3 summary
Download as PPTX, PDF0 likes245 views
The document discusses database security and authorization. It covers threats to data security like human error and theft. Authentication verifies users' identities while authorization grants access privileges. Encryption encodes data for safe access. The document provides examples of improper authorization in schools and banks. It also includes a quiz on database security and authorization topics.
1 of 7
Download to read offline



Recommended
2 r algebra



2 r algebraMr Patrick NIYISHAKA
Ěý
Relational algebra is a set of operations used to specify retrieval requests in the relational model. The basic operations produce new relations by manipulating existing relations. Operations include unary operations like select and project, and binary operations like union, intersection, difference, cartesian product, and join. A join operation identifies and selects related tuples from two relations based on a join condition.1 db security



1 db securityMr Patrick NIYISHAKA
Ěý
Database security aims to protect data from accidental or intentional harm through threats like human error, software/hardware failures, theft, and improper access. These threats can result in losses of privacy, secrecy, confidentiality, data integrity, and availability. Countermeasures and responses to database failures help increase database security against various threats.2 countermeasures



2 countermeasuresMr Patrick NIYISHAKA
Ěý
This document discusses various countermeasures for database security including authorization, authentication, backups, journalizing, encryption, RAID technology, user-defined procedures, and checkpoints. It also discusses responses to different types of database failures such as aborted transactions, incorrect data, system failures with the database intact, and total database destruction. The preferred and alternative recovery approaches are outlined for each failure scenario.A Locally Finite Maximal Cofinitary Group



A Locally Finite Maximal Cofinitary Groupkasterma
Ěý
This document summarizes the key points from a talk on locally finite maximal cofinite groups. It begins with definitions of cofinite permutations and cofinite and maximal cofinite groups. It then discusses previous results on the complexity of maximal almost disjoint families and maximal cofinite groups. The main result is that under the assumption of Martin's Axiom, there exists a locally finite maximal cofinite group. The proof constructs such a group by carefully adding finite permutations to an increasing union of finite cofinite groups.2 countermeasures



2 countermeasuresMr Patrick NIYISHAKA
Ěý
This document discusses various countermeasures for database security including authorization, authentication, backups, journalizing, encryption, RAID technology, user-defined procedures, and checkpoints. It also discusses responses to different types of database failures such as aborted transactions, incorrect data, system failures with the database intact, and total database destruction. The preferred and alternative recovery approaches are outlined for each failure scenario.1 ddb



1 ddbMr Patrick NIYISHAKA
Ěý
1. The document discusses types of distributed databases and distributed database architecture. It describes distributed databases as collections of shared data distributed over a computer network. Distributed databases can be either homogeneous, with all sites using the same DBMS, or heterogeneous, with different sites using different DBMSs. A distributed DBMS manages the distributed database and aims to make the distribution transparent to users.Summary



SummaryMr Patrick NIYISHAKA
Ěý
This document discusses vectors, force systems, and moments of force. It provides examples of torques, moments, and the cross product as they relate to force vectors. It also uses a skateboard and a hinged rectangular platform suspended by a cable as examples to illustrate moments of force and bending stresses. The document aims to explain vectors with force systems and resultants, and how moments are calculated as both scalar and vector formulations. It concludes with a problem asking the reader to find the moment about each coordinate axis of the force exerted by a cable suspending a hinged platform.3 summary



3 summaryMr Patrick NIYISHAKA
Ěý
This document introduces the topic of distributed database systems. It discusses distributed data independence and transaction atomicity. It provides a real-life example of a travel company using a distributed database with branches around the world. It then gives a quiz to test understanding of distributed database definitions, types, and functionality.Cybersecurity.pptx



Cybersecurity.pptxssuser2209e8
Ěý
This is a presentation of the fundamentals of cybersecurity. It is well planned and presented. It offers a great deal of information to both the novice and the professional.
I strongly advise those who want to learn about Cybersecurity to view this work. It is done with a professional accuracy and with a touch of good learning objectives. test bank MANAGEMENT of INFORMATION SECURITY, Fifth Edition



test bank MANAGEMENT of INFORMATION SECURITY, Fifth Editionhusseinalshomali
Ěý
The document contains a quiz on information security concepts with multiple choice questions and answers. It covers topics like authentication, authorization, threats, attacks, and the CIA triad. Planning, organizing, leading and controlling are discussed as the four principles of management. Problem solving steps and specialized security areas are also listed. The document serves to test the reader's understanding of foundational information security terms and processes.SECO 406100422-ISF-Sample-Exam-en-v1-0.pdf



SECO 406100422-ISF-Sample-Exam-en-v1-0.pdfJohnRicos
Ěý
1) The document provides a sample exam for an Information Security Foundation certification. It includes 40 multiple choice questions to familiarize students with the exam structure and topics.
2) The exam is computer-based, takes 60 minutes to complete, and requires a passing score of 60% to pass. No open books or electronic devices are permitted.
3) The questions cover topics like information security frameworks, data classification, risk management, security principles, threats and vulnerabilities, security policies, incident management, and security controls.Residency ResearchISOL 536 Security Architecture and Design.docx



Residency ResearchISOL 536 Security Architecture and Design.docxbrittneyj3
Ěý
Residency Research
ISOL 536
Security Architecture and Design
Using Resources to Promote
Critical Thinking
Critical thinking is an integral part of any educational program
At UC, we encourage and provide applicable resources for the promotion of critical thinking
In order to properly research and complete course papers, proper resources must be utilized
Critical Thinking helps us to:
Understand the links between ideas.
Determine the importance and relevance of arguments and ideas.
Recognize, build and appraise arguments.
Identify inconsistencies and errors in reasoning.
Approach problems in a consistent and systematic way.
Reflect on the justification of their own assumptions, beliefs and values.
http://www.skillsyouneed.com/learn/critical-thinking.html
Researching Using the Critical Questions
When using research resources, it is imperative to review the six critical questions and implement that data into your writings.
Proper Resources for Research
When asked to completed a research paper in the UC School for Computer and Information Sciences, you must use scholarly, peer-reviewed articles.
A peer-reviewed article is one that has “been evaluated by several researchers or subject specialist in the academic community prior to accepting it for publication” and is “also known as scholarly or refereed.”
Your professor or the UC Librarian team can help you determine whether or not an article is peer-reviewed.
Proper Resources for Research
Examples of sites with peer-reviewed resources
UC Library Site
EBSCOhost
JSTOR
Google Scholar
Examples of sites with unacceptable resources
PC Magazine
Cisco
Ars Technica
Reddit
Proper Format is Important
All papers written for courses within the School for Computer and Information Sciences must follow the American Psychological Association (APA) writing style.
University Resources
The UC Library provides a myriad of online resources to assist students with proper research
Resources referring to Information Security can be found inside the UC Library site
www.ucumberlands.edu/library
Groups
Group 1
Group Topic: Meltdown
[emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected]
Group 2
Group Topic: Spectre
[emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected]
Group 3
Group Topic: ZombieLoad
[emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected]
Group 4
Group Topic: RIDL
[emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected]
Group 5
Group Topic: Fallout
[emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected]
Research Topic
Security researchers have discovered major vulnerabilities with the design of Intel chips
The vulnerabilities stem from several issues and their immediate remediations create severe loss of performance
Each vulnerability is similar but different
Res.Top Network Security Interview Questions That You Should Know.pptx



Top Network Security Interview Questions That You Should Know.pptxInfosectrain3
Ěý
To ensure optimum digital security and compliance, organizations of all sizes and scales should have proper strategies and mitigation processes in place to secure their networks. In this article, we will discuss the most frequently asked questions in a network security interview.CISSP Exam-Certified Information Systems Security Professional 



CISSP Exam-Certified Information Systems Security Professional Isabella789
Ěý
If you need help preparing for CISSP Exam-Certified Information Systems Security Professional (CISSP) visit@ https://www.troytec.com/CISSP-exams.html EM - Security and Privacy Incidents - Module 4 Powerpoint Presentation



EM - Security and Privacy Incidents - Module 4 Powerpoint Presentationtrevor501353
Ěý
EM - Security and Privacy Incidents - Module 4 Powerpoint Presentationdokumen_tips_computer_security_by_william_stallings_ch_1_mcq.docx



dokumen_tips_computer_security_by_william_stallings_ch_1_mcq.docxams1ams11
Ěý
The document contains questions and answers about computer security concepts from Chapter 1 of the textbook "Computer Security: Principles and Practice, 2nd Edition". It addresses key topics like the CIA triad of confidentiality, integrity and availability, security threats, vulnerabilities, attacks, and countermeasures. It also discusses security policies, models, and the importance of contingency planning and risk assessment.Cissp cbk final_exam-answers_v5.5



Cissp cbk final_exam-answers_v5.5madunix
Ěý
This document contains a CISSP CBK review exam with 55 multiple choice questions covering various topics in cybersecurity. Some of the questions test knowledge of risk management, access controls, cryptography, security operations and incident response. The exam is assessing understanding of fundamental cybersecurity concepts as defined in the Common Body of Knowledge for the CISSP certification.Data base security & integrity



Data base security & integrityPooja Dixit
Ěý
DATABASE SECURITY, REQUIREMENTS, GOALS, DATA SECURITY LIFECYCLE, AUTHORIZATION, AUTHENTICATION, BACKUP & RECOVERY, INTEGRITY, ENCRYPTION & DECRYPTIONCis 333 Education Redefined - snaptutorial.com



Cis 333 Education Redefined - snaptutorial.comDavisMurphyC75
Ěý
This document provides an overview of the entire CIS 333 course from SNAP Tutorial, including discussions, labs, assignments, and exams. The course covers topics such as providing security over data, risk management, cryptography, malware, and eliminating threats with a layered security approach. Labs involve tasks like performing reconnaissance and probing with common tools, enabling Windows Active Directory controls, and packet capture analysis. Assignments require identifying potential attacks and vulnerabilities, and developing risk response and recovery plans. The document lists the materials included for each week of the course.IT 549 Scenario Assignment Module Six Guidelines and Rubric .docx



IT 549 Scenario Assignment Module Six Guidelines and Rubric .docxvrickens
Ěý
IT 549 Scenario Assignment Module Six Guidelines and Rubric
For the Module Six assignment, students will be placed into the role of an IT consultant whose task is to evaluate an existin g organization’s security protocols.
Once the protocols have been analyzed, students will synthesize this knowledge to provide insight into the likelihood of certain threats occurring. The skills
acquired from this exercise will prove to be beneficial during the final stages of designing the information assurance plan.
Prompt: In your role as a highly paid consultant, you are given a list of potential threats to and vulnerabilities of the current communication security protocols of
an organization. You are asked to provide quantitative data to measure the likelihood that any of these threats will actually occur for the information assets of the
client. Conduct research and describe resources you found that might provide insight into measuring the likelihood that some of the threats would actually occur.
In the explanation, include whether you see a trend in resources that might indicate a specific industry is particularly involved in gathering this kind of data.
Additionally, evaluate which communication security protocols are more effective and provide an explanation.
Guidelines for Submission: Your responses for the prompt must be submitted as two to three paragraphs and as a Microsoft Word document with double
spacing, 12-point Times New Roman font, one-inch margins, and at least three sources cited in APA format.
Critical Elements Exemplary (100%) Proficient (85%) Needs Improvement (55%) Not Evident (0%) Value
Quantitative Data Meets “Proficient” criteria and
the quantitative data is
substantiated with research
based evidence
Response provides quantitative
data to measure the likelihood
that any of these threats will
actually occur
Response attempts to provide
quantitative data; however, the
data requires more substantial
evidence to prove the likeliness
of the threats occurring or not
Response does not provide any
quantitative data
20
Insight Meets “Proficient” criteria and
explanation uses content based
vocabulary and research based
evidence to support the answer
Response explains and provides
insight into measuring the
likelihood that some of the
threats would actually occur
Response provides insight into
measuring the likelihood that
some of the threats would
actually occur but does not
explain the likelihood of the
threats
Response does not provide
insight into measuring the
likelihood that some of the
threats would actually occur
20
Trend in Resources Meets “Proficient” criteria and
the trend that is identified is
substantiated with research
based evidence
Response specifies a trend in
resources that might indicate a
specific industry is particularly
involved in gathering this kind
of data
Response specifies a trend in
resources that might indicate a
spec ...Top_10_Interview_Questions_That_You_Should_Know_as_an_Information.pptx



Top_10_Interview_Questions_That_You_Should_Know_as_an_Information.pptxinfosec train
Ěý
Cyber security practices involve preventing malicious attacks on computers, servers, mobile devices, electronic systems, networks, and data. It is also called information technology security or electronic information security.
https://www.infosectrain.com/courses/ceh-v11-certification-training/
Security in network computing



Security in network computingManoj VNV
Ěý
This document discusses network security and defines key concepts. It explains that security aims to protect confidentiality, integrity, and availability of information. The main pillars of security are the CIA triangle of confidentiality, integrity, and availability. Vulnerabilities are weaknesses that can be exploited by threats to carry out attacks, which aim to intercept, interrupt, modify or fabricate information. Common attacks include eavesdropping, cryptanalysis, password pilfering through guessing, social engineering, dictionary attacks and password sniffing. Controls work to reduce vulnerabilities and block threats to prevent harm.Module1_Intro to Security1111111_Final.ppt



Module1_Intro to Security1111111_Final.pptVijaykumarMaloth2
Ěý
Module1_Intro to Security1111111_Final.pptModule1_Intro to Security1111111_Final.pptModule1_Intro to Security1111111_Final.pptModule1_Intro to Security1111111_Final.pptModule1_Intro to Security1111111_Final.pptModule1_Intro to Security1111111_Final.ppt2 ddb architecture



2 ddb architectureMr Patrick NIYISHAKA
Ěý
This document discusses distributed database architecture. It describes the advantages as improved processing power through distributed processing across multiple machines, removal of single point of failure, and easier expandability. The disadvantages include increased complexity, costs, security challenges, and difficulties with integrity control and standardization. Different architectures are shared-nothing, shared-disk, and shared-memory. Distributed databases are well-suited for applications involving multiple sites like manufacturing, military systems, and airline reservations.4 summary



4 summaryMr Patrick NIYISHAKA
Ěý
This document covers transaction processing concepts including:
- Typical OLTP environments and how to recover from failures
- The ACID properties of transactions including atomicity, consistency, isolation, and durability
- Transaction states like active, aborted, and committed
- Transactions as concurrency units and how they execute concurrently while maintaining serializability
- Quizzes to test understanding of transaction processing, ACID properties, transaction states, and ensuring consistency through synchronizationMore Related Content
Similar to 3 summary (20)
Cybersecurity.pptx



Cybersecurity.pptxssuser2209e8
Ěý
This is a presentation of the fundamentals of cybersecurity. It is well planned and presented. It offers a great deal of information to both the novice and the professional.
I strongly advise those who want to learn about Cybersecurity to view this work. It is done with a professional accuracy and with a touch of good learning objectives. test bank MANAGEMENT of INFORMATION SECURITY, Fifth Edition



test bank MANAGEMENT of INFORMATION SECURITY, Fifth Editionhusseinalshomali
Ěý
The document contains a quiz on information security concepts with multiple choice questions and answers. It covers topics like authentication, authorization, threats, attacks, and the CIA triad. Planning, organizing, leading and controlling are discussed as the four principles of management. Problem solving steps and specialized security areas are also listed. The document serves to test the reader's understanding of foundational information security terms and processes.SECO 406100422-ISF-Sample-Exam-en-v1-0.pdf



SECO 406100422-ISF-Sample-Exam-en-v1-0.pdfJohnRicos
Ěý
1) The document provides a sample exam for an Information Security Foundation certification. It includes 40 multiple choice questions to familiarize students with the exam structure and topics.
2) The exam is computer-based, takes 60 minutes to complete, and requires a passing score of 60% to pass. No open books or electronic devices are permitted.
3) The questions cover topics like information security frameworks, data classification, risk management, security principles, threats and vulnerabilities, security policies, incident management, and security controls.Residency ResearchISOL 536 Security Architecture and Design.docx



Residency ResearchISOL 536 Security Architecture and Design.docxbrittneyj3
Ěý
Residency Research
ISOL 536
Security Architecture and Design
Using Resources to Promote
Critical Thinking
Critical thinking is an integral part of any educational program
At UC, we encourage and provide applicable resources for the promotion of critical thinking
In order to properly research and complete course papers, proper resources must be utilized
Critical Thinking helps us to:
Understand the links between ideas.
Determine the importance and relevance of arguments and ideas.
Recognize, build and appraise arguments.
Identify inconsistencies and errors in reasoning.
Approach problems in a consistent and systematic way.
Reflect on the justification of their own assumptions, beliefs and values.
http://www.skillsyouneed.com/learn/critical-thinking.html
Researching Using the Critical Questions
When using research resources, it is imperative to review the six critical questions and implement that data into your writings.
Proper Resources for Research
When asked to completed a research paper in the UC School for Computer and Information Sciences, you must use scholarly, peer-reviewed articles.
A peer-reviewed article is one that has “been evaluated by several researchers or subject specialist in the academic community prior to accepting it for publication” and is “also known as scholarly or refereed.”
Your professor or the UC Librarian team can help you determine whether or not an article is peer-reviewed.
Proper Resources for Research
Examples of sites with peer-reviewed resources
UC Library Site
EBSCOhost
JSTOR
Google Scholar
Examples of sites with unacceptable resources
PC Magazine
Cisco
Ars Technica
Reddit
Proper Format is Important
All papers written for courses within the School for Computer and Information Sciences must follow the American Psychological Association (APA) writing style.
University Resources
The UC Library provides a myriad of online resources to assist students with proper research
Resources referring to Information Security can be found inside the UC Library site
www.ucumberlands.edu/library
Groups
Group 1
Group Topic: Meltdown
[emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected]
Group 2
Group Topic: Spectre
[emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected]
Group 3
Group Topic: ZombieLoad
[emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected]
Group 4
Group Topic: RIDL
[emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected]
Group 5
Group Topic: Fallout
[emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected][emailĚýprotected]
Research Topic
Security researchers have discovered major vulnerabilities with the design of Intel chips
The vulnerabilities stem from several issues and their immediate remediations create severe loss of performance
Each vulnerability is similar but different
Res.Top Network Security Interview Questions That You Should Know.pptx



Top Network Security Interview Questions That You Should Know.pptxInfosectrain3
Ěý
To ensure optimum digital security and compliance, organizations of all sizes and scales should have proper strategies and mitigation processes in place to secure their networks. In this article, we will discuss the most frequently asked questions in a network security interview.CISSP Exam-Certified Information Systems Security Professional 



CISSP Exam-Certified Information Systems Security Professional Isabella789
Ěý
If you need help preparing for CISSP Exam-Certified Information Systems Security Professional (CISSP) visit@ https://www.troytec.com/CISSP-exams.html EM - Security and Privacy Incidents - Module 4 Powerpoint Presentation



EM - Security and Privacy Incidents - Module 4 Powerpoint Presentationtrevor501353
Ěý
EM - Security and Privacy Incidents - Module 4 Powerpoint Presentationdokumen_tips_computer_security_by_william_stallings_ch_1_mcq.docx



dokumen_tips_computer_security_by_william_stallings_ch_1_mcq.docxams1ams11
Ěý
The document contains questions and answers about computer security concepts from Chapter 1 of the textbook "Computer Security: Principles and Practice, 2nd Edition". It addresses key topics like the CIA triad of confidentiality, integrity and availability, security threats, vulnerabilities, attacks, and countermeasures. It also discusses security policies, models, and the importance of contingency planning and risk assessment.Cissp cbk final_exam-answers_v5.5



Cissp cbk final_exam-answers_v5.5madunix
Ěý
This document contains a CISSP CBK review exam with 55 multiple choice questions covering various topics in cybersecurity. Some of the questions test knowledge of risk management, access controls, cryptography, security operations and incident response. The exam is assessing understanding of fundamental cybersecurity concepts as defined in the Common Body of Knowledge for the CISSP certification.Data base security & integrity



Data base security & integrityPooja Dixit
Ěý
DATABASE SECURITY, REQUIREMENTS, GOALS, DATA SECURITY LIFECYCLE, AUTHORIZATION, AUTHENTICATION, BACKUP & RECOVERY, INTEGRITY, ENCRYPTION & DECRYPTIONCis 333 Education Redefined - snaptutorial.com



Cis 333 Education Redefined - snaptutorial.comDavisMurphyC75
Ěý
This document provides an overview of the entire CIS 333 course from SNAP Tutorial, including discussions, labs, assignments, and exams. The course covers topics such as providing security over data, risk management, cryptography, malware, and eliminating threats with a layered security approach. Labs involve tasks like performing reconnaissance and probing with common tools, enabling Windows Active Directory controls, and packet capture analysis. Assignments require identifying potential attacks and vulnerabilities, and developing risk response and recovery plans. The document lists the materials included for each week of the course.IT 549 Scenario Assignment Module Six Guidelines and Rubric .docx



IT 549 Scenario Assignment Module Six Guidelines and Rubric .docxvrickens
Ěý
IT 549 Scenario Assignment Module Six Guidelines and Rubric
For the Module Six assignment, students will be placed into the role of an IT consultant whose task is to evaluate an existin g organization’s security protocols.
Once the protocols have been analyzed, students will synthesize this knowledge to provide insight into the likelihood of certain threats occurring. The skills
acquired from this exercise will prove to be beneficial during the final stages of designing the information assurance plan.
Prompt: In your role as a highly paid consultant, you are given a list of potential threats to and vulnerabilities of the current communication security protocols of
an organization. You are asked to provide quantitative data to measure the likelihood that any of these threats will actually occur for the information assets of the
client. Conduct research and describe resources you found that might provide insight into measuring the likelihood that some of the threats would actually occur.
In the explanation, include whether you see a trend in resources that might indicate a specific industry is particularly involved in gathering this kind of data.
Additionally, evaluate which communication security protocols are more effective and provide an explanation.
Guidelines for Submission: Your responses for the prompt must be submitted as two to three paragraphs and as a Microsoft Word document with double
spacing, 12-point Times New Roman font, one-inch margins, and at least three sources cited in APA format.
Critical Elements Exemplary (100%) Proficient (85%) Needs Improvement (55%) Not Evident (0%) Value
Quantitative Data Meets “Proficient” criteria and
the quantitative data is
substantiated with research
based evidence
Response provides quantitative
data to measure the likelihood
that any of these threats will
actually occur
Response attempts to provide
quantitative data; however, the
data requires more substantial
evidence to prove the likeliness
of the threats occurring or not
Response does not provide any
quantitative data
20
Insight Meets “Proficient” criteria and
explanation uses content based
vocabulary and research based
evidence to support the answer
Response explains and provides
insight into measuring the
likelihood that some of the
threats would actually occur
Response provides insight into
measuring the likelihood that
some of the threats would
actually occur but does not
explain the likelihood of the
threats
Response does not provide
insight into measuring the
likelihood that some of the
threats would actually occur
20
Trend in Resources Meets “Proficient” criteria and
the trend that is identified is
substantiated with research
based evidence
Response specifies a trend in
resources that might indicate a
specific industry is particularly
involved in gathering this kind
of data
Response specifies a trend in
resources that might indicate a
spec ...Top_10_Interview_Questions_That_You_Should_Know_as_an_Information.pptx



Top_10_Interview_Questions_That_You_Should_Know_as_an_Information.pptxinfosec train
Ěý
Cyber security practices involve preventing malicious attacks on computers, servers, mobile devices, electronic systems, networks, and data. It is also called information technology security or electronic information security.
https://www.infosectrain.com/courses/ceh-v11-certification-training/
Security in network computing



Security in network computingManoj VNV
Ěý
This document discusses network security and defines key concepts. It explains that security aims to protect confidentiality, integrity, and availability of information. The main pillars of security are the CIA triangle of confidentiality, integrity, and availability. Vulnerabilities are weaknesses that can be exploited by threats to carry out attacks, which aim to intercept, interrupt, modify or fabricate information. Common attacks include eavesdropping, cryptanalysis, password pilfering through guessing, social engineering, dictionary attacks and password sniffing. Controls work to reduce vulnerabilities and block threats to prevent harm.Module1_Intro to Security1111111_Final.ppt



Module1_Intro to Security1111111_Final.pptVijaykumarMaloth2
Ěý
Module1_Intro to Security1111111_Final.pptModule1_Intro to Security1111111_Final.pptModule1_Intro to Security1111111_Final.pptModule1_Intro to Security1111111_Final.pptModule1_Intro to Security1111111_Final.pptModule1_Intro to Security1111111_Final.pptMore from Mr Patrick NIYISHAKA (20)
2 ddb architecture



2 ddb architectureMr Patrick NIYISHAKA
Ěý
This document discusses distributed database architecture. It describes the advantages as improved processing power through distributed processing across multiple machines, removal of single point of failure, and easier expandability. The disadvantages include increased complexity, costs, security challenges, and difficulties with integrity control and standardization. Different architectures are shared-nothing, shared-disk, and shared-memory. Distributed databases are well-suited for applications involving multiple sites like manufacturing, military systems, and airline reservations.4 summary



4 summaryMr Patrick NIYISHAKA
Ěý
This document covers transaction processing concepts including:
- Typical OLTP environments and how to recover from failures
- The ACID properties of transactions including atomicity, consistency, isolation, and durability
- Transaction states like active, aborted, and committed
- Transactions as concurrency units and how they execute concurrently while maintaining serializability
- Quizzes to test understanding of transaction processing, ACID properties, transaction states, and ensuring consistency through synchronization3 summary



3 summaryMr Patrick NIYISHAKA
Ěý
This document discusses concurrency control techniques for managing concurrent execution of transactions. It provides an example of how concurrency control is needed when multiple passengers try to purchase the last remaining airline ticket. The document then covers topics like transaction serialization, pessimistic and optimistic concurrency control, locking techniques, and two-phase locking. It concludes with sample multiple choice questions about problems with concurrent transactions, methods for serialization, locking data items, and definitions of deadlock and concurrency control.2 con control



2 con controlMr Patrick NIYISHAKA
Ěý
This document discusses concurrency control techniques for databases, including pessimistic and optimistic concurrency control. It describes locking techniques used for synchronization, including binary locks, certify locks, and two-phase locking to ensure serializability. It also discusses problems that can occur with locking such as deadlocks and starvation.1 con exe



1 con exeMr Patrick NIYISHAKA
Ěý
This document discusses concurrency control and methods to ensure serializability when transactions execute concurrently in a database. It begins by describing three problems that can occur with concurrent transaction execution: lost updates, unrepeatable reads, and dirty reads. It then explains two methods for achieving serializability: multi-version concurrency control and timestamp ordering. Timestamp ordering assigns timestamps to transactions and data items and uses the timestamps to determine when transactions can read and write data items to prevent conflicts. The document also briefly mentions using concurrency control protocols that employ locking to serialize transaction access.1 basic concepts



1 basic conceptsMr Patrick NIYISHAKA
Ěý
This document discusses transaction processing in online transaction processing (OLTP) environments. It covers typical OLTP environments like airline, banking, and trading systems. It also covers topics like transactions being atomic units of execution that must have ACID (atomicity, consistency, isolation, durability) properties and can be in different states during processing. Transactions are sequences of database operations that must generate a consistent database when applied to a consistent one.2 recovery



2 recoveryMr Patrick NIYISHAKA
Ěý
The document discusses database recovery from failures. It explains that a DBMS uses techniques like logging transactions, periodic backups, and mirroring databases to restore the system to a consistent state if a failure occurs. There are two types of recovery - from transaction failures, where the DBMS undoes uncommitted transactions, and from catastrophic failures like disk or system crashes, where the entire database must be restored from a backup and the log is used to replay committed transactions. Proper recovery is needed to ensure transactions are fully committed or have no effect, and that the database remains in a consistent state.3 transaction



3 transactionMr Patrick NIYISHAKA
Ěý
The document discusses the ACID properties that transactions should possess:
1. Atomicity - Transactions are atomic units that are fully completed or not completed at all.
2. Consistency - Transactions preserve consistency by ensuring the database only transitions between valid states.
3. Isolation - The execution of one transaction is isolated and not interfered with by other concurrent transactions.
4. Durability - Committed transaction changes persist in the database and survive failures through logging and recovery.3 summary



3 summaryMr Patrick NIYISHAKA
Ěý
The document discusses query processing and optimization techniques. It provides an example of querying a database to find the name of the last member to borrow a book with the title "Zeus". There are several ways to structure the query, but some methods are more optimized than others. Query processing involves translating SQL queries into relational algebra operations, generating execution plans, and executing the queries. Query optimization examines multiple query plans to identify the most efficient plan to retrieve the required data.1 query processing



1 query processingMr Patrick NIYISHAKA
Ěý
The document discusses the process of query processing, which includes translating SQL queries into relational algebra, generating an evaluation plan, and executing the query. It provides examples of translating a SQL query into relational algebra expressions and generating an annotated evaluation plan specifying the detailed strategy for evaluating the query.1 query processing



1 query processingMr Patrick NIYISHAKA
Ěý
The document discusses the process of query processing, which includes translating SQL queries into relational algebra, generating an evaluation plan, and executing the query. It provides examples of translating a SQL query into relational algebra expressions and generating an annotated evaluation plan specifying the detailed strategy for evaluating the query.2 optimization



2 optimizationMr Patrick NIYISHAKA
Ěý
The document discusses query optimization techniques used by database systems. It describes how a database catalog is used to estimate query execution costs. Alternative execution plans are enumerated using heuristic rules and the lowest cost plan is selected. Examples are provided of applying translation rules to optimize a query tree by pushing down select and project operations, avoiding Cartesian products, and reordering joins and selections. Cost estimation considers factors like I/O, memory usage, and computation to select a suboptimal but efficient execution plan.2 collision



2 collisionMr Patrick NIYISHAKA
Ěý
This document discusses collisions, center of mass, and impulse and momentum. It provides information on inelastic 2D collisions and notes that analyzing collisions using impulse and momentum is useful when solving for collisions between two bodies. It also defines center of mass as the point where all the mass of an object or system can be considered concentrated.4 summary



4 summaryMr Patrick NIYISHAKA
Ěý
This document provides an overview of week 1 topics for a database systems course, including database concepts and architecture. It discusses database models, schemas, languages, and interfaces. It also provides a real-world example of a DVD rental database, showing sample schemas for DVDs, customers, directors, and actors. Finally, it includes a quiz on basic database terms like data, records, fields, and DBMS.3 summary



3 summaryMr Patrick NIYISHAKA
Ěý
This document discusses database design concepts and normalization theory. It covers topics such as functional dependency, the first, second, and third normal forms, benefits of normalization like minimizing data redundancy, and concepts of denormalization. It includes a quiz to test understanding with questions about the goal of normalization, benefits of normalization, characteristics of third normal form, database anomalies, and the definition of denormalization.2 normalization



2 normalizationMr Patrick NIYISHAKA
Ěý
This document discusses normalization, which is the process of organizing data in a database to minimize redundancy and dependency. It defines normalization through various normal forms, including first normal form (1NF), second normal form (2NF), and third normal form (3NF). These normal forms help reduce data anomalies like insertion, deletion, and update anomalies that can occur when data is redundant or dependent on other data. The benefits of normalization include using less storage space, allowing for quicker updates, and reducing data inconsistencies.1 fn dependency



1 fn dependencyMr Patrick NIYISHAKA
Ěý
This document discusses functional dependencies in database relations. It defines functional dependency as a relationship where the value of one attribute (the dependent attribute) is determined by the value of another attribute or set of attributes (the determinant attributes). It provides examples of functional dependencies, such as child being functionally dependent on mother, but not vice versa. The document also includes an example employee database relation showing the primary key of empno and functional dependencies between attributes.4 summary



4 summaryMr Patrick NIYISHAKA
Ěý
This document provides an introduction to SQL and covers topics like SQL data types, data definition language (DDL), data manipulation language (DML), and data control language (DCL). It includes examples of creating tables for DVDs, customers, directors, actors, and relationship tables. It concludes with a quiz on SQL fundamentals.2 dml



2 dmlMr Patrick NIYISHAKA
Ěý
This document discusses Data Manipulation Language (DML) which provides basic operations to query and manipulate data in a database. It describes common DML commands like SELECT that allow users to retrieve data from one or more tables based on specific conditions. Examples are provided showing how to use the SELECT statement to query a student database table to list records by name, house code, district code, or other fields based on parameters like class, gender, fee remission status. DML allows users to efficiently access and manage data stored in a relational database.1 ddl



1 ddlMr Patrick NIYISHAKA
Ěý
This document discusses SQL and its data types, data definition language (DDL), data manipulation language (DML), and data control language (DCL). It defines SQL as a standardized language for querying and updating databases and lists common SQL data types like string, numeric, and date/time. It describes DDL commands for creating, altering, and dropping database tables as well as adding, modifying, and removing columns.Recently uploaded (20)
Kaun TALHA quiz Prelims - El Dorado 2025



Kaun TALHA quiz Prelims - El Dorado 2025Conquiztadors- the Quiz Society of Sri Venkateswara College
Ěý
Prelims of Kaun TALHA : a Travel, Architecture, Lifestyle, Heritage and Activism quiz, organized by Conquiztadors, the Quiz society of Sri Venkateswara College under their annual quizzing fest El Dorado 2025. Adventure Activities Final By H R Gohil Sir



Adventure Activities Final By H R Gohil SirGUJARATCOMMERCECOLLE
Ěý
Adventure Activities Final By H R Gohil SirCBSE Arabic Grammar - Class 10 ppt.pptx



CBSE Arabic Grammar - Class 10 ppt.pptxsuhail849886
Ěý
cbse arabic grammar
grade 10 cbse arabic grammar
cbse class 10 arabic grammar
arabic marathon cbse arabic 10
nominal sentences
Eng7-Q4-Lesson 1 Part 1 Understanding Discipline-Specific Words, Voice, and T...



Eng7-Q4-Lesson 1 Part 1 Understanding Discipline-Specific Words, Voice, and T...sandynavergas1
Ěý
Understanding Discipline-Specific Words, Voice, and Technical TermsDigital Tools with AI for e-Content Development.pptx



Digital Tools with AI for e-Content Development.pptxDr. Sarita Anand
Ěý
This ppt is useful for not only for B.Ed., M.Ed., M.A. (Education) or any other PG level students or Ph.D. scholars but also for the school, college and university teachers who are interested to prepare an e-content with AI for their students and others.How to attach file using upload button Odoo 18



How to attach file using upload button Odoo 18Celine George
Ěý
In this slide, we’ll discuss on how to attach file using upload button Odoo 18. Odoo features a dedicated model, 'ir.attachments,' designed for storing attachments submitted by end users. We can see the process of utilizing the 'ir.attachments' model to enable file uploads through web forms in this slide.How to Setup WhatsApp in Odoo 17 - Odoo şÝşÝߣs



How to Setup WhatsApp in Odoo 17 - Odoo şÝşÝߣsCeline George
Ěý
Integrate WhatsApp into Odoo using the WhatsApp Business API or third-party modules to enhance communication. This integration enables automated messaging and customer interaction management within Odoo 17.Useful environment methods in Odoo 18 - Odoo şÝşÝߣs



Useful environment methods in Odoo 18 - Odoo şÝşÝߣsCeline George
Ěý
In this slide we’ll discuss on the useful environment methods in Odoo 18. In Odoo 18, environment methods play a crucial role in simplifying model interactions and enhancing data processing within the ORM framework.How to Configure Flexible Working Schedule in Odoo 18 Employee



How to Configure Flexible Working Schedule in Odoo 18 EmployeeCeline George
Ěý
In this slide, we’ll discuss on how to configure flexible working schedule in Odoo 18 Employee module. In Odoo 18, the Employee module offers powerful tools to configure and manage flexible working schedules tailored to your organization's needs.A PPT Presentation on The Princess and the God: A tale of ancient India by A...



A PPT Presentation on The Princess and the God: A tale of ancient India by A...Beena E S
Ěý
A PPT Presentation on The Princess and the God: A tale of ancient India by Aaron ShepardTLE 7 - 3rd Topic - Hand Tools, Power Tools, Instruments, and Equipment Used ...



TLE 7 - 3rd Topic - Hand Tools, Power Tools, Instruments, and Equipment Used ...RizaBedayo
Ěý
Hand Tools, Power Tools, and Equipment in Industrial ArtsPrinciple and Practices of Animal Breeding || Boby Basnet



Principle and Practices of Animal Breeding || Boby BasnetBoby Basnet
Ěý
Principle and Practices of Animal Breeding Full Note
|| Assistant Professor Boby Basnet ||IAAS || AFU || PU || FUKaun TALHA quiz Prelims - El Dorado 2025



Kaun TALHA quiz Prelims - El Dorado 2025Conquiztadors- the Quiz Society of Sri Venkateswara College
Ěý
3 summary
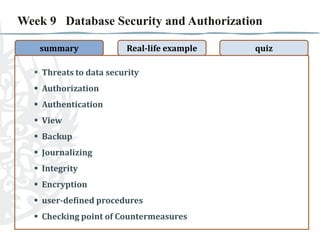
- 1. Week 9 Database Security and Authorization summary Real-life example  Threats to data security  Authorization  Authentication  View  Backup  Journalizing  Integrity  Encryption  user-defined procedures  Checking point of Countermeasures quiz
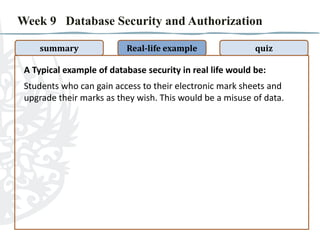
- 2. Week 9 Database Security and Authorization summary Real-life example quiz A Typical example of database security in real life would be: Students who can gain access to their electronic mark sheets and upgrade their marks as they wish. This would be a misuse of data.
- 3. Week 9 Database Security and Authorization summary Real-life example quiz A Typical example of database authorization in real life would be: A bank cashier who has the right to see the amounts of customer accounts and then divulgate them to robbers who, themselves can blackmail customers or threaten them and demand them ransoms. This is a badly granted right on the important data.
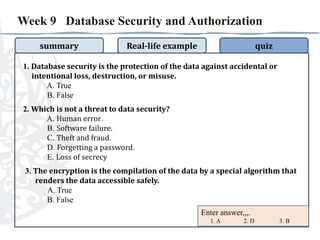
- 4. Week 9 Database Security and Authorization summary Real-life example quiz 1. Database security is the protection of the data against accidental or intentional loss, destruction, or misuse. A. True B. False 2. Which is not a threat to data security? A. Human error. B. Software failure. C. Theft and fraud. D. Forgetting a password. E. Loss of secrecy 3. The encryption is the compilation of the data by a special algorithm that renders the data accessible safely. A. True B. False Enter answer,,,. 1. 2. 3.
- 5. Week 9 Database Security and Authorization summary Real-life example quiz 1. Database security is the protection of the data against accidental or intentional loss, destruction, or misuse. A. True B. False 2. Which is not a threat to data security? A. Human error. B. Software failure. C. Theft and fraud. D. Forgetting a password. E. Loss of secrecy 3. The encryption is the compilation of the data by a special algorithm that renders the data accessible safely. A. True B. False Enter answer,,,. 1. A 2. D 3. B
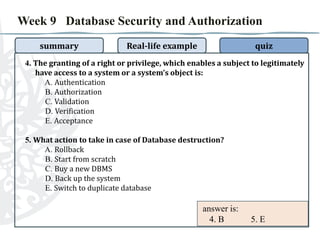
- 6. Week 9 Database Security and Authorization summary Real-life example quiz 4. The granting of a right or privilege, which enables a subject to legitimately have access to a system or a system’s object is: A. Authentication B. Authorization C. Validation D. Verification E. Acceptance 5. What action to take in case of Database destruction? A. Rollback B. Start from scratch C. Buy a new DBMS D. Back up the system E. Switch to duplicate database answer is: 4. 5.
- 7. Week 9 Database Security and Authorization summary Real-life example quiz 4. The granting of a right or privilege, which enables a subject to legitimately have access to a system or a system’s object is: A. Authentication B. Authorization C. Validation D. Verification E. Acceptance 5. What action to take in case of Database destruction? A. Rollback B. Start from scratch C. Buy a new DBMS D. Back up the system E. Switch to duplicate database answer is: 4. B 5. E













