Use Jupyter notebook guide in 5 minutes
0 likes193 views
Tutorial of Jupyter notebook in a fast way. Introduce what is notebook and simple shortcuts - command mode, edit mode
1 of 12
Download to read offline











Recommended
Shortcut Keys for Windows 10 - Customize Word Document



Shortcut Keys for Windows 10 - Customize Word DocumentDavid J Rosenthal
?
Shortcut Keys for Windows 10
This guide lists shortcut keys that you can use from the desktop in Windows 10.
Shortcut keys-for-windows-10-www.penajam



Shortcut keys-for-windows-10-www.penajamInspektorat
?
This document lists shortcut keys that can be used from the desktop in Windows 10. Some examples include:
- Windows key to open the Start menu
- +1, +2 etc. to switch between applications in the taskbar
- +D to toggle between minimizing all windows and returning to the previous state
- +I to open the Settings app
- +TAB to open Task View to see all open windows and switch between themHow to install windows 8 using usb pen drive



How to install windows 8 using usb pen driveparag dhok
?
Computer System Requirement to install windows 8 on your computer
1 GB of Ram
16 GB Or More Free Hard disk Space
DVD - RW
Working Keyboard & Mouse
P4 Processor
Graphics card: Microsoft DirectX 9 graphics device with WDDM driver
Step 1 :: Insert Windows 8 0r windows 8.1 DVD In DVD -RW...
Step 2 :: Go to CMOS Setup | Bios Configuration By Continuous Pressing DEL Key From Keyboard Some common Keys are F1,F2,F10,F12
42 windows-10-hotkeys



42 windows-10-hotkeysHeba Toukhi
?
This document provides a summary of shortcut keys that can be used in Windows 10 from the desktop. It lists shortcuts for launching the Start menu, switching between apps and desktops, using Cortana, taking screenshots, managing windows, and more. The shortcuts are concisely presented and categorized by function for easy reference.Watercolor Painting Effect



Watercolor Painting Effectshalace09
?
The document provides steps to apply a watercolor painting effect to an image in a photo editing program:
1. Duplicate the background layer 3 times to create 4 layers total. Turn off the top 2 layers, leaving only the bottom layer visible.
2. Apply the Cutout filter to the bottom layer, then change the blend mode to Luminosity.
3. Turn on the layer above and apply the Dry Brush filter, setting the brush size to 10 and texture to 3, changing the blend mode to Screen.
4. Turn on the top layer and apply the Median filter with a radius of 12, changing the blend mode to Soft Light to complete the watercolor effect.Second life training_viewer2



Second life training_viewer2liam edwards
?
This quick start guide introduces the interface, controls, and basic actions in Second Life through explanations of menus, function buttons, keyboard commands, avatar interactions, communications, inventory, camera controls and more. It provides an overview of how to navigate, communicate, and engage with the virtual world.Wordnotes



WordnotesGul Sanga
?
This document provides tips and shortcuts for using Microsoft Word. It discusses customizing toolbars and menus, adding items to toolbars, cursor movement shortcuts, special characters, styles, and adding a shortcut to your directory for easy access to files. The document offers advice on using styles to make global changes and provides examples of modifying common styles like Normal, Heading 1, and Heading 2.Alpha Tech



Alpha Techthinkict
?
The document provides an outline for an Alpha Tech Program trainer kit that teaches basic computer skills. The program aims to remove fear of computers and teach basic usage skills like operating a computer, connecting to the internet, creating documents and sending emails. The outline includes 4 modules that cover computer basics, common terminology, types of computers and operating systems, and teaches how to use Windows and manage files and folders.Jupyter Notebook_CheatSheet.pdf



Jupyter Notebook_CheatSheet.pdfhesam ahmadian
?
Jupyter Notebook allows users to create and share documents that contain code, equations, visualizations and explanatory text. It supports interactive coding in over 40 programming languages. Notebooks contain cells that can contain code, equations, visualizations or explanatory text. Kernels run the code cells and communicate results. Common kernels include IPython for Python and IRkernel for R.Exceljet excel shortcuts_160623



Exceljet excel shortcuts_160623Rishav Singh
?
This document provides keyboard shortcuts for Microsoft Excel on Windows and Mac. It includes shortcuts for navigation, selection, formatting, formulas and other tasks. It also lists video tutorials and over 300 formula examples available on the ExcelJet website. Users can click shortcut titles to access more detailed online explanations. A printed quick reference card with all shortcuts is also available.Productivity Tips For Altium Designer



Productivity Tips For Altium DesignerSchattke
?
The document provides 17 productivity tips for using Altium Designer, an electronic design automation software. It describes tips such as how to walk through nets to check a design, manage layer sets, use net name prefixes to set up classes, find unconnected nets, place drill drawings, close out test point errors, and more. The tips are meant to improve efficiency and help hide some less known features of the software. It concludes by providing additional resources for more Altium Designer tips and tutorials.Lecture 2: C# Programming for VR application in Unity



Lecture 2: C# Programming for VR application in UnityKobkrit Viriyayudhakorn
?
This document provides an overview and instructions for a C# programming lecture on creating a gold miner game in Unity. It discusses troubleshooting resources, writing code in Unity using MonoDevelop IDE, code structure, printing text to the console, attaching scripts to game objects, variables, conditional statements, planning the game, pseudocode, reading user input, updating location, using classes and objects, methods, and key terminology. The goal is to program a game where the player controls a gold miner to navigate a world and find a gold pit by pressing arrow keys to move while the distance to the pit is displayed, with the objective of finding it in as few turns as possible.Quick start guide english



Quick start guide englishGopal Krishna Potanaboyina
?
The quick start guide provides instructions for installing the tablet driver and connecting the tablet to a computer. It explains the system requirements, how to install the driver software by inserting the driver CD, and how to connect the tablet to the computer via USB cable or dongle. It also provides an overview of the tablet hardware components and their functions.OpenOffice.org Walc



OpenOffice.org WalcCzarli Evangelista
?
This document provides an introduction to Calc, the spreadsheet component of OpenOffice. It discusses how to get started with Calc, manage files, work with sheets, cells, rows and columns. It also covers entering and formatting data, using formulas and functions, sorting and filtering data. The document contains exercises for students to practice these skills.Altium productivity



Altium productivityAlex Borisov
?
This document provides 17 productivity tips for Altium Designer, including how to walk through nets to check a design, manage layer sets, use net name prefixes to set up classes, find unconnected nets, delete long traces quickly, and move selections by X and Y coordinates. It also recommends additional resources for learning more Altium Designer tips and tricks.Vi editor



Vi editorEr Mittinpreet Singh
?
Vi editor is a popular text editor in Unix systems. It has three modes of operation - command mode, insert mode, and ex command mode. Command mode allows navigation and editing using keyboard commands while insert mode allows inserting new text. Ex command mode allows issuing commands from the command line. Vi is more advanced than earlier line editors like ed allowing screen-based editing. However, it can be difficult to learn due to its modal nature and lack of error messages.Productivity Enhencement with Visual Studio



Productivity Enhencement with Visual StudioAhasan Habib
?
This document outlines various productivity features in Visual Studio, including keyboard shortcuts, code analyzers, code snippets, debugging tools, and extensions like Web Essentials and Resharper. It discusses features for formatting, refactoring, navigating, and inspecting code. The conclusion compares Visual Studio and Resharper features and notes considerations for using extensions like hardware requirements and compatibility issues.fontlab tutorial en inglés.pdf



fontlab tutorial en inglés.pdfAnaliaAlcain
?
Fontlab Ltd.
http://www.fontlab.com
Basics of
FontLab Studio 5
Ted Harrison
OpenType / TrueType fonts exist in two flavors: Windows TrueType (.ttf) and OpenType PostScript (.otf). They can use either TrueType or Type 1 glyphs and work across Windows, Mac and Unix platforms.
The font table in FontLab Studio displays information about glyphs and allows editing characters. Cells are color coded to indicate encoding status. Context menus provide glyph editing and encoding options.
This document provides an overview of basic FontLab Studio interface and tools for editing glyphs, contours, nodes and performing transformations. Guidelines, layers and hints can be used to aid inЕвгений Обрезков "Behind the terminal"



Евгений Обрезков "Behind the terminal"Fwdays
?
Я расскажу о том, как можно использовать терминал не по назначению.
Какие подводные камни мне встречались, когда я разрабатывал canvas для терминала. Какие алгоритмы я использовал, чтобы оптимизировать скорость отрисовки элементов.
И конечно же покажу все на реальных примерах и отвечу на вопросы.MANUAL-BIOS 2



MANUAL-BIOS 2JAVIER PABLO TOCTO
?
The BIOS Setup Utility allows the user to configure settings that control how the computer initializes and operates. Key pages in the utility include Standard CMOS Features to set date/time and hardware, Advanced BIOS Features for boot priorities and security options, and Advanced Chipset Features for timing parameters. The utility must be used carefully to avoid incorrect settings that could cause system errors.3.8.a how to - vim course book



3.8.a how to - vim course bookAcácio Oliveira
?
The document discusses VIM basics, including its three main modes: command mode, insert mode, and visual mode. It provides examples of commands for navigating and editing text in VIM. Navigation commands cover moving the cursor within a line and between lines/pages. Editing commands demonstrate how to delete, change, copy/paste text using commands optionally followed by a number or text object for precision. Visual block mode and text objects in visual mode are also summarized as ways to efficiently edit selected text across multiple lines.101 3.8.1 vim course book



101 3.8.1 vim course bookAcácio Oliveira
?
The document discusses VIM basics, including its three main modes: command mode, insert mode, and visual mode. It provides examples of commands for navigating and editing text in VIM. Navigation commands cover moving the cursor within a line and between lines/pages. Editing commands demonstrate how to delete, change, copy/paste text using commands optionally followed by a number or text object for precision editing. Visual block mode and text objects in visual mode are also summarized as advanced editing techniques in VIM.13457272.ppt



13457272.pptaptechaligarh
?
Swing is a Java GUI widget toolkit that improves upon the older AWT toolkit. It includes common GUI components like JFrame, JPanel, and JLabel. JFrame represents a window, JPanel is used to group and layout components, and JLabel displays text. These components have constructors and methods to create, configure, add, and listen to GUI elements. Layout managers automatically position components and should be used for most applications.What is Texture.pdf



What is Texture.pdfDong Heon Cho
?
The document discusses texture analysis in computer vision. It begins by asking what texture is and whether objects themselves can be considered textures. It then outlines several statistical and Fourier approaches to texture analysis, citing specific papers on texture energy measures, texton theory, and using textons to model materials. Deep convolutional neural networks are also discussed as being able to recognize and describe texture through learned filter banks. The concept of texels is introduced as low-level features that make up texture at different scales from edges to shapes. The document hypothesizes that CNNs are sensitive to texture because texture repeats across images while object shapes do not, and that CNNs act as texture mappers rather than template matchers. It also questions whether primary visual cortexBADGE



BADGEDong Heon Cho
?
This document discusses active learning techniques called Deep Badge Active Learning. It proposes using gradient embeddings to represent samples and k-means++ initialization for sample selection. Specifically, it uses the gradient embedding for feature representation, then performs k-means++ initialization to select samples by finding those with the maximum 2-norm and those farthest from existing samples, adding them to the set iteratively. This aims to select a diverse set of samples, similar to how binary search works. The technique could improve over entropy-based and core-set selection approaches for active learning with convolutional neural networks.Neural Radiance Field



Neural Radiance FieldDong Heon Cho
?
Neural Radiance Fields (NeRF) represent scenes as neural networks that map 5D input (3D position and 2D viewing direction) to a 4D output (RGB color and opacity). NeRF uses an MLP that is trained to predict volumetric density and color for a scene from many camera views. Key aspects of NeRF include using positional encodings as inputs to help model view-dependent effects, and training to optimize for integrated color and density values along camera rays. NeRF has enabled novel applications beyond novel view synthesis, including pose estimation, dense descriptors, and self-supervised segmentation.2020 > Self supervised learning



2020 > Self supervised learningDong Heon Cho
?
Self Supervised Learning after 2020
SimCLR, MOCO, BYOL and etc
Start from SimCLRAll about that pooling



All about that poolingDong Heon Cho
?
The document discusses various pooling operations used in image processing and convolutional neural networks (CNNs). It provides an overview of common pooling methods like max pooling, average pooling, and spatial pyramid pooling. It also discusses more advanced and trainable pooling techniques like stochastic pooling, mixed/gated pooling, fractional pooling, local importance pooling, and global feature guided local pooling. The document analyzes the tradeoffs of different pooling methods and how they can balance preserving details versus achieving invariance to changes in position or lighting. It references several influential papers that analyzed properties of pooling operations.Background elimination review



Background elimination reviewDong Heon Cho
?
This document discusses background elimination techniques which involve three main steps: object detection to select the target, segmentation to isolate the target from the background, and refinement to improve the quality of the segmented mask. It provides an overview of approaches that have been used for each step, including early methods based on SVM and more recent deep learning-based techniques like Mask R-CNN that integrate detection and segmentation. The document also notes that segmentation is challenging without object detection cues and discusses types of segmentation as well as refinement methods that use transformations, dimension reduction, and graph-based modeling.More Related Content
Similar to Use Jupyter notebook guide in 5 minutes (15)
Jupyter Notebook_CheatSheet.pdf



Jupyter Notebook_CheatSheet.pdfhesam ahmadian
?
Jupyter Notebook allows users to create and share documents that contain code, equations, visualizations and explanatory text. It supports interactive coding in over 40 programming languages. Notebooks contain cells that can contain code, equations, visualizations or explanatory text. Kernels run the code cells and communicate results. Common kernels include IPython for Python and IRkernel for R.Exceljet excel shortcuts_160623



Exceljet excel shortcuts_160623Rishav Singh
?
This document provides keyboard shortcuts for Microsoft Excel on Windows and Mac. It includes shortcuts for navigation, selection, formatting, formulas and other tasks. It also lists video tutorials and over 300 formula examples available on the ExcelJet website. Users can click shortcut titles to access more detailed online explanations. A printed quick reference card with all shortcuts is also available.Productivity Tips For Altium Designer



Productivity Tips For Altium DesignerSchattke
?
The document provides 17 productivity tips for using Altium Designer, an electronic design automation software. It describes tips such as how to walk through nets to check a design, manage layer sets, use net name prefixes to set up classes, find unconnected nets, place drill drawings, close out test point errors, and more. The tips are meant to improve efficiency and help hide some less known features of the software. It concludes by providing additional resources for more Altium Designer tips and tutorials.Lecture 2: C# Programming for VR application in Unity



Lecture 2: C# Programming for VR application in UnityKobkrit Viriyayudhakorn
?
This document provides an overview and instructions for a C# programming lecture on creating a gold miner game in Unity. It discusses troubleshooting resources, writing code in Unity using MonoDevelop IDE, code structure, printing text to the console, attaching scripts to game objects, variables, conditional statements, planning the game, pseudocode, reading user input, updating location, using classes and objects, methods, and key terminology. The goal is to program a game where the player controls a gold miner to navigate a world and find a gold pit by pressing arrow keys to move while the distance to the pit is displayed, with the objective of finding it in as few turns as possible.Quick start guide english



Quick start guide englishGopal Krishna Potanaboyina
?
The quick start guide provides instructions for installing the tablet driver and connecting the tablet to a computer. It explains the system requirements, how to install the driver software by inserting the driver CD, and how to connect the tablet to the computer via USB cable or dongle. It also provides an overview of the tablet hardware components and their functions.OpenOffice.org Walc



OpenOffice.org WalcCzarli Evangelista
?
This document provides an introduction to Calc, the spreadsheet component of OpenOffice. It discusses how to get started with Calc, manage files, work with sheets, cells, rows and columns. It also covers entering and formatting data, using formulas and functions, sorting and filtering data. The document contains exercises for students to practice these skills.Altium productivity



Altium productivityAlex Borisov
?
This document provides 17 productivity tips for Altium Designer, including how to walk through nets to check a design, manage layer sets, use net name prefixes to set up classes, find unconnected nets, delete long traces quickly, and move selections by X and Y coordinates. It also recommends additional resources for learning more Altium Designer tips and tricks.Vi editor



Vi editorEr Mittinpreet Singh
?
Vi editor is a popular text editor in Unix systems. It has three modes of operation - command mode, insert mode, and ex command mode. Command mode allows navigation and editing using keyboard commands while insert mode allows inserting new text. Ex command mode allows issuing commands from the command line. Vi is more advanced than earlier line editors like ed allowing screen-based editing. However, it can be difficult to learn due to its modal nature and lack of error messages.Productivity Enhencement with Visual Studio



Productivity Enhencement with Visual StudioAhasan Habib
?
This document outlines various productivity features in Visual Studio, including keyboard shortcuts, code analyzers, code snippets, debugging tools, and extensions like Web Essentials and Resharper. It discusses features for formatting, refactoring, navigating, and inspecting code. The conclusion compares Visual Studio and Resharper features and notes considerations for using extensions like hardware requirements and compatibility issues.fontlab tutorial en inglés.pdf



fontlab tutorial en inglés.pdfAnaliaAlcain
?
Fontlab Ltd.
http://www.fontlab.com
Basics of
FontLab Studio 5
Ted Harrison
OpenType / TrueType fonts exist in two flavors: Windows TrueType (.ttf) and OpenType PostScript (.otf). They can use either TrueType or Type 1 glyphs and work across Windows, Mac and Unix platforms.
The font table in FontLab Studio displays information about glyphs and allows editing characters. Cells are color coded to indicate encoding status. Context menus provide glyph editing and encoding options.
This document provides an overview of basic FontLab Studio interface and tools for editing glyphs, contours, nodes and performing transformations. Guidelines, layers and hints can be used to aid inЕвгений Обрезков "Behind the terminal"



Евгений Обрезков "Behind the terminal"Fwdays
?
Я расскажу о том, как можно использовать терминал не по назначению.
Какие подводные камни мне встречались, когда я разрабатывал canvas для терминала. Какие алгоритмы я использовал, чтобы оптимизировать скорость отрисовки элементов.
И конечно же покажу все на реальных примерах и отвечу на вопросы.MANUAL-BIOS 2



MANUAL-BIOS 2JAVIER PABLO TOCTO
?
The BIOS Setup Utility allows the user to configure settings that control how the computer initializes and operates. Key pages in the utility include Standard CMOS Features to set date/time and hardware, Advanced BIOS Features for boot priorities and security options, and Advanced Chipset Features for timing parameters. The utility must be used carefully to avoid incorrect settings that could cause system errors.3.8.a how to - vim course book



3.8.a how to - vim course bookAcácio Oliveira
?
The document discusses VIM basics, including its three main modes: command mode, insert mode, and visual mode. It provides examples of commands for navigating and editing text in VIM. Navigation commands cover moving the cursor within a line and between lines/pages. Editing commands demonstrate how to delete, change, copy/paste text using commands optionally followed by a number or text object for precision. Visual block mode and text objects in visual mode are also summarized as ways to efficiently edit selected text across multiple lines.101 3.8.1 vim course book



101 3.8.1 vim course bookAcácio Oliveira
?
The document discusses VIM basics, including its three main modes: command mode, insert mode, and visual mode. It provides examples of commands for navigating and editing text in VIM. Navigation commands cover moving the cursor within a line and between lines/pages. Editing commands demonstrate how to delete, change, copy/paste text using commands optionally followed by a number or text object for precision editing. Visual block mode and text objects in visual mode are also summarized as advanced editing techniques in VIM.13457272.ppt



13457272.pptaptechaligarh
?
Swing is a Java GUI widget toolkit that improves upon the older AWT toolkit. It includes common GUI components like JFrame, JPanel, and JLabel. JFrame represents a window, JPanel is used to group and layout components, and JLabel displays text. These components have constructors and methods to create, configure, add, and listen to GUI elements. Layout managers automatically position components and should be used for most applications.More from Dong Heon Cho (20)
What is Texture.pdf



What is Texture.pdfDong Heon Cho
?
The document discusses texture analysis in computer vision. It begins by asking what texture is and whether objects themselves can be considered textures. It then outlines several statistical and Fourier approaches to texture analysis, citing specific papers on texture energy measures, texton theory, and using textons to model materials. Deep convolutional neural networks are also discussed as being able to recognize and describe texture through learned filter banks. The concept of texels is introduced as low-level features that make up texture at different scales from edges to shapes. The document hypothesizes that CNNs are sensitive to texture because texture repeats across images while object shapes do not, and that CNNs act as texture mappers rather than template matchers. It also questions whether primary visual cortexBADGE



BADGEDong Heon Cho
?
This document discusses active learning techniques called Deep Badge Active Learning. It proposes using gradient embeddings to represent samples and k-means++ initialization for sample selection. Specifically, it uses the gradient embedding for feature representation, then performs k-means++ initialization to select samples by finding those with the maximum 2-norm and those farthest from existing samples, adding them to the set iteratively. This aims to select a diverse set of samples, similar to how binary search works. The technique could improve over entropy-based and core-set selection approaches for active learning with convolutional neural networks.Neural Radiance Field



Neural Radiance FieldDong Heon Cho
?
Neural Radiance Fields (NeRF) represent scenes as neural networks that map 5D input (3D position and 2D viewing direction) to a 4D output (RGB color and opacity). NeRF uses an MLP that is trained to predict volumetric density and color for a scene from many camera views. Key aspects of NeRF include using positional encodings as inputs to help model view-dependent effects, and training to optimize for integrated color and density values along camera rays. NeRF has enabled novel applications beyond novel view synthesis, including pose estimation, dense descriptors, and self-supervised segmentation.2020 > Self supervised learning



2020 > Self supervised learningDong Heon Cho
?
Self Supervised Learning after 2020
SimCLR, MOCO, BYOL and etc
Start from SimCLRAll about that pooling



All about that poolingDong Heon Cho
?
The document discusses various pooling operations used in image processing and convolutional neural networks (CNNs). It provides an overview of common pooling methods like max pooling, average pooling, and spatial pyramid pooling. It also discusses more advanced and trainable pooling techniques like stochastic pooling, mixed/gated pooling, fractional pooling, local importance pooling, and global feature guided local pooling. The document analyzes the tradeoffs of different pooling methods and how they can balance preserving details versus achieving invariance to changes in position or lighting. It references several influential papers that analyzed properties of pooling operations.Background elimination review



Background elimination reviewDong Heon Cho
?
This document discusses background elimination techniques which involve three main steps: object detection to select the target, segmentation to isolate the target from the background, and refinement to improve the quality of the segmented mask. It provides an overview of approaches that have been used for each step, including early methods based on SVM and more recent deep learning-based techniques like Mask R-CNN that integrate detection and segmentation. The document also notes that segmentation is challenging without object detection cues and discusses types of segmentation as well as refinement methods that use transformations, dimension reduction, and graph-based modeling.Transparent Latent GAN



Transparent Latent GANDong Heon Cho
?
1. TL-GAN matches feature axes in the latent space to generate images without fine-tuning the neural network.
2. It discovers correlations between the latent vector Z and image labels by applying multivariate linear regression and normalizing the coefficients.
3. The vectors are then adjusted to be orthogonal, allowing different properties to be matched while labeling unlabeled data to add descriptions.Image matting atoc



Image matting atocDong Heon Cho
?
Image matting is the process of separating the foreground and background of an image by assigning each pixel an alpha value between 0 and 1 indicating its transparency. Traditionally, matting uses a trimap to classify pixels as foreground, background, or uncertain. Early sampling-based methods calculated alpha values based on feature distances of closest foreground and background pixels. More recent approaches use deep learning, where the first deep learning matting method in 2016 took local and non-local information as input, and the 2017 Deep Image Matting method used an RGB image and trimap as input in a fully deep learning framework.Multi object Deep reinforcement learning



Multi object Deep reinforcement learningDong Heon Cho
?
This document discusses multi-objective reinforcement learning and introduces Deep OLS Learning, which combines multi-objective learning with deep Q-networks. It presents Deep OLS Learning with Partial Reuse and Full Reuse to handle multi-objective Markov decision processes by finding a convergence set of policies that optimize multiple conflicting objectives, such as maximizing server performance while minimizing power consumption. The approach is evaluated on multi-objective versions of mountain car and deep sea treasure problems.Multi agent reinforcement learning for sequential social dilemmas



Multi agent reinforcement learning for sequential social dilemmasDong Heon Cho
?
This document summarizes research on multi-agent reinforcement learning in sequential social dilemmas. It discusses how sequential social dilemmas extend traditional matrix games by adding temporal aspects like partial observability. Simulation experiments are described where agents learn cooperative or defective policies for tasks like fruit gathering and wolfpack hunting in a partially observable environment. The agents' learned policies are then used to construct an empirical payoff matrix to analyze whether cooperation or defection is rewarded more, relating the multi-agent reinforcement learning results back to classic social dilemmas.Multi agent System



Multi agent SystemDong Heon Cho
?
This document discusses multi-agent systems and their applications. It provides examples of multi-agent systems for spacecraft control, manufacturing scheduling, and more. Key points:
- Multi-agent systems consist of interacting intelligent agents that can cooperate, coordinate, and negotiate to achieve goals. They offer benefits like robustness, scalability, and reusability.
- Challenges include defining global goals from local actions and incentivizing cooperation. Games like the prisoner's dilemma model social dilemmas around cooperation versus defection.
- The document outlines architectures like the blackboard model and BDI (belief-desire-intention) model. It also provides a manufacturing example using the JADE platform.Hybrid reward architecture



Hybrid reward architectureDong Heon Cho
?
The document discusses Hybrid Reward Architecture (HRA), a reinforcement learning method that decomposes the reward function of an environment into multiple sub-reward functions. In HRA, each sub-reward function is learned by a separate agent using DQN. This allows HRA to learn complex reward functions more quickly and stably compared to using a single reward signal. An experiment is described where HRA learns to eat 5 randomly placed fruits in an environment over 300 steps more effectively than a standard DQN agent.AlexNet and so on...



AlexNet and so on...Dong Heon Cho
?
AlexNet 2012 Contributions and Structure with Simple keras Code.
Multi GPU, Pooling, Data Augmentation...Deep Learning AtoC with Image Perspective



Deep Learning AtoC with Image PerspectiveDong Heon Cho
?
Deep learning models like CNNs, RNNs, and GANs are widely used for image classification and computer vision tasks. CNNs are commonly used for tasks like classification, detection, segmentation through learning hierarchical image features. Fully convolutional networks with encoder-decoder architectures like SegNet and Mask R-CNN can perform pixel-level semantic segmentation and instance segmentation by combining classification and bounding box detection. Deep learning has achieved state-of-the-art performance on many image applications due to its ability to learn powerful visual representations from large datasets.LOL win prediction



LOL win predictionDong Heon Cho
?
League of legend win prediction on master 1 tier.
A pipeline of data analytics and how to improve results.How can we train with few data



How can we train with few dataDong Heon Cho
?
The document discusses approaches for using deep learning with small datasets, including transfer learning techniques like fine-tuning pre-trained models, multi-task learning, and metric learning approaches for few-shot and zero-shot learning problems. It also covers domain adaptation techniques when labels are not available, as well as anomaly detection for skewed label distributions. Traditional models like SVM are suggested as initial approaches, with deep learning techniques applied if those are not satisfactory.Domain adaptation gan



Domain adaptation ganDong Heon Cho
?
The document discusses domain adaptation and transfer learning techniques in deep learning such as feature extraction, fine tuning, and parameter sharing. It specifically describes domain-adversarial neural networks which aim to make the source and target feature distributions indistinguishable and domain separation networks which extract domain-invariant and private features to model each domain separately.Dense sparse-dense training for dnn and Other Models



Dense sparse-dense training for dnn and Other ModelsDong Heon Cho
?
Deep Learning Training methods & Squeezing methodsSqueeeze models



Squeeeze modelsDong Heon Cho
?
This document discusses various techniques for compressing and speeding up deep neural networks, including singular value decomposition, pruning, and SqueezeNet. Singular value decomposition can be used to compress fully connected layers by minimizing the difference between the original weight matrix and its low-rank approximation. Pruning techniques remove unimportant weights below a threshold. SqueezeNet is highlighted as designing a small CNN architecture from the start that achieves AlexNet-level accuracy with 50x fewer parameters and less than 0.5MB in size.Recently uploaded (20)
AI + Disability. Coded Futures: Better opportunities or biased outcomes?



AI + Disability. Coded Futures: Better opportunities or biased outcomes?Christine Hemphill
?
A summary report into attitudes to and implications of AI as it relates to disability. Will AI enabled solutions create greater opportunities or amplify biases in society and datasets? Informed by primary mixed methods research conducted in the UK and globally by Open Inclusion on behalf of the Institute of People Centred AI, Uni of Surrey and Royal Holloway University. Initially presented at Google London in Jan 2025.
If you prefer an audio visual format you can access the full video recorded at Google ADC London where we presented this research in January 2025. It has captioned content and audio described visuals and is available at https://www.youtube.com/watch?v=p_1cv042U_U. There is also a short Fireside Chat about the research held at Zero Project Conference March 2025 available at https://www.youtube.com/live/oFCgIg78-mI?si=EoIaEgDw2U7DFXsN&t=11879.
If 狠狠撸 Share's format is not accessible to you in any way, please contact us at contact@openinclusion.com and we can provide you with the underlying document. 办理魁北克大学成绩单触购买加拿大鲍蚕础惭成绩单文凭定制



办理魁北克大学成绩单触购买加拿大鲍蚕础惭成绩单文凭定制taqyed
?
真实可查毕业证加拿大文凭购买,加拿大文凭定制,加拿大魁北克大学文凭补办【q薇1954292140】专业在线定制加拿大大学文凭成绩单用纸,定做加拿大本科文凭,【q薇1954292140】复制加拿大Université du Québec à Montréal completion letter。在线快速补办加拿大本科毕业证、硕士文凭证书,购买加拿大学位证、魁北克大学Offer,加拿大大学文凭在线购买。高仿真还原加拿大文凭证书和外壳,定制加拿大魁北克大学成绩单和信封。毕业证网上可查学历信息UQAM毕业证【q薇1954292140】办理加拿大魁北克大学毕业证(UQAM毕业证书)【q薇1954292140】毕业证外壳魁北克大学offer/学位证办学位证、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决魁北克大学学历学位认证难题。
特殊原因导致无法毕业,也可以联系我们帮您办理相关材料:
1:在魁北克大学挂科了,不想读了,成绩不理想怎么办???
2:打算回国了,找工作的时候,需要提供认证《UQAM成绩单购买办理魁北克大学毕业证书范本》【Q/WeChat:1954292140】Buy Université du Québec à Montréal Diploma《正式成绩单论文没过》有文凭却得不到认证。又该怎么办???加拿大毕业证购买,加拿大文凭购买,
3:回国了找工作没有魁北克大学文凭怎么办?有本科却要求硕士又怎么办?
帮您解决在加拿大魁北克大学未毕业难题(Université du Québec à Montréal)文凭购买、毕业证购买、大学文凭购买、大学毕业证购买、买文凭、日韩文凭、英国大学文凭、美国大学文凭、澳洲大学文凭、加拿大大学文凭(q薇1954292140)新加坡大学文凭、新西兰大学文凭、爱尔兰文凭、西班牙文凭、德国文凭、教育部认证,买毕业证,毕业证购买,买大学文凭,购买日韩毕业证、英国大学毕业证、美国大学毕业证、澳洲大学毕业证、加拿大大学毕业证(q薇1954292140)新加坡大学毕业证、新西兰大学毕业证、爱尔兰毕业证、西班牙毕业证、德国毕业证,回国证明,留信网认证,留信认证办理,学历认证。从而完成就业。
如果您在英、加、美、澳、欧洲等留学过程中或回国后:
1、在校期间因各种原因未能顺利毕业《UQAM成绩单工艺详解》【Q/WeChat:1954292140】《Buy Université du Québec à Montréal Transcript快速办理魁北克大学教育部学历认证书毕业文凭证书》,拿不到官方毕业证;
2、面对父母的压力,希望尽快拿到;
3、不清楚认证流程以及材料该如何准备;
4、回国时间很长,忘记办理;
5、回国马上就要找工作《正式成绩单魁北克大学学历认证失败怎么办》【q薇1954292140】《成绩单水印UQAM成绩单如何办理》办给用人单位看;
6、企事业单位必须要求办理的;
7、需要报考公务员、购买免税车、落转户口、申请留学生创业基金。
加拿大文凭魁北克大学成绩单,UQAM毕业证【q薇1954292140】办理加拿大魁北克大学毕业证(UQAM毕业证书)【q薇1954292140】学历认证失败怎么办魁北克大学offer/学位证成绩单制作案例、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决魁北克大学学历学位认证难题。
【q薇1954292140】办理魁北克大学毕业证(UQAM毕业证书)毕业证范本【q薇1954292140】魁北克大学offer/学位证、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作加拿大魁北克大学毕业证(UQAM毕业证书)学历学位证制作
主营项目:
1、真实教育部国外学历学位认证《加拿大毕业文凭证书快速办理魁北克大学在线制作假学位证》【q薇1954292140】《论文没过魁北克大学正式成绩单》,教育部存档,教育部留服网站100%可查.
2、办理UQAM毕业证,改成绩单《UQAM毕业证明办理魁北克大学毕业证书购买》【Q/WeChat:1954292140】Buy Université du Québec à Montréal Certificates《正式成绩单论文没过》,魁北克大学Offer、在读证明、学生卡、信封、证明信等全套材料,从防伪到印刷,从水印到钢印烫金,高精仿度跟学校原版100%相同.
3、真实使馆认证(即留学人员回国证明),使馆存档可通过大使馆查询确认.
4、留信网认证,国家专业人才认证中心颁发入库证书,留信网存档可查.
《魁北克大学学位证书制作代办流程加拿大毕业证书办理UQAM学位证学生卡录取书》【q薇1954292140】学位证1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。
成绩单购买最佳渠道加拿大文凭魁北克大学成绩单【q薇1954292140】复刻成绩单加拿大魁北克大学毕业证(UQAM毕业证书)研究生学历文凭 魁北克大学毕业证办理,修改成绩单GPA加拿大魁北克大学文凭办理,加拿大魁北克大学成绩单办理和真实留信认证、留服认证、魁北克大学学历认证。学院文凭定制,魁北克大学原版文凭补办,扫描件文凭定做,100%文凭复刻。【q薇1954292140】Buy Université du Québec à Montréal Diploma购买美国毕业证,购买英国毕业证,购买澳洲毕业证,购买加拿大毕业证,以及德国毕业证,购买法国毕业证(q薇1954292140)购买荷兰毕业证、购买瑞士毕业证、购买日本毕业证、购买韩国毕业证、购买新西兰毕业证、购买新加坡毕业证、购买西班牙毕业证、购买马来西亚毕业证等。包括了本科毕业证,硕士毕业证。
留信认证的作用:
1. 身份认证:留信认证可以证明你的留学经历是真实的,且你获得的学历或学位是正规且经过认证的。这对于一些用人单位来说,尤其是对留学经历有高度要求的公司(如跨国公司或国内高端公司),这是非常重要的一个凭证。
专业评定:留信认证不仅认证你的学位证书,还会对你的所学专业进行评定。这有助于展示你的学术背景,特别是对于国内公司而言,能够清楚了解你所学专业的水平和价值。
国家人才库入库:认证后,你的信息将被纳入国家人才库,并且可以在国家人才网等平台上展示,供包括500强公司等大型公司挑选和聘用人才。这对于回国找工作特别是进入大公司,具有非常积极的作用。
2. 留信认证对就业的好处
提高竞争力:通过留信认证,尤其是对你所学专业的认证,可以大大提高你在国内求职时的竞争力。许多公司对留学生背景和所学专业有很高的要求,认证后的信息能够帮助公司快速识别符合条件的候选人。
增强信任度:公司往往会对没有认证的学历背景产生疑虑,而留信认证为你的学历背景提供了第三方权威机构的背书,增强了雇主的信任。Kaggle & Datathons: A Practical Guide to AI Competitions



Kaggle & Datathons: A Practical Guide to AI Competitionsrasheedsrq
?
Kaggle & Datathons: A Practical Guide to AI CompetitionsAnalyzing Consumer Spending Trends and Purchasing Behavior



Analyzing Consumer Spending Trends and Purchasing Behavioromololaokeowo1
?
This project explores consumer spending patterns using Kaggle-sourced data to uncover key trends in purchasing behavior. The analysis involved cleaning and preparing the data, performing exploratory data analysis (EDA), and visualizing insights using ExcelI. Key focus areas included customer demographics, product performance, seasonal trends, and pricing strategies. The project provided actionable insights into consumer preferences, helping businesses optimize sales strategies and improve decision-making.The Marketability of Rice Straw Yarn Among Selected Customers of Gantsilyo Guru



The Marketability of Rice Straw Yarn Among Selected Customers of Gantsilyo Gurukenyoncenteno12
?
IMR Paper加拿大成绩单购买原版(顿补濒毕业证书)戴尔豪斯大学毕业证文凭



加拿大成绩单购买原版(顿补濒毕业证书)戴尔豪斯大学毕业证文凭taqyed
?
专业定制国外文凭学历证书加拿大文凭戴尔豪斯大学成绩单?【q薇1954292140】复刻成绩单加拿大戴尔豪斯大学毕业证(Dal毕业证书)《国外学历学位认证书》 戴尔豪斯大学毕业证办理,办学历认证加拿大戴尔豪斯大学文凭办理,加拿大戴尔豪斯大学成绩单办理和真实留信认证、留服认证、戴尔豪斯大学学历认证。学院文凭定制,戴尔豪斯大学原版文凭补办,扫描件文凭定做,100%文凭复刻。【q薇1954292140】Buy Dalhousie University Diploma购买美国毕业证,购买英国毕业证,购买澳洲毕业证,购买加拿大毕业证,以及德国毕业证,购买法国毕业证(q薇1954292140)购买荷兰毕业证、购买瑞士毕业证、购买日本毕业证、购买韩国毕业证、购买新西兰毕业证、购买新加坡毕业证、购买西班牙毕业证、购买马来西亚毕业证等。包括了本科毕业证,硕士毕业证。
如果您在英、加、美、澳、欧洲等留学过程中或回国后:
1、在校期间因各种原因未能顺利毕业《Dal成绩单工艺详解》【Q/WeChat:1954292140】《Buy Dalhousie University Transcript快速办理戴尔豪斯大学教育部学历认证书毕业文凭证书》,拿不到官方毕业证;
2、面对父母的压力,希望尽快拿到;
3、不清楚认证流程以及材料该如何准备;
4、回国时间很长,忘记办理;
5、回国马上就要找工作《正式成绩单戴尔豪斯大学在线制作学位证书》【q薇1954292140】《办留学学历认证Dal专业定制国外成绩单修改GPA》办给用人单位看;
6、企事业单位必须要求办理的;
7、需要报考公务员、购买免税车、落转户口、申请留学生创业基金。
加拿大文凭戴尔豪斯大学成绩单,Dal毕业证【q薇1954292140】办理加拿大戴尔豪斯大学毕业证(Dal毕业证书)【q薇1954292140】定制成绩单GPA戴尔豪斯大学offer/学位证毕业证详解细节、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决戴尔豪斯大学学历学位认证难题。
加拿大文凭购买,加拿大文凭定制,加拿大文凭补办。专业在线定制加拿大大学文凭,定做加拿大本科文凭,【q薇1954292140】复制加拿大Dalhousie University completion letter。在线快速补办加拿大本科毕业证、硕士文凭证书,购买加拿大学位证、戴尔豪斯大学Offer,加拿大大学文凭在线购买。高仿真还原加拿大文凭证书和外壳,定制加拿大戴尔豪斯大学成绩单和信封。购买学位证Dal毕业证【q薇1954292140】办理加拿大戴尔豪斯大学毕业证(Dal毕业证书)【q薇1954292140】文凭购买戴尔豪斯大学offer/学位证研究生文凭、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决戴尔豪斯大学学历学位认证难题。
特殊原因导致无法毕业,也可以联系我们帮您办理相关材料:
1:在戴尔豪斯大学挂科了,不想读了,成绩不理想怎么办???
2:打算回国了,找工作的时候,需要提供认证《Dal成绩单购买办理戴尔豪斯大学毕业证书范本》【Q/WeChat:1954292140】Buy Dalhousie University Diploma《正式成绩单论文没过》有文凭却得不到认证。又该怎么办???加拿大毕业证购买,加拿大文凭购买,
3:回国了找工作没有戴尔豪斯大学文凭怎么办?有本科却要求硕士又怎么办?
帮您解决在加拿大戴尔豪斯大学未毕业难题(Dalhousie University)文凭购买、毕业证购买、大学文凭购买、大学毕业证购买、买文凭、日韩文凭、英国大学文凭、美国大学文凭、澳洲大学文凭、加拿大大学文凭(q薇1954292140)新加坡大学文凭、新西兰大学文凭、爱尔兰文凭、西班牙文凭、德国文凭、教育部认证,买毕业证,毕业证购买,买大学文凭,购买日韩毕业证、英国大学毕业证、美国大学毕业证、澳洲大学毕业证、加拿大大学毕业证(q薇1954292140)新加坡大学毕业证、新西兰大学毕业证、爱尔兰毕业证、西班牙毕业证、德国毕业证,回国证明,留信网认证,留信认证办理,学历认证。从而完成就业。
主营项目:
1、真实教育部国外学历学位认证《加拿大毕业文凭证书快速办理戴尔豪斯大学成绩单原版仿制》【q薇1954292140】《论文没过戴尔豪斯大学正式成绩单》,教育部存档,教育部留服网站100%可查.
2、办理Dal毕业证,改成绩单《Dal毕业证明办理戴尔豪斯大学文凭皮套购买》【Q/WeChat:1954292140】Buy Dalhousie University Certificates《正式成绩单论文没过》,戴尔豪斯大学Offer、在读证明、学生卡、信封、证明信等全套材料,从防伪到印刷,从水印到钢印烫金,高精仿度跟学校原版100%相同.
3、真实使馆认证(即留学人员回国证明),使馆存档可通过大使馆查询确认.
4、留信网认证,国家专业人才认证中心颁发入库证书,留信网存档可查.
《戴尔豪斯大学学历认证报告怎么弄加拿大毕业证书办理Dal成绩单样本》【q薇1954292140】学位证1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。
【q薇1954292140】办理戴尔豪斯大学毕业证(Dal毕业证书)成绩单影本【q薇1954292140】戴尔豪斯大学offer/学位证、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作加拿大戴尔豪斯大学毕业证(Dal毕业证书)学校原版文凭补办
留信认证的作用:
1. 身份认证:留信认证可以证明你的留学经历是真实的,且你获得的学历或学位是正规且经过认证的。这对于一些用人单位来说,尤其是对留学经历有高度要求的公司(如跨国公司或国内高端公司),这是非常重要的一个凭证。
专业评定:留信认证不仅认证你的学位证书,还会对你的所学专业进行评定。这有助于展示你的学术背景,特别是对于国内公司而言,能够清楚了解你所学专业的水平和价值。
国家人才库入库:认证后,你的信息将被纳入国家人才库,并且可以在国家人才网等平台上展示,供包括500强公司等大型公司挑选和聘用人才。这对于回国找工作特别是进入大公司,具有非常积极的作用。2025-03-03-Philly-AAAI-GoodData-Build Secure RAG Apps With Open LLM



2025-03-03-Philly-AAAI-GoodData-Build Secure RAG Apps With Open LLMTimothy Spann
?
2025-03-03-Philly-AAAI-GoodData-Build Secure RAG Apps With Open LLM
https://aaai.org/conference/aaai/aaai-25/workshop-list/#ws14Introduction to database and analysis software’s suitable for.pptx



Introduction to database and analysis software’s suitable for.pptxnabinparajuli9
?
This ppt provides brief introduction and major strengths and limitations of database and analysis software’s suitable for health research.
Introduction Lecture 01 Data Science.pdf



Introduction Lecture 01 Data Science.pdfmessagetome133
?
Data Science Lectures Data Science Lectures Data Science Lectures Data Science Lectures Data Science Lectures Data Science Lectures Data Science Lectures Data Science Lectures Data Science Lectures Data Science Lectures Data Science Lectures Data Science Lectures Optimizing Common Table Expressions in Apache Hive with Calcite



Optimizing Common Table Expressions in Apache Hive with CalciteStamatis Zampetakis
?
In many real-world queries, certain expressions may appear multiple times, requiring repeated computations to construct the final result. These recurring computations, known as common table expressions (CTEs), can be explicitly defined in SQL queries using the WITH clause or implicitly derived through transformation rules. Identifying and leveraging CTEs is essential for reducing the cost of executing complex queries and is a critical component of modern data management systems.
Apache Hive, a SQL-based data management system, provides powerful mechanisms to detect and exploit CTEs through heuristic and cost-based optimization techniques.
This talk delves into the internals of Hive's planner, focusing on its integration with Apache Calcite for CTE optimization. We will begin with a high-level overview of Hive's planner architecture and its reliance on Calcite in various planning phases. The discussion will then shift to the CTE rewriting phase, highlighting key Calcite concepts and demonstrating how they are employed to optimize CTEs effectively.MLecture 1 Introduction to AI . The basics.pptx



MLecture 1 Introduction to AI . The basics.pptxFaizaKhan720183
?
Machine learning and artificial intelligence introduction. Machine learning and artificial intelligence introduction.Machine learning and artificial intelligence introduction.Machine learning and artificial intelligence introduction.Machine learning and artificial intelligence introduction.Machine learning and artificial intelligence introduction.Machine learning and artificial intelligence introduction.Machine learning and artificial intelligence introduction.Cost sheet. with basics and formats of sheet



Cost sheet. with basics and formats of sheetsupreetk82004
?
Cost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetCost sheet. with basics and formats of sheetThe truth behind the numbers: spotting statistical misuse.pptx



The truth behind the numbers: spotting statistical misuse.pptxandyprosser3
?
As a producer of official statistics, being able to define what misinformation means in relation to data and statistics is so important to us.
For our sixth webinar, we explored how we handle statistical misuse especially in the media. We were also joined by speakers from the Office for Statistics Regulation (OSR) to explain how they play an important role in investigating and challenging the misuse of statistics across government.Use Jupyter notebook guide in 5 minutes
- 2. Jupyter Notebook SWAG usage davinnovation@gmail.com
- 3. Notebook ? (IPython Notebook) Interactive environment with code, text, plot, media etc
- 5. Notebook ? Current Kernel Name
- 6. Notebook ? Run Cell & Select Below Interrupt kernel Restart the kernel
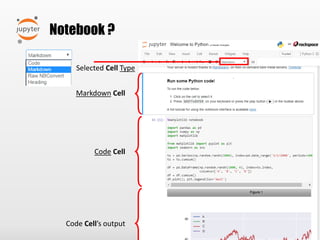
- 7. Notebook ? Selected Cell Type Markdown Cell Code Cell Code Cell’s output
- 8. Jupyter Notebook MODE Esc Command Mode Enter Edit Mode Control Cell Modify Cell
- 9. Just remember 7 THINGS! Esc Command Mode a Insert cell above b Insert cell below delete selected cellsd d Shift + Enter Ctrl + Enter Run cell, select || create below Run selected cells m To markdown y To code
- 10. Just remember 3 THINGS! Enter Edit Mode Tab Code indent Shift + Tab tooltip Ctrl + m Command mode Same as ESC
- 12. Use Jupyter Notebook SWAG








