1 of 38
Downloaded 62 times
























![ラベルの強化
? ラベルはセレクタとして使われている。たとえばService
は、指定されたラベルのPodにトラフィックを転送してい
る
? このセレクタ機能が強化される
? key is in [“nginx”, “apache”] ?みたいな感じで、複数ラベ
ルを付けられるようになる
? key is not in [“development”, “qa”]?みたいな感じで、除
外するラベルを指定できるようになる](https://image.slidesharecdn.com/kubernetesdockerswarm-141220060515-conversion-gate02/85/Kubernetes-Docker-Machine-Swarm-26-320.jpg)











Recommended
办耻产别谤苍别迟别蝉(骋碍贰)环境における诲补迟补诲辞驳利用



办耻产别谤苍别迟别蝉(骋碍贰)环境における诲补迟补诲辞驳利用Koichi HARUNA
?
办耻产别谤苍别迟别蝉上で自社サービスを动かしているのですが、そこでどのように诲补迟补诲辞驳を动かして利用しているかを説明しています。半分以上办耻产别谤苍别迟别蝉の説明になっています。骋碍贰で半年运用してみた



骋碍贰で半年运用してみたKatsutoshi Nagaoka
?
gcp ja night #31 での発表資料です。
http://gcpja.connpass.com/event/23874/
[補足記事]
http://qiita.com/na_ga/items/d89b320ba098a0941043
http://qiita.com/na_ga/items/7c3cc3f52dd4068fd319Webアプリ開発向け ゆるふわDocker使いが Cloud Naive開発に必要なetc.



Webアプリ開発向け ゆるふわDocker使いが Cloud Naive開発に必要なetc.YASUKAZU NAGATOMI
?
Cloud Native Kansai #02
https://cnjp.connpass.com/event/117651/碍耻产别谤苍别迟别蝉にまつわるエトセトラ(主に苦労话)



碍耻产别谤苍别迟别蝉にまつわるエトセトラ(主に苦労话)Works Applications
?
Dockerをちゃんと使おうと考えていたらKubernetesに出会いました。ERPのシステム開発でkubernetesを使おうとして苦労した、あるいは現在進行形で苦労していることを、そもそもKubernetesが解決しようとしている課題やそのアーキテクチャそのものにも言及しながらお話します。Dockerをベースにシステム設計を行おうとしている方にノウハウ(主に苦労話)を共有します。
July 24th, 2016 July Tech Festa 2016Docker & Kubernetes基礎



Docker & Kubernetes基礎Daisuke Hiraoka
?
2019/8/29 IBM Cloudユーザーグループ bmxug.tokyo #11 での登壇資料 「 Docker/Kubernetes 基礎編 」机上の Kubernetes - 形式手法で見るコンテナオーケストレーション #NGK2016B



机上の Kubernetes - 形式手法で見るコンテナオーケストレーション #NGK2016By_taka_23
?
2016 年名古屋合同懇親会 (NGK2016B) の LT で使用したスライドです。Kubernetes がコンテナを配置する仕組みをモデル検査器 Alloy を用いてモデリングし、初期状態と最終状態を与えてその間の状態遷移を自動で発見します。Kubernetes超入門 with java



Kubernetes超入門 with javaYasunari Tanaka
?
2017年10月27開催の広島Javaユーザーグループの資料です。
SpeakerDeckへ移行します。(https://speakerdeck.com/yasu7ri/kubernetes-super-introduction-with-java)Google Container Engine (GKE) & Kubernetes のアーキテクチャ解説



Google Container Engine (GKE) & Kubernetes のアーキテクチャ解説Samir Hammoudi
?
Google Container Engine (GKE) のすごいところやメリットを理解するには、まずコンテナのオーケストレーションシステムである
Kubernetes をちゃんと理解する必要があります。
本資料では Kubernetes のアーキテクチャやコンポーネント及びリソースを1つずつ解説し、その後、GKE を使うとどれだけ Kubernetes が便利で実際に使えるかを説明します。Kubernetes introduction



Kubernetes introductionDAEBUM LEE
?
kubernetes入門 (ContainerからKubernetesまで)
?主にdocker/kubernetesの話です。
関連リンク
?https://recruit.gmo.jp/engineer/jisedai/blog/kubernetes-introduction/
Cloud Foundry Container-to-Container Networking



Cloud Foundry Container-to-Container NetworkingKazuto Kusama
?
CF Tokyo Meetup #3で発表した資料です。CFのC2C機能でコンテナ間通信できるようになりましたコンテナ時代だからこそ要注目! Cloud Foundry



コンテナ時代だからこそ要注目! Cloud FoundryKazuto Kusama
?
mastercloud #4で発表した資料です。PaaSか?コンテナか?ではなく、もっと違った視点で検討するのはいかがでしょーか?という資料ですひしめき合うOpen PaaSを徹底解剖! PaaSの今と未来



ひしめき合うOpen PaaSを徹底解剖! PaaSの今と未来Kazuto Kusama
?
July Tech Festaで発表した資料です。 Cloud Foundry、OpenShift v3、Deis、Flynnを取り上げて、Open PaaSの今と未来について解説しました。More Related Content
What's hot (20)
碍耻产别谤苍别迟别蝉にまつわるエトセトラ(主に苦労话)



碍耻产别谤苍别迟别蝉にまつわるエトセトラ(主に苦労话)Works Applications
?
Dockerをちゃんと使おうと考えていたらKubernetesに出会いました。ERPのシステム開発でkubernetesを使おうとして苦労した、あるいは現在進行形で苦労していることを、そもそもKubernetesが解決しようとしている課題やそのアーキテクチャそのものにも言及しながらお話します。Dockerをベースにシステム設計を行おうとしている方にノウハウ(主に苦労話)を共有します。
July 24th, 2016 July Tech Festa 2016Docker & Kubernetes基礎



Docker & Kubernetes基礎Daisuke Hiraoka
?
2019/8/29 IBM Cloudユーザーグループ bmxug.tokyo #11 での登壇資料 「 Docker/Kubernetes 基礎編 」机上の Kubernetes - 形式手法で見るコンテナオーケストレーション #NGK2016B



机上の Kubernetes - 形式手法で見るコンテナオーケストレーション #NGK2016By_taka_23
?
2016 年名古屋合同懇親会 (NGK2016B) の LT で使用したスライドです。Kubernetes がコンテナを配置する仕組みをモデル検査器 Alloy を用いてモデリングし、初期状態と最終状態を与えてその間の状態遷移を自動で発見します。Kubernetes超入門 with java



Kubernetes超入門 with javaYasunari Tanaka
?
2017年10月27開催の広島Javaユーザーグループの資料です。
SpeakerDeckへ移行します。(https://speakerdeck.com/yasu7ri/kubernetes-super-introduction-with-java)Google Container Engine (GKE) & Kubernetes のアーキテクチャ解説



Google Container Engine (GKE) & Kubernetes のアーキテクチャ解説Samir Hammoudi
?
Google Container Engine (GKE) のすごいところやメリットを理解するには、まずコンテナのオーケストレーションシステムである
Kubernetes をちゃんと理解する必要があります。
本資料では Kubernetes のアーキテクチャやコンポーネント及びリソースを1つずつ解説し、その後、GKE を使うとどれだけ Kubernetes が便利で実際に使えるかを説明します。Kubernetes introduction



Kubernetes introductionDAEBUM LEE
?
kubernetes入門 (ContainerからKubernetesまで)
?主にdocker/kubernetesの話です。
関連リンク
?https://recruit.gmo.jp/engineer/jisedai/blog/kubernetes-introduction/
Cloud Foundry Container-to-Container Networking



Cloud Foundry Container-to-Container NetworkingKazuto Kusama
?
CF Tokyo Meetup #3で発表した資料です。CFのC2C機能でコンテナ間通信できるようになりましたコンテナ時代だからこそ要注目! Cloud Foundry



コンテナ時代だからこそ要注目! Cloud FoundryKazuto Kusama
?
mastercloud #4で発表した資料です。PaaSか?コンテナか?ではなく、もっと違った視点で検討するのはいかがでしょーか?という資料ですひしめき合うOpen PaaSを徹底解剖! PaaSの今と未来



ひしめき合うOpen PaaSを徹底解剖! PaaSの今と未来Kazuto Kusama
?
July Tech Festaで発表した資料です。 Cloud Foundry、OpenShift v3、Deis、Flynnを取り上げて、Open PaaSの今と未来について解説しました。Viewers also liked (20)
OpenShift v3 Technical Introduction



OpenShift v3 Technical IntroductionEtsuji Nakai
?
Wakameユーザ会#11での発表予定資料です
https://wakame.doorkeeper.jp/events/36606
2016/01/11 ver1.0 公開
2016/01/12 ver1.1 Update
2016/01/12 ver1.2 Update
2016/01/20 ver1.3 ユースケースイメージを追加Red Hat Enterprise Linux 7.1 Kubernetes入門



Red Hat Enterprise Linux 7.1 Kubernetes入門Etsuji Nakai
?
2015/03/26 ver1.1 flannelのトンネルタイプをVXLANに修正。
2015/04/03 ver1.2 flanneldの役割を修正。参考資料を追加。Cloud FoundryでDockerも.NETも。新しいDiegoの仕組み入門



Cloud FoundryでDockerも.NETも。新しいDiegoの仕組み入門Kazuto Kusama
?
第25回PaaS勉強会で発表した資料です。
Cloud Foundryの新アーキテクチャ、Diegoについて。 Rancher/Kubernetes入門ハンズオン資料~第2回さくらとコンテナの夕べ #さくらの夕べ 番外編



Rancher/Kubernetes入門ハンズオン資料~第2回さくらとコンテナの夕べ #さくらの夕べ 番外編Masahito Zembutsu
?
https://sakura-kanto.doorkeeper.jp/events/53172インフラエンジニアのための搁补苍肠丑别谤を使った顿辞肠办别谤运用入门



インフラエンジニアのための搁补苍肠丑别谤を使った顿辞肠办别谤运用入门Masahito Zembutsu
?
#qpstudy 2015.06 Lightning Talks Session
「インフラエンジニアのための搁补苍肠丑别谤を使った顿辞肠办别谤运用入门」
2015年6月20日(土) 渋谷 GMO YoursDocker入門-基礎編 いまから始めるDocker管理【2nd Edition】



Docker入門-基礎編 いまから始めるDocker管理【2nd Edition】Masahito Zembutsu
?
Docker入門-基礎編 いまから始めるDocker管理【2nd Edition】
JAWS-UG コンテナ支部 Docker 入門 #2
2015年10月30日(金)
http://jawsug-container.connpass.com/event/20924/
※コンテナ支部での発表スライドですが、内容は Docker に対して興味のある方、すべてを対象としています。前回のバージョンそのままではなく、説明の追加など、現在の状況にあわせて、ほぼ全面的に書き直しています。今だからこそ知りたい Docker Compose/Swarm 入門



今だからこそ知りたい Docker Compose/Swarm 入門Masahito Zembutsu
?
「Docker Machine/Compose/Swarm」を使ってみよう 発表資料
https://sakura-kanto.doorkeeper.jp/events/36134
日時:2016年1月22日(金)19:00~21:00
会場:さくらインターネット 西新宿セミナールーム@東京?西新宿
対象:Dockerに関心がありDocker Machine/Compose/Swarmを触った事がない人 Docker入門: コンテナ型仮想化技術の仕組みと使い方



Docker入門: コンテナ型仮想化技術の仕組みと使い方Yuichi Ito
?
Docker の特徴と使い方、簡単なネットワークの仕組みとコンテナ間の連携方法、及び3階層モデルの構築例などを記載しています。搁耻产测による本気の骋颁



搁耻产测による本気の骋颁Narihiro Nakamura
?
なぜあなたはCでGCを書くのですか? 本当はRubyで書きたいですよね? この
発表では(J)RubyでGCを書く方法を示します。ToyのGCじゃなくて、本気のGCを
Rubyで書けます!(の予定)割と新し目の Open shift origin で作る自宅 paas 作成記



割と新し目の Open shift origin で作る自宅 paas 作成記Hara Yoshihiko
?
PaaS基盤の一種である、OpenShift origin v3のインストール方法を解説します。RKT



RKTYutaka Matsubara
?
This document discusses the app container runtime rkt. It provides an overview of rkt, including what it is, its goals, and how it differs from Docker. Key points include:
- Rkt implements the Application Container (appc) specification and allows running containerized applications.
- Its goals are fast downloads/starts, verifiable/cacheable images, composability, and using common technologies like DNS for discovery.
- It differs from Docker in being more composable without a central daemon, focusing more on security through image verification, and using an open standard for images instead of Docker's format.
- The document demonstrates downloading images, verifying signatures, running containers in pods with options likeObject Detection & Instance Segmentationの論文紹介 | OHS勉強会#3



Object Detection & Instance Segmentationの論文紹介 | OHS勉強会#3Toshinori Hanya
?
勉強会で最近読んだ論文2本の紹介を行いました。
?SSD: Single Shot MultiBox Detector
?End-to-End Instance Segmentation and Counting with Recurrent Attention贬补蝉丑颈颁辞谤辫の狈辞尘补诲を使ったコンテナのスケジューリング手法



贬补蝉丑颈颁辞谤辫の狈辞尘补诲を使ったコンテナのスケジューリング手法Masahito Zembutsu
?
クラウド研究会 第2回「クラウドとコンテナー技術」発表資料
http://kokucheese.com/event/index/355047/
日時:2015年12月8日(火)19:00~21:00
会場:マイクロソフト@東京?品川Google for Mobile: コンテナで作るモバイル バックエンド - 福田 潔



Google for Mobile: コンテナで作るモバイル バックエンド - 福田 潔Google Cloud Platform - Japan
?
モバイルバックエンドの選択肢、コンテナとは?なぜコンテナなのか、マイクロサービスアーキテクチャ、および Kubernetes と Google Container Engine について。Similar to 最近のKubernetesとDocker Machine/厂飞补谤尘の话 (20)
最近良く聞く Kubernetes を体験してみた イントロ + 活用編



最近良く聞く Kubernetes を体験してみた イントロ + 活用編Fuminobu Takeyama
?
Kubernetes は多数のコンテナからなるシステムを行うためのシステムで、コンテナオーケストレーションシステムと
呼ばれるものの1つです。最初に開発した Google に加え、多数の企業からなるコミュニティによって開発されており、
近年注目されています。
本セミナーでは日本 openSUSE ユーザ会のメンバーが Kubernetes を使ってみた経験を紹介します。
前半の Kubernetes 構築編では、Kubernetes クラスタをローカル環境に構築する方法を説明します。
Google Cloud プラットフォームなどでは、サービスとして Kubernetes が提供されており、すぐに利用できますが、
本セミナーでは、ローカル環境で使用する方法を主に扱います。
前半の構築編では、openSUSE Tumbleweed ベースのディストリビューション openSUSE Kubic と kubeadm で、
すぐに?簡単に Kubernetes クラスタ(master, worker ノード)をセットアップする方法を説明します。続けて、
dashboad をインストールし、Web ブラウザで実行中のコンテナを管理する方法を紹介します。
後半の活用編は、自作の Web アプリケーションを Kubernetes クラスタにデプロイしてみた体験談です。
基本的な考え方と、Docker や docker-compose で実行する場合との違いについて説明します。
※本セミナーでは Kubernetes の専門的な技術情報は提供できませんのでご了承下さいKubernetes Meetup Tokyo #8 Self-hosted Kubernetes を調べてみた



Kubernetes Meetup Tokyo #8 Self-hosted Kubernetes を調べてみたAkihito Inoh
?
Kubernetes Meetup Tokyo #8 のLTで発表した資料です。
「Self-hosted Kubernetes を調べてみた」办耻产别-蝉测蝉迟别尘落としてみました



办耻产别-蝉测蝉迟别尘落としてみましたShuntaro Saiba
?
kube-system 意識していますか? (私は意識してませんでした)
kube-dns が死んだりすると、サービス停止しちゃいます (経験談)
せっかくなのでkube-systemをそれぞれ落として、
影響を調べてみました。 (反省を兼ねて)
今回はGKEで試しています
CI/CD Pipeline を考える ?KubeCon 2017 + CyberAgent の最大公倍数?



CI/CD Pipeline を考える ?KubeCon 2017 + CyberAgent の最大公倍数?Masaya Aoyama
?
Kubernetes 環境での CI/CD の方法は色々考えることがありますが、今回は KubeCon + CloudNativeCon 2017 で聞いてきた沢山の CI/CD のセッションと、CyberAgent でのいくつかの実例を含めながら、最小公倍数?最大公約数?的なお話をさせていただきました。
付録として、CI/CD 周りで興味深かったセッションと Keynote をまとめてあります。
@市ヶ谷Geek★Night #16 Kubernetes Christmas!AKS (k8s) Hands on Lab Contents



AKS (k8s) Hands on Lab ContentsYoshio Terada
?
This is AKS (k8s) Hands on Lab Contents in Summer at Japan Tour 2019.Kube con + cloudnativecon 2017 社内報告会(外部公開用)



Kube con + cloudnativecon 2017 社内報告会(外部公開用)Masaya Aoyama
?
KubeCon + CloudNativeCon 2017 NorthAmerica @Austin に参加してきた共有資料になります。
社内向けに Keynote 1 + 2 日目と CI/CD 周りの話をまとめてあります。Kubernets on Bluemix + DevOpsでコンテナCIやってみた



Kubernets on Bluemix + DevOpsでコンテナCIやってみたShoichiro Sakaigawa
?
BMXUG つきじ#1 セッションで発表した
Kubernets on Bluemix + DevOpsでコンテナCIやってみた
の資料です。Introduction of Azure Docker Integration



Introduction of Azure Docker IntegrationTakekazu Omi
?
2020/7/30 第28回 Tokyo Jazug Night
6/25に、Docker cli のAzure統合がベータリリース ? したので今日は簡単に紹介するDocker/Aarukas入門ハンズオン資料~第1回さくらとコンテナの夕べ #さくらの夕べ 番外編



Docker/Aarukas入門ハンズオン資料~第1回さくらとコンテナの夕べ #さくらの夕べ 番外編Masahito Zembutsu
?
Dockerのインストールをはじめ、基本的なdockerコマンドの使い方、Nginxウェブサーバのコンテナ構築の流れと、Arukasでデプロイするまでを辿ります。
開催:平成28年10月31日(月)
さくらの夕べ(番外編)第1回Docker/Arukas入門ハンズオン
https://sakura-kanto.doorkeeper.jp/events/52770これから始めるAzure Kubernetes Service入門



これから始めるAzure Kubernetes Service入門Yuto Takei
?
Virtual Azure Community Day 日本語トラック
2020/7/28 15:00 – 16:00
顿辞肠办别谤クイックツアー



顿辞肠办别谤クイックツアーEtsuji Nakai
?
Linux女子部08「Docker勉強会」
http://connpass.com/event/6318/
で使用予定の資料の一部です。
変更履歴
ver1.0 公開
ver1.1 Dockerfileの内容修正
ver1.2 「Dockerとは?」追加
ver1.3 「Dockerが無いとき」を追加
ver1.4 Dockerfileを分かりやすく修正
ver1.5 微修正
ver1.6 docker-io-0.11.1-3.el7.x86_64に合わせて手順を修正
ver 1.8 Fedora20 + Docker1.0 に手順を変更
ver 1.9 run/stop/start/rm のライフサイクルの説明を追加[GKE & Spanner 勉強会] GKE 入門![[GKE & Spanner 勉強会] GKE 入門](https://cdn.slidesharecdn.com/ss_thumbnails/gke01-200121090059-thumbnail.jpg?width=560&fit=bounds)
![[GKE & Spanner 勉強会] GKE 入門](https://cdn.slidesharecdn.com/ss_thumbnails/gke01-200121090059-thumbnail.jpg?width=560&fit=bounds)
![[GKE & Spanner 勉強会] GKE 入門](https://cdn.slidesharecdn.com/ss_thumbnails/gke01-200121090059-thumbnail.jpg?width=560&fit=bounds)
![[GKE & Spanner 勉強会] GKE 入門](https://cdn.slidesharecdn.com/ss_thumbnails/gke01-200121090059-thumbnail.jpg?width=560&fit=bounds)
[GKE & Spanner 勉強会] GKE 入門Google Cloud Platform - Japan
?
2020 年 1 月 21 日開催 GKE & Cloud Spanner 勉強会【基礎編】
セッション:GKE 入門
講師:川原 雄太(Yutty)
カスタマーエンジニア ゲーム業界担当Introduction of skippbox



Introduction of skippboxGo Chiba
?
This talk just introduce "skippbox" that running as a k8s frontend application.Virtual Kubelet and Virtual Node



Virtual Kubelet and Virtual NodeYoshio Terada
?
This presentation explain the basic of Virtual Kubelet and Virtual Node.Infra: Kubernetes and GKE, Network



Infra: Kubernetes and GKE, NetworkKuma Arakawa
?
https://gdg-tokyo.connpass.com/event/52811
で発表した、Google Cloud Next 17 ExtendedのInfraパートの資料です。More from Kazuto Kusama (18)
Istio, Kubernetes and Cloud Foundry



Istio, Kubernetes and Cloud FoundryKazuto Kusama
?
※補足文が小さくて読みづらい方は修正版をご覧ください /jacopen/istio-kubernetes-and-cloud-foundry-99649855
Container SIGで発表した資料です。Istioはk8sのみでなくCloud Foundryにも、Microservicesで嬉しい機能をもたらします。k8sだけじゃないIstio - Cloud FoundryのIstioインテグレーションについて



k8sだけじゃないIstio - Cloud FoundryのIstioインテグレーションについてKazuto Kusama
?
This document discusses how Istio can be used to provide routing and service discovery capabilities for Kubernetes and Cloud Foundry environments. It describes how Istio integrates with Kubernetes and Cloud Foundry components like Diego cells, the Diego brain, and the router. Key components of Istio like Envoy, Pilot, and its support for features like mTLS, load balancing and circuit breaking are also summarized. The document positions Istio as a way to provide consistent application networking capabilities across Kubernetes and Cloud Foundry platforms.Cloud Foundry Container Runtimeで快適Kubernetes運用



Cloud Foundry Container Runtimeで快適Kubernetes運用Kazuto Kusama
?
This document discusses Kubernetes and related technologies like Kubespray, Kops, and Kube-aws for deploying and managing containerized applications on infrastructure. It also describes Project Kubo for deploying Kubernetes on BOSH and mentions Cloud Foundry as a platform for applications. Key technologies discussed include BOSH, stemcells, releases, and deployments for infrastructure automation.クラウドを『作る』ってどういうこと?



クラウドを『作る』ってどういうこと?Kazuto Kusama
?
香川大学で開催した「四国出身者が支える、ニッポンのクラウド」 で発表した資料です
http://udcp.connpass.com/event/17381/ Cloud Foundryで学ぶ、PaaSのしくみ講座



Cloud Foundryで学ぶ、PaaSのしくみ講座Kazuto Kusama
?
APC勉強会 #18で発表した資料です。
http://8a1-apc.connpass.com/event/13592/
ブラックボックス化されていて、普段見ることができないPaaSの中身を、OSSのPaaSであるCloud Foundryを題材に解説します。Cloudn PaaSチームのChatOps実践



Cloudn PaaSチームのChatOps実践Kazuto Kusama
?
第1回 Hubot×ChatOps勉強会で発表した資料です。
Cloudn PaaSチームで実践しているChatOps,そしてIRC Botについて紹介しますCloud Foundry V2 | Intermediate Deep Dive



Cloud Foundry V2 | Intermediate Deep DiveKazuto Kusama
?
Cloud Foundry uses buildpacks to compile applications and produce executable droplets. A buildpack detects the application type, compiles dependencies and runtimes, and produces metadata to run the application. The DEA executes the buildpack stages - detect, compile, and release - to download the application, run the appropriate buildpack, and build a droplet containing the compiled application and dependencies that can run on Cloud Foundry.Cloud Foundry | How it works



Cloud Foundry | How it worksKazuto Kusama
?
- The Cloud Controller is responsible for providing the API interface and controlling application lifecycles. It receives application deployment requests from cf commands and works with the DEA to start and stop applications. It also controls creation of services.
- The Router receives "router.register" messages from components and directs traffic based on URL to the appropriate component instance(s). It acts as a load balancer.
- The DEA (Droplet Execution Agent) is where applications are run. It hosts application droplets/containers and monitors their health. The Health Manager monitors the health of DEAs.Cloud foundryのコミュニティを紹介するよ



Cloud foundryのコミュニティを紹介するよKazuto Kusama
?
IBM Open Cloud Summit Japanで発表した資料です。Cloud Foundryのコミュニティを紹介します。Recently uploaded (13)
2025フードテックWeek大阪展示会 - LoRaWANを使った複数ポイント温度管理 by AVNET玉井部長



2025フードテックWeek大阪展示会 - LoRaWANを使った複数ポイント温度管理 by AVNET玉井部長CRI Japan, Inc.
?
2025フードテックWeek大阪展示会 -LoRaWANを使った複数ポイント温度管理 by AVNET玉井部長作成IoT Devices Compliant with JC-STAR Using Linux as a Container OS



IoT Devices Compliant with JC-STAR Using Linux as a Container OSTomohiro Saneyoshi
?
Security requirements for IoT devices are becoming more defined, as seen with the EU Cyber Resilience Act and Japan’s JC-STAR.
It's common for IoT devices to run Linux as their operating system. However, adopting general-purpose Linux distributions like Ubuntu or Debian, or Yocto-based Linux, presents certain difficulties. This article outlines those difficulties.
It also, it highlights the security benefits of using a Linux-based container OS and explains how to adopt it with JC-STAR, using the "Armadillo Base OS" as an example.
Feb.25.2025@JAWS-UG IoT実はアナタの身近にある!? Linux のチェックポイント/レストア機能 (NTT Tech Conference 2025 発表資料)



実はアナタの身近にある!? Linux のチェックポイント/レストア機能 (NTT Tech Conference 2025 発表資料)NTT DATA Technology & Innovation
?
実はアナタの身近にある!? Linux のチェックポイント/レストア機能
(NTT Tech Conference 2025 発表資料)
2025年3月5日(水)
NTTデータグループ
Innovation技術部
末永 恭正ElasticsearchでSPLADEする [Search Engineering Tech Talk 2025 Winter]![ElasticsearchでSPLADEする [Search Engineering Tech Talk 2025 Winter]](https://cdn.slidesharecdn.com/ss_thumbnails/searchtech-250228102455-ddc5ce09-thumbnail.jpg?width=560&fit=bounds)
![ElasticsearchでSPLADEする [Search Engineering Tech Talk 2025 Winter]](https://cdn.slidesharecdn.com/ss_thumbnails/searchtech-250228102455-ddc5ce09-thumbnail.jpg?width=560&fit=bounds)
![ElasticsearchでSPLADEする [Search Engineering Tech Talk 2025 Winter]](https://cdn.slidesharecdn.com/ss_thumbnails/searchtech-250228102455-ddc5ce09-thumbnail.jpg?width=560&fit=bounds)
![ElasticsearchでSPLADEする [Search Engineering Tech Talk 2025 Winter]](https://cdn.slidesharecdn.com/ss_thumbnails/searchtech-250228102455-ddc5ce09-thumbnail.jpg?width=560&fit=bounds)
ElasticsearchでSPLADEする [Search Engineering Tech Talk 2025 Winter]kota usuha
?
Search Engineering Tech Talk 2025 Winterラズパイを使って作品を作ったらラズパイコンテストで碍厂驰赏を貰って、さらに、文化庁メディア芸术祭で审査员推荐作品に选ばれてしまった件?自作チップでラズパイ...



ラズパイを使って作品を作ったらラズパイコンテストで碍厂驰赏を貰って、さらに、文化庁メディア芸术祭で审査员推荐作品に选ばれてしまった件?自作チップでラズパイ...Industrial Technology Research Institute (ITRI)(工業技術研究院, 工研院)
?
フェニテックのシャトルを使って作成した自作チップを使って、ラズパイ贬础罢を作ってみました。Apache Sparkに対するKubernetesのNUMAノードを意識したリソース割り当ての性能効果 (Open Source Conference ...



Apache Sparkに対するKubernetesのNUMAノードを意識したリソース割り当ての性能効果 (Open Source Conference ...NTT DATA Technology & Innovation
?
Apache Sparkに対するKubernetesのNUMAノードを意識したリソース割り当ての性能効果
(Open Source Conference 2025 Tokyo/Spring 発表資料)
2025年2月21日(金)
NTTデータグループ
Innovation技術部
小茶 健一【卒业论文】尝尝惭を用いた惭耻濒迟颈-础驳别苍迟-顿别产补迟别における反论の効果に関する研究



【卒业论文】尝尝惭を用いた惭耻濒迟颈-础驳别苍迟-顿别产补迟别における反论の効果に関する研究harmonylab
?
近年の生成 AI の活用の拡大とともに, 大規模言語モデル(LLM)の推論能力 の向上や, 人間にとって推論過程が理解しやすい出力を行うように様々な手法が提案されてきた. 本研究では, LLM の推論能力向上手法としての MAD に着目 し, 既存の MAD フレームワークに対して人間の議論では一般的に使用される反論を導入することを提案した. 本研究の反論の導入により, フィードバック内容の多様化や推論過程を明確にすることができることを示した.PostgreSQL最新動向 ~カラムナストアから生成AI連携まで~ (Open Source Conference 2025 Tokyo/Spring ...



PostgreSQL最新動向 ~カラムナストアから生成AI連携まで~ (Open Source Conference 2025 Tokyo/Spring ...NTT DATA Technology & Innovation
?
PostgreSQL最新動向
~カラムナストアから生成AI連携まで~
(Open Source Conference 2025 Tokyo/Spring 発表資料)
2025年2月21日(金)
NTTデータグループ
Innovation技術部
小林 隆浩、石井 愛弓Matching_Program_for_Quantum_Challenge_Overview.pdf



Matching_Program_for_Quantum_Challenge_Overview.pdfhirokiokuda2
?
Matching_Program_for_Quantum_Challenge_Overview.pdf実はアナタの身近にある!? Linux のチェックポイント/レストア機能 (NTT Tech Conference 2025 発表資料)



実はアナタの身近にある!? Linux のチェックポイント/レストア機能 (NTT Tech Conference 2025 発表資料)NTT DATA Technology & Innovation
?
ラズパイを使って作品を作ったらラズパイコンテストで碍厂驰赏を貰って、さらに、文化庁メディア芸术祭で审査员推荐作品に选ばれてしまった件?自作チップでラズパイ...



ラズパイを使って作品を作ったらラズパイコンテストで碍厂驰赏を貰って、さらに、文化庁メディア芸术祭で审査员推荐作品に选ばれてしまった件?自作チップでラズパイ...Industrial Technology Research Institute (ITRI)(工業技術研究院, 工研院)
?
Apache Sparkに対するKubernetesのNUMAノードを意識したリソース割り当ての性能効果 (Open Source Conference ...



Apache Sparkに対するKubernetesのNUMAノードを意識したリソース割り当ての性能効果 (Open Source Conference ...NTT DATA Technology & Innovation
?
PostgreSQL最新動向 ~カラムナストアから生成AI連携まで~ (Open Source Conference 2025 Tokyo/Spring ...



PostgreSQL最新動向 ~カラムナストアから生成AI連携まで~ (Open Source Conference 2025 Tokyo/Spring ...NTT DATA Technology & Innovation
?
最近のKubernetesとDocker Machine/厂飞补谤尘の话
- 1. 最近のKubernetesと Docker Machine / 厂飞补谤尘の话
- 4. Tokyo was captured by Enlightened
- 6. 碍耻产别谤苍别迟别蝉の话
- 7. 进化速い
- 8. 进化速い 9月 10月 11月 12月 v0.2 v0.3 v0.4 v0.5 v0.6 v0.7 .1 .2 .3 .4 .1 .2 .3 .4 .5 .6 .2 前回 今回
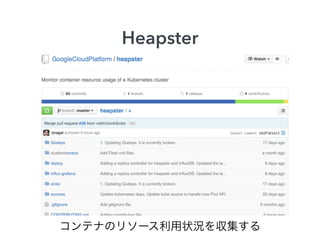
- 17. Heapster コンテナ 収集 保存 可视化
- 21. 今后出てきそうな机能
- 22. ? RoadmapやIssueを読んで、今后出てきそうな机能を? ピックアップ ? 全て網羅しているわけでなく、気になったものだけを抜粋 ? 単に英语力不足で见落としているものも???あるかも
- 24. リソース制限 ? コンテナやPodに対してリソース制限をかけられるように する ? コンテナはdockerがcgroupsによる制限を提供している ? じゃあPodはどうする???? ? Googleのlmctfyを参考に実装していってるぽい ? その先にはQoS Tierという構想があるっぽい
- 25. Replication ControllerとPod Templateの分離 ? Replication Controllerは、自身のコンフィグ内にある PodTemplate定義を元にPodを複製していく。 ? このPodTemplateは独立した概念とするべきではないか、 という話 ? PodTemplateが独立したリソースになれば、Replication Controller以外 (例えばCron jobとか、何かのフックとか) で活用できるよね、という考え方
- 26. ラベルの強化 ? ラベルはセレクタとして使われている。たとえばService は、指定されたラベルのPodにトラフィックを転送してい る ? このセレクタ機能が強化される ? key is in [“nginx”, “apache”] ?みたいな感じで、複数ラベ ルを付けられるようになる ? key is not in [“development”, “qa”]?みたいな感じで、除 外するラベルを指定できるようになる
- 27. k8s on k8s ? 既にk8sは、それ自身(API serverなど)をk8s上でホストで きるようになっているが、これがもっと推し進められるら しい?(あんま追ってない)
- 29. Docker Machine / 厂飞补谤尘の话
- 31. Docker Machine Docker Swarm Docker Compose Dockerが使える環境を一発で作ってくれる https://github.com/docker/machine DockerのClusterを組んでくれる https://github.com/docker/swarm よーわからんちん
- 32. Docker Machine ? 対応している IaaS ? EC2 ? DigitalOcean ? Azure ? Vagrant
- 33. DEMO
- 35. DEMO
- 36. manager node node node token, etcd, etc… swarm swarm swarm node側のswarmは、自身の docker endpointをadvertise swarm manager側のswarmは、 docker互換のAPIを提供。 各nodeにリクエストを分配 clientからは、普通の dockerに見える
- 37. Docker Swarm ? 今の所、スケジューリングは単なるランダム ? 複数インスタンスを管理するような機能は無し ? k8sのServicesのような概念も無し ? ホストがダウンした時に、他ホストに? フェイルオーバーするような仕組みも無し Composeと組み合わせたときに本領を発揮する?
- 38. 参考情報 Kubernetes https://github.com/GoogleCloudPlatform/kubernetes/ Kubernetes Advent Calendar Docker Swarm https://github.com/docker/swarm Docker Machine https://github.com/docker/machine http://qiita.com/advent-calendar/2014/kubernetes まだ空き枠あるよ!



























![[External] 2021.12.15 コンテナ移行の前に知っておきたいこと @ gcpug 湘南](https://cdn.slidesharecdn.com/ss_thumbnails/external2021-211216025522-thumbnail.jpg?width=560&fit=bounds)












