恳亲会の余兴スライド
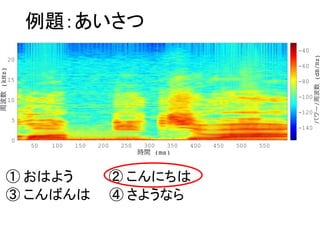
- 4. 例題:あいさつ ① おはよう ② こんにちは ③ こんばんは ④ さようなら 50 100 150 200 250 300 350 400 450 500 550 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 5. 名古屋名物 ① 手羽先 ② きしめん ③ ういろう ④ 味噌カツ 100 200 300 400 500 600 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 6. 名古屋名物 ① 天むす ② エビフライ ③ ひつまぶし ④ 味噌おでん 100 200 300 400 500 600 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 7. 音声関連研究室の先生(敬称略) ① 板倉 文忠 ② 中川 聖一 ③ 北村 正 ④ 北澤 茂良 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 1 1.1 0 5 10 15 20 -140 -120 -100 -80 -60 -40 (スペクトログラムに入っている不自然な線は収録時に混入したノイズのためです)
- 8. 音声関連研究室の先生(敬称略) ① 武田 一哉 ② 徳田 恵一 ③ 西村 雅史 ④ 秋葉 友良 100 200 300 400 500 600 700 0 5 10 15 20 -140 -120 -100 -80 -60 -40 (スペクトログラムに入っている不自然な線は収録時に混入したノイズのためです)
- 9. 音声関連研究室の先生(敬称略) ① 甲斐 充彦 ② 李 晃伸 ③ 速水 悟 ④ 竹林 洋一 0.2 0.4 0.6 0.8 1 1.2 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 10. 音声関連研究室の先生(敬称略) ① 小暮 悟 ② 立蔵 洋介 ③ 西野 隆典 ④ 坂野 秀樹 100 200 300 400 500 600 700 800 900 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 11. ATR音素バランス503文 ① あらゆる現実を全て自分のほうへねじ曲げたのだ ② 小さな鰻屋に、熱気のようなものがみなぎる ③ 周りの美しい雪景色を見る余裕も出た ④ どろぼうでも入ったかと、一瞬僕は思った 0.5 1 1.5 2 2.5 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 12. ATR音素バランス503文 ① 一週間ばかり、ニューヨークを取材した ② テレビゲームやパソコンで、ゲームをして遊ぶ ③ 切符を買うのは、自動販売機からである ④ 一票の格差は、さらに拡がるだろう 0.5 1 1.5 2 2.5 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 13. ATR音素バランス503文 ① なぜ自分ばかりこんな目にあうのだろう ② 変わり雛は世相をつづる ③ 不公平の存在は否認しなかった ④ 青い青い海は、女性の美しさをもっている 0.2 0.4 0.6 0.8 1 1.2 1.4 0 5 10 15 20 -140 -120 -100 -80 -60 -40 (スペクトログラムに入っている不自然な線は収録時に混入したノイズのためです)
- 14. 音声関連研究分野 ① 音声合成 ② 音声認識 ③ 音声対話 ④ 声質変換 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 1 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 15. 音声関連研究分野 ① 音声検索 ② 歌声合成 ③ 話者認識 ④ 音源分離 100 200 300 400 500 600 700 800 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 16. 大学 ① 名古屋大学 ② 岐阜大学 ③ 静岡大学 ④ 名城大学 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 1 1.1 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 17. 大学 ① 名古屋工業大学 ② 三重大学 ③ 豊橋科学技術大学 ④ 岐阜大学 100 200 300 400 500 600 700 800 900 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 18. お酒 ① ワイン ② ビール ③ 焼酎 ④ 梅酒 50 100 150 200 250 300 350 400 450 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 19. 温泉の名所 ① 草津 ② 箱根 ③ 熱海 ④ 有馬 50 100 150 200 250 300 350 400 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 20. 答え合わせ
- 21. 名古屋名物 ① 手羽先 ② きしめん ③ ういろう ④ 味噌カツ 100 200 300 400 500 600 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 22. 名古屋名物 ① 天むす ② エビフライ ③ ひつまぶし ④ 味噌おでん 100 200 300 400 500 600 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 23. 音声関連研究室の先生(敬称略) ① 板倉 文忠 ② 中川 聖一 ③ 北村 正 ④ 北澤 茂良 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 1 1.1 0 5 10 15 20 -140 -120 -100 -80 -60 -40 (スペクトログラムに入っている不自然な線は収録時に混入したノイズのためです)
- 24. 音声関連研究室の先生(敬称略) ① 武田 一哉 ② 徳田 恵一 ③ 西村 雅史 ④ 秋葉 友良 100 200 300 400 500 600 700 0 5 10 15 20 -140 -120 -100 -80 -60 -40 (スペクトログラムに入っている不自然な線は収録時に混入したノイズのためです)
- 25. 音声関連研究室の先生(敬称略) ① 甲斐 充彦 ② 李 晃伸 ③ 速水 悟 ④ 竹林 洋一 0.2 0.4 0.6 0.8 1 1.2 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 26. 音声関連研究室の先生(敬称略) ① 小暮 悟 ② 立蔵 洋介 ③ 西野 隆典 ④ 坂野 秀樹 100 200 300 400 500 600 700 800 900 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 27. ATR音素バランス503文 ① あらゆる現実を全て自分のほうへねじ曲げたのだ ② 小さな鰻屋に、熱気のようなものがみなぎる ③ 周りの美しい雪景色を見る余裕も出た ④ どろぼうでも入ったかと、一瞬僕は思った 0.5 1 1.5 2 2.5 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 28. ATR音素バランス503文 ① 一週間ばかり、ニューヨークを取材した ② テレビゲームやパソコンで、ゲームをして遊ぶ ③ 切符を買うのは、自動販売機からである ④ 一票の格差は、さらに拡がるだろう 0.5 1 1.5 2 2.5 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 29. ATR音素バランス503文 ① なぜ自分ばかりこんな目にあうのだろう ② 変わり雛は世相をつづる ③ 不公平の存在は否認しなかった ④ 青い青い海は、女性の美しさをもっている 0.2 0.4 0.6 0.8 1 1.2 1.4 0 5 10 15 20 -140 -120 -100 -80 -60 -40 (スペクトログラムに入っている不自然な線は収録時に混入したノイズのためです)
- 30. 音声関連研究分野 ① 音声合成 ② 音声認識 ③ 音声対話 ④ 声質変換 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 1 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 31. 音声関連研究分野 ① 音声検索 ② 歌声合成 ③ 話者認識 ④ 音源分離 100 200 300 400 500 600 700 800 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 32. 大学 ① 名古屋大学 ② 岐阜大学 ③ 静岡大学 ④ 名城大学 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 1 1.1 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 33. 大学 ① 名古屋工業大学 ② 三重大学 ③ 豊橋科学技術大学 ④ 岐阜大学 100 200 300 400 500 600 700 800 900 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 34. お酒 ① ワイン ② ビール ③ 焼酎 ④ 梅酒 50 100 150 200 250 300 350 400 450 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 35. 温泉の名所 ① 草津 ② 箱根 ③ 熱海 ④ 有馬 50 100 150 200 250 300 350 400 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 36. 答え合わせ ここまで
- 39. お肉 ① ロース ② カルビ ③ レバー ④ ハラミ 正解 50 100 150 200 250 300 350 400 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 40. ラーメン ① 豚骨ラーメン ② 塩ラーメン ③ 醤油ラーメン ④ 台湾ラーメン 100 200 300 400 500 600 700 800 900 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 41. 動物 ① うさぎ ② ラクダ ③ パンダ ④ ゴリラ 50 100 150 200 250 300 350 400 450 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 42. 果物 ① メロン ② マンゴー ③ オレンジ ④ パイナップル 50 100 150 200 250 300 350 400 450 500 550 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 43. 県名 ① 滋賀 ② 佐賀 ③ 三重 ④ 千葉 50 100 150 200 250 300 350 400 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 44. IT企業 ① グーグル ② マイクロソフト ③ アップル ④ アマゾン 50 100 150 200 250 300 350 400 450 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 45. 野菜 ① ニンジン ② カボチャ ③ ピーマン ④ キャベツ 50 100 150 200 250 300 350 400 450 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 46. 魚 ① サンマ ② カレイ ③ マグロ ④ カジキ 50 100 150 200 250 300 350 400 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 47. 丼もの ① 牛丼 ② 天丼 ③ 豚丼 ④ うな丼 50 100 150 200 250 300 350 400 450 500 550 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 48. 理科系科目 ① 微分積分 ② 線形代数 ③ 複素解析 ④ 数値解析 100 200 300 400 500 600 700 800 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 49. 県名 ① 岡山 ② 大分 ③ 山形 ④ 石川 100 200 300 400 500 600 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 50. カレー ① カツカレー ② ドライカレー ③ スープカレー ④ グリーンカレー 100 200 300 400 500 600 700 800 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 51. 冬に食べるアレ ① 肉まん ② あんまん ③ ピザまん ④ カレーまん 50 100 150 200 250 300 350 400 450 500 550 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 52. 小学校の科目 ① 国語 ② 図工 ③ 体育 ④ 音楽 100 200 300 400 500 600 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 53. ポーカーの役 ① ストレート ② フラッシュ ③ フルハウス ④ ワンペア 100 200 300 400 500 600 700 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 54. 県名 ① 鹿児島 ② 茨城 ③ 新潟 ④ 青森 50 100 150 200 250 300 350 400 450 500 550 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 55. 家電 ① 掃除機 ② 洗濯機 ③ 乾燥機 ④ 冷蔵庫 100 200 300 400 500 600 700 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 56. 麺類 ① ラーメン ② つけ麺 ③ タンメン ④ チャンポン 50 100 150 200 250 300 350 400 450 500 550 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 57. プログラミング言語 ① Perl ② Ruby ③ Python ④ Java 50 100 150 200 250 300 350 0 5 10 15 20 -140 -120 -100 -80 -60 -40
- 58. 県名 ① 愛知 ② 栃木 ③ 岩手 ④ 群馬 50 100 150 200 250 300 350 400 0 5 10 15 20 -140 -120 -100 -80 -60 -40



































































































![[DL輪読会]Wavenet a generative model for raw audio](https://cdn.slidesharecdn.com/ss_thumbnails/wavenetagenerativemodelforrawaudio-160920054055-thumbnail.jpg?width=560&fit=bounds)




