? ??? ??? 11
- 12. ???? ?? Ī± HALMX ???? Ī http://www.stm32duino.com/ ?? STM32CubeMX? ???? ???? ??? ?? Ī https://github.com/rogerclarkmelbourne/Arduino_STM32 Ī ???? F1/F3/F4? ??? Ī± ?? ?? Ī HALMX ????? F7 ???? ???? ??? ?? cores? variants? ??? ???? STM32CubeF7 ?????? ???? ??? 12
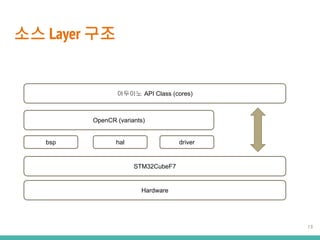
- 13. ?? Layer ?? ???? API Class (cores) STM32CubeF7 OpenCR (variants) bsp hal driver Hardware 13
- 14. ??? ?? Ī± github? json??? ??? ?? ???? ??? Ī ???? IDE 1.6.4 ?? ?? ?? ???? ?? ????? ?? ???? Ī https://github.com/arduino/Arduino/wiki/Arduino-IDE-1.6.x-package_index.json-format-sp ecification Ī± OpenCR json ?? Ī https://github.com/ROBOTIS-GIT/OpenCR/blob/master/arduino/opencr_release/package_ opencr_index.json 14
- 15. json ?? Ī± platforms 15 ???? ?? ?? gcc ???? ????
- 16. json ?? Ī± opencr_gcc 16 Ī± opencr_tools
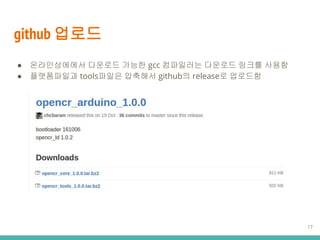
- 17. github ??? Ī± ??????? ???? ??? gcc ????? ???? ??? ??? Ī± ?????? tools??? ???? github? release? ???? 17
- 18. ?? ??? Ī± ???? IDE? ???? ????? URL? json ??? ???? ??? 18
- 19. ????? 19
- 20. ???? ?? ?? ?? 20
- 21. ?? Ī± TFT LCD Ī https://youtu.be/y4if5J_upyY 21
- 22. ?? Ī± ???? ?? ??? ??? ?? ?? ??? ???? ?? ??? ?? ? ?? Ī± OpenCR??? ?? ?? ???? ??? ?? ????? ???? IDE? ?? ?? ?? ??? ?? ??? Ī± ???? ?? ??? ???? ??? OS? ?? ?? ?? Ī± github? ?? ??? ?? ?? Ī± ARM? ???? ??? ?? ?? ?????? ?? ??? ??? 22
- 23. ?? ?? Ī± OpenCR ???? Ī ???? Ī÷ https://github.com/ROBOTIS-GIT/OpenCR/tree/master/arduino/opencr_bootloader Ī ???? Ī÷ https://github.com/ROBOTIS-GIT/OpenCR/tree/master/arduino/opencr_ld Ī ???? ?? ?? Ī÷ https://github.com/ROBOTIS-GIT/OpenCR/tree/master/arduino/opencr_arduino/opencr Ī ??? ?? ?? Ī÷ https://github.com/ROBOTIS-GIT/OpenCR/tree/master/arduino/opencr_release Ī± ???? Ī https://github.com/arduino/Arduino/wiki/Arduino-IDE-1.5-3rd-party-Hardware-specification Ī https://github.com/arduino/Arduino/wiki/Arduino-IDE-1.6.x-package_index.json-format-specification 23